Overview
Table of Contents
On November 10, The Raft protocol (@raft_fi), a decentralized finance (DeFi) platform on the Ethereum blockchain, suffered a major exploit, leading to a loss of ~1577 ETH. The attack revolved around a precision loss issue in the protocol’s smart contracts, which significantly manipulated Raft’s stablecoin, R.
About Raft
Raft, a platform within the cryptocurrency ecosystem, offers a variety of financial services and operates as a decentralized finance (DeFi) platform.
It has also launched its stablecoin—R, which plays a key role in its financial operations and services.
Root Cause of the Exploit
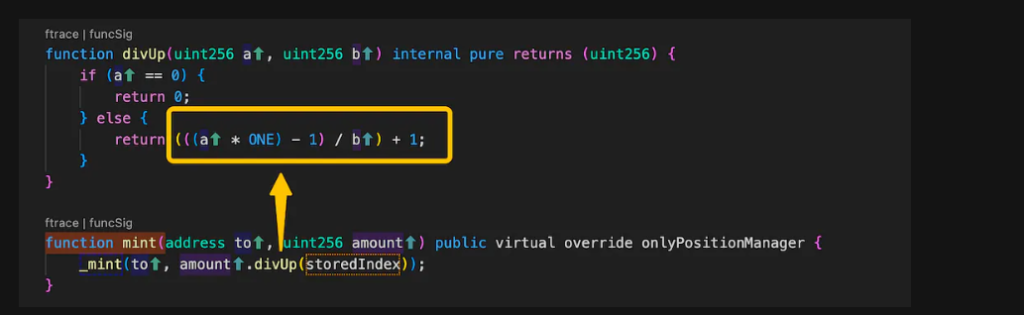
The primary root cause of the hack was a precision calculation issue in the minting process of share tokens. This issue was exploited by the attacker to obtain extra share tokens by manipulating the collateral token’s index rate.
Key elements involved in the hack:
Exploit Transaction: https://etherscan.io/tx/0xfeedbf51b4e2338e38171f6e19501327294ab1907ab44cfd2d7e7336c975ace7
Raft Exploiter: https://etherscan.io/address/0xc1f2b71a502b551a65eee9c96318afdd5fd439fa
Exploited Contract (InterestRatePositionManager): https://etherscan.io/address/0x9ab6b21cdf116f611110b048987e58894786c244
The attacker used a rounding issue in the mint function of the rcbETH-c contract to mint approximately $6.7 million of unbacked R stablecoin.
Detailed Technical Analysis
Exploitation of the Precision Loss Issue
Initial Actions: The attacker targeted the rcbETH-c contract within the Raft ecosystem, a collateralized token, by capitalizing on a rounding issue in its mint function.
Donation and Liquidation: The attacker donated 1,061 cbETH to the InterestRatePositionManager (IRPM) contract and then liquidated their position, a critical step in manipulating the collateral token’s index rate.
https://etherscan.io/tx/0xa1378a4d61e81339daaf2c7c8bb669be42002919f10379c616d0aee34047794e
Outcome: This manipulation led to the minting of approximately $6.7 million in unbacked R stablecoin.
Attack Sequence
Initial Borrowing: Using a flash loan, the attacker borrowed 6,000 cbETH from AAVE.
Transfer and Liquidation: The attacker transferred 6,001 cbETH to the InterestRatePositionManager contract and liquidated a pre-created position.
https://etherscan.io/address/0x011992114806e2c3770df73fa0d19884215db85f#tokentxns
Index Manipulation: The index of the raft collateral indexable token was set to an artificially high value, enabling the minting of 1 wei share with just 1 wei cbETH.
Repeated Minting: This process was repeated sixty times to acquire 60 wei shares, equivalent to 10,050 cbETH.
Redemption: The attacker redeemed 6,003 cbETH with only 90 wei rcbETH-c.
Manipulation Tactics
Strategic Increase: The attacker systematically increased their position by one collateral at a time, each time receiving one share.
https://etherscan.io/tx/0xfeedbf51b4e2338e38171f6e19501327294ab1907ab44cfd2d7e7336c975ace7
Smart Contract Flaw: Typically, such a minting process would result in zero shares due to the small size of the collateral. However, the rounding-up method used in the smart contract granted the attacker one share per transaction.
Accumulation of Shares: This enabled the accumulation of an additional 6,705,028 R tokens.
Unforeseen Outcome for the Attacker
Coding Error: A coding error led to the loss of 1,570 ETH (approximately $3.25 million), which were irreversibly sent to a burn address.
Net Loss: Considering the costs associated with the attack, such as gas fees, the attacker’s net profit turned into a net loss of about 4 ETH.
Swapping of Minted R
Conversion to Other Cryptocurrencies: The minted R was swapped through various pools, including R/sDAI and R/DAI on Balancer, and R/USDC on Uniswap.
Burning of ETH: Due to the attacker’s coding error, 1,570 ETH were burned.
Stolen Fund Details
In the Raft hack incident, a significant coding error by the attacker led to the loss of 1,570 ETH, valued at approximately $3.25 million, which were irreversibly sent to a burn address.
This error, combined with the costs associated with the attack, like gas fees, resulted in the attacker’s net profit turning into a net loss of about 4 ETH.
Additionally, in an attempt to convert the illicit gains, the minted R stablecoin was swapped through various pools, including R/sDAI and R/DAI on Balancer, and R/USDC on Uniswap, but the substantial loss overshadowed this effort due to the burning of 1,570 ETH because of the coding error.
Hack Aftermath
The security breach had immediate and significant consequences, prompting a series of responses to mitigate the impact and prevent further losses:
Stablecoin Devaluation: In the wake of the hack, the R stablecoin experienced a substantial drop in value, losing its peg and falling to approximately $0.70.
Operational Responses:
- Raft immediately paused all minting activities.
- Raft smart contracts were temporarily suspended to control the situation and reduce additional risks.
Recovery and Investigation Efforts:
- Raft has filed a police complaint and is actively working with law enforcement to investigate the incident.
- It collaborated with centralized exchanges and other relevant entities are underway to trace the stolen funds and identify the attacker.
Communication and Planning:
- Raft released official statements to inform its stakeholders about the steps it is planning to take to mitigate the effect of this attack, including a detailed recovery plan aimed at compensating the users affected by the hack.
Audit Status
A third-party smart contract security auditor had audited the exploited smart contracts, but the vulnerabilities leading to this incident were not detected in these audits.
Mitigation Steps
To avoid such incidents in the future, it is crucial to:
- Implement rigorous testing and auditing processes, especially focusing on precision calculation issues in smart contracts.
- Enhance monitoring systems to detect and prevent suspicious activities swiftly.
- Educate users and developers about potential vulnerabilities and best practices in smart contract design.
Conclusion
The Raft hack highlights the critical need for robust security measures in the blockchain space.
The exploitation of a precision calculation issue led to significant financial loss and impacted the stability of the R stablecoin.
This incident underlines the importance of thorough audits and continuous vigilance in smart contract design and operation.
Future efforts should focus on enhancing security protocols and educating the blockchain community to prevent similar occurrences.

