Overview
Table of Contents
PlayDapp, a well-known South Korean crypto gaming and NFT platform operating on Ethereum was exploited twice between February 9th and 12th, 2024. The exploit resulted in a staggering loss of $290 million.
The evidence indicates a private key breach, allowing the addition of a new minter to PlayDapp shortly before the attacks occurred. The attacker successfully minted 1.79 billion PLA tokens on two separate occasions. However, they could only convert $32 million of the initially stolen funds. To obscure their tracks, the attacker scattered the funds across various EOAs and chains.
About PlayDapp
PlayDapp is a popular gaming platform and NFT marketplace. Its primary goal is to transition non-crypto users into blockchain-based gamers by offering an extensive gaming and crypto network.
On the PlayDapp platform, games are primarily offered as NFTs (non-fungible tokens), which users can directly purchase from others on the blockchain-based platform. PLA serves as the main token for transactional activities on PlayDapp. Additionally, game developers receive PLA when users make in-game purchases.
Established in Seoul, Korea, in 2017, PlayDapp was founded by Sung-Wone “Moshua” Choi. Choi, recognized as the founder of PlayDapp, also holds the position of CEO at SuperTree, a publisher of metaverse content platforms.
Root Cause of the Hack
The root cause behind the PlayDapp loss is a private key exploit. A private key exploit occurs when an unauthorized person gains access to the private cryptographic key of a user or platform. In the context of cryptocurrency, particularly Ethereum-based platforms like PlayDapp, the private key is essentially the secret code that allows individuals to access and manage their digital assets, such as tokens or cryptocurrencies.
Attacker’s EOA addresses:
- Initial Address: 0xD151050d43c28690766f50Ce9ea8686c5D243a40
- EOA/2: 0x1cae9eAa76E880fe47A26dd838E5Ec056C289155
- EOA/3: 0xe84d086f2c402d297d05b1bccc06d0e0942ec03c
- EOA/4: 0x23cAeE3666b553445e430D1635AD64fBF388B07d
Victim contract: 0x3a4f40631a4f906c2bad353ed06de7a5d3fcb430
Detailed Technical Analysis
Following is the sequence of events that unfolded during the hacking incident:
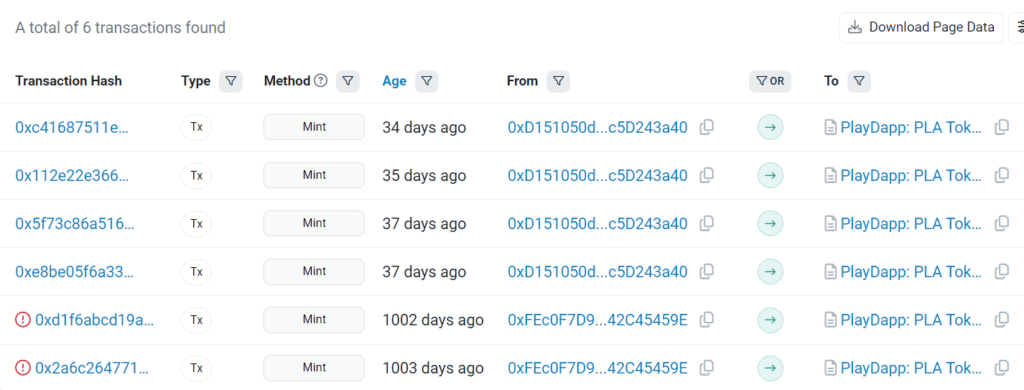
Attack Transactions (Etherscan)
- Tx1: 0xe8be05f6a3360f63b9e78a30b4ba16ea4c7d0b530a8abf99390f1c831851fb7e
- Tx2: 0xc41687511e31f5612b73647c4b39e500e45dbfb2ae66789b7b8705d2336002f8
- Tx3: 0x5f73c86a516616e25b3d13188f3289472d22a06cb1029ff174e00596a97e13b9
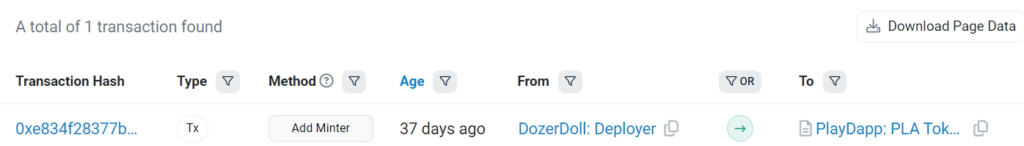
- “Add Minter” Tx4: 0xe834f28377b79759ac5495a91975a01e0876af9aae312228c1ac525846406170
The address of the contract deployer was reportedly compromised, allegedly due to a private key exploit.
The compromised and unauthorized wallet then added the attacker’s address as a minter for the PLA Token.
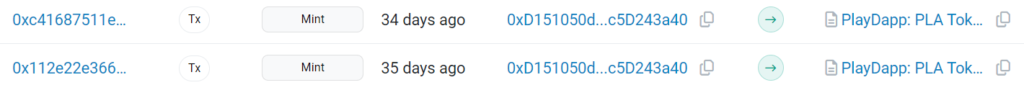
During the first attack on February 9th, over 200 million PLA tokens were minted, valued at $36.5 million. This amount represented 72% of the total supply originally minted.
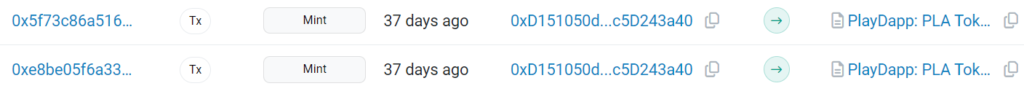
In the subsequent attack on February 12th, an additional 1.59 billion PLA tokens were minted, valued at $253.9 million at that time.
Stolen Fund Flow
The hacker could only convert $32 million of the stolen tokens due to the considerable challenge posed by the large number of newly minted tokens. With the total circulating supply of PLA at $577 million before the exploit, selling such a substantial amount, especially at pre-hack market rates, presents a significant hurdle. The hacker minted 72% of the total supply originally minted.
After the exploit, a considerable number of tokens still reside with the attacker. The stolen tokens were dispersed through various transactions:
- 0x964837f1cffd9d54aae2d8a2083a8927219095ff7857194865b65b1d32669414
- 0x1cb750dfcd6a425eac3013a4b0994eaa719d5e6824196fe3c06dafe4b6fa55a2
- 0xfae62c49a680b22bc4f591cff9af57e86d5219f667307e3a06b96c77b417eba4
Hack Aftermath
Following the exploit, PlayDapp contacted the exploiter and extended a $1 million white hat reward for the safe return of the stolen assets by February 13.
Message from PlayDapp to the hacker: 0xb8c379f3ae8ea3ba48cdb7dac79c9b995f0e7a372a8bf9d620a6bfc875a31628
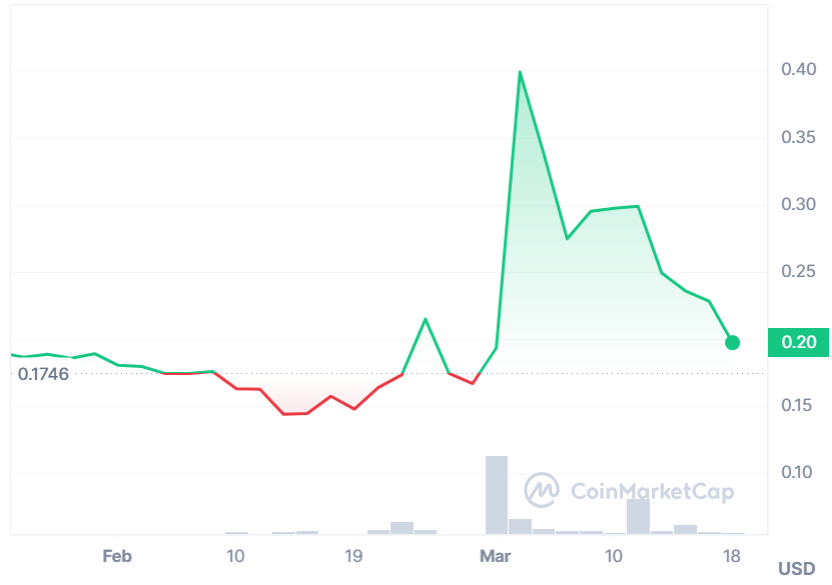
Before the exploit, the total circulating supply of PLA tokens stood at $577 million. Following the breach, the PLA token plummeted in value, trading 0.4% lower at approximately $0.14, marking a decline of over 15% in that week.
On February 13, 2024, PlayDapp halted the PLA smart contract to capture a screenshot for migration amidst the ongoing hacking situation.
Coinbase halted PLA token trading after the platform’s smart contract was paused.
The value of the PLA token underwent fluctuations, dropping significantly after the breach, yet showing a recovery afterward.
Mitigation Steps
Mitigation steps for the exploit on PlayDapp could include:
Enhanced Security Measures:
Enhancing security protocols for private keys and ensuring their secure storage.
Implementing multi-signature wallets requires multiple approvals for significant transactions.
Regular Security Audits:
Conducting routine security audits and penetration testing to identify vulnerabilities.
Engaging third-party cybersecurity firms to assess the platform’s security posture.
Improved Monitoring and Detection:
Introducing real-time monitoring tools to identify abnormal activity or unauthorized access.
Setting up alerts for any suspicious transactions or changes to critical systems.
Implementing Delayed Minting or Transfer:
Introducing a delay mechanism for minting or transferring tokens, allowing time for validation and verification.
This can prevent the immediate exploitation of any compromised accounts.
Emergency Response Plan:
Developing a comprehensive incident response plan to address any security breaches swiftly.
Clearly defining roles and responsibilities for responding to security incidents.
By implementing these mitigation steps, a protocol can bolster its defenses against similar exploits, protect user funds, and maintain trust within the crypto community.
Conclusion
The PlayDapp exploit, which occurred between February 9th and 12th, 2024, involved an attacker gaining access to the contract deployer’s address through a private key exploit.
This allowed the attacker to mint 200 million PLA tokens worth $36.5 million initially and later an additional 1.59 billion PLA tokens worth $253.9 million. PlayDapp offered a $1 million white hat reward for the safe return of assets, however, the attacker has refused. The attacker still holds a significant portion of the stolen tokens as of the last known update.
Mitigation steps for a private key exploit involve securing keys, using multi-signature wallets, and regular smart contract security audits. Real-time monitoring detects anomalies while educating users, implementing transaction delays, and engaging with the security community to strengthen defenses. Prioritizing the strengthening of security measures and educating the community is crucial to prevent similar incidents.

