In blockchain technology, security remains paramount, especially considering cryptocurrency transactions rely heavily on digital signatures for their integrity. However, this reliance on digital signatures also introduces vulnerabilities, one of which is known as signature malleability attacks.
Signature malleability attacks present significant threats to the security and operation of smart contracts. This article will explore the intricacies of signature malleability attacks, dissecting their anatomy and providing examples implemented in Solidity.
Additionally, we will discuss strategies to mitigate these vulnerabilities, ensuring the robustness and security of Solidity smart contracts.
Understanding Digital Signatures
Table of Contents
Digital signatures are pivotal in upholding the authenticity and integrity of messages within cryptocurrency transactions. These signatures utilize cryptographic methods and rely on a pair of keys: a private key and its corresponding public key.
When a user initiates a transaction, they utilize their private key to create a distinct signature for the message. This signature is essentially a mathematical representation of the transaction data, encrypted using the private key. It functions as a digital seal, confirming that the transaction originates from the holder of the private key.
The recipient utilizes the public key linked to the sender’s private key to authenticate the signature. By decrypting the signature using the public key, the recipient can verify that the message was genuinely signed by the sender and that the message’s content remained unaltered during transmission.
Understanding Signature Malleability
Signature malleability represents a critical vulnerability in the realm of blockchain technology. It exploits the inherent flexibility of digital signatures, allowing attackers to alter signatures without rendering them invalid. This manipulation opens the door to various malicious activities, including transaction replay attacks and disruptions in the execution of smart contracts.
At the heart of signature malleability is the fact that digital signatures, while robust and secure, still retain a degree of adaptability. When a transaction is signed, the resulting signature is not static but rather subject to certain mathematical operations and encoding schemes. Attackers can exploit this flexibility to subtly modify the signature’s representation without altering its validity.
One of the primary consequences of signature malleability is the potential for transaction replay attacks. In such attacks, attackers intercept legitimate transactions, modify their signatures, and then broadcast them to the network. Since the modified transactions still carry valid signatures, they are accepted by the blockchain network, leading to unintended and potentially harmful outcomes.
Furthermore, signature malleability can also disrupt the execution of smart contracts, which rely heavily on the integrity and predictability of transaction signatures. By tampering with signatures, attackers can manipulate the inputs and outputs of smart contracts, causing them to behave unexpectedly or maliciously.
This can occur due to various factors, such as the structure of the signature scheme or the way signatures are encoded in transactions.
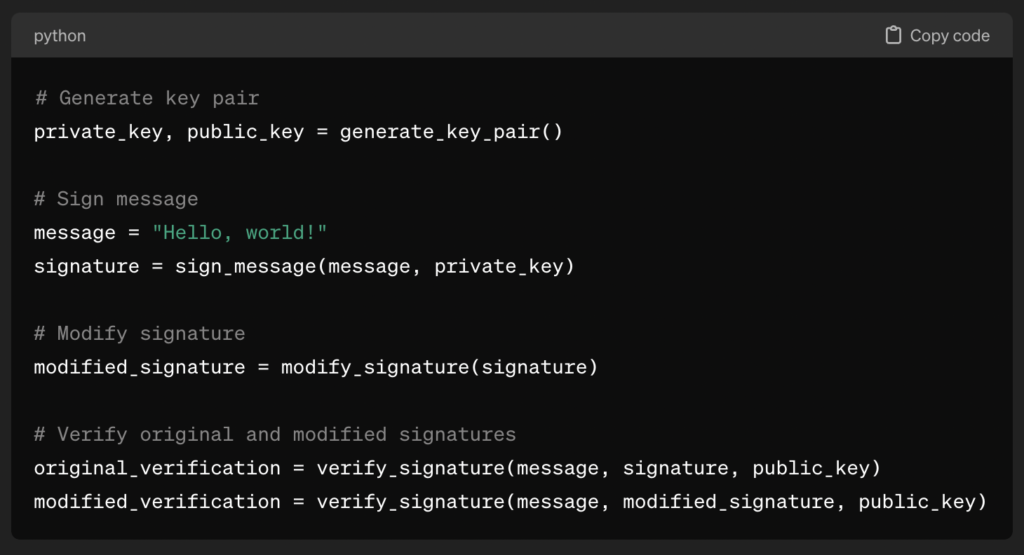
Code Example – Python
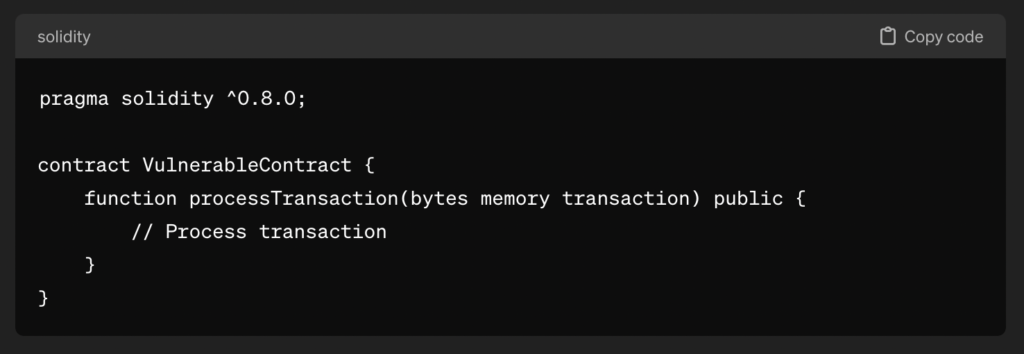
Code Example – Solidity
Anatomy of a Signature Malleability Attack
The anatomy of a signature malleability attack involves several distinct steps that attackers take to exploit vulnerabilities in digital signatures within blockchain transactions. Let’s delve deeper into each component:
Capture the Signature
In the initial stage of the attack, perpetrators intercept legitimate transactions occurring on the blockchain network. These transactions include digital signatures generated by the sender to authenticate and authorize the transfer of assets or execution of smart contracts. Attackers capture these signatures as they traverse the network, either by eavesdropping on communication channels or by directly accessing transaction data stored on the blockchain.
Modify the Signature
Once attackers obtain the signatures, they proceed to modify them using various techniques and manipulation methods. It’s important to note that the goal of this modification is to alter the signature’s representation without rendering it invalid.
Attackers may employ mathematical algorithms, cryptographic exploits, or software vulnerabilities to manipulate the signature’s structure or content subtly. By doing so, they can create a modified version of the signature that still appears valid to the blockchain network and its participants.
Broadcast the Modified Transaction
With the modified signature in hand, attackers then broadcast the tampered transaction back into the blockchain network. This step involves submitting the modified transaction data to nodes within the network for validation and inclusion in the blockchain’s distributed ledger.
By broadcasting the modified transaction, attackers aim to achieve various objectives, such as executing unauthorized transactions, bypassing security controls, or disrupting the normal operation of smart contracts and decentralized applications (DApps).
The outcomes of transmitting an altered transaction can fluctuate based on the attacker’s motives and the particular vulnerabilities targeted. In some cases, the modified transaction may result in financial losses, transaction replays, or unauthorized access to assets. In other instances, it may lead to disruptions in blockchain consensus, delays in transaction processing, or inconsistencies in the ledger state.
Overall, the anatomy of a signature malleability attack underscores the sophisticated tactics employed by attackers to exploit weaknesses in digital signature schemes and blockchain protocols. By understanding these components, blockchain developers and security professionals can better anticipate and mitigate the risks posed by signature malleability attacks, thereby enhancing the security and resilience of decentralized systems.
Types of Signature Malleability Attacks
Signature malleability attacks manifest in various forms, each targeting different signature or transaction structure components. Here, we’ll delve into three prominent types of signature malleability attacks:
Transaction ID Malleability
In this type of attack, attackers focus on modifying the transaction ID (TxID) associated with a transaction. The transaction ID is typically derived from the hash of the transaction data, including inputs, outputs, and signatures.
By altering certain elements of the transaction, such as the signature or sequence numbers, attackers can generate multiple valid transaction IDs for the same transaction. This could cause confusion among network nodes and open up opportunities for double spending, allowing the same funds to be spent multiple times.
ScriptSig Malleability
ScriptSig is a field within a Bitcoin transaction that contains the script required to spend the associated inputs. Attackers can exploit vulnerabilities in the ScriptSig field to modify its contents without invalidating the transaction.
By changing the ScriptSig, the resulting transaction hash (TxHash) is also altered, affecting the transaction’s inclusion in blocks. This manipulation can disrupt the transaction’s confirmation process and potentially delay its execution.
ECDSA Signature Malleability
ECDSA (Elliptic Curve Digital Signature Algorithm) is the cryptographic algorithm used to create digital signatures in Bitcoin and many other blockchain networks. This type of attack exploits weaknesses in the ECDSA algorithm to produce different valid signatures for the same message.
By adjusting certain parameters or introducing specific mathematical transformations, attackers can generate alternative signatures that remain valid but differ from the original signature. Such occurrences can result in discrepancies in transaction verification, potentially undermining the security of the blockchain network.
Each of these signature malleability attacks highlights the nuanced vulnerabilities inherent in blockchain transactions and digital signatures. By understanding the mechanisms behind these attacks, developers and network participants can implement robust countermeasures to mitigate their impact and safeguard the integrity of blockchain systems.
Implications and Risks
Signature malleability attacks introduce significant implications and risks to blockchain systems, jeopardizing their security and functionality. Let’s explore these risks in more detail:
Potential for Transaction Replays and Double Spending
One of the most immediate risks associated with signature malleability attacks is the potential for transaction replays and double-spending.
When attackers manipulate signatures to generate multiple valid transaction IDs for the same transaction, they can exploit this to execute transactions multiple times or spend the same funds in different transactions.
This undermines the fundamental principle of transaction uniqueness and integrity in blockchain networks, leading to inconsistencies in the ledger state and compromising the reliability of transactions.
Challenges in Transaction Verification and Block Validation
Signature malleability attacks can create challenges in the verification and validation of transactions and blocks within the blockchain network.
Modified signatures may result in discrepancies between the expected and actual transaction data, making it difficult for nodes to verify the authenticity and integrity of transactions.
This can lead to delays in transaction processing, increased computational overhead, and potential disruptions in the network’s consensus mechanism. Consequently, the overall efficiency and reliability of the blockchain system could be jeopardized.
Disruption of Smart Contract Execution and Decentralized Applications
Smart contracts and decentralized applications (DApps) rely heavily on secure and predictable transaction execution to operate effectively. Signature malleability attacks can disrupt the execution of smart contracts by introducing unexpected changes to transaction data or signatures. ‘
This can lead to erroneous contract outcomes, unauthorized access to sensitive functions, or manipulation of contract states. As a result, the integrity and reliability of DApps built on the blockchain may be compromised, potentially exposing users to financial losses or security breaches.
Overall, the implications of signature malleability attacks extend beyond individual transactions to impact the broader security and functionality of blockchain systems. It is essential for blockchain developers, network participants, and security experts to remain vigilant and implement robust countermeasures to mitigate these risks and safeguard the integrity of decentralized networks.
Examples of Signature Malleability in Solidity
Here are a few examples of signature malleability vulnerabilities that take place in Solidity smart contracts:
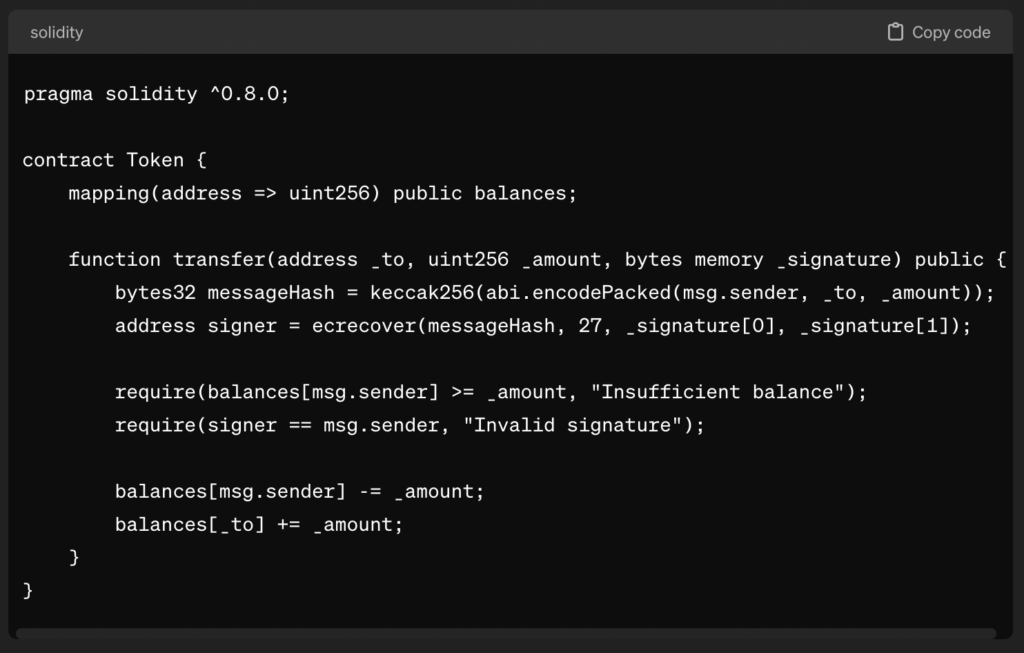
Example 1: Token Transfer Vulnerability
Herein, to manipulate the signature address, an attacker might alter the signature, thereby resulting in the transfer of tokens to unintended recipients.
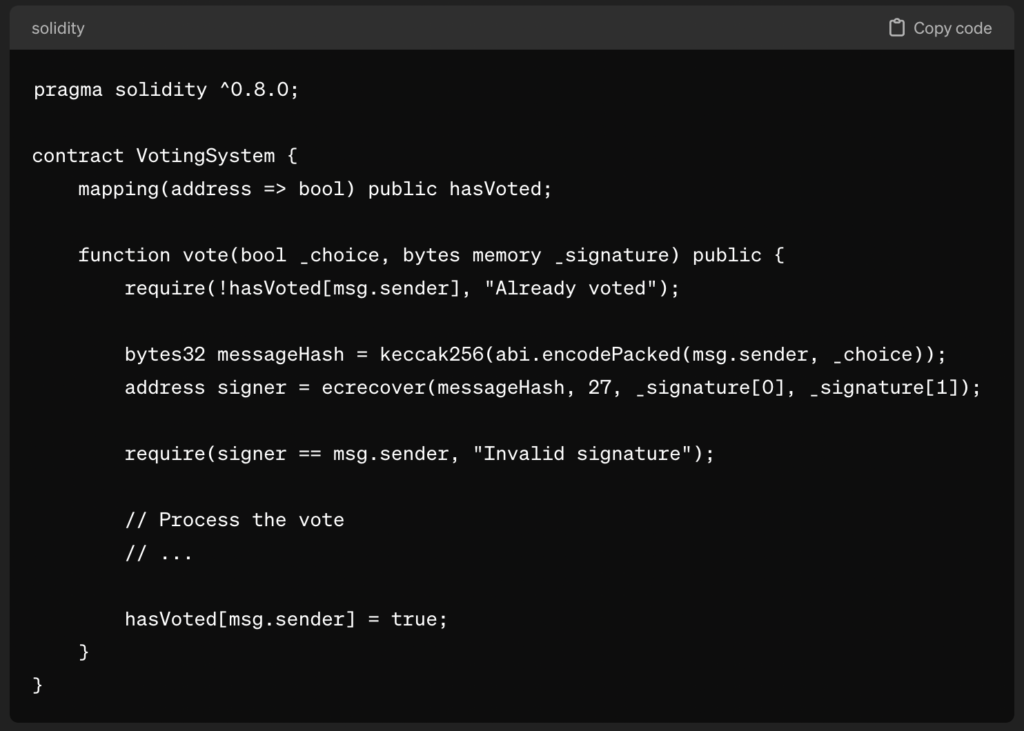
Example 2: Voting System Exploitation
In this case, to cast multiple votes undetected an attacker might manipulate the signature, undermining the integrity of the voting system.
Conclusion
The security of Solidity smart contracts is being hindered by signature malleability attacks. Developers can enhance security by comprehending these attacks and implementing robust measures. Vigilance and proactive security measures are crucial for maintaining the integrity of decentralized systems. By maintaining consistent diligence and adhering to industry best practices, the blockchain ecosystem can flourish in a secure and reliable fashion.

