Overview
Table of Contents
The BRA token experienced an exploit on January 10, 2023, resulting in a hacker successfully absconding with 819 $WBNB, equivalent to approximately $225,000. BRA token is compatible with the BNB Smart Chain and can also be found on PancakeSwap for trading.
The methodology behind this incident was a logical vulnerability that enabled the attacker to activate the transfer function, leading to double rewards when the sender and recipient formed a pair.
Root Cause of the Hack
The underlying reason for the vulnerability stems from a logical flaw in the BRA contract. This flaw is manifested in the transfer function of the contract, where rewards are generated in such a manner if the caller or recipient were a pair.
The hacker took advantage of a tax-sharing loophole in the token transfer process, creating an additional 1.6 million BRA tokens seemingly out of nowhere. These tokens were subsequently sold, resulting in a total profit of approximately 310,000 US dollars.
Vulnerable Smart Contract of the BRA token: https://bscscan.com/token/0x449fea37d339a11efe1b181e5d5462464bba3752#code
Victim liquidity pool BUSD-BRA: https://bscscan.com/address/0x8f4ba1832611f0c364de7114bbff92ba676adf0e
Attacker’s Address: 0x67a909f2953fb1138bea4b60894b51291d2d0795
Attack Contract: https://bscscan.com/address/0x6066435edce9c2772f3f1184b33fc5f7826d03e7
Attack Transaction: https://bscscan.com/tx/0x6759db55a4edec4f6bedb5691fc42cf024be3a1a534ddcc7edd471ef205d4047
Detailed Technical Analysis
Following is the sequence of events that unfolded during the hacking incident:
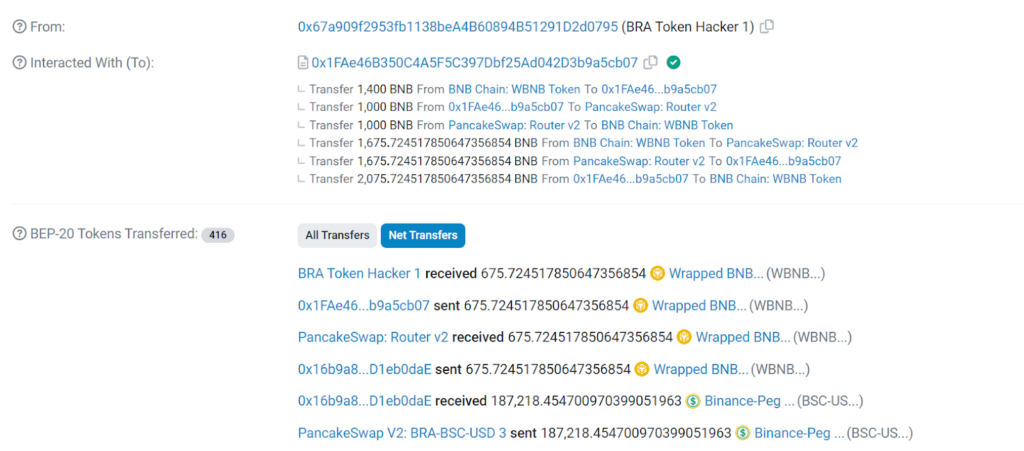
1. Flash Loan — Get WBNB
The attackers secured a flash loan of 1,400 WBNB by calling the attack contract. The attack contract utilizes the flashLoan() of DPPAdvanced (0x0fe261aee0d1c4dfddee4102e82dd425999065f4) to initiate a flash loan and borrowing 1000 WBNB.
2. Token Swap — BNB to BRA
The attack contract, initially holding 1000 BNB, withdraws from the WBNB contract and then exchanges WBNB to BNB. Conclusively, the attack contract invokes the swapExactETHforTokens function of PancakeSwap to convert 1000 BNB into BRA.
3. Transfer to the liquidity pool
The transferred amount to the liquidity pool involves a direct operation, as the assault contract sends the 83,337 BRA it possesses to the liquidity pool through a transfer.
Naturally, this transfer procedure involves tax collection. However, following tax collection, the tax proceeds are also directed into the liquidity pool. Consequently, the entire 83,337 BRA is effectively transferred to the liquidity pool.
4. Core Attack Point: Calling the skim() function
The attack contract invokes the skim() function to execute the pivotal step of the attack and receive rewards.
In the skim function, the attacker configures the “to” parameter as the liquidity pool, leading to a transfer from the liquidity pool to itself.
function skim(address to) external lock {
address _token0 = token0;
address _token1 = token1;
_safeTransfer(_token0, to, IERC20(_token0).balanceOf(address(this)).sub(reserve0));
_safeTransfer(_token1, to, IERC20(_token1).balanceOf(address(this)).sub(reserve1));
}The “skim()” function serves as a recovery mechanism when the quantity of tokens supplied to a pair surpasses the storage capacity of the two uint112 reserves.
5. Doubling of the Reward
In the scenario described above, the attacker designated the pair as the destination address, causing BRA to revert to the pair. This led to a doubling of the BRA amount with each individual skim. This process was repeated 100 times, leading to a substantial increase in the BRA balance held by the contract pair.
6. Closing the attack
The assailant reclaimed 1.675K WBNB tokens. Then repaid the 1.4K WBNB flash loan, which generated a profit of 675 WBNB, which was then transferred to their address.
The attacker repeated the same strategy, securing a profit of 144 WBNB from the BRA contract in another instance of the attack.
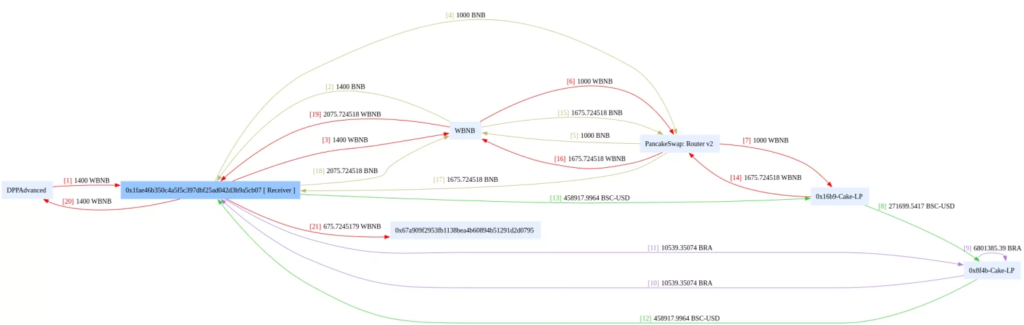
Stolen Fund Details
819 $WBNB were lost in this incident. Hence, funds equivalent to approximately $225,000 were stolen. The fund flow during the hack can be seen below:
Fund Flow during the Incident
Hack Aftermath
The whereabouts of the team associated with BRA tokens are undisclosed; consequently, there has been no official acknowledgment of the incident.
The value of BRA tokens plummeted by 98%.
Mitigation Steps
Mitigating flash loan attacks requires a comprehensive approach to enhance the security of smart contracts and the overall decentralized finance (DeFi) ecosystem. Here are some suggested mitigation steps:
- Reentrancy Protection:
Implement reentrancy protection in your smart contracts to prevent attackers from exploiting vulnerabilities related to recursive calls. Use mechanisms like the reentrancyGuard modifier to minimize the risk. - Use Authenticated Sender:
Implement transaction authentication to guarantee that only authorized users or contracts can engage with crucial functions. Achieve this by incorporating access controls and conducting permission checks. - Leverage Time Delays:
Introduce time delays or waiting periods for certain critical functions, providing a window for potential attacks to be detected and halted before any irreversible actions occur. - Limit External Calls:
Minimize external calls to other contracts or external systems within critical functions. This reduces the attack surface and reduces the possibility of manipulating the flow of execution. - Consistent Code Audits:
Regularly conduct code audits by experienced professionals or third-party security firms to identify and rectify potential vulnerabilities. This includes reviewing contract logic, access controls, and dependencies. - Use Standard Libraries:
Utilize standardized and audited smart contract libraries in smart contracts. This reduces the likelihood of incorporating vulnerable code and increases the overall security of your smart contracts. - Decentralized Oracles:
When using oracles, prefer decentralized oracles to obtain external data. Centralized oracles can be vulnerable to manipulation, leading to inaccurate data and potential exploits. - Implement Circuit Breakers:
Integrate circuit breakers or emergency stop mechanisms that can temporarily halt certain functions in the event of suspicious activities.
Conclusion
The incident of the BRA token hack clearly demonstrates how the smart contract industry is still naive when it comes to implementing complex logic such as flash loans and tax collection.
When creating tokens with tax collection functionality, it is crucial to carefully consider the tax payment amount to align with the design specifications. Simultaneously, ensure that the logic for sales tax and purchase tax are inverse to each other to prevent unintended secondary tax issuance.
However, following the mitigation practices mentioned above, one can avoid such losses. It is of utmost importance to prioritize reinforcing security measures and educating the community to prevent similar incidents.

