Overview
Table of Contents
On March 28, 2023, SafeMoon, a DeFi platform on the Binance Smart Chain, suffered a significant security breach, resulting in the loss of approximately $9 million.
This incident was due to an access control vulnerability in the platform’s burn() function, inadvertently introduced during a smart contract upgrade by the SafeMoon Deployer.
The exploit involved the attacker manipulating the token’s value through this vulnerability, leading to substantial financial losses for SafeMoon and its users.
About SafeMoon
SafeMoon is a decentralized finance (DeFi) platform operating on the Binance Smart Chain. Designed to provide a secure environment for trading and holding cryptocurrencies, SafeMoon incorporates features like static rewards, automatic liquidity provider (LP) acquisition, and a token burn mechanism.
Launched with the aim of creating a stable and reliable platform for cryptocurrency enthusiasts, SafeMoon has positioned itself as a notable player in the DeFi space.
Root Cause of the Exploit
The fundamental reason behind the SafeMoon hack can be traced to an access control vulnerability within the smart contract, specifically in the burn() function. This vulnerability was inadvertently introduced during a contract upgrade executed by the SafeMoon Deployer.
Key Elements of the Vulnerability
Contract Upgrade Process: When the SafeMoon Deployer address upgraded the token contract to a new implementation, certain modifications were made to the contract’s functions, including burn().
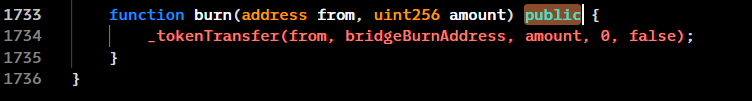
Access Control Oversight: The revised burn() function lacked adequate access control measures. Ideally, such critical functions should be restricted to specific addresses or require specific conditions to be met before execution. However, in this instance, the function was left publicly accessible, meaning any user could call it.
Functionality of burn() Method: The burn() function is designed to remove tokens from circulation, which in most DeFi protocols influences the token’s value due to changes in supply. The lack of access restrictions allowed the attacker to exploit this function to manipulate the token’s supply and, consequently, its market value.
Inefficient Smart Contract Auditing: The lapse in the auditing process (if any was conducted) for the upgraded contract is evident. A thorough audit should have identified such a critical vulnerability, especially in a function that directly impacts the token’s economics.
Technical Details
Vulnerable Contract Address: https://bscscan.com/address/0xeb11a0a0bef1ac028b8c2d4cd64138dd5938ca7a
Specific Code Reference: The vulnerability is located at line 1737 in the smart contract code.
SafeMoon Deployer’s EOA: 0x678ee23173dce625a90ed651e91ca5138149f590
Detailed Analysis of the Hack
Preparation Phase
Initial Token Acquisition:
- The attacker began their operations by acquiring a substantial amount of Wrapped Binance Coins (WBNB). This initial step involved purchasing approximately 102 WBNB tokens, a strategic move to ensure sufficient capital for the subsequent stages of the attack.
Execution Phase
Exploiting the Vulnerability:
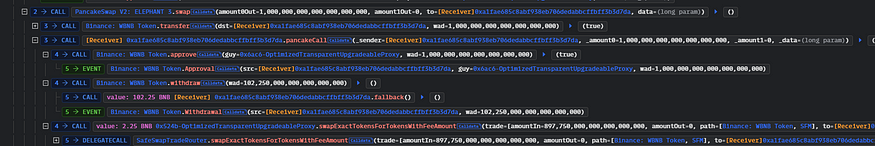
Burn Function Misuse: With the burn() function in the SafeMoon smart contract being inadvertently made public during a recent upgrade, the attacker leveraged this access control vulnerability. This function, which should have been restricted, was now exploitable by any external entity.
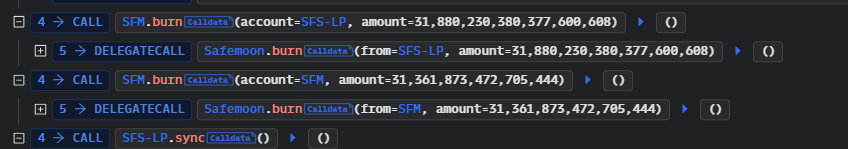
Token Inflation Mechanism: By burning a vast quantity of SFM tokens, the attacker artificially inflated the price of SFM tokens. This inflation was not due to organic market movements but a direct result of the reduced circulating supply caused by the unauthorized burn.
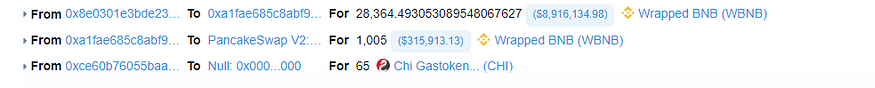
Conversion to WBNB: Capitalizing on the inflated SFM token value, the attacker quickly converted these tokens back into their WBNB counterpart. This conversion was calculated to extract maximum value based on the artificially spiked price of SFM tokens.
Withdrawal Phase:
Extraction of Funds: The final step of the attack was the withdrawal of around $9 million in tokens. This substantial sum represents the culmination of the attacker’s meticulously planned and executed exploit, leading to a significant loss for the SafeMoon ecosystem and its users.
MEV Bot Intervention
Front-running by MEV Bot:
- An unexpected turn in the attack scenario was the intervention of an MEV (Maximum Extractable Value) bot. This bot, known for its involvement in other high-profile hacks such as the Nuwa Exploiter and DBALL Exploiter incidents, front-ran the original attack transaction.
- Impact of MEV Bot: The involvement of the MEV bot added complexity to the attack’s dynamics, potentially altering the flow of transactions and the distribution of extracted funds.
Transaction Details
Key Transactions Involved:
Attacker’s address: https://bscscan.com/address/0x286e09932b8d096cba3423d12965042736b8f850
Attackers transaction: https://explorer.phalcon.xyz/tx/bsc/0x48e52a12cb297354a2a1c54cbc897cf3772328e7e71f51c9889bb8c5e533a934
Attacker’s contract: https://bscscan.com/address/0xa1fae685c8abf938eb706dedabbcffbff3b3d7da#code
Attackers message: https://bscscan.com/tx/0x7243d10c0241beee49ffc2bb118dc019c6f1af00c215ca5c55be4b303e237f07
MEV Bot Address: https://bscscan.com/address/0x286e09932b8d096cba3423d12965042736b8f850
Original attack txn (failed): https://bscscan.com/tx/0xbcf5e30c164837b5d7c42fd7e33e47a0072dc014e7f0a67aa7710af49d0ce53b
MEV Bot Attack txn: https://bscscan.com/tx/0x48e52a12cb297354a2a1c54cbc897cf3772328e7e71f51c9889bb8c5e533a934
Stolen Fund Details
The SafeMoon exploit resulted in the hacker draining nearly $9 million worth of SFM tokens from the liquidity pool. The subsequent movements of these funds were significant and carefully monitored.
Key Developments in Fund Movement:
Communication for Fund Return: On March 29, 2023, the exploiter indicated through a secure communication channel their intention to return the funds to the SafeMoon team.
Bug Bounty Arrangement: A 20% bug bounty, amounting to around $1.8 million, was agreed upon to be awarded to the hacker as part of the negotiation.
Agreement to Return Funds: The hacker agreed to return 80% of the stolen funds, valued at $7.1 million, as observed in on-chain data.
Transaction Details: The process of returning the funds and the agreement specifics were communicated via on-chain transactions on the Binance Smart Chain block explorer.
These developments show a unique instance in DeFi hacks where a significant portion of stolen funds was negotiated for return.
Hack Aftermath
The aftermath of the SafeMoon hack involved several crucial steps taken by the team and the community, along with legal implications.
Key Aftermath Developments:
Public Announcement: The SafeMoon team announced the attack on their Twitter account, informing the community about the impact on the SFM:BNB LP pool and assuring the safety of the DEX.
Legal Considerations: In a rare instance of legal leniency in DeFi hacking cases, SafeMoon developers confirmed that no charges would be filed against the hacker following the agreement for fund return.
On March 29, 2023, the exploiter communicated their intention to return the stolen funds. They were awaiting the establishment of a secure line of communication to facilitate the transaction back to the team.
https://bscscan.com/tx/0xf98a8b7e3ffee676f06f0c037141483ec2c9cf8753a57fbcdbd718590e4d77ff
Return of Funds: On March 30, 2023, SafeMoon responded to the exploiter, directing them to return the agreed funds to SafeMoon’s Treasury.
https://bscscan.com/tx/0x63939c2f2a63ab17d3c1f8d493ec80ad0410c69d76960bbb601acce54bf51f2c
SEC’s Involvement: Despite the negotiations and partial fund recovery, the SEC charged SafeMoon and its executives with fraud and securities violations, possibly due to insider activities related to the exploit.
Impact on Project: The attack and subsequent events significantly impacted SafeMoon, drawing attention to security needs and regulatory scrutiny in DeFi projects.
Lessons Learnt
Following are the key lessons that can be learned by analyzing the SafeMoon hack:
- Rigorous Smart Contract Auditing: Regular and thorough audits, especially post-contract upgrades.
- Access Control Checks: Ensuring strict access control mechanisms in smart contract functions.
- Monitoring for Unusual Activities: Implementing real-time monitoring systems to detect abnormal token transactions.
Conclusion
The SafeMoon hack serves as a stark reminder of the vulnerabilities inherent in the blockchain and DeFi sector, particularly highlighting the risks associated with smart contract upgrades.
The incident not only resulted in substantial financial losses but also drew legal scrutiny, emphasizing the need for stringent security protocols in the blockchain industry.
This situation underscores the essential role of specialized security firms like ImmuneBytes, whose expertise in smart contract auditing and security analysis could play a pivotal role in preventing similar incidents.
The SafeMoon exploit demonstrates that continuous vigilance, thorough contract audits, especially post-upgrade, and proactive security measures are not just best practices but necessities for maintaining trust and integrity in the rapidly evolving blockchain ecosystem.

