In the realm of blockchain technology, Layer 1 (L1) protocols serve as the foundational layer, dictating consensus mechanisms, transaction formats, and data structures. Yet, testing L1 protocols presents a formidable challenge due to their intricate and interdependent components.
This article explores the intricacies of testing Layer 1 (L1) protocols and examines how fuzzing offers an effective solution for identifying and addressing security vulnerabilities within blockchain systems at the protocol level.
What is Fuzzing?
Table of Contents
Fuzzing is an essential automated testing method used to evaluate blockchain protocols and smart contracts. It generates diverse inputs to uncover security vulnerabilities by triggering unexpected system behavior. Unlike traditional testing, fuzzing operates with randomness, stressing the system to reveal weaknesses. It’s especially valuable for blockchain, enhancing security by identifying vulnerabilities in smart contracts and protocols before exploitation.
Types of Fuzzing?
L1 Fuzzing
Fuzzing proves invaluable for auditing Layer 1 protocols, particularly when examining virtual machines, as it streamlines security and stability assessments. Leveraging code coverage analysis, fuzzing unveils insights inaccessible to manual scrutiny, facilitating robust vulnerability detection.
Smart Contract Fuzzing
For smart contracts, fuzzing entails analyzing Application Binary Interfaces (ABI) or bytecode, generating randomized valid inputs, executing contract functions, and scrutinizing results for weaknesses.
Let’s explore how fuzz testing can effectively identify vulnerabilities in smart contracts:
- Generating Input Data: Fuzz testing begins by generating a diverse set of input data that will be used to test the smart contract. This data can include valid inputs, invalid inputs, random inputs, and edge cases.
Injecting Inputs: Once the input data is generated, it is injected into the smart contract to observe how it behaves under various conditions. The goal is to identify any unexpected behaviors or vulnerabilities that may arise when processing the input data. - Monitoring and Analysis: During the testing process, the behavior of the smart contract is monitored, and any anomalies or errors are recorded. This may involve analyzing runtime logs, transaction outputs, and other relevant metrics to identify potential vulnerabilities.
- Feedback and Iteration: Based on the findings from the fuzz testing, developers can then refine the smart contract code to address any identified vulnerabilities. This iterative process helps improve the overall security and robustness of the smart contract.
- Automation: To streamline the fuzz testing process, developers can leverage automated fuzzing tools and frameworks specifically designed for smart contracts. These tools can efficiently generate input data, execute tests, and analyze results, saving time and effort in the testing phase.
By incorporating fuzz testing into the smart contract development lifecycle, developers can proactively identify and mitigate potential security vulnerabilities before deploying their contracts to the blockchain network. This proactive approach to security helps enhance trust and confidence in blockchain-based applications and contributes to the long-term success and adoption of decentralized technologies.
Code Examples
To illustrate fuzz testing, consider a simple, smart contract managing an account balance:
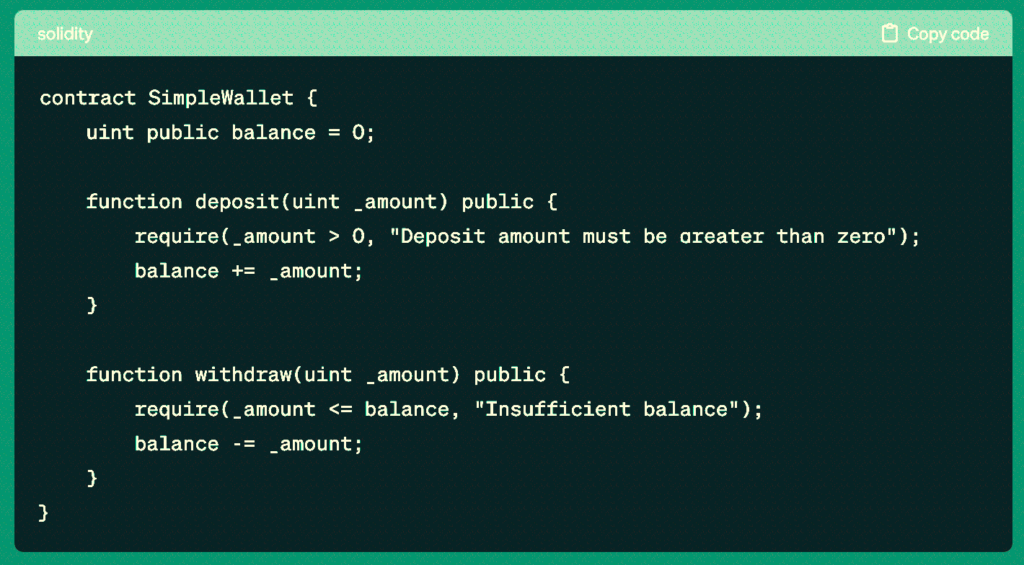
Fuzz testing for this contract would involve generating random input values for both the deposit and withdraw functions to ensure correct behavior under various conditions.
The Main Challenges of Fuzzing
Constructing a fuzz target stands out as a primary hurdle in fuzzing. A fuzz target refers to the specific component or system that is being tested using fuzzing techniques.
In the context of smart contracts and blockchain protocols, a fuzz target could be a particular function within a smart contract, a blockchain consensus algorithm, or a cryptographic component.
The process of building a fuzz target involves several intricate steps, each presenting its own set of challenges:
- Target Identification: The first challenge is to accurately identify the component or system to be tested. In the case of smart contracts, this could involve selecting specific functions or methods within the contract that are deemed critical or prone to vulnerabilities. For blockchain protocols, identifying the consensus algorithm or cryptographic components that require testing is crucial.
- Tokenization: Once the target is identified, it needs to be tokenized, i.e., broken down into smaller, manageable units for testing. This involves understanding the structure and behavior of the target and determining how it can be effectively tested using fuzzing techniques.
- Format Specification: Fuzzing requires a clear specification of the input formats expected by the target. This could include defining the data types, ranges, and constraints that the inputs must adhere to. Specifying the format accurately is essential to ensure that the generated inputs are valid and relevant to the target being tested.
- Cloud Deployment: Fuzzing often involves running tests on multiple machines or in distributed environments to achieve comprehensive coverage. Setting up and managing the infrastructure required for cloud deployment can be challenging, especially when dealing with large-scale fuzzing campaigns.
- Automation: Fuzz testing typically involves generating a large number of inputs and running them through the target system automatically. Automating this process requires developing scripts or tools that can handle input generation, test execution, result analysis, and reporting seamlessly.
- Parameterization: Fuzzing tools need to be configured with parameters that control the generation of inputs and the execution of tests. Parameterization involves fine-tuning these settings to ensure that the tests are effective and efficient in identifying vulnerabilities.
Addressing these hurdles demands a blend of technical proficiency, domain insight, and specialized tools. Moreover, the complexity and diversity of smart contracts and blockchain protocols further amplify the difficulty of building effective fuzz targets.
However, addressing these challenges is essential for harnessing fuzzing’s full potential in identifying and mitigating security vulnerabilities in blockchain systems.
Use Cases
Fuzzing is applicable in various scenarios where traditional testing methods may fall short in uncovering critical code errors and vulnerabilities. Here’s a deeper look into when fuzzing proves to be particularly effective:
- Detecting Elusive Code Errors: Fuzzing is adept at discovering code errors that may evade manual detection. These errors can include subtle logic flaws, edge cases, or unexpected behavior triggered by certain input combinations. By subjecting the software to a wide range of inputs, fuzzing can reveal hidden bugs that might go unnoticed during manual testing.
- Critical Vulnerabilities: Fuzzing is especially valuable in identifying critical vulnerabilities that have the potential to cause severe disruptions or compromise the system’s security. Examples of such vulnerabilities include infinite loops, where a program gets stuck in an endless cycle, buffer overflows, which can lead to unauthorized access or code execution, and memory allocation issues, which may result in crashes or system instability.
- Smart Contracts Security: In the realm of smart contracts, fuzzing plays a crucial role in addressing specific vulnerabilities inherent to blockchain-based applications. For instance, integer overflows, where arithmetic operations exceed the limits of data types, can lead to unexpected behavior or even exploitation by malicious actors.
Denial-of-service threats, which involve overwhelming the contract with excessive demands, can disrupt its functionality or lead to resource exhaustion. Additionally, reentrancy vulnerabilities, where a contract’s state can be manipulated unexpectedly during external calls, pose significant risks that fuzzing can help uncover.
By targeting these areas of concern, fuzzing contributes significantly to enhancing the security, reliability, and resilience of software systems, including smart contracts deployed on blockchain platforms. Its ability to uncover complex and nuanced vulnerabilities makes it an indispensable tool in the arsenal of developers and auditors seeking to fortify their code against potential threats.
Drawbacks of Fuzzing
While fuzzing is a powerful testing technique, it comes with its own set of drawbacks that need to be considered:
Post-Discovery Issue Resolution: One major challenge with fuzzing is the need to address issues promptly after their discovery. Fuzzing often uncovers a multitude of vulnerabilities, and each one needs to be fixed to prevent the fuzzer from repeatedly encountering the same issue. This can create a bottleneck in the development process, requiring developers to prioritize and address each vulnerability in a timely manner.
- Limitations in Detecting Complex Bugs: Fuzzing may struggle to detect bugs that require multiple steps to execute or involve intricate program logic. For example, if a bug manifests only after a specific sequence of operations or interactions, fuzzing may have difficulty reproducing it. This constraint may lead to undetected vulnerabilities, particularly in intricate software systems.
- Time-Consuming Execution: Fuzzing proves time-consuming, particularly with extensive codebases or complex applications. Generating and executing a large number of test cases to achieve adequate code coverage requires significant computational resources and time. As a result, fuzzing may not be suitable for rapid testing iterations or tight development timelines.
- Overlooking Logic Errors: Fuzzing primarily focuses on testing for crashes, assertion failures, or other forms of unexpected behavior caused by input data. As a result, it may overlook logic errors or flaws in the underlying algorithmic logic of the software. Logic errors can lead to subtle bugs or vulnerabilities that may not manifest as crashes but still affect the correctness or security of the system.
- Challenges with Stateful Components and Multi-threaded Applications: Fuzzing stateful components, such as those that maintain internal state or interact with external resources, can be challenging. Keeping track of the system’s state and ensuring consistent test coverage across different states requires sophisticated fuzzing techniques. Similarly, fuzzing multi-threaded applications presents difficulties in coordinating inputs and monitoring concurrent execution paths, potentially leading to incomplete test coverage or missed vulnerabilities.
Despite these drawbacks, fuzzing remains a valuable testing approach for uncovering a wide range of vulnerabilities and weaknesses in software systems.
Addressing Challenges with Fuzzing
Fuzzing stands out as a potent approach for delving into vulnerabilities within Layer 1 (L1) protocols. It adeptly simulates user actions, revealing latent vulnerabilities and scaling to address the intricacies inherent in these protocols. The Minima case study serves as a compelling illustration of fuzzing’s capability to unearth critical vulnerabilities, thereby fortifying the integrity of blockchain ecosystems.
Conclusions
Fuzzing stands as a powerful tool for blockchain audits, particularly in assessing virtual machines and smart contracts. While it complements manual review, fuzzing alone cannot substitute human expertise. Collaboration between automated testing tools like fuzzers and experienced auditors ensures comprehensive vulnerability detection and effective code remediation.
In essence, fuzzing for L1 protocols and smart contracts emerges as a pivotal practice in fortifying blockchain systems against potential vulnerabilities, paving the way for enhanced security and reliability in decentralized ecosystems.

