Overview
Table of Contents
On the 10th of November, 2022, DFX Finance, operating on an Ethereum-based protocol with the attack manifesting on the Polygon network, fell victim to a security breach involving a flash loan attack that exploited missing reentrancy protection.
The assailant executed a sophisticated scheme, siphoning off assets exceeding $7 million in value. Of this sum, the perpetrator directly appropriated $4.3 million while an opportunistic MEV bot front-ran the transaction, intercepting around $3.2 million.
The exploit underscores a critical vulnerability within the smart contract’s design, emphasizing the necessity for rigorous security measures in decentralized finance protocols.
About DFX Finance
DFX Finance is a Decentralized Exchange (DEX) protocol that operates on the Ethereum blockchain, catering specifically to fiat-backed stablecoins and leveraging real-world FX price feeds to optimize trades.
It utilizes dynamically tuned bonding curves to facilitate trading, ensuring price efficiency for stablecoin transactions. While specific statistics and notable clients were not provided, DFX has established a reputation in the cryptocurrency space for enabling efficient stablecoin trading.
Root Cause of the Hack
The primary reason for the hack was a missing reentrancy guard in the flash loan function. Due to this vulnerability, the contract incorrectly recognized the flash loan as repaid when, in fact, the attacker had only redeposited borrowed funds.
Attack Flow
Initiation of the Attack
The attack on DFX Finance commenced with the exploiter leveraging the protocol’s flash loan function. This maneuver involved borrowing USDC and XIDR stablecoins and then re-depositing them into the liquidity pools, thereby manipulating the protocol into falsely acknowledging the loan as repaid.
Execution of the Flash Loan Exploit
Calling the viewDeposit() Function: The attacker began by interacting with the “usdc-xidr” pair contract’s viewDeposit() function, which calculates the required amount of USDC and XIDR tokens and mints corresponding lptokens.
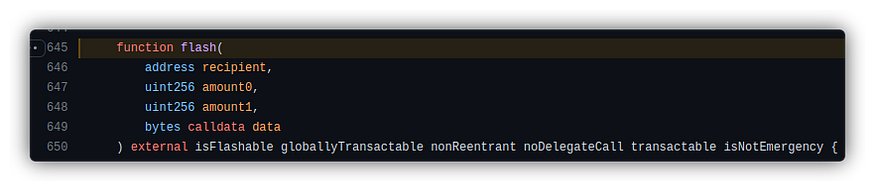
Borrowing and Redepositing
Enough USDC and XIDR were borrowed and then redeposited back into the contract. This was facilitated through the deposit() method, which then invoked the ProportionalLiquidity.proportionalDeposit() function, registering the attacker’s LP token and placing the borrowed funds back into the pool.
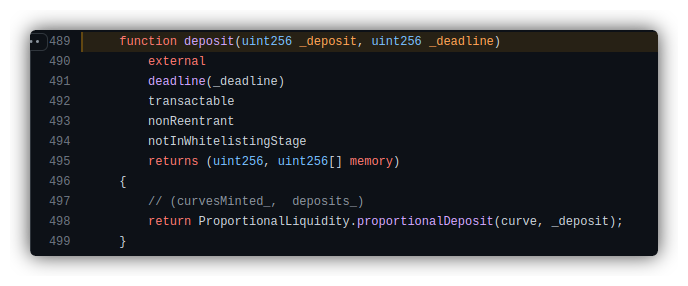
Bypassing Flash Loan Checks
The contract was tricked into believing the loan was settled as there was no outstanding amount under the attacker’s address, allowing the bypass of transaction pair checks.
Withdrawal of Funds
The attacker then executed the withdraw() function, destroying the lptoken and seizing the USDC and XIDR tokens.
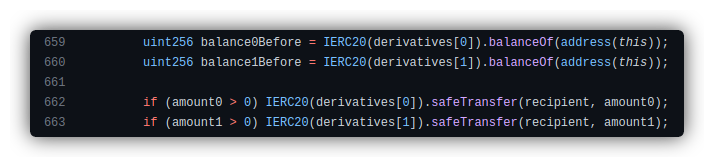
Re-entrancy and Emergency Withdrawal
The withdraw function’s re-entrancy protection was ineffective since the flash loan appeared complete, yet the attacker’s lptokens remained in the lending contract.
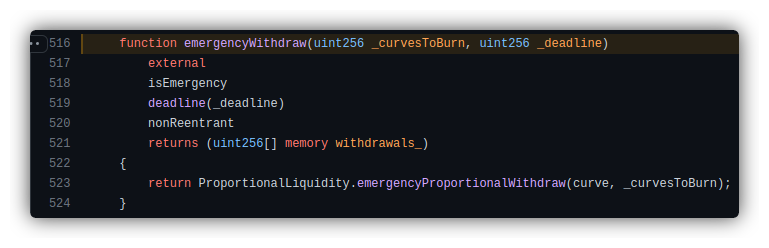
This allowed the attacker to repeatedly call the emergencyWithdraw() function, withdrawing all deposited tokens.
MEV Bot Intervention
Front-Running Transaction
An MEV bot intervened during the attack, executing a front-running transaction and siphoning approximately $3.2 million from the transaction flow. This unexpected development resulted in the attacker losing a significant portion of the stolen funds.
In an interesting turn, DFX Finance reached out to the MEV bot owner, requesting the return of the front-run funds.
Attack Txn: https://etherscan.io/tx/0x390def749b71f516d8bf4329a4cb07bb3568a3627c25e607556621182a17f1f9
Attacker’s Address: https://etherscan.io/address/0x14c19962e4a899f29b3dd9ff52ebfb5e4cb9a067
Attacker Contract: https://etherscan.io/address/0x6cfa86a352339e766ff1ca119c8c40824f41f22d#code
MEV Bot Address & transaction:
https://etherscan.io/address/0x6c6b87d44d239b3750bf9badce26a9a0a3d2364e
MEV Bot’s wallet address: https://etherscan.io/address/0xfde0d1575ed8e06fbf36256bcdfa1f359281455a
Unconventional ordering transaction Block: https://etherscan.io/block/15941904
MEV Bot & wallet transaction address analysis: https://etherscan.io/address/0xfde0d1575ed8e06fbf36256bcdfa1f359281455a
DFX Finance Code: https://etherscan.io/token/0x888888435fde8e7d4c54cab67f206e4199454c60#code
Stolen Fund Details
The attacker could only transfer $4.3 million worth of assets into their wallet. The remaining portion–about $3.2 million– was extracted by an MEV bot in a front-running transaction, also called a sandwich attack.
Hack Aftermath
DFX Finance had confirmed the breach, noting that they were alerted to unusual activities within 20–30 minutes after the initial transaction. In response, they swiftly suspended all DFX contracts minutes after validating the attack.
Furthermore, the DFX team has acknowledged the involvement of an MEV bot in the incident. This bot managed to divert a substantial amount of funds from the hacker. The team is currently seeking communication with the bot’s owner.
In addition to these developments, the team had raised concerns about the vulnerability of Polygon contracts to similar exploits. Consequently, they are proceeding with an urgent shutdown of these pools and plan to publish a detailed analysis of the attack in an upcoming postmortem report.
Mitigation Steps to Avoid Such Hacks
To avoid such re-entrancy attacks, the following measures could have been implemented:
- Mutex implementation to prevent multiple accesses.
- Reentrancy guard modifiers like those provided by OpenZeppelin.
- State changes should precede external calls (check-effect-interaction pattern).
Conclusion
The DFX Finance hack highlights the importance of thorough, smart contract auditing and the implementation of robust security practices such as reentrancy guards. A detailed and comprehensive smart contract auditing can potentially prevent such vulnerabilities and secure the DeFi ecosystem.

