On October 6th, 2022, the $RES Token on the Binance Smart Chain suffered a flash loan attack, leading to a theft of roughly $290,000.
The attacker exploited a vulnerability in the thisAtoB function of the token’s smart contract, manipulated the pool price, and profited by swapping tokens.
This incident caused a severe 97% depreciation in the token’s value and emphasized the ever-present risks in the DeFi ecosystem, highlighting the urgency for enhanced security measures and continuous auditing.
Executive Summary:
Table of Contents
On October 6th, 2022, the $RES Token, a BEP20 token on the Binance Smart Chain (BSC), was subjected to a flash loan attack. This exploitation led to the theft of approximately $290,000.
Overview of $RES Token
$RES is a digital currency developed on the Binance Smart Chain platform, adhering to the BEP-20 standard. It participates in the growing DeFi ecosystem, enabling various financial transactions on the blockchain.
Flash Loan Attacks: A Primer
Flash loan attacks exploit the fundamental feature of smart contracts, wherein an attacker can borrow vast sums without collateral. They then leverage this to distort a crypto asset’s price on one platform, selling it off rapidly on another, typically for a profit.
Source of Vulnerability
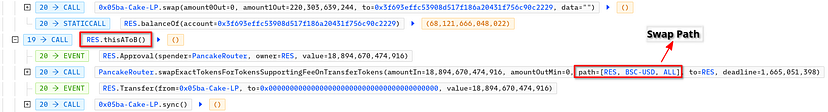
The primary point of exploitation was discovered in the thisAtoB function embedded in the contract. This specific function facilitated the conversion of $RES tokens into $ALL tokens, following the RES-BSCUSD-ALL route.
The Attack Mechanics
- The hacker began by transferring 0.5 BNB from an external source to their personal wallet.
- Exploits thisAToB function to internally call the _thisAToB function in order to convert $RES tokens to $ALL tokens.
- Executes flash loan attacks along with several swaps subsequently to accumulate $ALL tokens. These $ALL tokens were then incinerated using the thisAToB() function.
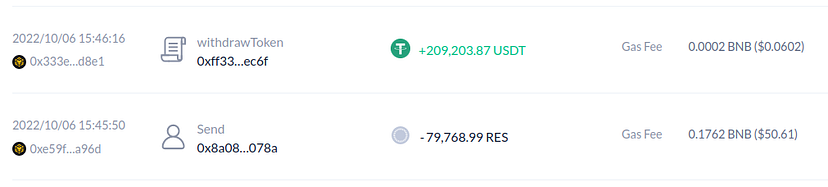
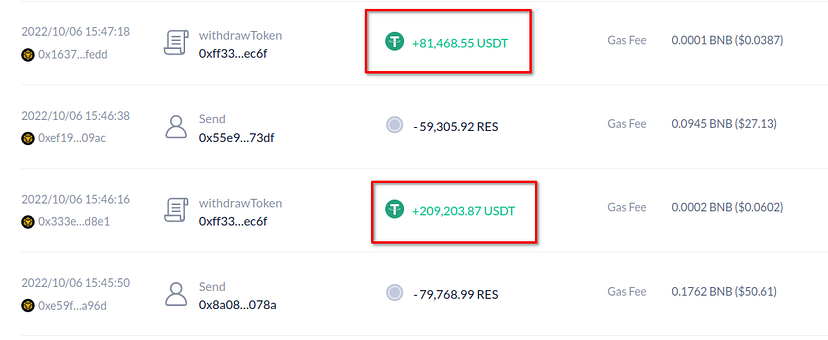
- This token burn escalates the reserve ratio of the pair. The attacker then proceeds to swap $ALL tokens for USDT, bagging a profit close to $209,203.
- The hacker repeats the aforementioned steps a number of times to further pocket $81,268, cumulatively stealing around $290,000.
Amount Stolen & Impact on Token Price
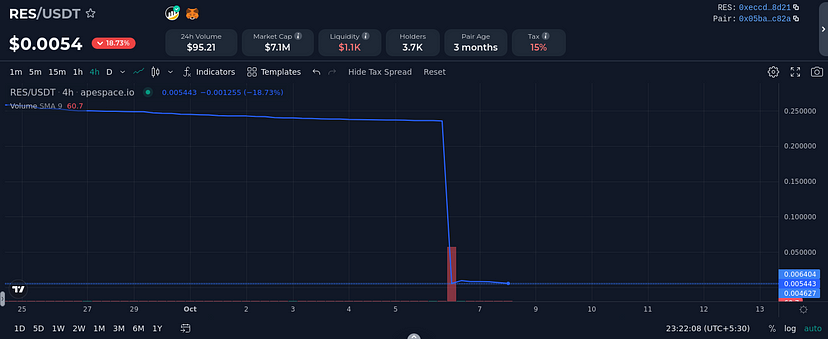
Following the attack, the $RES token’s valuation plummeted sharply, witnessing a 97% decline. From an initial price point of $0.23, it dwindled to a mere $0.0060.
Addresses and Transactions Involved
Attacker’s Address:
0x986b2e2a1cf303536138d8aC762447500Fd781c6
Contract Deployed for Attack:
0xff333de02129af88aae101ab777d3f5d709fec6f
Targeted ($RES) Contract:
0xeccd8b08ac3b587b7175d40fb9c60a20990f8d21
Transactions:
0xe59fa48212c4ee716c03e648e04f0ca390f4a4fc921a890fded0e01afa4ba96d
0xef19a4dfd69874d5efda3e38b5a19cae4e0b0bdc95769760bd85ede4d15609ac
Status of Stolen Funds
Post-theft, the attacker cleverly swapped the ill-gotten assets into diverse tokens like BUSD and BNB. Subsequently, all these funds were transferred to a new contract, viewable at: https://bscscan.com/address/0x5f330ba134051d247a6700babed73b587b75b21b
Preventative Measures
The surge in flash loan attack incidents within the DeFi ecosystem has prompted the development of robust countermeasures. Two prevailing solutions include:
Decentralized Pricing Oracles: This approach decentralizes the process of fetching and verifying external data, reducing the chance of price manipulation.
DeFi Security Firms: These firms audit, verify, and monitor smart contracts for any anomalies or vulnerabilities that can be exploited, ensuring safer DeFi interactions.
Conclusion
The flash loan attack on the $RES Token serves as a testament to the evolving threat landscape in the DeFi space. It underscores the need for rigorous security measures, continuous auditing, and a proactive approach to safeguard assets and maintain investor confidence.

