Overview
Table of Contents
On September 7, 2022, the Nereus protocol’s AVAX/USDC Joe LP NXUSD market was reported to be exploited, leading to the creation of $500k NXUSD bad debt. The incident was initially reported by the Nereus team through community channels and later highlighted by on-chain analytics groups. The exploit utilized a flash loan and culminated in a $371k profit for the attacker.
The Discovery of Exploit
At roughly 10:30PM UTC on September 6, 2022, the Nereus team became aware of the issue and quickly communicated it to their community through their discord platform.
Subsequent monitoring and assessment by some 3rd party auditors and on-chain analysis groups, identified the event as a flash-loan exploit, which led to a financial advantage of approximately $371k for the exploiter.
Immediately following the discovery, Nereus liaised with security professionals to devise a containment strategy. Law enforcement was notified to assist in the investigation.
In terms of mitigation, the compromised JLP market was both liquidated and paused by the Nereus team. The bad debt was covered by using NXUSD from the team’s treasury, ensuring no user funds were jeopardized. The NXUSD remained over-collateralized throughout this crisis.
It was clarified by the Nereus team that the lending and borrowing components of the protocol were never vulnerable during this incident.
The Flash Loan Attack
The exploit was orchestrated by an individual or group who devised a tailored smart contract. This contract utilized a massive $51M flash loan to momentarily manipulate the AVAX/USDC Trader Joe LP pool’s price. As a result, the attacker managed to mint 998,000 NXUSD, which was disproportionate to their collateral valued at approximately $508k.
The vulnerability stemmed from the recent introduction of a collateral type that supported AVAX/USDC Trader Joe LP tokens. A critical oversight occurred in the price determination process, making it prone to exploitation. Price calculations depended on real-time values without implementing any time-weighted average price (TWAP) mechanism. This absence of TWAP exposed the protocol to single-block price manipulation.
The Attack Details
The exploit was centered on the Nereus protocol’s recent support for AVAX/USDC Trader Joe LP tokens as collateral. A critical oversight in the price calculation mechanism for this collateral type was identified as the vulnerability.
Specifically, the protocol’s price calculation depended on real-time on-chain values: wAvaxReserve, usdcReserve, and totalSupply from the Trader Joe Pool.
Due to the absence of a Time Weighted Average Price (TWAP) mechanism, these values were open to manipulation within a single block.
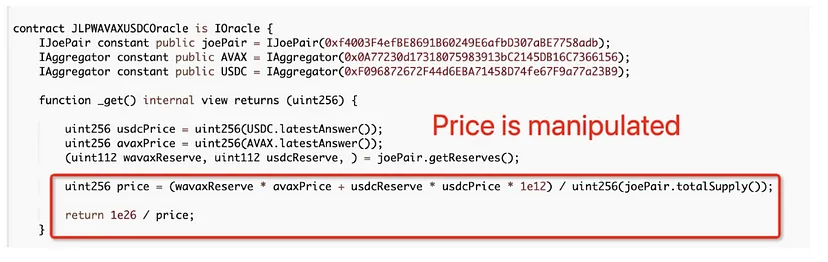
The formula used for LP price calculation was:
[ \text{LP price} = \frac{(wavaxReserve \times avaxPrice) + (usdcReserve \times usdcPrice)}{totalSupply} ]
The vulnerability was evident in the pool price chart, with a noticeable spike at Block Height: 19613453.
The exploit transaction can be referenced at: Snowtrace Transaction: https://snowtrace.io/tx/0x0ab12913f9232b27b0664cd2d50e482ad6aa896aeb811b53081712f42d54c026
Sequence of the Exploit
- Initiate a flash loan of 51,000,000 USDC from AAVE v3.
- Swap 280,000 USDC for 14,735 WAVAX in the wAVAX/USDC Joe pool.
- Inject liquidity using 260,000 USDC and 13,401 WAVAX into the Joe pool, resulting in the acquisition of 0.04533097793130507 JLP tokens.
- Swap the remaining 50,460,000 USDC for 505,213 WAVAX, artificially inflating the pool price to about $98 per WAVAX.
- Utilize the borrow function in the NXUSD market, depositing 0.04533097793130507 JLP, and borrowing 998,000 NXUSD. Here, the manipulated collateral value was ~$1,330M USD, whereas its true market value was around $500K USD.
- Swap 506,547 WAVAX (505,213 + (14,735–13,401)) back to 50,426,896 USDC.
- Convert 998,000 NXUSD into 955,678 avCRV using the NXUSD Factory 3crv pool.
- Swap 955,678 avCRV for 977,269 USDC.e in the 3crv pool.
- Convert 977,269 USDC.e into 970,010 USDC.
- Repay the flash loan with 51,025,500 USDC to AAVE v3.
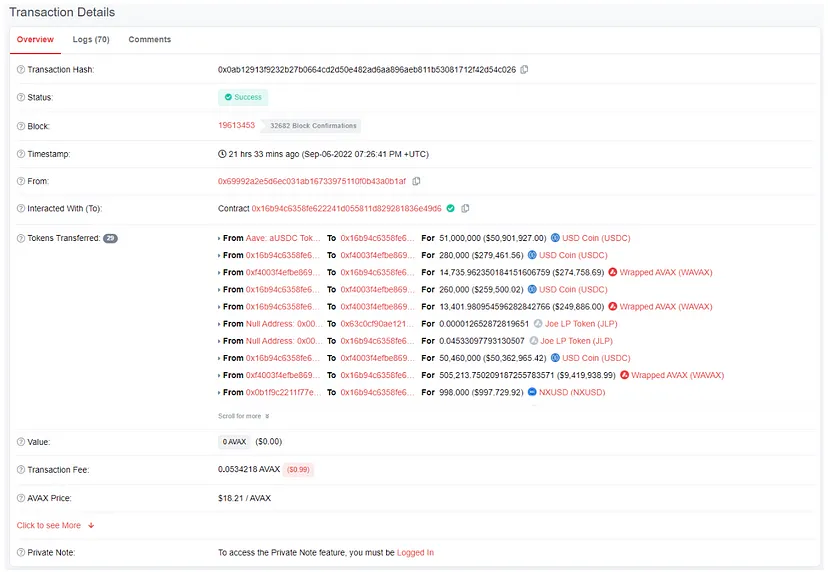
Net Outcome for the Exploiter: A profit of 371,406 USDC.
Immediate Response and Mitigation
Upon detection, the Nereus team promptly:
- Notified the community and relevant stakeholders.
- Consulted with security experts.
- Developed a mitigation plan, which included liquidating and pausing the affected JLP market.
- Paid off the bad debt from the Team’s treasury, ensuring no user funds were at risk.
- NXUSD remains over-collateralized and its lending/borrowing functions were never at risk and continue to function as intended.
Future Steps and Security Enhancements
- Implementation of TWAP calculations for more secure price feeds, especially for assets without Chainlink oracles.
- Continuous review and update of audit and security practices to prevent future vulnerabilities.
- A 20% White Hat reward was offered for the return of the exploited funds, alongside active efforts to trace and recover the stolen amount.
- While the incident was regrettable, it served as a valuable lesson for the Nereus team, who reiterated their commitment to user safety, protocol security, and risk mitigation.

