April 2024
Table of Contents
😈On April 23, 2024, the cross-chain infrastructure Magpie Protocol @magpieprotocol got exploited for ~$129k belonging to 221 wallets.
After the exploit was detected, Magpie Protocol asked its users to revoke approvals for the MagpieRouterV2 contract on multiple chains.
Magpie Contract Addresses at the risk of fund loss and advised to be revoked permission for:
- Ethereum 0xcf32c5bb41f7a302298a2d2072155800871baad3
- Polygon 0xcf32c5bb41f7a302298a2d2072155800871baad3
- BSC 0xcf32c5bb41f7a302298a2d2072155800871baad3
- Avalanche 0x746b0ca3762e229d4dcbd22b4a10906aa788d396
- Arbitrum 0xcf32c5bb41f7a302298a2d2072155800871baad3
- Optimism 0xcf32c5bb41f7a302298a2d2072155800871baad3
- Polygon zkEVM 0x59b37ed62599f3d2f9a593be0153ef08702cb370
- Base 0x6a1431bb23e08e3209dae3130b441863855fc14b
- zkSync 0x5fe556bcf5fc7db6e075ca6f4cd4f8bbee2a3e54
- Blast 0x956df8424b556f0076e8abf5481605f5a791cc7f
- Blast 0x956df8424b556f0076e8abf5481605f5a791cc7f
Update on the Exploit
As per the latest update, the exploited MagpieRouterV2 contract has since been locked to contain the exploit, and revoking the approval to the contract is no longer necessary.
The hack is currently being investigated, and a compensation plan for the affected users is being worked out.
😈On April 9, 2024, XBL token mining app @xblast_app on the Arbitrum chain suffered an exploit of ~23 $ETH ( ~$84.5K).
The exploiter transferred XBL tokens by exploiting the project’s main wallet to their wallet
https://arbiscan.io/address/0xae35602a7bfcf39e7c0d4dd2db04d223ae981de8
How the exploiters carried out the hack is still not clear, but the hack is currently being investigated to answer these questions.
Meanwhile, @xblast_app has acknowledged the hack through a post on its X handle and assured its users that it will deploy a new XBL token to restore liquidity and will award fair compensation to the users affected by this hack.
😈On April 8, 2024, $UPS on BNB Chain lost ~$30K in an exploit. The exploit is currently under investigation, and the analysis report will be available once the investigations are completed.
Hack Txn: https://bscscan.com/tx/0xafea61edb932f816550ef7241e62355d4d50be1bdb7727d69a7a9fb4d510482e
Attacker:
https://bscscan.com/address/0xc4c306c20b4a22f1d261f11c40e88603dd2a2888
Attack contract:
https://bscscan.com/address/0xf5d943805284bfa9c58eb3d777dd5791b5f9da10
Target contract:
https://bscscan.com/address/0x3da4828640ad831f3301a4597821cc3461b06678 (UPS)
Post exploit, the attacker deposited 50 $BNB to Tornado Cash
Top Tornado Cash Alternatives in 2024
😈On April 1, 2024, the permissionless defi protocol @OpenLeverage has been exploited for ~$236K. The attacker was funded by Tornado Cash.
Popular Decentralized Coin Mixers Used by Hackers in 2024
OpenLeverage protocol has acknowledged the breach and has paused the protocol while the hack is being investigated.
Team OpenLeverage has assured its users that any losses suffered in the exploit would be compensated using the accumulated insurance and buyback funds.
Hack Txn: https://bscscan.com/tx/0xf08b6d36dc6f650c030344b6307ae94528f77a01db11d1284ed966e7e44337d3
Addresses Involved in the Exploit:
https://bscscan.com/address/0x5bb5b6d41c3e5e41d9b9ed33d12f1537a1293d5f
https://bscscan.com/address/0xd0c8af170397c04525a02234b65e9a39969f4e93
March 2024
👿On March 26, 2024, Munchables @_munchables_ , a nonfungible token (NFT) game on the @Blast_L2 blockchain suffered an exploit and lost ~$63 million worth of ether (ETH).
A total of 17,413.96 ETH was stolen and transferred to an EOA by a developer who had admin-level access to the @_munchables_ lock contract. Using this privilege, they upgraded the Lock contract, which is deployed to lock tokens for a specified period of time.
Hack Txn: https://blastscan.io/tx/0x9a7e4d16ed15b0367b8ad677eaf1db6a2a54663610696d69e1b4aa1a08f55c95
Hacker’s Address:
https://blastscan.io/address/0x6e8836f050a315611208a5cd7e228701563d09c5
Although @_munchables_ had put appropriate checks in place to ensure that no one could withdraw more than they deposited, but right before upgrading, the attacker assigned himself a deposited balance of 1,000,000 Ether.
Contract Implementation Address for Exploit:
https://blastscan.io/address/0x910fFc04A3006007A453E5dD325BABe1e1fc4511
This huge deposit was made possible by the hacker, who manipulated storage slots manually five days ago on March 21, 2024, and subsequently assigned himself the enormous Ether balance before changing the contract implementation to make it look legit.
Ref Txn: https://blastscan.io/tx/0x3d08f2fcfe51cf5758f4e9ba057c51543b0ff386ba53e0b4f267850871b88170
Once the TVL became sufficiently high, the exploiter withdrew that balance to complete the exploit.
Post-hack, the exploiter’s wallet address transferred $10,700 worth of ETH through the Orbiter Bridge and the Blast ETH back into native ETH.
Later, the exploiter’s wallet sent an additional 1 ETH to a new wallet address.
The Hacker’s North Korean Connection
Crypto sleuth @ZachXBT claimed that the exploit was carried out by a North Korean developer known by the alias “Werewolves0943, hired by the Munchables team. This was found after @ZachXBT
tracked their activity based on their GitHub commit, where they are listed as “Werewolves0493”.
Other suspicious Github Usernames are NelsonMurua913, BrightDragon0719, and Super1114, which recommended each other for the jobs, transferred payments to the two same exchange deposit addresses regularly and funded each other’s wallets several times.
Is it Possible to Undo the Theft?
Although using centralized intervention to undo the effects of the theft is considered against the ethos of decentralized networks, several crypto developers and traders are advocating for a chain rollback to help recover the funds.
For the unversed, a chain rollback in blockchain refers to the reversal of transactional history within a blockchain network. It’s a retroactive alteration of the ledger, where transactions that were previously confirmed and recorded in blocks are invalidated and removed.
Doing a chain rollback can undo the effects of a hack or other malicious activity that resulted in the theft of funds or other assets.
Recovery of Stolen Funds
As per the latest update, @Blast_L2 core contributors intervened in the exploit and have secured $97m in a multisig to avert this colossal theft.
Multisig Address: 0x4D2F75F1cF76C8689b4FDdCF4744A22943c6048C
The funds are being returned without any ransom or bounty, which has come as a sigh of relief for the investors.
@_munchables_ will distribute these funds to the affected users, and details will be made available later.
Team Munchables has also confirmed that the Munchables developer has shared all private keys involved to assist in recovering the user funds, including the key that currently holds $62,535,441.24 USD and the key that holds 73 WETH, along with the owner key, which contains the rest of the funds.
The fund is currently in a multisig wallet 0x4D2F75F1cF76C8689b4FDdCF4744A22943c6048C
Multisig Wallet Owners:
0xFfE8d74881C29A9942C9D7f7F55aa0d8049C304A0xe0C5B8341A0453177F5b0Ec2fcEDc57f6E2112Bc
0x94103f5554D15F95d9c3A8Fa05A9c79c62eDBD6f
👿The burnable meme rune coin Zongzi @ZongZiFa_ was exploited for ~$232k (391.33 WBNB) on March 25, 2024, when the attacker inflated the price of ZongZi to make profits from the invitation rewards.
Exploiter Address: https://bscscan.com/address/0x2c42824ef89d6efa7847d3997266b62599560a26
Hack Txn: https://bscscan.com/tx/0x247f4b3dbde9d8ab95c9766588d80f8dae835129225775ebd05a6dd2c69cd79f
Exploiter Contract: https://bscscan.com/address/0x0bd0d9ba4f52db225b265c3cffa7bc4a418d22a9
Stolen Funds are currently Stored at EOA: 0x20f62b7dd38fbb5c85a6ffe2733f2f12bdb900c9
There has been no official acknowledgment of the exploit from @ZongZiFa_so far.
👿On March 23, 2023, the Curio defi project @curio_invest suffered an attack, resulting in the loss of $16 million worth of assets.
The primary reason for the exploit is a permission access logic vulnerability in the smart contract based on
@MakerDAO, which the attacker exploited to mint an additional 1B $CGT.
Exploiter Address: https://etherscan.io/address/0xdaAa6294C47b5743BDafe0613d1926eE27ae8cf5
Hack Txn: https://etherscan.io/tx/0x4ff4028b03c3df468197358b99f5160e5709e7fce3884cc8ce818856d058e106
Attack contract:
https://etherscan.io/address/0x1e791527aea32cddbd7ceb7f04612db536816545
Target contract:
https://etherscan.io/address/0x579a3244f38112b8aabefce0227555c9b6e7aaf0
Post hack, the exploiter has conducted multiple swaps and transfers to make stolen funds tracing obscure.
The Hack Flow
In the exploit, the attacker used the “cook function” of the attack contract to manipulate the ”IDSChief” and ”IDSPause” contracts to carry out a governance manipulation and mass token minting scheme.
The attacker initially minted 2e18 CGT tokens, which they subsequently locked and used for voting. This allowed the attacker to alter the governance system in their favor.
Once the control was gained, the attacker executed a delegate call to the attack contract Spell using the IDSPause contract.
👿On March 20, 2024, ParaSwap, a middleware for traders and decentralized applications, discovered a critical vulnerability in its Augustus V6 contract.
By the time the vulnerability was discovered and @paraswap paused the V6 API, four of the users (who had approved the vulnerable contract) had already lost ~$ 24k worth of assets.
@paraswap has officially confirmed that the stolen amount has been recovered, and for refunds, impacted users can contact their support team.
Remain user funds have now been moved to a new address, and users have been advised to revoke approvals for the vulnerable contract at address 0x00000000FdAC7708D0D360BDDc1bc7d097F47439
👿On March 20, 2024, Defi Protocol Dolomite @Dolomite_io on the Arbitrum chain has been exploited for ~$1.8m in USDC. The exploit happened to an old Dolomite contract from 2019 on #ethereum.
In an official tweet, Dolomite confirmed that the hack did not impact their current product on Arbitrum.
The exploiter’s wallet was funded by the reltor.eth (tornado cash relayer) from Tornado Cash twelve days ago.
Realtor.eth address: 0x4750BCfcC340AA4B31be7e71fa072716d28c29C5
Immediately after getting funded on March 8, the hacker tried to steal funds from the
@Dolomite_io exchanged its old contract, but the attack could not go through.
Hack Attempt Txn on March 12: https://etherscan.io/tx/0x105e05c8eb7d0f9d8e57e9bce21ba55a22908acb0e7ac84d07b6bb483deb4cd5
However, on March 20, the exploiter managed to steal 541 ETH and 94k DAI from the contract using the ‘submit rings’ method.
Exploit tx:
https://etherscan.io/tx/0x8756db0d30f8c5ba0eee75c4d4337ee03df2b240d5989dee353a937327e642bd
Exploiter address:
https://etherscan.io/address/0x52522d35725836d48e12e64731fa170bcd9423bf
The Hack Aftermath
As per the latest update by @Dolomite_io , they have submitted a transaction that disables the exploited contract from being called.
https://etherscan.io/tx/0x0b4dd1fa64d94322bfec73e59996792f1094e7fe3bdb7981829888bacbfc30ba
As a result, the users who still have not revoked approval to the exploited contract will be safe from further exploits, but they have been urged to revoke approval to the following old contracts.
Contract 1 for Revoking Approval: https://etherscan.io/address/0xE2466deB9536A69BF8131Ecd0c267EE41dd1cdA0
Contract 2 for Revoking Approval: https://etherscan.io/address/0x7f49ac8fdb38d24b686130e22579c7efe69b19c0
The unattended Permit2 ERC20 token approvals can put your crypto assets at grave risk. Read this to know how you can avoid such fund loss:
PERMIT2 ERC-20 Token Approvals and Associated Risks
👿On March 20, 2024, the community-governed L1 blockchain @airdao_io suffered an exploit of ~$880K in which it lost 35.2m AMB tokens and 125.51 ETH from the AMB/ETH Uniswap pool.
Hacker’s Address Which Received Stolen Funds
https://etherscan.io/address/0xFD1754f6Cb9DA53c6F26E3E2eE3DE875CC11C7AA
Exploited Address:
https://etherscan.io/address/0x35e5fd25370b6445a5501956870c93b7ad5ae50e
Hack Txns: https://etherscan.io/tx/0x2e0087b709f158c4272a02bf0038b2770a94d8146b2633d7d1bbb2c452ec91b4
https://etherscan.io/tx/0x12019c14cd4da75f7af310fc1a6ef843ce394c7a414b3c231632d7bde6c124b0
The official reason for the exploit has been stated as the exploiter’s unauthorized access to the LP using social engineering methods and malicious email attachments sent to one of @airdao_io ‘s partners.
The stolen funds are on the move post hack. The attacker has used multiple exchanges including #Binance, #MEXC, #ChangeNOW, #KuCoin, and #BitMart to swap stolen funds to $ETH, which were then deposited to
@MEXC_Official , by routing it through different addresses.
In response to the hack the AirDAO team has initiated contact with various crypto exchanges to track and freeze the stolen funds.
Along with that, the team has also announced a white-hat bounty of 10% for the hacker if he agrees to return the stolen funds. If the hacker fails to comply with the condition of returning funds for a bounty, the case will be reported to the law enforcement authorities for further action.
As per the official statement, in this exploit, the users’ funds on the AirDAO blockchain or exchanges, as well as the AirDAO multisig, remained unaffected.
The detailed hack analysis is currently underway, and its findings will be shared with the community as soon as it is completed.
👿On March 17, 2024, Krishna Okhandiar, the founder of Remilia and Milady, who also goes by the name of Charlotte Fang, was reportedly hacked for millions of dollars worth of crypto assets, including ether and NFTs, which were transferred to a new wallet address.
The said malicious wallet immediately started selling the NFTs and swapping tokens after receiving the stolen NFTs and ether.
The wallet appears to be selling the NFTs (so far, 5 Miladys and 40 Remilios) and swapping tokens to accumulate ETH.
The blockchain data shows that the exploiter sent $1 million in ether to a secondary address, and it still holds nearly $1 million in ether and several other tokens (143 NFTx-staked Miladys and 104 NFTx-staked Remilios) as of writing this.
As per the last update received, all the stolen NFTs have been sold to accumulate 850 ETH ($3 million).
The exact reason for the hack is not known yet, but there is an ownership transfer of Remilia’s treasury to the drainer, which happened before the hack, which raises doubts about this being either a rug pull or an insider’s job.
Tx of Ownership Transfer: https://etherscan.io/tx/0x1178ae5d067eb5e950e5d98fc060081992d7d50366974421212be33951eef186
Stolen assets were moved to the following address:
0x778Be423ef77A20A4493f846BdbcDDfc30252cE9
What is Milady?
Milady, a collection of 10,000 anime profile picture NFTs designed by Charlotte Fang, was launched in the year 2021. In May 2023, Elon Musk (Tesla CEO) publicly endorsed Milady NFTs, which shot up its floor price from 3.8 ETH to 7.8 ETH.
Remilia and Milady Controversy
Since 2022, Okhandiar and the Milady community have been embroiled in legal disputes involving the ownership of project assets, which has negatively impacted Milady’s market value.
In September 2023, Charlotte Fang informed the community through a post on X (formerly Twitter) that a developer in the Milady ecosystem stole around $1 million in generated fees from Remilia Corporation along with the ownership of its three official X accounts—Miladymaker, Remilionaire, and Remiliacorp.
👿On March 14, 2024, a victim on the #ethereum chain fell to a phishing attack when it lost 501 http://ether.fi ETH(~$2 million)
Victim Address: 0x39b28b4ef189ea7ecc961b08f4d3f89f39ad1ccf
Phishing Addresses:
- 0x1AF48964975CCF8fb66140873B3D16237587CBe7 (Fake_Phishing187019)
- 0x0000db5c8B030ae20308ac975898E09741e70000
- 0xf672775e124E66f8cC3FB584ed739120d32bBaad (Fake_Phishing322740)
Phishing Txn: https://etherscan.io/tx/0x16d1e75227e8317999fdbe9cf00817c31fe52898f44c57b8dabac72b674be6e4
👿On March 11, 2024, the DeFi protocol BlastOff (@blastozone) on the@Blast_L2chain was exploited for ~150 ETH.
In the breach, malicious actors entered the future yield minter vault and stole ~$606K worth of crypto assets.
According to the official statement, the affected users in the breach have been duly compensated, and the hacker has been offered a 20% bounty for returning the stolen assets.
The exact cause of the breach is currently being investigated and the protocol is also being reaudited for any vulnerabilities, left undiscovered due to the oversight of earlier blockchain auditors.
What is the Blast?
Blast is an Ethereum layer-2 project that has garnered over $1 billion in capital in the last few months.
@Blast_L2 chain just went live on the mainnet on March 1, 2024. On February 25, a Decentralized betting platform @RiskOnBlast project on the @Blast_L2 ecosystem executed an exit scam and duped its investors out of $1.3M.
👿On Mar 6, 2024, a user on the Ethereum chain lost ~1.1 million $PAAL, worth ~$700K, when it signed a Uniswap Permit2 malicious signature.
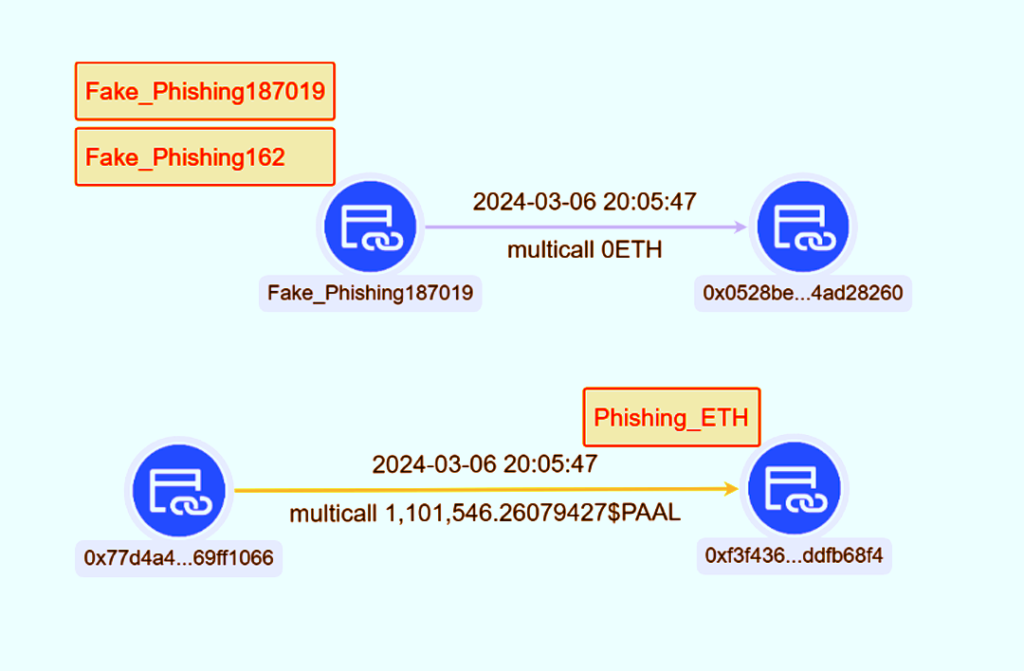
Victim:
0x77d4a46b39f2e206411280a12c9344b769ff1066
Contract Address: 0x0528BEc5405178F112A0cdA7266c92c04Ad28260
Scammers:
- 0xf3f436aa46406eb77ede9abeee410aadddfb68f4
- 0x0000db5c8B030ae20308ac975898E09741e70000 (#Fake_Phishing187019)
Phishing Txn: https://etherscan.io/tx/0x3e47db5a54e132886f648f5c5f17f3ce6ef750455aa911bec5508b7a5b2df33d
Do you know what Permit2 signatures are and what risks are associated with them? Learn about it here: PERMIT2 ERC-20 Token Approvals and Associated Risks
👿On Mar 6, 2024, the TGBS token was exploited for ~$151k by using a flash loan attack.
What Is A Flash Loan Attack, And How To Prevent It?
The hacker’s modus operandi was to repeatedly transfer a small amount of TGBS to themself, which triggered the burning of tokens on the LP.
As a result, the token price fluctuated, which the exploiter manipulated to rake in profits.
The attacker was initially funded by Tornado Cash
.
Attacker:
0xff1db040e4f2a44305e28f8de728dabff58f01e1
Due to the exploit, the TGBS token prices took a steep fall and have yet to regain their lost levels.
Hack Txn: https://bscscan.com/tx/0xa0408770d158af99a10c60474d6433f4c20f3052e54423f4e590321341d4f2a4
Malicious Contract:
0x1a8eb8eca01819b695637c55c1707f9497b51cd9
Victim contract:
0xedecfa18cae067b2489a2287784a543069f950f4 (TGBS)
😈On March 5, 2024, Wootrade’s @_WOOFi WooPPV2 contract was targeted by malicious actors and got away with $8.5M worth of crypto assets on the Arbitrum chain.
The cause of the exploit is a price manipulation attack.
The price calculation in the WooPPV2 contract was flawed. The hacker exploited this flaw by flash-loaning $USDC.e and $Woo to manipulate the price.
This was followed by successive token swaps, which allowed the hacker to rake in profits due to price differences.
The attacker was initially funded by @TornadoCash on $ETH. Post exploit, the attacker has started obfuscating the stolen funds by transferring it to different EOAs and bridging them to other chains.
Exploited Contract: https://arbiscan.io/address/0xeFF23B4bE1091b53205E35f3AfCD9C7182bf3062
Exploiter Address: https://etherscan.io/address/0x9961190B258897BCa7a12B8f37F415E689D281C4
At the time of writing this, the exploiter is still holding ~$730K at this address.
Other Address Receiving Stolen Funds: https://arbiscan.io/address/0xb59d04d9957c9e266dff5c4173d4d2324eb029ad (~$7.4M)
Hack Txn: https://arbiscan.io/tx/0x57e555328b7def90e1fc2a0f7aa6df8d601a8f15803800a5aaf0a20382f21fbd
Hack Response:
On realizing the exploit, @_WOOFi immediately paused the affected contract and asked all its users to revoke approvals to the said contract.
The contract was paused within 13 minutes of the exploit, as per the officially released statement. This prevented the losses from escalating.
The vulnerabilities in the exploited contract are being rectified. WOOFi Swap is expected to be fully functional again within the next two weeks, as per the team @_WOOFi.
The team also confirmed that the current user assets in Earn vaults were not impacted in the exploit.
Oracle price manipulation attacks using flash loans are not new. There have been several crypto exploits in the past which have caused huge losses to the defi projects.
Know about Oracle Price Manipulation attacks and how they are executed in detail here:
What are Oracle Manipulation Attacks in Blockchain?
A detailed insight into flash loan attacks can be found here:
What Is A Flash Loan Attack, And How To Prevent It?
Feb 2024
😈On Feb 29, 2024, Shido blockchain’s Ethereum staking contract has been exploited for ~$35m worth 4,353,473,223.864904 $SHIDO.
This number of SHIDO tokens drained out by the exploiter happens to be around half of the current circulating token supply of the token, which is 9 billion.
Due to the exploit, the SHIDO token prices quickly plummeted by 94% within the first 30 minutes.
How the Hack Was Executed?
The ownership of the contract was changed to a new address (0x1982), which immediately after acquiring the ownership, upgraded the StakingV4Proxy contract using a hidden withdrawToken() function, which was ultimately called to drain out ~4.3B SHIDO tokens.
Exploiter Address: https://etherscan.io/address/0x1982358c84da9d0b4b96fc9e8564d132f7d0041f
Exploited Contract:
https://etherscan.io/address/0xcda954a0c574d8c408f0b8c89a2b367d6a2d3354
Ownership transfer Txn: https://etherscan.io/tx/0xaa76ea503fadddf775b1ef7f195676440fdc3ac46ab642798ab6fa7ae3aafcbe
StakingV4Proxy upgrade by New Owner Txn: https://etherscan.io/tx/0x5d4056cdf40d09a6715fd0f26895d0c60038899b45620f0a6a402c4cd425b672
Draining Funds Txn:
https://etherscan.io/tx/0xed3000ddd8b4feb0902107f97a91815ecee8d7ccb57de9a9dbc50a4c07593cb3
How exactly the hacker was able to change ownership of the contract, raises suspicion about this exploit actually being a rug pull.
The exploiter was funded with 0.78075984 ETH via @AcrossProtocol by address
https://etherscan.io/address/0x147b12c06d9e8e3837280f783fd8070848d4412e which was funded via Layerswap and another address.
AcrossProtocol Funding Txn: https://etherscan.io/tx/0x5b6ee537d4ac6f184758f1f8d1caa0cc2af9268bb71ee9ce82f6b706fbe2883d
Response to the Hack
Shido has officially acknowledged the hack and has informed the community that it has asked the exploiter to accept a bounty and return the stolen funds.
The team Shido also stated that the measures to prevent such exploits have been put in place and assured that all those who have staked SHIDO, will have their tokens returned.
Is this the first Shido Exploit?
On June 23, 2023, Shido was exploited on the BNB chain due to a configuration error, which resulted in a loss of 976 BNB, worth approximately $238,500.
What is Shido?
Shido is a Layer 1 POS blockchain, which has launched its testnet and is planning to launch its mainnet in the coming week, as per the update released on its X handle.
The native SHIDO token is an Ethereum-based ERC-20 token, which users have staked on the project’s DEX, which is offering an annual yield of 8% as per the info available on its website.
😈On Feb 28, 2024, the defi protocol @SenecaUSD was exploited for ~1,900 $ETH worth ~$6.5M. The Attacker was funded by @FixedFloat
Exploited Address: https://etherscan.io/address/0x94641c01a4937f2c8ef930580cf396142a2942dc
Hack Txns:
- https://etherscan.io/tx/0x775cc19c5c29deda98220cf3d244cb2f3f0e63e1c842060abeb26f84df2fb76d
- https://etherscan.io/tx/0x288d02902224e50719b49b2683b9f25e19abc197f4c3e0b3babbf75966130c83
- https://etherscan.io/tx/0xab7f14e2b75e70c8b136c8facb7a94d1947b812749660d0cb961e1a0db7c2f64
- https://etherscan.io/tx/0xa97ee9580ca7845c4e830eb6e00a0ba1a85b71a5ead2fbfafab20327817900cb
- https://etherscan.io/tx/0xb9f650e1dcd9c92983a2ef1a9973628ed9a89060765f2e208527d71ca9e9adad
How the Hack Happened?
The hack happened due to a vulnerability in the smart contract.
Using a lack of input validation, the exploiter called performOperations function externally using a constructed call data. This enabled them to call any contract with arbitrary data.
Using this privilege, the exploiter transferred assets from addresses that had granted approvals to the vulnerable contracts directly to themself by calling the ‘transferfrom’ function.
The Hack Aftermath
Team Seneca has confirmed the hack and has asked its users to revoke the following approvals:
On Ethereum
- PT-ezETH 0x529eBB6D157dFE5AE2AA7199a6f9E0e9830E6Dc1
- apxETH 0xD837321Fc7fabA9af2f37EFFA08d4973A9BaCe34
- PT-weETH 0xBC83F2711D0749D7454e4A9D53d8594DF0377c05
- PT-rsETH 0x65c210c59B43EB68112b7a4f75C8393C36491F06
On Arbitrum
- PT-weETH 0x11446bbb511e4ea8B0622CB7d1437C23C2f3489b
- stEUR 0x7C160FfE3741a28e754E018DCcBD25dB04B313AC
- PT-aUSDC 0x4D7b1A1900b74ea4b843a5747740F483152cbA5C
- wstETH 0x2d99E1116E73110B88C468189aa6AF8Bb4675ec9
- PT-rsETH 0x2216E32006BB80d20f7906b88876964F9AF68aFb
Team Seneca has offered a 20% bounty to the exploiter in return for stolen funds.
The address provided for returning funds: https://etherscan.io/address/0xb7aF0Aa318706D94469d8d851015F9Aa12D9c53a
Team Seneca threatened to pursue legal action against the exploiter in case he failed to return funds.
Return of Funds by the Hacker
As per the latest update (Feb-29-2024 05:11:59 AM +UTC), the hacker has returned $5.3M (1537 ETH) at https://etherscan.io/address/0xb7aF0Aa318706D94469d8d851015F9Aa12D9c53a, which was specified by
@SenecaUSD for receiving stolen funds.
The remaining stolen funds 300 ETH (worth $1.04M) were split equally at the following addresses by the hacker.
- https://etherscan.io/address/0x0c77350c4bde539ffcee261a149dbc6e6afda517
- https://etherscan.io/address/0xa07c64e55f52aaf5c361321cf01b316ecbddb5a9
😈Decentralized betting platform @RiskOnBlast on @Blast_L2 ecosystem executed an exit scam on Feb 25, 2024, when it duped its investors of $1.3M.
The scam was cleverly executed after raising funds on the pretext of an IDO, which was capped at 420 ETH.
The social media handles have been deleted, and the website http://Riskonblast.xyz is not accessible anymore.
The IDO was being promoted for over a week, and users were continuously lured by posting info about partnerships with different crypto exchanges and using scarcity marketing tactics.
The accumulated funds were stolen from over 750 wallets and were bridged to exchanges ChangeNow ($500,000), MEXC ($360,000), and Bybit ($187,000).
RiskOnBlast has recently raised over $1M in a seed funding round around a week ago. It was one of the 47 projects shortlisted (out of 3000 applications) to receive additional funding in Blast’s Big Bang competition.
What is @Blast_L2?
Blast is an Ethereum layer-2 project that has garnered over $1 billion in capital in the last few months, after going live.
This was the first rug pull of the Blast ecosystem. Blast is now being criticized for not taking enough due diligence checks before promoting the RiskOnBlast project through its official X handle, terming its potential as “undeniable.”
😈Defi protocol Blueberry Protocol Foundation @blueberryFDN came under attack on Feb 23, 2024, when multiple lending markets were collectively exploited for ~💰457.68 ETH ($1.34M) (TX Profit) 1 bWETH (Leftover value).
The total gas fee used was 0.093022519261676367 ETH.
Hack Txn:
https://etherscan.io/tx/0xf0464b01d962f714eee9d4392b2494524d0e10ce3eb3723873afd1346b8b06e4
Fortunately, all of the drained funds were front-run by a validator MEV bot @coffeebabe_eth
, and the stolen funds of ~366.65 ETH (excluding the validator fee of ~91.04 ETH) have been returned to a multisig address.
https://etherscan.io/tx/0xc4d45a5143d04d98f11c56f0944ad60426bfbe70b25b5b43a95f0e61a9386a52
The markets affected by the exploit are BTC, OHM, and USDC.
While the hack is being investigated, the protocol has been paused to avoid any further fund loss. The front end was already down as a result of the exploit.
The users were asked to withdraw their funds if they could establish an indirect connection with the exploited contract.
Team @blueberryFDN is also trying to get in touch with the white-hat managing MEV bot @coffeebabe_eth
to return ~91.04 ETH of the validator fee.
What is Coffeebabe.eth?
It is a white-hat hacker known by the pseudonym ‘coffeebabe.eth’, who has thwarted exploits by the crypto hackers on at least one more occasion.
In July 2023, the same white-hat hacker saved Curve protocol @CurveFinance from a ~$5.5M exploit (2800 ETH) by front-running the exploit transaction.
What is front-running in crypto?
Find all the information in an in-depth article here:
Front-Running Attacks in Blockchain: The Complete Guide
Is the front-running attack the same as the sandwich attack?
Find all your answers here: What are Sandwich Attacks in Blockchain?
😈On Feb 22, 2024, two wallets on Ronin Network belonging to Jeff Zirlin @Jihoz_Axie, co-founder of @Ronin_Network, were compromised in what appears to be a private key compromise.
The total loss in the theft was 3088693.24 RON tokens worth around 💰$10 million at the time of the hack.
Jeff clarified through a post from his official X (formerly Twitter) handle that the hack was limited to his personal wallets, and it had no impact on the Ronin bridge or Sky Mavis, which is a blockchain-based video game development studio, also co-founded by Jeff.
- Compromised Wallet 1: 0x121ad060686848b196df8ca5c5e24722efe57115
- Compromised Wallet 2: 0xa09a9b6f90ab23fcdcd6c3d087c1dfb65dddfb05
Hack Txns:
- https://app.roninchain.com/tx/0x6a89b582d37920e7c5ffde327417c2fd06f39c4c4a9aeef6e8bb3a45096f0585 (~11,130 RON)
- https://app.roninchain.com/tx/0xe5fcb3ea3993811a23eb919a2c78806a9af7ea907f0c5abf4d85394aba937003 (~298,000 RON)
- https://app.roninchain.com/tx/0x87841c81acde4828c10e7ce51f033c1bca613a0eaee2000a1ee6df3c3827830e (~830,000 RON)
- https://app.roninchain.com/tx/0x002e0c2213ea72c5ea749f6fa00f74c7bfab792189255fe9046c3aa865a68d1f (~1,949,561 RON)
Total Loss: ~3088693.24 RONS
The stolen funds were first moved to the hacker’s address: 😈0x39f817976c51a91b60145febad81067e69713105 on the Ronin chain and were later bridged to Ethereum and finally to the Tornado Cash.
https://etherscan.io/address/0x64192819ac13ef72bf6b5ae239ac672b43a9af08#tokentxns
Private keys should be kept protected all the time as hackers are always looking to steal them from you through malicious apps, social engineering, phishing, and scamming.
Learn how you can protect your keys from falling into the hands of hackers by reading
Crypto Security Essentials: Secure Encryption Key Management
To get into more technicalities about private and public crypto keys, read
Public and Private Keys: A Must Know In Cryptography!
😈In another crypto security incident, the password manager @LastPass users suffered a breach in which 22 users lost $6.2 million worth of crypto assets. The breach is known to have happened between Feb 19 and 20, 2024.
The stolen funds on EVM have already been swapped and bridged to Bitcoin via THORChain.
The list of affected users and domains can be found at
https://chainabuse.com/report/ff7c260c-88e2-4d1b-a386-efe448b737e2
Is this the first breach at LastPass?
This is the fourth time that LastPass’ security was breached by malicious actors.
In the last breach, which happened in Oct 2023, the losses were to the tune of $4.4 million, and it involved 80 crypto wallets belonging to 25 victims.
Before that, in Dec 2021, @LastPass users faced security incidents related to credential stuffing.
Also, in June 2015, LastPass acknowledged a breach in which email addresses, password reminders, server-per-user salts, and authentication hashes were compromised.
How did the Hack Happen?
In Dec 2022, @LastPass informed its users about unauthorized access to its third-party cloud-based storage service, which was being used by LastPass to store archived backups of production data.
This exploiter had stolen some source code and technical information from LassPass’s development environment in an earlier breach in Aug 2022.
This stolen information was used to target other LastPass employees, and the attacker ended up getting credentials and private keys, which were used in the exploit of Dec 2022.
LassPass, in a post-mortem report for the exploit, had assured its users that the attacker could only get his hands on basic customer account information and a backup of customer vault data from the encrypted storage container, where sensitive information like usernames and passwords, secure notes, and form-filled data was fully encrypted and secured.
Team LastPass was pretty sure that it was nearly impossible for the hacker to crack the master password required for decrypting the encrypted data through a brute force attack or any other password-cracking tool or algorithm.
But, clearly, they were proved wrong by the exploiter on Oct 25, 2023, when they stole away $4.4m of assets.
Why do the LastPass users continue to bear the brunt?
Users, who had ever used @LassPass to save their seed phrases or keys, were strongly urged by security researchers and experts to migrate their crypto assets.
They were also asked to strictly avoid reusing their master passwords on other websites as it might land them in a situation where a threat actor could use dumps of compromised credentials available on the Internet to attempt a breach of their crypto wallets.
It seems some of the LastPass users did not heed this advice, and hence, the breach continues unabated.
What steps should LastPass users take to avoid/mitigate the fund losses?
If you are a @LastPass user, consider taking the following steps urgently:
- Rotate your keys by regenerating the seed phrase using a set of new seed keywords.
- Move your crypto assets to a new address secured with this new seed phrase.
- Do not use your LastPass password/seed phrase ever on any website
- File a report on IC3.gov at https://ic3.gov/Home/ComplaintChoice
😈Cryptocurrency exchange @FixedFloat was exploited for ~$4.85m on #Ethereum and ~$21.1m on BTC on Feb 16 and 17, 2024, respectively.
The stolen assets include 409 BTC and ~1,728 $ETH
For Ethereum Chain
- Victim Address: 0x4E5B2e1dc63F6b91cb6Cd759936495434C7e972F
- Attacker Address: 0x85c4fF99bF0eCb24e02921b0D4b5d336523Fa085
For BTC
- Victim Address: bc1qns9f7yfx3ry9lj6yz7c9er0vwa0ye2eklpzqfw
- Attacker Address: bc1q2skp47p9f5mr4n4m27k66v0l68gh3xdd7ad4e5
What is FixedFloat?
FixedFloat is an automated crypto exchange that uses the Lightning Network for Bitcoin transactions.
The exchange does not require users’ registration or Know Your Customer (KYC) verifications.
Useful Read: Bitcoin’s Lightning Network: An Inkling Shot at Mass Adoption
What Happened to Stolen Funds?
The drainer already transferred most of the stolen $ETH to #eXch on #Ethereum. The stolen BTCs have been moved by the hacker to 3 different addresses.
- Bc1qmrqgrusknj7zzhh5r975a7d6espsukgts805ns (~200 BTC)
- Bc1q04yvaefxyan4fuygsv4nr08pxet8ae426dxxf3 (~170.85 BTC)
- Bc1qp6gjx8par8e83lfqnem5q049x2qfpydfg27tjf (~38.45 BTC)
The Hack
The exact reason for the exploit is being investigated. There has yet to be an official acknowledgment from FixedFloat at the time of writing this.
Initially, Team FixedFloat had ruled out the possibility of the attack when a massive outflow of funds was reported.
They attributed outflow to “minor technical problems” and switched its services to maintenance mode.
At the time of writing this, the official website https://fixedfloat.com still shows an under-maintenance message.
👿On Feb 15, 2024, in two separate incidents, @particle_trade—a permissionless leverage trading protocol on BSC and defi protocol @dualpools , were exploited for ~$139k and ~$41k, respectively.
Initial reports are emerging that the @particle_trade exploit happened because of unchecked user input.
In an officially released statement, @particle_trade confirmed the exploit and stated that the exploit happened to Particle’s previously deprecated NFT contract and that Particle’s current protocol was not impacted in this security incident.
On the other hand, @dualpools has yet to acknowledge the hack officially.
Breakup of Stolen Funds for @dualpools Exploit
- 50074554968631063877 BNB
- 0.171600491149762551 ВТСВ
- 3.992080348227829799 ETH
- 6,378.808120780430189153 ADA
- 911.577466008813446041 BSC-USD
@dualpools Hack Txn: https://bscscan.com/tx/0x90f374ca33fbd5aaa0d01f5fcf5dee4c7af49a98dc56b47459d8b7ad52ef1e93
@dualpools Attacker address: https://bscscan.com/address/0x4645863205b47a0a3344684489e8c446a437d66c
Malicious contract Used for @dualpools Exploit
Exploit: https://bscscan.com/address/0x38721b0d67dfdba1411bb277d95af3d53fa7200e
👿Miner (@minerercx), a token based on an experimental token standard ERC-X, was exploited for ~168.8 ETH (~$463.4k) on Feb 14, 2024.
The attacker stole funds in multiple transactions by exploiting a vulnerability in the #smartcontract.
The ERC-X token prices took a nosedive of -87% as a result of the exploit.
The Vulnerability
The root cause lies with the _update function, which was awarding free tokens every time someone transferred tokens to themselves.
Being aware of this vulnerability, the attacker decided to manipulate this flaw and started sending tokens to himself in multiple transactions.
As soon as the tokens were sent, the _balances[from] function came into play and accurately calculated the attacker’s balance after subtracting the tokens the attacker sent but, due to the flaw, it was immediately overwritten by _balances[to], which erroneously added the sent value to the attacker’s balance, resulting in doubling of tokens in the account.
Attacker Address: 0xbff51c9c3d50d6168dfef72133f5dbda453ebf29
What Miner is Doing About the Exploit?
In an officially released statement, The Miner Team stated that they are re-auditing the vulnerable contract, and after its completion, the contract would be redeployed.
It also informed the community that the remaining liquidity of ~130 ETH will be used as LP for redeployment and that they are planning to take a pre-exploit snapshot of the current holders.
The Miner team has also left an on-chain message for the hacker to negotiate a deal for returning the funds in exchange for 30% (~$120k) of the stolen funds but, the attacker is yet to respond to this message.
On Chain Message: https://etherscan.io/tx/0x27a01149b321eaab0b16d488aefaffa04517a5cf73397b1bbcb8192a4db692ae
😈In an exploit on Feb 13, 2024, the crypto casino platform @Duelbits suffered a massive exploit in which it lost ~$4.6m worth of crypto assets.
The hack has happened in @Duelbits wallets on $ETH and $BNB chains.
There has been no official statement from Duelbits on the hack so far, but the most likely reason behind the exploit is speculated to be a private key compromise or the loss of wallet access control.
The stolen funds comprise, but not limited to, $USDT, $APE, and $SHIB tokens.
The exploiter has managed to bridge stolen assets from BNB chain to Ethereum after swapping $USDT, $APE, and $SHIB to $ETH.
This was obviously an attempt to obfuscate the stolen funds trail. While swapping BNB for BSC-USD the exploiter came across a situation where the bridging to the Ethereum chain could not happen due to the lack of gas fees.
To overcome this, the hacker used the FixedFloat service, which allows quick cryptocurrency exchanges.
Attacker Address: https://etherscan.io/address/0x3933924faf011ae8d24e44bee450b3d78e46a666
Exploit Txn:
https://etherscan.io/tx/0x3bf414c5a62704cc917242336394eeeed15a7e1a50e857c15e611dab92999aa4
Learn how to keep your private keys safe here: Compromised Private Keys: Threats and Remedies
👿Crypto gaming and NFT platform PlayDapp, which collectively lost ~$290M worth of PLA tokens in two separate attacks—on Feb 9 and Feb 12, 2024—has informed the community that it has paused its PLA smart contract to conduct a migration based on the snapshot.
Address: https://etherscan.io/address/0xD151050d43c28690766f50Ce9ea8686c5D243a40
What has Transpired So Far?
In two separate exploits on Feb 9 and again on Feb 12, the exploiter managed to mint 200 million PLA tokens (worth ~$36.5 million) and 1.79 billion PLA tokens (worth $253.9 million), respectively.
As per the initial analysis, an unauthorized wallet possibly used a private key compromise to mint ~1.83 Billion PLA tokens in the two attacks.
However, PlayDapp tried contacting the exploiter through an on-chain transaction, offering a $1 million bounty in return for stolen funds.
Instead of responding to the offer, the hacker decided to mint 1.59 billion more PLA tokens valued at $253.9 million on Feb. 12 and simultaneously started laundering the funds through crypto exchanges.
Since the total circulating supply of PLA tokens was a mere 577 million before the breach, the exploiter struggled to sell the 1.8 billion newly minted tokens at anything close to their market value before the hacks.
The Hack Aftermath
The prices of the PLA token took a steep fall in response to the exploit.
In an effort to contain the exploit and stop the hacker from laundering the stolen funds, PlayDapp contacted numerous central exchanges and asked them to suspend deposits and withdrawals of PLA tokens.
It is also chalking out a strategy with blockchain forensic firms and law enforcement agencies to track the stolen funds. It is also holding discussions with the exchanges to launch airdrops for the migration of stolen funds.
The actual reason behind the intrusion is being investigated and will be known after the completion of the investigation.
Jan 2024
😈Defi protocol @MIM_Spell was exploited on Jan 30, 2024, for over $6.5m, in what appears to be a result of an exploitation of a rounding error.
In total, @MIM_Spell lost 2.74K $ETH in the attack which was initially funded with 1 $ETH from #TornadoCash.
Hack Txn: https://etherscan.io/tx/0x26a83db7e28838dd9fee6fb7314ae58dcc6aee9a20bf224c386ff5e80f7e4cf2
Attacker: https://etherscan.io/address/0x87f585809ce79ae39a5fa0c7c96d0d159eb678c9
As per the preliminary findings, the attacker attacked specific Cauldrons V3 & V4, which resulted in unauthorized MIM borrowing.
To minimize any further losses, @MIM_Spell set borrowing limits to zero for the attacked V3 and V4 cauldrons.
Team @MIM_Spell acknowledged the hack and confirmed that the issue has now been fully contained.
@MIM_Spell also confirmed that no user collateral is at risk. The hack is currently being investigated thoroughly, and the report will be published soon.
Team @MIM_Spell has also left an on-chain message to the attacker in an attempt to persuade him to return funds and accept some part of the stolen funds as a bug bounty.
On-Chain Message Txn: https://etherscan.io/tx/0xa1f8e3c30917f33956ef0a96417987a07a70509a2e48b6426b65906462faad6b
As of writing this, the hacker has yet to respond to this offer.
Immediately after the hack, the MIM initially fell to $0.77, only to later recover and reach $0.98.
The recovery could be attributed to @MIM_Spell DAO treasury’s buying back of MIM from the market to burn them.
Rounding error or precision loss vulnerability can cause grave losses in well-orchestrated attacks by the crypto exploiters. Learn how you can fix these vulnerabilities in your project here:
Precision Loss Vulnerability in Solidity: A Deep Technical Dive
😈In a massive phishing attack, a victim on #ethereum lost $1.1M worth of $LINK on Jan 25, 2024.
After the victim signed a malicious swap transaction, the victim suffered a sandwich attack during the swap (without slippage protection) of 58.2K $LINK (worth ~$813K) for 222.4 $ETH (worth ~$494K). This led to a loss of $300K.
In this attack, the MEV bot received a bribe of 135.56 ETH (equivalent to $301K).
Hack Txns:
- https://etherscan.io/tx/0x16ac84571af9a83017ca53cae15ccd090434013c7d14bae3c7d04b17484627e6
- https://etherscan.io/tx/0x827cb7d0b74b8c8d0d84b14a5d2b7b58c95a606e7b9037a4ca6f0c0286c79d64
Do you know what are Sandwich Attacks in Blockchain?
Find all your answers here: What are Sandwich Attacks in Blockchain?
😈On Jan 25, 2024, a victim on Ethereum lost ~$164k worth of PudgyPenguins NFTs to a phishing attack.
The hack’s cause was the victim’s signing of a malicious Blur Bulk signature.
This phishing exploit method is not new and is based on a malicious Blur bulk listing signature used by scammers to steal NFTs with just one message signature.
What is Blur Bulk Listing Message Phishing
Usually, NFT owners are tricked by a malicious website to sign a listing for selling their NFTs for 0 ETH.
Due to Blur’s unreadable bulk listing messages, it gets difficult for NFT owners to identify a malicious request from the marketplace, and they end up losing their NFTs to hackers.
To avoid falling for such traps, always check the source of the signature request before signing any approval for NFT transfers.
If the source doesn’t show http://blur.io, do not proceed with the signing request. Never sign any Blur bulk listing signature that is not from the official website i.e., http://blur.io
Hack Txn: https://etherscan.io/tx/0x2c837d3abc13ab662c84d518b129d045417d2e55af54748d932d7607f5cec10a
Victim:
https://etherscan.io/address/0x57179b08bd29b441da18ba84c526c3f0be23dacc
Scammer:
https://etherscan.io/address/0x9e09dc51ad3b33464093f5505b81bc96e2eccde0
😈The phishing scams continue to bleed the crypto investors. On Jan 23, 2024, the address 0xf8ebfa lost ~$1.3m worth of stablecoins on multiple chains.
- 154.16K $USDC on #Ethereum
- 300.34K $USDT on #Arbitrum
- 834.24K $USDT on #BNBChain
Hack Txn: https://bscscan.com/tx/0x400b7583b892024db19940e2e74a26b22b188196e3c6cbff4e6663295a50daed
Victim: 0xf8ebfacb4768b4152dd38416c1ea5fd143f5f807
Scammer: 0xabd75cd4117fa7bfaa096f581abcec69b8d68f50
The phishing happened when the victim signed increaseAllowance transaction and multiple ERC20 Permit signatures/
The addresses used for receiving stolen tokens are the temporary addresses pre-computed by CREATE2.
😈DeFi @ConcentricFi or Arbitrum chain suffered an exploit on Jan 22, 2024, and has reportedly lost ~$1.72M worth of crypto assets (715 $ETH).
The exploiters got unauthorized access to the protocol through a targeted social engineering attack on one of the team members holding the deployer wallet.
Although the smart contracts of the vault were duly audited before deployment but these contracts were upgradable, and the attackers manipulated this vulnerability to upgrade the vaults and minted LP tokens to drain the vault.
The Attack Methodology
The attacker got hold of the private key through social engineering attacks on one of the team members with access to the deployer wallet.
As the vaults were upgradable, the attacker updated the implementation contract of the CONE-1 proxy contract from the original ConeCamelotVault contract to the attacker-controlled contract.
To mint LP tokens, the attacker added admin to the adminMint() function and subsequently drained the vaults.
Attacker Address 1: 0x105f52fcC329cEF4CBe25BC946f8a3738414E4A1.
Attacker Address 2: 0xc62A25462A61f02EBAB35Cd39C5E9651426e760b
The address which created 3 upgraded ConeCamelotVault contracts is
0x5A58D1a81c73Dc5f1d56bA41e413Ee5288c65d7F.
Addresses Holding Stolen Funds:
- 0x17865c33e40814d691663bc292b2f77000f94c34 — (115.749555148545411 ETH)
- 0x1F14E38666cDd8e8975f9acC09e24E9a28fbC42d — (300 ETH)
- 0xFD681A9aA555391Ef772C53144db8404AEC76030 — (300 ETH)
Address 0x1F14E38666cDd8e8975f9acC09e24E9a28fbC42d, holding stolen funds, is labeled as OKX Exploiter 2 on #Etherscan
Other addresses holding funds: 0xFD681A9aA555391Ef772C53144db8404AEC76030 and 0x17865c33e40814d691663bc292b2f77000f94c34 both have previously received funds from OKX Exploiter 2 on Dec 13, 2023, as checked on #Etherscan.
Precautionary Measures
To keep user funds safe, users are advised to revoke all approvals for the following addresses on $ARB:
- 0x39c1bc90ba23d4d95eafa9335ceb83e0826e7ea7
- 0x0f9da8eaf006079d772955644bac36f17934b36e
- 0x319e70fc896a138619617b7d06f0dfcd2e554808
- 0x6277f4f9f55bfc331bcbe8db2f221ae186489915
- 0x7f8863c2086fde3d199f5dd27d555574d1bb7228
Actions Taken:
Post exploit Team @ConcentricFi:
- Initiated a detailed investigation to identify the culprits behind the attack and promised to release an in-depth post-mortem report on the completion of the investigation.
- Started working towards implementing security measures to prevent future breaches.
- Finding all possible options to mitigate the losses and safeguard the community’s interests.
😈On Jan 22, 2024, the @GAMEEToken on Polygon was exploited for $7M (600M $GMEE tokens).
The primary reason for the hack was a lack of access control, which led to the compromise of the $GMEE deployer address.
In the attack, the attacker withdrew a significant amount $GMEE from Animoca.
The stolen funds were later swapped to $MATIC. The attacker later bridged some of the funds to $ETH chain.
Due to the exchange of stolen funds by the exploiter at various DEX, the $GMEE token price across various exchanges has taken a hit.
In an official communication, the team @GAMEEToken confirmed that the exploit has only affected proprietary team token reserves, and no community-owned assets have been impacted in the attack.
Their initial investigation revealed that the compromise of the Polygon $GMEE deployer address might have happened via unauthorized GitLab access.
Attacker Address: https://polygonscan.com/address/0x16afa519642c932b073cd21d82162bdc7a471b86
GAMEE Token Contract Address: https://polygonscan.com/address/0xcf32822ff397ef82425153a9dcb726e5ff61dca7
The Hack Aftermath
Following are the actions taken by the team @GAMEEToken
- The compromised deployer address was replaced with a new secure address
- Liquidity provisioning was temporarily closed on all DEXs
- All centralized exchanges with $GMEE markets were contacted to disable deposits temporarily and freeze tokens linked to the hack
- A detailed audit of all existing procedures and contracts has been initiated.
- Help from law enforcement agencies is being pursued to take legal action against the culprits and recover stolen funds.
Access control vulnerabilities can seriously impact a project’s stability, security, and integrity. Learn how such vulnerabilities can be mitigated at:
Access Control Vulnerabilities in Solidity Smart Contracts
😈On Jan 21, 2024, a phishing attack on #ethereum cost a victim ~$4.2M worth of aEthWETH and aEthUNI.
The loss happened due to the victim’s signing of multiple ERC20 Permit signatures.
Attack Txn: https://etherscan.io/tx/0x93a0ce0711edaf7664c26b3654095f1052010bb7da62c135b6ef0c425c0c2f09
Victim:
0x1749ad951fb612b42dc105944da86c362a783487
Attackers:
0x0000372B2BC916D6c904495e53533Ae90740F688
0xf672775e124E66f8cC3FB584ed739120d32bBaad
The addresses created to transfer these tokens are the temp addresses pre-computed by CREATE2.
CREATE2 is now increasingly being used by scammers to carry out phishing attacks.
To Know What is CREATE2 and How it is Used by Scammers for Phishing Read
Explained: Create2 Opcode in Solidity
😈DeFi protocol @BasketDAOOrg was hacked on Jan 17, 2024, for over $107K due to a vulnerability in its smart contract.
The attack was an arbitrary low-level call exploit that happened due to a bug in the contract’s approval process.
In March 2022, the same contract, along with another contract (0x01A903c12A2Dd87A5410173A29543504DF8bD14B), were found to have similar vulnerabilities, which had caused fund loss.
Hack Txn: https://etherscan.io/tx/0x97201900198d0054a2f7a914f5625591feb6a18e7fc6bb4f0c964b967a6c15f6
Hacked Contract: https://etherscan.io/address/0x4622aff8e521a444c9301da0efd05f6b482221b8
Attacker Add: https://etherscan.io/address/0x63136677355840F26c0695dD6DE5C9E4f514f8e8
😈On Jan 17, 2024, a victim on the Ethereum chain lost $149,435 worth of tokens due to signing malicious phishing signatures on a phishing site.
Hack Txn:
Jan-17-2024 09:42:35 PM +UTC
https://etherscan.io/tx/0x98480bb8e5c212b4f408a3f74fbb94dc60529a97d14fe2356372b170ab320773
Victim Add:
0x373adc79ff63d5076d0685ca35031339d4e0da82
Scammer Add 1:
0x4f4314e1e81650497d46e5b2179f5f3430902011
Scammer Add 2: 0x9fA7bB759641FCd37fe4aE41f725e0f653f2C726 (PinkDrainer: Wallet 2)
😈In another phishing incident on Jan 17, 2024, a victim on the Ethereum chain lost $178,030 worth ~6667 Auction tokens to the phishing maneuvers of the scammer.
Hack Txn: Jan-17-2024 01:37:59 PM +UTC
https://etherscan.io/tx/0x8f6cb49baa8886d1d1fef5146afbccdb6075b3f0cc0fd3a9cf604fb9b9f0b94f
Victim Add: 0xefbf320e8bc2e0a051db24f73b6f5756deeddcda
Scammer Add 1: 0xa2f10ccba0f5950eea846be601d7e0a627144b4e
Scammer Add 2: 0xa3aa460c12713a000a33893b024d95db80945a2f (Fake_Phishing270927)
😈On Jan 16, 2024, an address lost $229,553 worth of WBTC and ETH after signing malicious phishing signatures on a phishing website.
Hack Txn:
https://etherscan.io/tx/0x6d34b0f63da4f7402c467a657eb4c12894d1dfaa3b0095992d19eb64de2282fc
Victim: 0x23f8c7db7a1b656652e9726ab264c5b181418b9f
Scammer: 0x145f2b66b7bf5ad64b4ae21d1c77a20c61bf45a9
The victim signed three ERC20 Permit signatures, and these token spenders are the temp address pre-computed by CREATE2.
CREATE2, although better than the previous CREATE, is now increasingly being used by scammers to carry out phishing attacks.
Explained: Create2 Opcode in Solidity
😈DeFi protocol Socket @SocketDotTech on Ethereum has been exploited for ~$3.3M on Jan 16, 2024, due to a bad route added 3 days ago.
Added Route tx: https://etherscan.io/tx/0x1df44e224c7a715da25fa33dcad2ca3a930d1a4dafd263e61c07b52673d505f4
This has affected users who had given infinite approval to the SocketGateway contract https://etherscan.io/address/0x3a23f943181408eac424116af7b7790c94cb97a5
The attacker took advantage of the incomplete user input validation to steal funds from the users who had approved the contract.
The Input Validation Vulnerability
The attack was carried out by making an unsafe call in the performAction function.
Due to an input validation vulnerability in the contract, when transferring 0 WETH, the caller can specify other functions in the call and still pass the balance check validation.
Manipulating this flaw, the attacker constructed calldata to call transferfrom() of arbitrary tokens and transferred tokens approved to the contract by other users.
Attacker Add: https://etherscan.io/address/0x50df5a2217588772471b84adbbe4194a2ed39066
Hack Txn: https://etherscan.io/tx/0x591d054a9db63f0976e533f447df482bed5f24d7429646570b2108a67e24ce54
To contain the hack, the exploited contract was paused, and Socket asked its users to revoke all approvals to avoid loss of funds.
The bad route was also removed by Socket.
Disable route tx:
https://etherscan.io/tx/0xac75adcc1cb3fef158c4f200c48fcbcbb9b6ce3250bdf3751d6231d41a9e604b
The Hack Aftermath
As of writing this, @SocketDotTech has informed the community that they have bridged on @BungeeExchange , and most of their partner frontends have been resumed.
They also stated that they are conducting a detailed analysis of the exploit, the report of which would be shared later with the community.
😈Defi WiseLending protocol @Wise_Lending on Rthereum came under a price manipulation attack on Jan 12, 2024, when the exploiter manipulated a rounding error and caused losses of ~$460K (~178ETH)
The hacker knew that WiseLending uses rounding up when calculating shares withdrawals.
The attacker repeatedly called the withdraw function with a unit amount to cause a mismatch between the protocol token balance and shares. This led to the price manipulation.
The stolen funds are currently held at 0x592856d68B3FEE1D2dAa34CdC9851f3477C52530
Manipulated Contract: https://etherscan.io/address/0xb90cf1d740b206b6d80854bc525e609dc42b45dc
Hack Txn: https://etherscan.io/tx/0x04e16a79ff928db2fa88619cdd045cdfc7979a61d836c9c9e585b3d6f6d8bc31
Rounding errors in smart contracts can lead to severe security vulnerabilities. To know how these can be mitigated, read:
How to Bypass the Integer Division Error in Smart Contracts?
Precision Loss Vulnerability in Solidity: A Deep Technical Dive
😈An address on the #Avalache chain lost 9.41 $BTC (~$433K) in a phishing attack on Jan 12, 2024. The victim transferred the stolen amount in two transfers in a single transaction.
Read: The Beginner’s Guide to Phishing Attacks
Hack Txn: https://subnets.avax.network/c-chain/tx/0xe00e4c8c11cff74c6a2296ef4e20cd0bc9811365022460f7207197923c4f51ed
Victim: 0xda60167db93bfd982204a55afb7321a76afc419b
Contract Add: 0xf455878e14d435e23dd8a2000c8fac3fca2f33d5
Scammer Add 1: 0xa3aa460C12713A000a33893b024D95db80945a2F (1.41147824 aAvaBTC.b)
Scammer Add 2: 0x7666a59f3A38934cb1262d22Fac52A67fda4B123 (7.99837663 aAvaBTC.b)
👿On Jan 11, 2024, a victim on the Ethereum chain was scammed for over ~$772K worth of stETH when it signed a malicious ERC20 Permit signature.
An ERC20 token approval given on a scam website can be activated by the hacker to carry out illegitimate transfers from an address without the knowledge of the owner.
Victim: 0x551b30bc933e26e098bd2e68d436c24ed39b7312
Scammer: 0x1A42605D92C210E4bE47A6363046c591659ab444 (Fake_Phishing269883)
Hack Txn: https://etherscan.io/tx/0xa653ede5787d5ee4b869d01643c3178b38d470445cd2078c23a5f2cfed4ff37b
To stay protected from ERC20 token approval phishing scams, always:
- Set the token transfer limits for token approvals to minimal.
- Ensure that the website authorized for token approvals is genuine and trustworthy.
- Bookmark the URL of the website or access it from the official channels.
- Look for the approvals which are no longer in use and revoke them ASAP.
- Stay updated with the news of exploits in the crypto world.
Revoke the approval without losing time to protect your funds from being drained by an exploiter of the dApp approved previously.
ERC20 Permit2 approval and the associated risks
😈A victim on #Ethereum fell victim to a zero-address transfer scam on Jan 10, 2024, when it accidentally sent 960,000 USDT to the scam address instead of the address it meant to transfer.
Zero transfer scams have become quite common in the crypto world. They are increasingly getting popular with scammers as it requires minimal effort on the scammer’s part to steal money from novice #cryptoinvestors.
Victim: 0x3dFf6f65Fd3354D2f98e065B814456Dc54435F0a
Intended Address: 0x9462B598aa7e45e6C2df22c35337Be248Df98CD6
Phishing Address: 0x946c8e51d95a1f1643c3617363aee83439f98cd6
What is a Zero Transfer Scam, and how do you avoid it?
😈On Jan 10, 2023, the BRA token on #BSC was exploited for $225,000 when it lost 819 WBNB due to a smart contract vulnerability.
The Vulnerability
Due to a logic vulnerability in the smart contract, every time the transfer function was invoked, the sender and recipient got twice the rewards if they were a pair.
The Attack Flow
>>Step 1
The attacker took a flash loan of 1,400 WBNB and exchanged 1,000 WBNB for 10.5K BRA tokens, which they later transferred to the Pancakeswap pair.
>>Step 2
Using the skim() function, the attacker invoked the BRA contract’s transfer function to receive rewards.
>>Step 3
The ‘skim()’ was set to work as a recovery mechanism whenever the number of tokens supplied to a pair exceeded the two uint112 storage spaces for reserves.
The attacker manipulated this and provided pair as the recipient address for receiving the BRA tokens.
Due to the vulnerability in the smart contract, the number of BRA tokens after every single skim became twice the intended amount.
The hacker repeatedly called skim() around 100 times to significantly increase the contract pair’s BRA balance.
>>Step 4
The attacker then returned 1.675K WBNB tokens and repaid the 1.4K WBNB token flash loan.
A profit of 675 WBNB was generated in this process, which the hacker sent to their address.
The whole sequence of attack was repeated one more time, and this time, the profit gained by the attacker was 144 WBNB.
Technical Info:
Attack Transaction: https://bscscan.com/tx/0x6759db55a4edec4f6bedb5691fc42cf024be3a1a534ddcc7edd471ef205d4047
Attacker’s Address:
- https://bscscan.com/address/0x67a909f2953fb1138bea4b60894b51291d2d0795
- https://bscscan.com/address/0xE2Ba15be8C6Fb0d7C1F7bEA9106eb8232248FB8B
BRA Token Code: https://bscscan.com/token/0x449fea37d339a11efe1b181e5d5462464bba3752#code
Pancake Swap Contract:
https://bscscan.com/address/0x8f4ba1832611f0c364de7114bbff92ba676adf0e
How to Avoid Such Attacks?
This attack would not have happened if the smart contract auditors had examined the contract for logical issues. By conducting thorough testing and reviews of the smart contract code, the auditors can discover and fix potential vulnerabilities before deployment.
BRA Token Detailed Hack Analysis
😈MangoFarmSOL, a farming protocol on Solana, which promised unprecedented yield in the $SOL space to its investors, stole away ~$2M of its investors’ wealth on Jan 7, 2024, in a well-orchestrated exit scam.
It had announced its MANGO token airdrop on Jan. 10, and to participate in the airdrop, users had to deposit their Solana SOL tokens in the protocol.
The TellTale Signs of the Scam
“Foobar,” a pseudonymous developer recently appointed as MangoFarmSOL’s security auditor, had warned users about MangoFarmSOL’s compromised front end on Jan 6 through a post on X (formerly Twitter).
He also predicted that the protocol could be a potential rug pull.
The Disappearing Act
The official website of MangoFarmSOL is now being flagged as a deceptive website. Their profile on X no longer exists, and the Telegram channel (with 1000 existing members) is not accepting new members anymore.
Is there Another Scam in Waiting?
There have been reports about screenshots being circulated on social media in which the developer of the now-scam project @MangoFarmSOL is shown claiming that he was forced to create Ponzi schemes and that he is involved with another project, BananaMiner.
Representatives from BananaMiner have refuted all such allegations and have categorically denied any connection to MangoFarmSOL, except that they were approached for collaboration by them.
MangoFarmSOL must not be confused with another Solana-based project, Mango Markets, which was exploited in October 2022 for over $100 million.
The Conclusion
The Solana ecosystem has been increasingly targeted by scammers using wallet drainers.
The seriousness of the security threat for Solana-based projects can be gauged by the fact that the cybercriminals have been selling Solana drainer kits since December, and one of the large communities for SOL’s wallet drainer kit maintained by these cybercriminals has over 6k members.
Beware of the scammers who lure novice #cryptoinvestors to invest in fake projects and tokens.
Equip yourself with knowledge on detecting such scams and avoid falling for them.
You can get a great deal of knowledge about identifying such scams here:
Crypto & Defi Rug Pull: How to Spot?
World of Rising DeFi Scams: 5 Types of Scams that are Deceiving Investors
😈Narwhal project on #BSC suffered an exploit on Jan 5 and Jan 6, 2024, for a total of ~$1.5M worth of NRW tokens ($970k on Jan 6 and $500k on Jan 5).
On Jan 7, @Narwhal_fyi confirmed in an official tweet that it was exploited and is in the process of rebuilding the liquidity pool in the next 3 days.
It also stated that they are working on a new platform with enhanced security to avoid such exploits in the future.
The stolen NRW was later swapped for ETH and bridged to the Ethereum Network.
The address 0x9481b7c8f83A7BB3E8e3648b453d6Eb59dFFcC30 deposited 375 ETH into TornadoCash and also received ETH from 0xEa55BAEF29dc70799fAec4E2896b4D16A750E568
At the time of reporting, ~$1M out of the stolen ~$1.5M has already been deposited into Tornado Cash
by the attacker.
The remaining Stolen funds are currently at:
- ETH: 0xe07bCffac8cEC86886B49b509A4924182D2596d3 (~80 ETH)
- ETH:: 0x51eF9B64e5Bc4A23C522ECE8769De87b022d3c41 (~100.3 ETH)
On Jan 6, the attacker called the withdraw() function with the signer info. In the decompiled contract, it has been found that the signer’s address was actually set by the contract owner, and it is possible that the signer’s private key was either compromised or the information was forged.
Exploited Contract: 0x8A2DF808CCb0DB866C5C152412D1718929143f53
The Alternate Theory
There are speculations that what seems to be an exploit by a malicious hacker could possibly be a cleverly executed exit scam in the shroud of an exploit.
To support the theory, the on-chain analysts have presented the following:
The NRW token price shows two major drops—Jan 5 and Jan 7.
The drop on Jan 5 is likely caused by the large transfer of NRW tokens to an EOA 0xEa55BAEF29dc70799fAec4E2896b4D16A750E568 from multiple wallets.
Suspiciously, all these wallets received funding from the same address: 0x28B38A8B0b5AbEcE315a5064495056ad158DDDfF
The 0x28B38 address itself was initially funded by 0xfc8Cd26F86E6169e95A0256004B5c8FD1a6EFdDF, which received funds via FixedFloat.
The same address also funded the NRW deployer.
The Jan 7 price drop was triggered by EOA 0x9481b7c8f83A7BB3E8e3648b453d6Eb59dFFcC30, which called withdraw on unverified malicious contract 0x814304B1e200b4D36B26f53358BbBA6D6136B2F5.
This contract was created by 0x6eA, which was, in fact, funded by 0xfc8C, which had earlier funded the NRW deployer.
😈On Jan 4, 2024, the Defi Protocol Gamma Strategies was exploited for ~1535 $ETH (~$3.43M) in what seems to be the attack on Camelot pools, utilizing Gamma CLMM.
Hack Txn: https://arbiscan.io/tx/0x025cf2858723369d606ee3abbc4ec01eab064a97cc9ec578bf91c6908679be75
Other than @GammaStrategies, decentralized exchanges (DEX), such as @Quickswap, @SushiSwap, and
@CamelotDEX, could be affected due to this exploit.
Gamma has strongly advised all its users to revoke all approvals to avoid a possible fund loss due to the exploit.
@CryptoAlgebra, which was earlier speculated to be exploited, has confirmed that the exploit is not connected with Algebra’s code, and it is safe to use services from its partners.
Beware of the phishing websites claiming to check for exposure and revoke access from @CryptoAlgebra
In an official statement, Gamma confirmed that the hacks were carried out using flash loan attacks.
The total fund loss in the exploit is 1535 ETH, worth ~$3.43M, which the attacker: https://arbiscan.io/address/0x5351536145610aa448a8bf85ba97c71caf31909c
has now bridged to #Ethereum in the multiple transactions.
Ref: https://etherscan.io/address/0x5351536145610aa448a8bf85ba97c71caf31909c
Gamma Exploiter Malicious Contract: https://arbiscan.io/address/0x4b57adc00ac38f74506d29fc4080e3dc65b78a69
Mitigation Steps
As a precautionary measure, Gamma has shut off all deposits on public-facing vaults. At the time of writing, the rebalances and management of the positions are active and operational, as they are not affected by the exploit.
What Caused the Exploit?
Although multiple measures were in place to prevent flash loan attacks but out of those measures, there was one that had a flaw.
The measure—where Gamma had set a price change threshold to disallow deposits on price change exceeding a certain threshold—was manipulated by the exploiter.
The threshold limits were set too high, which allowed up to 50-200% price change on specific LST and stablecoin vaults.
The attacker manipulated the price up to this high threshold limit and then minted a large number of LP tokens.
Corrective Measures
To set things right, Gamma has taken the following steps:
- Setting of rice change thresholds to a safe threshold level
- Getting a 3rd party code review before re-enabling deposits
- Maximizing recovery for all affected users
- Conduct a detailed post-mortem analysis and propose a remediation plan
😈In another major crypto exploit, on Jan 2, 2024, Radiant Capital @RDNTCapital on the Arbitrum chain was exploited for ~$4.5M (~1.9K ETH).
The root cause of the hack is price manipulation, which was carried out by exploiting a rounding issue in the rayDiv() function.
The Exploitation
First, the index parameter (used as a denominator in the calculations) was inflated due to manipulation. The corresponding precision error also skyrocketed due to this inflation.
The attacker reaped profits through repeated deposit() and withdraw() operations.
The attack happened within the time frame of 6 seconds immediately after a new USDC market was deployed.
The rounding issue is a known issue in the current Compound/Aave codebase, which is forked by lending markets for activating new marketing.
To mitigate this, Aave has a mandatory policy to deposit alongside any new listing. While forking, it seems this practice was not taken into consideration.
Attacker’s address: https://arbiscan.io/address/0x826d5f4d8084980366f975e10db6c4cf1f9dde6d
Malicious contract:
https://arbiscan.io/address/0x39519c027b503f40867548fb0c890b11728faa8f
The Aftermath
The team @RDNTCapital is trying to initiate contact with the attacker by leaving an on-chain message for the attacker, but they are still waiting to receive a response.
Ref: https://arbiscan.io/tx/0xcd1865e3bf185fc5fe0b5fb055f6d74cfa68ee50335ff92ad721063538922664
While the hack is being investigated, the Radiant DAO Council has paused lending/borrowing markets on Arbitrum temporarily.

