Nov 1
Table of Contents
😈On Nov 1, 2023, a fake Fake Celestia (TIA) Token On ETH was rugged for ~$208.1K, where the deployer swapped over 19,453,820,462,357.507 TIA tokens for 115.321 WETH.
The deployer has already moved the stolen funds to different addresses, and the token value has dropped by ~100%.
ImmuneBytes confirms that this is a honey pot token, and also, the token contract can mint more tokens, which gives a clear hint of a scam token.
Token Contract: 0xCd68ACC0E6C94c0226B0d760D19951143ee7Aa44
Deployer Add: 0xe3cD80B7668C24901d74E5fBed2902Eeaecf02A2
Txn: 0x3d9a1f15bd317ed8ec34b86bf7ec474922965cf2de34a9d83eea864d00640445
😈On Nov 1, 2023. a fake Memecoin (MEME) #Token On BSC was rugged for ~$117.9K, where the deployer sold 72,955,714,057,748.5 $MEME tokens for 117,859 BSC-USD.
Txn: 0x17409e86985e71524aad3aeeb51c1a7553595668f24d62a30d1372685d23bbef
Token Contract: 0xFCb1559536792523e802cd7e816A09F23D634778
Deployer Add: 0xCC78A24926dBd0bc6349aD223e20416fBFC2f66C
The deployer is constantly swapping these fake tokens for BSC-USD. We did our investigations and found that the deployer holds over 99% of these fake tokens.
😈On Nov 1, 2023, @OnyxProtocol, a decentralized finance platform on #ETHEREUM, came under an attack by exploiting a “precision loss vulnerability.”
The losses due to the exploit are to the tune of ~$2.1M.
This vulnerability revolves around a rounding issue, particularly seen in CompoundV2 forks.
Here are key details:
- The attack was orchestrated shortly after the oPEPE market was initialized within Onyx Protocol, as detailed by proposal 22.
- The assailant exploited the vulnerability by minting a minimal amount of shares and then making a substantial donation of PEPE to the oPEPE market.
- This action caused a skewed exchange rate, allowing the attacker to borrow Ethereum (ETH). The precision loss bug within the redeemUnderlying function then enabled the full amount of PEPE to be reverted back to the attacker.
- Following the attack, the exploiter laundered approximately 1,230 ETH using #TornadoCash.
- The total value lost due to the exploit is estimated to be around $2.1 million.
It is noteworthy that this vulnerability was previously identified in an audit conducted for Onyx Protocol and was subsequently acknowledged by the Onyx team.
As a consequence, questions are arising about the platform’s security measures and the steps taken after the audit’s revelations.
Attack Txn: 0xf7c21600452939a81b599017ee24ee0dfd92aaaccd0a55d02819a7658a6ef635
Hacker Add: 0x085bDfF2C522e8637D4154039Db8746bb8642BfF
😈 On Nov 1, 2022, the project @usdtdefi (USDTd) faced a rug pull amounting to ~395.2 BNB on the BSC chain.
Following the exploit, the value of the project plummeted by more than 86%.
The contract owner (0xc8495) quickly sold approximately 395.2 BNB and transferred the funds to 0x97D07.
Hacker’s Wallet: 0xc8495cc5008572208af0385c5aa10308ca4f0a78
Contract Address: 0x93d00a0fbd822f249458c5f973bee6c5248670a9
😈On Nov 1, 2021, A devastating attack on Boy X Highspeed (BXH), a decentralized cross-chain exchange, resulted in a loss of $139 million.
The hack, potentially an inside job, was due to a leaked administrator key, as revealed by CEO Neo Wang to CoinDesk.
Investigations suggest the hacker might have accessed the exchange’s Binance Smart Chain address via the administrator’s private key.
This attack could have been avoided if BXH had taken the security measures mentioned here:
Compromised Private Keys: Threats and Remedies
Nov 2
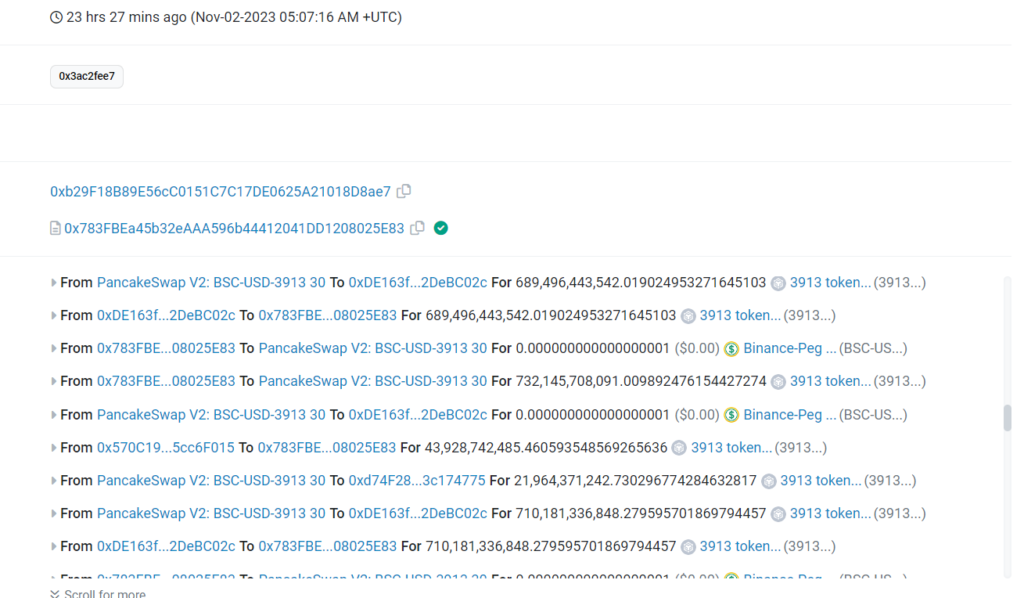
😈On Nov 2, 2023, Token 3913 on BSC was exploited for ~$31.5K in a flash loan attack.
Hack Details
Attack Txn: 0x8163738d6610ca32f048ee9d30f4aa1ffdb3ca1eddf95c0eba086c3e936199ed
Hacker Add: 0xb29F18B89E56cC0151C7C17DE0625A21018D8ae7
Token Contract: 0xd74F28c6E0E2c09881Ef2d9445F158833c174775
Attack Methodology
Bonus Mechanism Flaw: The token had a feature to give bonuses to new token holders. For this, _transfer function would check if a transaction is from a Pancake pair sending tokens to a new user, like a swap from USDT to 3913.
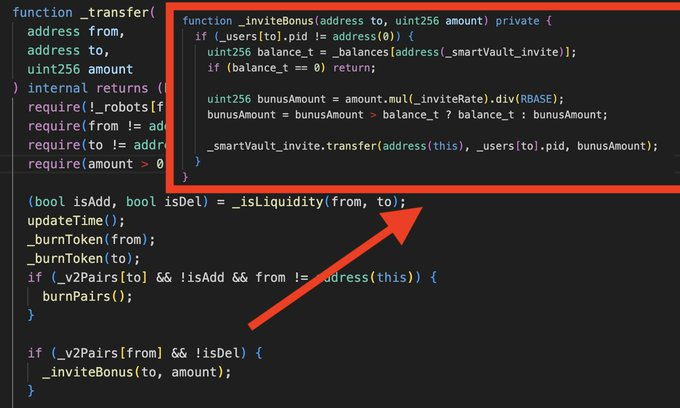
Skim Vulnerability: The contract didn’t safeguard against the potential that a malicious user could force a Pancake/Uniswap pair to send tokens to any address using a skim() call.
Exploitation Steps:
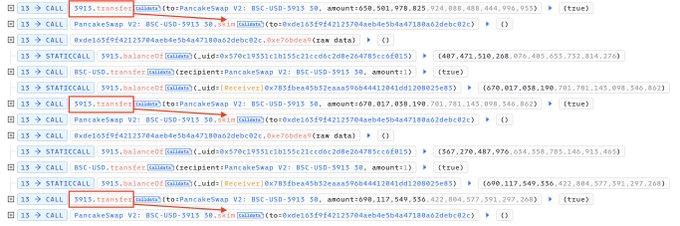
The attacker leveraged a flash loan to buy 3913 tokens.
They then kept transferring these tokens back to the pair address.
By repeatedly calling skim() and repeating the above step, the attacker deceived the contract into releasing all available bonuses.
😈On Nov 2, 2022, @solendprotocol (Solend) faced a sophisticated exploitation where an attacker manipulated the USDH stablecoin price on Saber for $1.2M.
The attacker took advantage of Solend’s isolated pools that relied on a vulnerable USDH price feed.
The attacker adeptly managed to pump the USDH price, write-lock the Saber account, and conduct self-arbitration to siphon off assets worth approximately $1.2M.
Although the initial loss was significant, by August 16, Solend successfully recovered ~$900K of the originally lost amount, ensuring that no users faced financial losses from the incident.
Solend’s Isolated Pools Exploitation—Nov 2, 2022—Detailed Analysis
Nov 5
😈On Nov 5, 2022, the decentralized finance protocol, @pando_im, experienced a significant breach.
The attackers made off with a staggering ~$20 million by exploiting an oracle manipulation vulnerability.
What are Oracle Manipulation Attacks in Blockchain?
The attacker managed to exploit a vulnerability in Pando’s Rings price oracle, manipulating the sBTC-WBTC liquidity provider token’s price on 4swap.
Pando Rings Hack—Nov 5, 2022—Detailed Analysis
Nov 7
😈On November 7, 2023, an MEV bot on the Ethereum network was exploited for approximately $2 million.
The vulnerability exploited was due to the absence of access controls on the bot’s arbitrage function, identified as 0xf6ebebbb.
The attacker initiated the exploit by taking out a flash loan from Aave to acquire a large amount of Wrapped Ethereum (WETH), which they then used to purchase Wrapped Bitcoin (wBTC) on Curve Finance’s exchange pools. This purchase was made at an inflated price due to the imbalance created in the exchange’s liquidity pool.
Subsequently, by exploiting the bot’s vulnerable function, the attacker forced the bot to conduct transactions that bought wBTC at these unreasonable prices. The attacker then sold the wBTC at a profit, completing the arbitrage by reversing the swaps and repaying the flash loan.
As a result of this exploit, significant slippage occurred across multiple Curve.fi pools. The bot’s owner has since withdrawn the remaining funds from the contract, potentially to prevent further losses.
Attack Txn: 0xbc08860cd0a08289c41033bdc84b2bb2b0c54a51ceae59620ed9904384287a38
Bot Contract: 0x46d9b3dfbc163465ca9e306487cba60bc438f5a2
😈On Nov 7, 2023, TrustPad, a known decentralized finance (DeFi) protocol, suffered a security breach resulting in an approximate loss of $155,000.
The exploit was carried out through a vulnerability in the protocol’s smart contract, specifically within the staking logic of the LaunchpadLockableStaking contract.
Detailed Report: Defi Launchpad ‘Trustpad’ Exploited for $155K
😈On Nov 7, 2023, @thestandard_io, a decentralized finance platform, experienced a significant security breach.
An exploiter capitalized on the low liquidity slippage of PAXOS GOLD on the Arbitrum network, operating through Uniswap, a popular decentralized exchange. The unauthorized party managed to extract approximately 8,500 USDC.e and 280,000 EURO tokens.
Following the exploit, the attacker minted an Algebra position NFT containing 222,819 EUROs, an action that may potentially allow them to move the funds or conceal their trail. The core team of the affected project has taken immediate action to mitigate the impact of the breach.
They have suspended the creation of any new V2 vaults and halted all new EUROs minting processes to prevent further exploitation. The team has also issued a public plea to the exploiter, urging them to negotiate a return of the assets.
They emphasized the project’s small scale and its mission to contribute positively to the world, highlighting the lack of extensive financial resources to absorb such losses.
Despite the exploit, the platform’s core team has assured stakeholders that no collateral has been compromised in the Smart Vaults, which are designed to safeguard users’ assets. They have declared that an active investigation is underway and have promised to keep the community updated as new information arises.
😈On Nov 7, 2022, the mooCakeCTX project on the BNB chain, experienced a flash loan attack, resulting in losses of $143,921.
The exploit was due to a critical flaw where the contract was re-invested without settling rewards.
An attacker utilized a flash loan of 50,000 CAKE tokens, which they then pledged and withdrew in quick succession, exploiting the contract’s failure to settle rewards.
Attacker’s Wallet: 0x35700c4a7bd65048f01d6675f09d15771c0facd5
😈DeFi Safe (dSafe) token on the BNB chain fell victim to an exit scam on Nov 7, 2022.
The contract creator blacklisted holders and removed liquidity to pocket approximately ~$127K. The token’s value plummeted by >99%.
Contract: 0x761776f726168c9dF6dC63d5864880801E21F403
😈 On Nov 7, 2022, the GDS token on the BNB chain suffered an exit scam with losses of around $60K.
The malicious actor set the selling fee to an exorbitant 9900 before draining the liquidity, resulting in a token price drop of >99%.
Contract: 0x7f19bF116B0F0a4af7d4464CbF584fE75a243fc9
😈On Nov 7, 2022, the EOA 0xa148a exploited @transhumancoin’s staking contract on the BNB chain to siphon rewards without a lockup period.
The attacker’s strategy involved “staking” and “unstaking” in a single transaction, gaining > 94 BNB.
Attacker Address: 0xa148a24188045a5cb3f7aacb9fed1dd60c3a6cfd
Exploited Contract: 0x144960c94c846d30c3b4f373c348ed5f13c1f42a
Exploit Tx: 0x213a45896c928a399fd2cde888989e7ee3bc461be46237e7bf367f1a52d81d60
The flawed “calcRewards” function was identified as the culprit, returning default rewards without accounting for lockup periods.
Nov 8
😈On Nov 8, 2023, Australian #cryptoexchange @coinspotau hot wallets were drained of 1,283 $ETH (~$2M).
The stolen ETHs were transferred to the attacker from 2 CoinSpot wallets.
Out of the allegedly stolen funds, the attacker bridged ~831 $ETH for 41 $BTC via #Thorchain and swapped 451 $ETH for 24 $WBTC.
The reasons behind the exploit are currently being investigated.
Attacker Add: (ETH) 0x326dc417d96c72349FA3d1fda4aE9C1c77FD89B8
Exploited CoinSpot Wallet 1:
0xE4b3dD9839ed1780351Dc5412925cf05F07A1939
Exploited CoinSpot Wallet 2:
0x32E567E8B527d3194C60ea3C6a5c009d58A0B36d
Stolen Funds are currently held at the following BTC Addresses:
- 21.12 BTC($756,577) at the address: bc1qfsm2vhhurrq54w40z8vasjkfhxrvsvysjk9jug
- 14.26 BTC($511,421) at the address: bc1q49d37gnmdu4p77n9j8c7ytrv30xrrue50r88lh
- 8.55 BTC ($306,742) at the address: bc1qtj29wrm56r0lvhqufsju9pr0vakj8uwd38p4gj
- 20 BTC ($731,836) at the address: bc1 bc1qzl2s7ajehkpu9wdqewg5xqy8nzxv7njctvrqzx
- 4.3 BTC ($146,367) at the address: 1LkaBjcEYycu4UezJK2F1pXjTff8b4bdXo
😈On Nov 8, the ‘To The Moon token’ ($TTM) token on the BSC chain suffered a price slippage when an EOA called the emergencyWithdraw() function on the FeeTreasury contract and sold his TTM tokens.
This EOA is suspected to be a privileged address, raising concerns of a possible rug pull.
Other holders have also started dumping their tokens, causing the price of the token to fall even more
Token Contract: 0x2728c49f42f4ac5A38dA0080B27DEd5EC04b05CC
EOA: 0x2a0711c272daAEd74593b60Dc39bC64965743de0
Txn: 0x3f60dd18151c3198b9a6a13cbd0a9796777091ff76a62bc9ff35cc2c78c979e5
😈On Nov 8, 2023, Mirage Finance $MRG on #ETH was exploited for ~$12K
The attacker used flash loans to manipulate the price and earned about ~7 ETH in profit, which have already been moved to different addresses. The $MRG token is already down by ~54%, and the attacker was
originally funded with 0.2 $ETH from #OKX.
Token Contract: 0x0d99F24E96c42432a758124496F4ce9C67f6aA7b
Txn: 0xb3456a338d7b3e7936a4d08b34e265818c116b7871baef8df1492a35f9f3b1bc
Exploiter add: 0x4843E00Ef4c9f9f6e6aE8d7b0A787f1C60050b01
😈 On Nov 8, 2022, USDTd on the BSC chain suffered a massive price slippage due to a potential exit scam.
The owner reportedly unlocked and sold USDTd for about ~$33K. Following the incident, the project’s social media presence, including Twitter, has vanished.
Contract: 0x93d00a0fbd822f249458c5f973bee6c5248670a9
😈 On Nov 8, 2022, The $BOXC token (@BOXCcasino) on Ethereum experienced a drastic ~99% drop after a massive sell-off by the deployer. The deployer got profited by ~$67.7K.
Transaction: 0x4343f5f263db8b7d04fc2c61559866e8e8b21a6bde18b126cc3847153d62df7e
Contract: 0x8f9f22f74eef70492b020783997012040fb49630
😈 On Nov 8, 2022, $BOXC token on the BSC chain suffered a rug pull when the deployer sold approximately ~$90K worth of tokens.
Transaction: 0x63ee773cafa976e891f212aeaf3022accb818162ec88f03fc3cad7f2b6b1ea1b
😈 On Nov 8, 2022, the Lottery Swap (LOTTO) token on the BSC chain suffered an #exitscam with losses of around ~$100K as the token’s value plummeted by more than 90%.
Contract: 0x605cfb514a2845902e17ed3c9416bd461e3f2e1b
😈 On Nov 8, 2022, SSIDToken (SSID) on the BSC chain also fell victim to an exit scam, erasing >93% of its value, equating to losses of ~$158K.
Contract: 0xC3241e111CCd9CF6c5a11dADE9498070082F2ed3
😈 On Nov 8, 2022, Defi Wz Token (DEFIWZ) on the BSC chain witnessed an exit scam, dropping >88% and resulting in approximately ~$208K stolen.
Contract: 0x418Db510B4f1CF33565C459cfB6D838bbbbFf8F9
Nov 10
😈On November 10, 2023, the Raft protocol (@raft_fi), a decentralized finance (DeFi) platform on the Ethereum blockchain, suffered a major exploit, leading to a loss of ~1577 ETH.
The attack revolved around a precision loss issue in the protocol’s smart contracts, which significantly manipulated Raft’s stablecoin, R.
Exploit Transaction: https://etherscan.io/tx/0xfeedbf51b4e2338e38171f6e19501327294ab1907ab44cfd2d7e7336c975ace7
Raft Exploiter: https://etherscan.io/address/0xc1f2b71a502b551a65eee9c96318afdd5fd439fa
Exploited Contract (InterestRatePositionManager): https://etherscan.io/address/0x9ab6b21cdf116f611110b048987e58894786c244
Raft Protocol Detailed Hack Analysis
😈On November 10, 2023, in a significant security incident, the cryptocurrency exchange @Poloniex experienced a breach in its hot wallet system, leading to a substantial loss of digital assets.
This incident involved the theft of approximately $130 million worth of cryptocurrencies across multiple blockchain networks, including Ethereum (ETH), TRON (TRX), and Bitcoin (BTC).
Breakdown of the Incident:
The extent of Losses: The breach resulted in the loss of around $130 million in cryptocurrencies, distributed as more than $56 million in ETH, more than $48 million in TRX, and more than $18 million in BTC.
Cause of the Breach: Preliminary analysis suggests that the breach was caused by a compromise of private keys (PK). This type of security lapse has accounted for 57% of all crypto asset losses in 2023.
Suspected Perpetrators: There is a strong belief that the North Korea-backed hacking group, the Lazarus Group, is behind this attack. This suspicion arises from the similar tactics used in this breach and a previous incident at http://Stake.com in September 2023.
Poloniex’s Immediate Actions: Following the detection of the breach, Poloniex temporarily disabled its wallet system to prevent further losses.
Asset Recovery Efforts: Justin Sun, the owner of Poloniex, reported that some of the stolen assets had been successfully identified and frozen. He also reassured that the losses are within manageable limits and can be covered by the exchange’s operating revenue.
User Reimbursement Plans: Justin Sun has committed to fully reimbursing affected users. Additionally, he has offered a 5% bounty to recover the stolen funds.
Operational Status: As of the latest updates, Poloniex has not specified when it will resume deposits and withdrawals.
This incident underscores the ongoing challenges crypto exchanges face in ensuring digital asset security.
The involvement of state-backed entities like the Lazarus Group highlights the sophisticated nature of threats in the crypto space. It also emphasizes the importance of robust security measures, especially regarding safeguarding private keys.
😈On Nov 10, 2022, DFX Finance on Ethereum faced a sophisticated attack with the perpetrator utilizing a flash loan exploit to siphon off over $7M.
The exploit took advantage of a missing reentrancy guard in the flash loan function, allowing the attacker to mislead the DFX contract into releasing funds without the proper checks.
Attack Txn (ETH): 0x390def749b71f516d8bf4329a4cb07bb3568a3627c25e607556621182a17f1f9
Attacker’s Address (ETH): 0x14c19962e4a899f29b3dd9ff52ebfb5e4cb9a067
DFX Finance Hack Analysis Report
😈On Nov 10, 2022, The Fair Coin (FAIR) project on the BSC network was hit by an exit scam. The token’s value plummeted by ~94.68%, with losses reaching ~$326K.
Token Contract: 0xC5C24Cb9177A130128Fb15b0B0a74a502974F379.
😈On Nov 10, 2022, a severe slippage incident occurred with the @OK__DAO (OKD) token.
The token saw a drop of over 90% in value. The deployer transferred OKD tokens to the address 0xe8e00, which were then sold for approximately ~$140K.
OKD contract (BSC): 0x048615944cce737ff3ddc1a20667e7ce1ef2b245
Nov 14
😈On November 14, 2020, Value DeFi was hacked for $7.4 million in DAI due to a sophisticated flash loan attack exploiting Oracle vulnerabilities.
The attacker manipulated asset prices on UniswapV2 and Curve’s 3pool, leading to an imbalanced exchange of tokens and a substantial profit.
Value DeFi Detailed Hack Analysis
Nov 15
😈On November 15, a trio of phishing addresses— #Fake_Phishing187019 and #Fake_Phishing188246, along with #Fake_Phishing188615—collectively scammed about $3.4 million in various cryptocurrencies.
The attacks spanned multiple networks — Ethereum, Polygon, and Arbitrum — specifically targeting the address 0xc108…2575.
Additionally, the phisher behind these schemes became a victim of a sandwich attack during an Ethereum (ETH) swap.
What are Sandwich Attacks in Blockchain?
Details of the Phishing Entities and Links
Fake_Phishing187019: https://etherscan.io/address/0x0000db5c8b030ae20308ac975898e09741e70000
Fake_Phishing188615: https://etherscan.io/address/0xed0e416e0feea5b484ba5c95d375545ac2b60572
This contract was created by Fake_Phishing187019 specifically for scamming purposes.
Fake_Phishing188246: https://etherscan.io/address/0x53d0e4dab3e125dd25ecfb24ca610075fa9bc8e1
Nov 16
On November 16, a new phishing incident emerged involving addresses:
😈#Fake_Phishing187019
😈#Fake_Phishing188246
😈#Fake_Phishing188695
These scammers successfully phished 581.07K $AIX, valued at ~$112.23K, from the victim with the address 0x1db3…fcda.
Fake_Phishing187019: https://etherscan.io/address/0x0000db5c8b030ae20308ac975898e09741e70000
Fake_Phishing188246: https://etherscan.io/address/0x53d0e4dab3e125dd25ecfb24ca610075fa9bc8e1
Fake_Phishing188695: https://etherscan.io/address/0x0000c5d73291e9ae226e7fe59ea1e6b68be30000
A Guide to Crypto Phishing Attacks
😈On Nov 16, 2022, LYRA (LYRA) Token Scam Was Rugged
Fake token with price slippage, value dropped >99%.
BSC Contract: 0x7CE571523587dd12A56Abd311cdbb7Eb69b72323
Amount Taken: ~$1.13M, swapped for USDT by the deployer.
😈On Nov 16, 2022, Artificial Intelligence Robot (AIT) Token on BSC Was Rug Pulled
Token value plummeted >89.3%.
BSC Contract: 0xD5B33544d03f54f4E4556Fe6CC53254c4FF43EF7
Amount Taken: ~ $152K by the deployer.
😈On Nov 16, 2022, Boxer Inu Finance (BOXER) on BSC Was Rugged
Approx. $146K taken, funds swapped to WBNB.
BSC Contract: 0x192e9321b6244d204d4301afa507eb29ca84d9ef
😈On Nov 16, 2022, Copycat Meta (META) Token on BSC Was Rugged
Token value dropped >99.97%.
BSC Contract: 0x40Be57E8910dA65f5B98746C730E26941aB3824A
Amount Lost: ~ $58.1K by the deployer.
Nov 17
😈On Nov 17, the third consecutive day of the phishing attacks by notorious phishing addresses, another victim
(0x46ba2370b09f4f56fba87052df92fe6beffd7e8d) took the bait and lost $67.15K worth of 155.96K $SAND tokens to the phishing addresses:
- Fake_Phishing187019: https://etherscan.io/address/0x0000db5c8b030ae20308ac975898e09741e70000
- Fake_Phishing188246: https://etherscan.io/address/0x53d0e4dab3e125dd25ecfb24ca610075fa9bc8e1
- Fake_Phishing188615: https://etherscan.io/address/0xed0e416e0feea5b484ba5c95d375545ac2b60572
These infamous addresses were found to be involved in the phishing incidents of Nov 15 and Nov 16, where they scammed other EOAs in excess of $3.4M worth of crypto assets.
Hack Txn: https://etherscan.io/tx/0x9f7a0742b573056185de72acb71afd1e59293ff41d6e06d8d41da6ce4b132c38
😈On Nov 17, 2022, the project TTTT token and CTT(@crazytreasure_) token on the BNB chain suffered an exit scam, and token prices took a beating of over 93% for both tokens.
The losses incurred by the Project TTTT and CTT tokens were ~$261K and ~$56K, respectively.
Contract BSC Project TTTT: 0x374DF15933567E9B3ef19361d64B708519D31695
Contract BSC CTT: 0xF56783b3A4fA5F09EfcA962bd4Bab1F5FADD9aB9
😈On Nov 17, 2022, the defi UEarnPool’s staking contract on the BNB chain was attacked using a flash loan, which caused the loss of 16,038 USDT.
Victim Contract Address on BSC: 0x02d841b976298dcd37ed6cc59f75d9dd39a3690c
😈On Nov 17, 2020, the Origin protocol was exploited for ~$7.7M of crypto assets, which included 11,809 ETH and 2,249,821 DAI.
The attacker took advantage of a bug in the handling of the mint logic in Origin protocol’s VaultCore smart contract and leveraged a reentrancy attack and flash loan attack to pull off the exploit.
Hack Txn: https://etherscan.io/tx/0xe1c76241dda7c5fcf1988454c621142495640e708e3f8377982f55f8cf2a8401
Attack Contract:
https://etherscan.io/address/0x47c3d84394043a4f42f6422accd27bb7240fdfe2
Nov 21
😈On November 21, 2022, the Trust Bridge (TWG) suffered an exit scam.
Chain: Binance Smart Chain (BSC)
Incident: An exit scam on the Trust Bridge (TWG) project.
Contract Address: https://bscscan.com/address/0x737F5942D70f8F433d65823535e7Ae1DE1950d8e
Impact: The token’s value dropped by more than 99%, with approximately $120K taken by the contract deployer.
😈On November 21, 2020 – Pickle Finance’s pDAI Jar on Ethereum was exploited for over 19M DAI
Exploit Details: Using multiple flaws in the system, including issues with Jar swap and convert logic, the attacker executed a sophisticated exploit.
Exploit Transaction: https://etherscan.io/tx/0xe72d4e7ba9b5af0cf2a8cfb1e30fd9f388df0ab3da79790be842bfbed11087b0
Pickle Finance Exploit—Detailed Analysis Report
Nov 22
😈On Nov 22, 2023, @KyberNetwork reportedly fell victim to a significant security breach.
The exploit, which spanned across several blockchain networks, resulted in the loss of ~ $45 million in various cryptocurrencies.
Detailed Report: KyberSwap Exploited Loses $45M in a Multi-Chain Exploit
😈On Nov 22, 2023, the HECO Bridge was exploited for ~$87 million due to a suspected private key compromise.
Additionally, ~ $12 million was also stolen from HTX’s hot wallets.
Detailed Report: HECO Bridge Exploited for Over $87M in a Suspected Private Key Leak
Nov 23
😈On Nov 23, 2023, $SAI Pro Token on BSC was exploited for ~$1.7m in an exit scam.
The deployer swapped ~$1.7m worth of $SAI tokens in multiple transactions.
The stolen funds were then transferred to add: 0x23f8c805306Bf27AB8bf3cEbEce4B778acfFd896.
This address had also been found to be involved in the Lucky Star exit scam.
Token Contract Add: 0xBa4cA4A9E1ca603310dF7a171D2291af9f3AfFaA
Deployer: 0x7dFeBF01aA57F48B78721E24A72182e18BcEBA2A
Ice Phishing: What Is It, And How Does It Jeopardize Blockchain And Web3?
😈On Nov 23, 2023, an ETH Address fell victim to a phishing attack where he lost ~375 $stETH.
The infamous phishing address, which goes by the name of Fake_Phishing188246, along with EOA: 0x48b31022D1b28d696a1A3cb7733Dd99409c95EA6 targeted the victim in a total of 2 txns.
This phishing attack is another one in a series of attacks that targeted different victims on Nov 15, Nov 16, and Nov 17, and it involved the same notorious phishing addresses and malicious contracts:
- 0x0000db5c8B030ae20308ac975898E09741e70000 (Fake_Phishing187019)
- 0xed0e416e0fEEA5b484ba5c95d375545AC2b60572 (Fake_Phishing188615)
- 0x53d0E4dAb3E125dd25EcfB24Ca610075Fa9bC8e1 (Fake_Phishing188246)
Hack Txn: 0x85e4c239ac4d68425514c37594e2be882e3e20a297edd2a580d33be74d963add
Victim Add: 0x68C405C11aB443169445646A544d142Eb655aF5d
😈On Nov 23, 2022, The AurumNodePool suffered a significant security breach, leading to a loss of 50 $BNB (approximately $14,538.04).
This incident targeted the AurumNodePool contract $AUR.
The vulnerability stemmed from an oversight in the changeRewardPerNode function within the contract, which lacked proper validation measures. This loophole enabled the attacker to manipulate the function to their advantage.
Utilizing the changeRewardPerNode function, the hacker inflated the daily reward value to an exorbitantly high figure. Following this manipulation, they claimed the node reward through the claimNodeReward function.
The payout for the node reward was calculated based on the artificially increased rewardPerDay value set by the attacker, resulting in a grossly exaggerated reward amount being claimed.
Nov 26
😈On Nov 26, 2023, an ETH address 0xee439Ee079AC05D9d33a6926A16e0c820fB2713A was scammed for ~$1.25M in a phishing attack where it lost ~605 $aETHWETH to Fake_Phishing188696.
Hack Txn: https://etherscan.io/tx/0x8458905f78216cb0e6151977c9977fd0cd5ce46819cc01a738ac3aed3bc5e7bc
The addresses involved are:
- Fake_Phishing187019:
0x0000db5c8B030ae20308ac975898E09741e70000 - Fake_Phishing188583:
0x00004FD598eAcFda276553cdf9f1bE668eAB0000
Fake_Phishing188696: 0xc7C195a20EE6991ef20de42C669F30B27D7c4dD1
The Fake_Phishing187019 address has been involved in many other phishing attacks this month.
Nov 23, 2023: ~$770K
Nov 17, 2023: $67.15K
Nov 16, 2023: $112.23K
Nov 15, 2023: $3.4 million
Avoid falling for phishing scams by crypto scammers by learning more about common phishing techniques.
Nov 27
😈On Nov 27, 2023, RWA Protocol Florence Finance, on the Arbitrum chain, lost about ~$1.45M in an address poisoning scam.
The scammer polluted the victim’s transaction history with fake $USDC token transfers and got hold of USDC tokens worth ~$1.45M when the victim used the phishing address from his transaction history instead of the intended address.
Victim Address: 0x26E4CB4A6787419ac53B7D3FE92fA1DaD1C8548E
Intended address: 0xB087cfa70498175a1579104a1E1240Bd947f5870
Phishing address: 0xB087269DE7ba93d0Db2e12ff164D60F0b3675870
Must Read: What is Address Poisoning? How Can It Result In the Loss of Crypto Assets?
😈 On Nov 27, 2023, a BSC address fell victim to a phishing attack, losing ~$74.4K worth of $USDC.
These scams are becoming common nowadays, especially on BSC and ETH.
Txn: 0x000467487fafd41eca882701da9cba8131777dd54e6252cd0ced1ca235d43820
Victim Add: 0x7Dae328f0c97727d2386c67Caa4C9C0427E6C671
Phishing Addresses:
- 0x000000093E55f433Fb57a32AA5d5Fe717B3f7AB1
- 0x009515EfabCcdBAfA485f3919d94C85Ff23Ba75D
😈On November 27, 2019, Upbit, a major South Korean #cryptocurrency exchange, suffered a significant #hack, leading to the loss of 342,000 ETH, valued at around $50 million.
Established in 2017 and backed by Kakao Corp, Upbit rapidly became a leading exchange in South Korea, offering trades in various cryptocurrencies.
The hack occurred when the exchange’s Ethereum hot wallet, containing $350 million worth of ETH, was compromised.
This incident, executed through phishing and malware to access the wallet’s private keys, highlighted the vulnerabilities in even well-regarded exchanges and profoundly impacted the industry.
Must Read: Compromised Private Keys: Threats and Remedies
Nov 29
😈On Nov 29, 2023, the $AIS token on BSC was exploited for ~$60K in a suspected #flashloan attack, executed by exploiting a smart contract vulnerability.
The attack was executed by a contract created by a different address, which executed a series of transactions, and address 0x8594 got away with 60,686.88 BSC-USD.
Hack Txn: 0x0be817b6a522a111e06293435c233dab6576d7437d0e148b45efcf7ab8a10de0
Token Contract: 0x6844Ef18012A383c14E9a76a93602616EE9d6132
Malicious Contract: 0x15FFd1D02B3918C9e56f75E30D23786D3eF2B5bc
Malicious Contract Deployer: 0x7cb74265E3E2D2B707122BF45aeA66137C6C8891
Address Receiving funds: 0x859444a27eff21b443f6213ec54fd2f1a09de346
😈On November 29, 2022, MBC Token Hack on BSC Was Hacked for ~5.6K BUSD.
Token Contract Add: https://bscscan.com/address/0x4e87880a72f6896e7e0a635a5838ffc89b13bd17
Hacker’s Wallet: https://bscscan.com/address/0x9cc3270de4a3948449c1a73eabff5d0275f60785
Transaction: https://bscscan.com/tx/0xdc53a6b5bf8e2962cf0e0eada6451f10956f4c0845a3ce134ddb050365f15c86
Vulnerability: Misuse of addLiquidity() function & exposed public interface in swapAndLiquifyStepv1() function.
Attack Method: Flash loan attack swapping 11.6k MBC tokens, manipulating token ratio.
😈On November 29, 2022, SEAMAN Token Was Exploited for ~$7.78K.
Token Contract Add: https://bscscan.com/token/0x6bc9b4976ba6f8c9574326375204ee469993d038
Exploit Method: Manipulating $SEAMAN and $GVC token prices via the transfer function.
Hacker triggered small $SEAMAN transfers, causing the contract to swap for $BUSD, then swapped $BUSD for $GVC, inflating $GVC price.
Exploit Txn: https://bscscan.com/tx/0x6f1af27d08b10caa7e96ec3d580bf39e29fd5ece00abda7d8955715403bf34a8
😈On November 29, 2022, the Deployer of BTC-POR Token (@Btop_token) on the BSC chain Executed an Exit Scam for ~$70K
Token Contract: https://bscscan.com/address/0x7e20fec0e64e81e4b9812bd4886cd1fd3ad4df45
Token Contract deployer: https://bscscan.com/address/0x67a935989516ad099a54e8e5ee661a718fce2780
Nov 30
😈On Nov 30, 2023, an ETH address fell victim to a phishing attack where it lost ~118 $WETH (worth ~$242K) to an infamous scammer by the name of ‘angeldrainer’.
Victim Add: 0xC18E70163dfdB13e4057F67fbD1F4Ad9c231653B
Attacker Add: 0x412f10AAd96fD78da6736387e2C84931Ac20313f
Hack Txn: 0x5272405e932b8fdbe201d07c7593c86c7f1cd9d2fbc2f4d8ede1f651ffa98287
Address involved:
0x0000d38a234679F88dd6343d34E26DCB50C30000 (Fake_Phishing228344)
Avoid falling for Phishing Scams by Learning More About Phishing
😈 On Nov 30, 2023, Pink Drainer Scammed a User For ~$83K
PinkDrainer’s notorious acts continue as it drains another wallet (gillynator[.]eth) of ~$83K worth of WBTC.
Txn: https://etherscan.io/tx/0x0dd16020f1e538ea547d3064b6b16581f07042708ef1e6944ddbfb1f661a6565
😈 On November 30, 2021, MonoX, a DeFi protocol, suffered a severe security breach resulting in over $31 million loss, with assets drained from Ethereum and Polygon networks.
The attacker exploited a smart contract vulnerability in the swapping function, allowing them to artificially inflate the price of MONO tokens and exchange them for other assets within the protocol.
MonoX Hack Incident—Nov 30, 2021—Detailed Analysis

