Introduction
Table of Contents
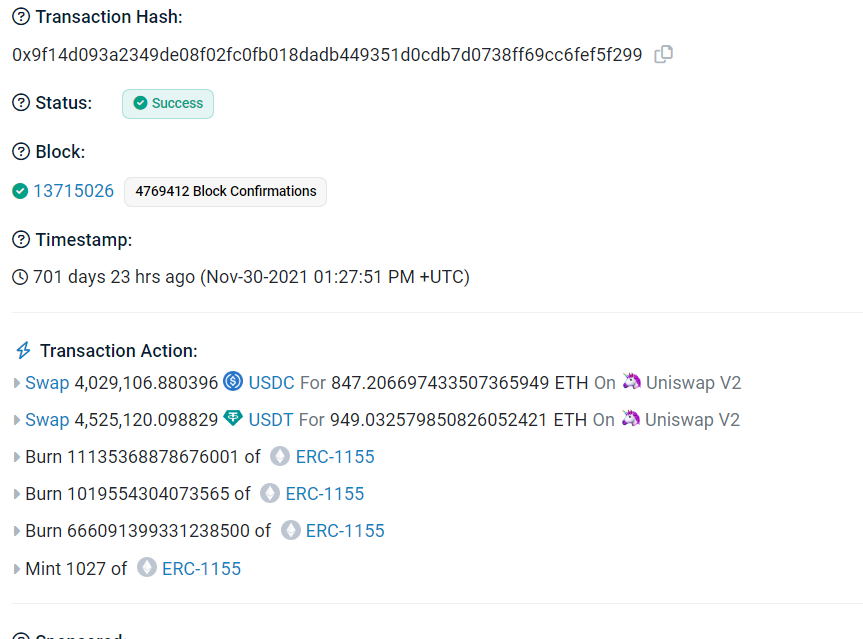
On November 30, 2021, the DeFi protocol, MonoX, experienced a significant security breach. The attacker drained considerable assets, amounting to a total loss of over $31 million.
A sophisticated attacker exploited the MonoX protocol, capitalizing on a loophole in the swapping function. The loss included assets such as WETH, Matic tokens, and several other prominent tokens like Wrapped Bitcoin and Chainlink. The attack was executed on both the Ethereum and Polygon networks.
What is MonoX?
MonoX is an innovative DeFi protocol introduced with a unique design. Instead of the traditional paired liquidity pools, it employs a single token design. This is achieved by virtually pairing deposited tokens with the vCASH stablecoin. Their first implementation of this design was the automatic market maker system known as Monoswap, which was unveiled in October 2021.
Attack Details
Attacker Addresses:
0xecbe385f78041895c311070f344b55bfaa953258
0x8f6a86f3ab015f4d03ddb13abb02710e6d7ab31b
Attack Contracts:
0xf079d7911c13369e7fd85607970036d2883afcfd
0x119914de3ae03256fd58b66cd6b8c6a12c70cfb2
Transaction References:
Etherscan Transaction: https://etherscan.io/tx/0x9f14d093a2349de08f02fc0fb018dadb449351d0cdb7d0738ff69cc6fef5f299
Polygonscan Transaction: https://polygonscan.com/tx/0x5a03b9c03eedcb9ec6e70c6841eaa4976a732d050a6218969e39483bb3004d5d
Root Cause
There was a vulnerability in the swap smart contract, which failed to verify if the transferred and outgoing tokens in the liquidity pool were identical.
The attacker leveraged this flaw in the price update function to manipulate the MONO token price artificially. Subsequently, they exchanged the inflated MONO tokens for other assets in the MonoX protocol.
Detailed Attack Breakdown
Initial Setup
- Action: The attacker began by using the
Monoswap.swapExactTokenForTokenfunction. - Outcome: Successfully swapped 0.1 WETH for approximately 79.99 MONO.
Asset Draining & Liquidity Manipulation:
- Method: The hacker constructed a custom contract to facilitate the attack.
- Execution: Drained all assets from a particular pool and subsequently replenished it with their own liquidity, amplifying the impact.
- Exploited the code located between lines 471–510 in
Monoswap.sol.
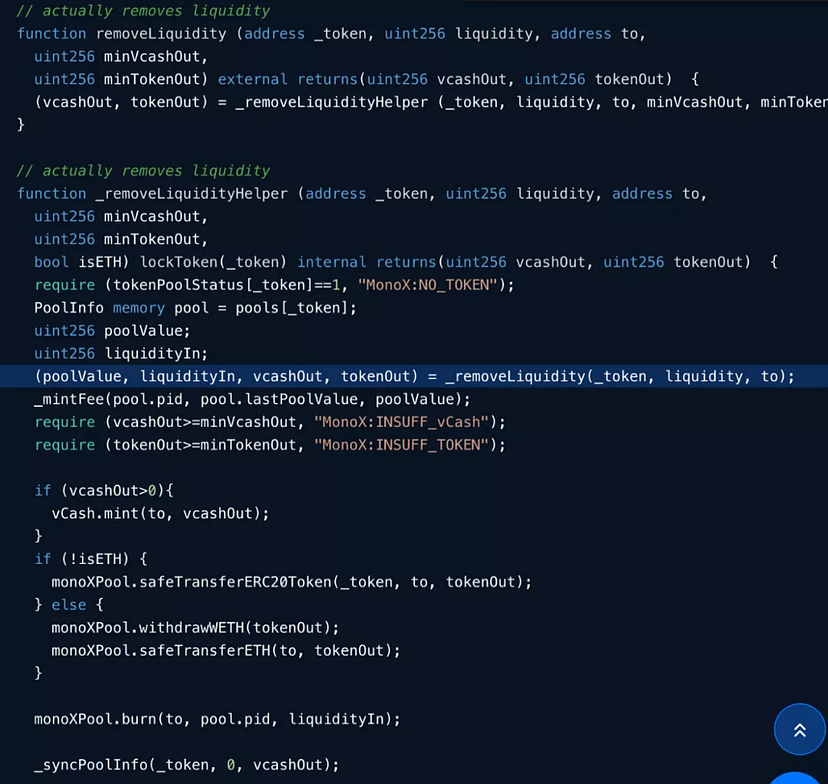
During this, the _removeLiquidityHelper function was invoked, sidestepping necessary authentication checks.
Specific Actions:
- Remove the liquidity of 0x7b9aa6, transfer 1670.7 MONO and 6.8622171986812230290 vCASH to 0x7b9aa6
- Remove the liquidity of cowrie.eth, transfer 152.9 MONO and 0.628300423692773565 vCASH to cowrie.eth
- Remove the liquidity of 0xab5167, transfer 99940.7 MONO and 410.478879590637971405 vCASH to 0xab5167
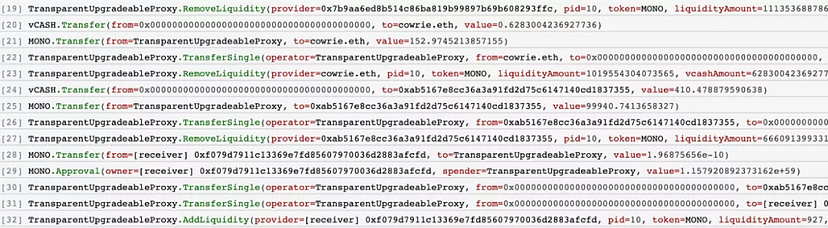
- Contributed liquidity to the MONO token pool via contract 1.
Inflating the Price
Strategy: Repeated use of the Monoswap.swapExactTokenForToken function.
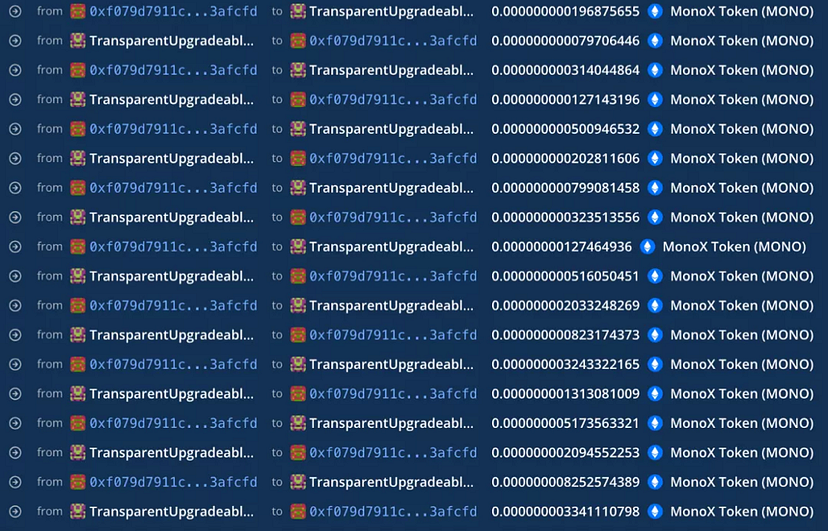
Frequency: The function was called 55 times to drive up the MONO price consistently.
Cause of Vulnerability
The swapExactTokenForToken function in Monoswap.sol permitted the use of identical tokens for both input and output, resulting in a price discrepancy.
Analysis of the swapIn function showed its dependency on the getAmountOut function, which subsequently used the _getNewPrice function for price computation.
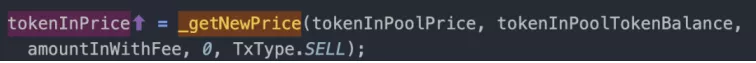
Due to similarities in the calculation parameters, we can deduce that the price of the output token (tokenOutPrice) was consistently higher than the input token (tokenInPrice).

Given that the tokens for input and output were identical, the price of the token was artificially inflated when the _updateTokenInfo the function was triggered post-calculation.
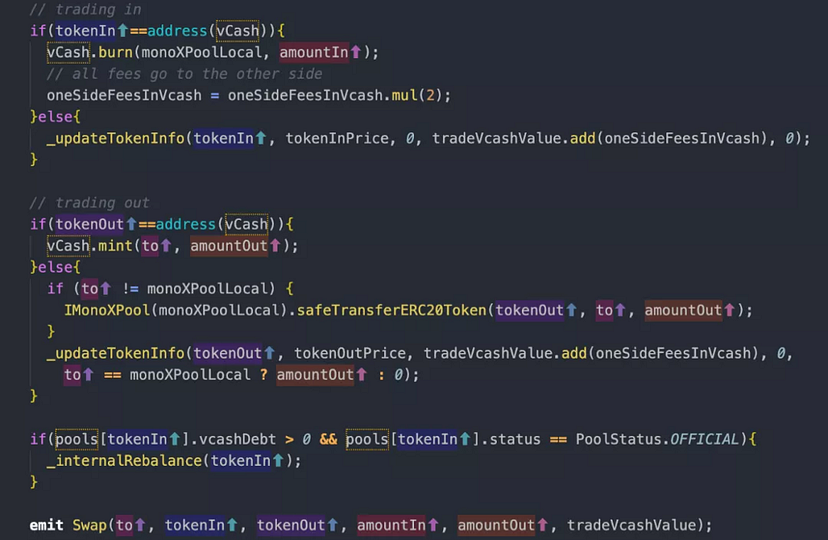
Final Phase – Asset Conversion & Profit
Action: Leveraging the inflated MONO price to call the swapTokenForExactToken function.
Objective: Swapping inflated MONO for other valuable tokens in the pool.
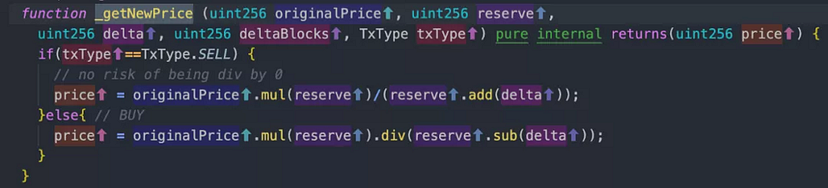
Technical Insight
Price determination was achieved by calling the swapOut function inside the swapTokenForExactToken function, which was further reliant on the getAmountIn function.
The price of MONO tokens in the pool (tokenInPoolPrice) was artificially high due to previous steps, which meant the MONO tokens were more valuable, enabling the hacker to purchase a larger array of assets from the MonoX protocol.
What Happened to Stolen Funds?
The stolen assets were eventually transferred to the address: 0x8f6a86f3ab015f4d03ddb13abb02710e6d7ab31b.
Loss Breakdown
MonoX Finance incurred a staggering loss nearing $34 million, segmented as follows:
- 2.1k WETH
- 1.9m WMATIC
- 36.1 WBTC
- 143.4k MONO
- $8.2m USDC
- $9.1m USDT
- 1.2k LINK
- 3.1k GHST
- 5.1m DUCK
- 4.1k MIM
- 274.9 IMX
Since then, the hacker has also moved a significant amount to Tornado Cash
Conclusion
The MonoX hack stands as a testament to the importance of rigorous smart contract auditing and the dangers of unchecked functions. It’s essential to ensure that such vulnerabilities are identified and rectified before deployment.
This serves as a reminder for all DeFi protocols to invest in regular security audits and maintain transparency with their communities.

