Overview
Table of Contents
On August 13, 2023, Zunami Protocol, a prominent DeFi platform on the Ethereum blockchain, fell victim to a sophisticated flash loan attack.
This exploit led to a substantial financial loss of 1,178 ETH, equivalent to approximately $2.16 million. The attacker, operating from an externally owned address (0x5f4C2), ingeniously manipulated the StakeDAO (SDT) price on Sushiswap.
This manipulation inflated the balance of Zunami’s stable token, UZD, allowing the attacker to transfer the stolen funds through Tornado Cash illicitly.
The attack unfolded in two major transactions, with the more significant one resulting in the extraction of 1,152 ETH, revealing vulnerabilities in Zunami Protocol’s security mechanisms.
About Zunami Protocol
Zunami Protocol, launched in the bustling sphere of decentralized finance (DeFi), is a platform on the Ethereum blockchain specializing in stablecoin management and yield optimization.
Its primary objective is to streamline and maximize returns for stablecoin investors. The protocol has carved a niche in the DeFi space, attracting attention with its innovative approach to yield farming and liquidity provision.
Despite its relatively recent inception, Zunami Protocol has marked significant milestones in terms of total value locked (TVL) and user adoption, positioning itself as a noteworthy player in the DeFi landscape.
However, the recent security breach underscores the perpetual challenges DeFi platforms face in safeguarding assets against increasingly sophisticated cyber threats.
Root Cause of the Exploit
The Zunami Protocol hack was fundamentally a consequence of price manipulation, exploiting the way UZD (Zunami’s stable token) balance was calculated. The core of this vulnerability lay in the assetPriceCached() function used in the formula:
Balance[address] * assetPriceCached()/DEFAULT_DECIMALS_FACTOR
Here, Balance[address] represents the UZD balance of the user, and DEFAULT_DECIMALS_FACTOR is a constant. The crucial aspect is the assetPriceCached() function, which returns the value of _assetPriceCached. This value was manipulated by the attacker using the cacheAssetPrice() function.
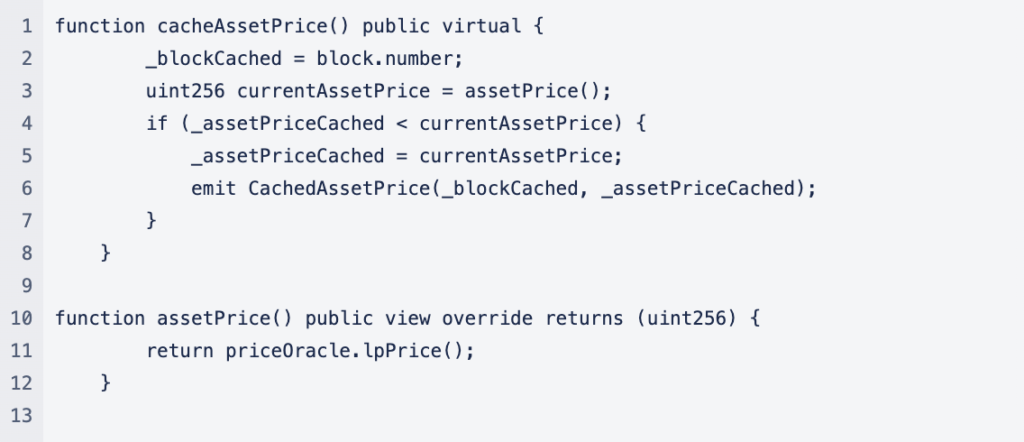
The contract responsible for the total holdings calculation across all Zunami pools is 0x2ffcc661011bec72e1a9524e12060983e74d14ce. The vulnerable pool in this exploit was identified as 0x984.
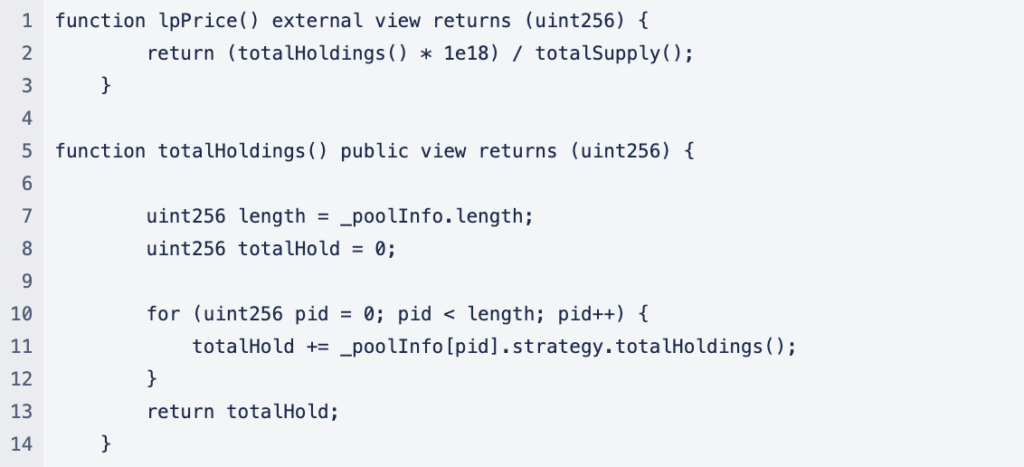
The formula for calculating total holdings in this strategy is:
_lpBalance * lpPrice + sdt * sdtPrice + config.crv * crvPrice

sdt is calculated by _config.sdt.balanceOf(address(this)), representing the balance of SDT in the strategy contract. The attacker increased this balance by transferring SDT into the strategy in one of the exploit steps.
priceTokenByExchange() function depends on the prices of Sushiswap pairs Stake DAO-WETH (0x22def8cf4e481417cb014d9dc64975ba12e3a184) and WETH-USDT (0x06da0fd433c1a5d7a4faa01111c044910a184553).
The attacker manipulated these prices in the exploit.
Vulnerable Contract: 0x2ffcc661011bec72e1a9524e12060983e74d14ce
Attack Contract: 0xa21a2b59d80dc42d332f778cbb9ea127100e5d75
Hacker Add: https://bit.ly/3OqXilq
Detailed Analysis of the Zunami Protocol Hack
The attack was executed in two major transactions, resulting in the loss of approximately 1,178 ETH:
The attack was carried out in two transactions:
- (26 ETH)Txn 1:https://bit.ly/455zElH
- (1152 ETH)Txn 2: https://bit.ly/3sfqkNf
For 2nd Transaction (Take the second attack, which yielded the most profit (i.e., ~1152 ETH), as an example):
Initial Transaction: The attacker withdrew 10 ETH from Tornado Cash for creating the attack contract.
Flash Loan Execution: Utilizing flash loans of 7,000,000 USDT from UniSwapV3, 7,000,000 USDC, and 10,011 WETH (~$18.4 million) from Balancer, the attacker initiated the exploit.
Token Swaps and Price Manipulation:
- Swapped 5,750,000 USDC for 5,746,896 crvFRAX on Curve, later exchanged for 4,082,036 UZD in pool 1.
- Swapped 1,250,000 USDC for 1,250,333 crvUSD on Curve, later exchanged for 791,280 UZD in pool 2.
- Swapped 11 WETH for 55,981 SDT in pool 3, transferring the SDT to the strategy.
- Swapped 10,000 WETH for 58,042 SDT in SushiSwap: SDT, and 7,000,000 USDT to 2,154 WETH in SushiSwap: USDT, significantly increasing the price of SDT-USDT.
Inflating UZD Balance: The attacker then called cacheAssetPrice() in the UZD contract (0xb40b), inflating their UZD balance from 4.8 million UZD to 16.9 million UZD.
Funds Conversion and Movement: The perpetrator skillfully manipulated their artificially inflated UZD balance, converting it into different crypto assets:
- In the first pool, they exchanged 14,158,424 UZD for 7,281,124 crvFRAX.
- In the second pool, 2,744,533 UZD was traded for 1,891,351 crvUSD.
- Following these transactions and the repayment of the borrowed amounts, the attacker successfully secured 1,152 WETH, equivalent to roughly $2.12 million.
Stolen Fund Details
Fund Movement
The stolen 1,178 ETH were moved through various transactions and eventually sent to Tornado Cash.
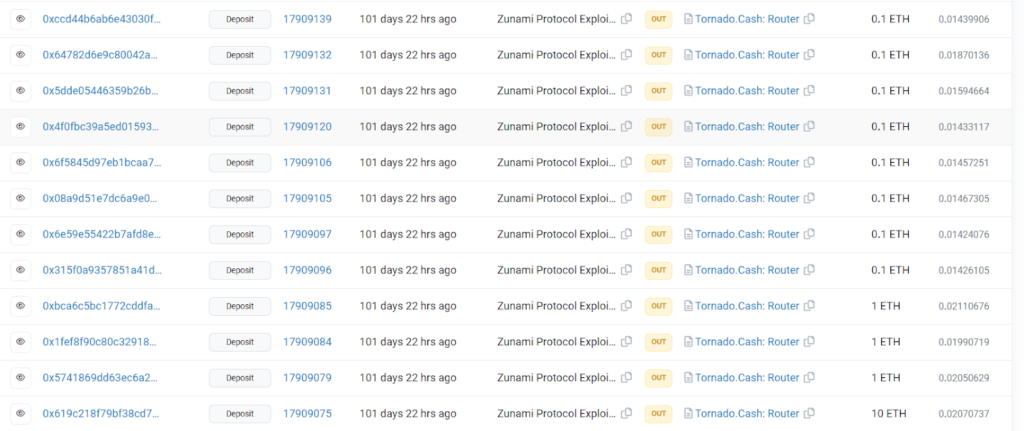
Hack Aftermath
Response by Zunami Protocol
Initial Acknowledgment: The team announced the occurrence of the exploit on their Twitter account, assuring users that the Omnipool collateral remained secure.
Collateral Distribution Plan: Zunami Protocol stated that UZD and zETH collateral would be distributed to holders from just before the hack, with equal compensation to all participants, regardless of their interaction with specific liquidity pools or addresses. This was communicated via Twitter.
Additional Measures: An extra comprehensive audit was planned for Zunami V2, along with updates and fixes to omnipools and zStables.
Compensation and Refund Details:
Process and Timeline: Users were informed about the upcoming collateral distribution in USDT/USDC/DAI, which they would need to claim themselves. The team posted updates on the expected start of fund distribution, as mentioned in their Twitter update.
Resources for Affected Users
Balance Calculation Script: https://github.com/ZunamiProtocol/ZunamiProtocol/commit/d00df349abc439b8e0d668d1d6879138b53334a8
UZD Balances: Detailed information was provided here:
https://docs.google.com/spreadsheets/d/121VgUuIOakQwhIdL3d7Af2SrvQHYInYqrNeer4TpsZ0/edit?usp=sharing
zETH Balances: Information was made available here:
https://docs.google.com/spreadsheets/d/15VneBK-Xg8TpSfbT2YkWr6thIqClKJqz32yCKSoEf1w/edit?usp=sharing
Claiming Process:
The official link for claiming the refund for UZD and zETH for the block before the hack was provided at claim.zunami.io. Official claiming addresses were also shared:
UZD: 0xa655Aa809D1FE7a55e22425780bb676E8AE0A143
zETH: 0x6756EfFa8aABeB9031279e4C71d8c1BD3Ae8f9Ef
Future Developments
Zunami V2 Launch: The team announced the upcoming launch of Zunami V2, which includes necessary fixes and an audit to prevent similar exploits in the future.
Based on the comprehensive analysis of the Zunami Protocol hack, the following lessons and mitigation steps can be drawn to prevent similar incidents in the future:
Lessons Learnt
Vulnerability in Pricing Mechanisms: The exploit highlighted the vulnerability in DeFi protocols related to the calculation of asset prices and balances. Protocols should rigorously test and secure their pricing mechanisms, especially when they are tied to complex functionalities like flash loans.
Flash Loan Attack Awareness: DeFi projects need to be highly cautious of flash loan attacks, as they allow attackers to amass significant temporary capital to manipulate markets or exploit vulnerabilities.
Importance of Comprehensive Audits: Engaging with security firms for periodic audits and staying updated with the latest security practices and patches. This also includes post-deployment monitoring and rapid response mechanisms. These audits should be conducted by reputable firms like ImmuneBytes with a strong track record in identifying similar vulnerabilities.
Robust Monitoring Systems: Continuous monitoring of the protocol’s activities for unusual patterns or spikes in transaction volume and prices can help in early detection of potential exploits.
Conclusion
The Zunami Protocol hack serves as a grave reminder of the vulnerabilities present in blockchain systems, particularly within the DeFi sector.
This incident, involving the exploitation of pricing mechanisms and the theft of over 2 million dollars, underscores the critical need for heightened security measures and the importance of regular, comprehensive audits in the blockchain domain.
It highlights the emerging challenges and the evolving nature of threats that such platforms face. Furthermore, the role of professional auditors like ImmuneBytes becomes increasingly vital.
Their expertise in proactive security assessments can play a pivotal role in identifying and mitigating potential vulnerabilities before they can be exploited, thereby bolstering blockchain projects’ overall security and integrity.
This hack not only sheds light on specific security flaws but also offers valuable lessons for the future of blockchain security, driving the industry toward more robust and resilient systems.

