Coding smart contracts aren’t for the faint of heart!
Smart contracts are complicated and despite being around for only a short while, there’s surprisingly too much information on them on the internet, which can sometimes be overwhelming. Moreover, the number of smart contract breaches and hacks stand right atop!
Smart contracts are nothing but computer programs that, once triggered, do your job for you and make life easier!
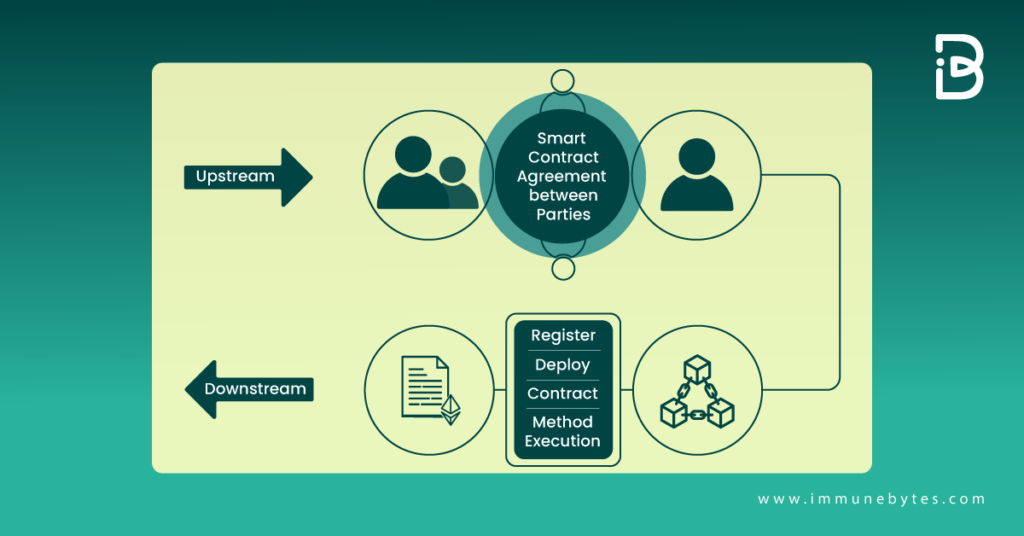
But for a computer program to not have any bugs and errors sounds downright fictitious.
Vulnerabilities in smart contracts have time and again caused the most enormous hacks in the history of blockchain and decentralized finance. So, what do you do to minimize the chances of your smart contract being struck by an asteroid-sized hack? You test!
In today’s article, we’re going to be talking about Smart Contract Fuzzing. A testing technique that is slowly gaining the popularity it deserves.

What is Smart Contract Fuzzing or Fuzz Testing?
Table of Contents
By definition, Fuzz testing or Fuzzing is a Black Box software testing technique, which basically consists of finding implementation bugs using malformed/semi-malformed data injection in an automated fashion.
It is the art of automatic bug detection. The aim behind implementing fuzzing is to stress the application and cause unexpected behavior, resource leaks, or crashes.
The Process of Smart Contract Fuzzing
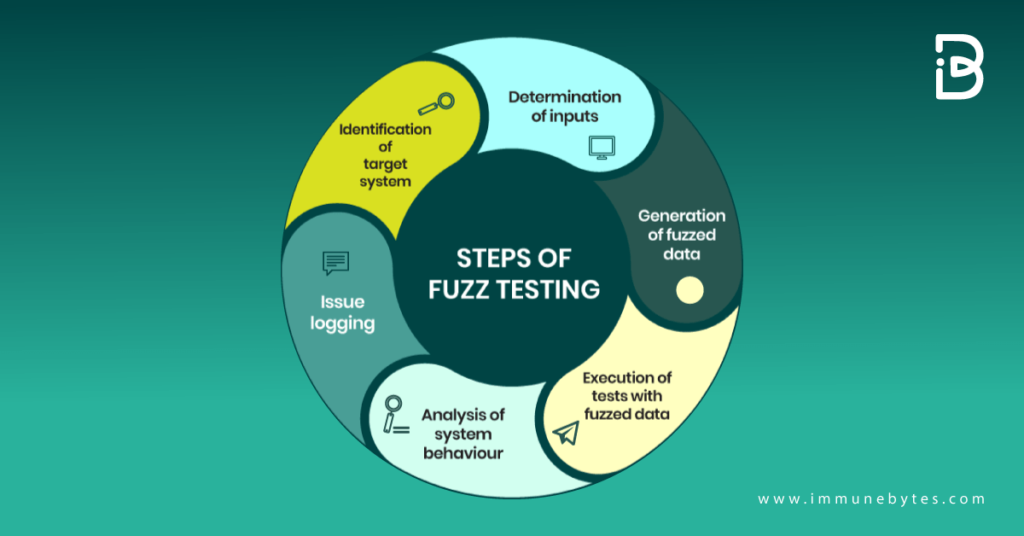
The process of Fuzzing involves throwing invalid, unexpected, or random data as inputs at a computer. Fuzzers repeat this process and monitor the environment until they detect a vulnerability.
Threat actors use fuzzing to find zero-day exploits ? this is known as a fuzzing attack. Security professionals, on the other hand, leverage fuzzing techniques to assess the security and stability of applications.
The purpose of fuzzing relies on the assumption that there are bugs within every program, which are waiting to be discovered. Therefore, a systematic approach should find them sooner or later.
Fuzz Testing Smart Contracts
Every smart contract goes through a security audit? or at least it should. And during the smart contract audit, most auditors analyze the codebase using some or the other automated testing tool. In the case of smart contracts, some of the Smart Contract Auditing tools are Manticore, Echidna, Mythril, Slither, and others.
A reason for using a fuzzer during an audit process is to find edge cases that couldn’t be found during/using unit or integration testing. However, using a fuzzer is not yet a common thing to do but it’s slowly gaining popularity.
Why is Fuzz Testing important?
If you aren’t Fuzz testing your smart contracts yet. Here are some reasons why you must!
- Fuzzing not only identifies a problem but also shows its cause and how an attacker may interact with it in a real-life attack.
- Fuzzing proves a vulnerability exists without having to sift through false positives.
- Fuzzing is fully automated and can run independently for days or even weeks, identifying as many vulnerabilities as possible in a system under test.
- Fuzzing is highly useful for developers. The role of developers is to develop and improve product features. While traditional security tools only point out flaws, fuzzers show the result of the flaw and demonstrate the impact of solving it.
Now that you’re convinced on why you should use it, let’s see how you can use Fuzzing!
How to Fuzz Smart Contracts?
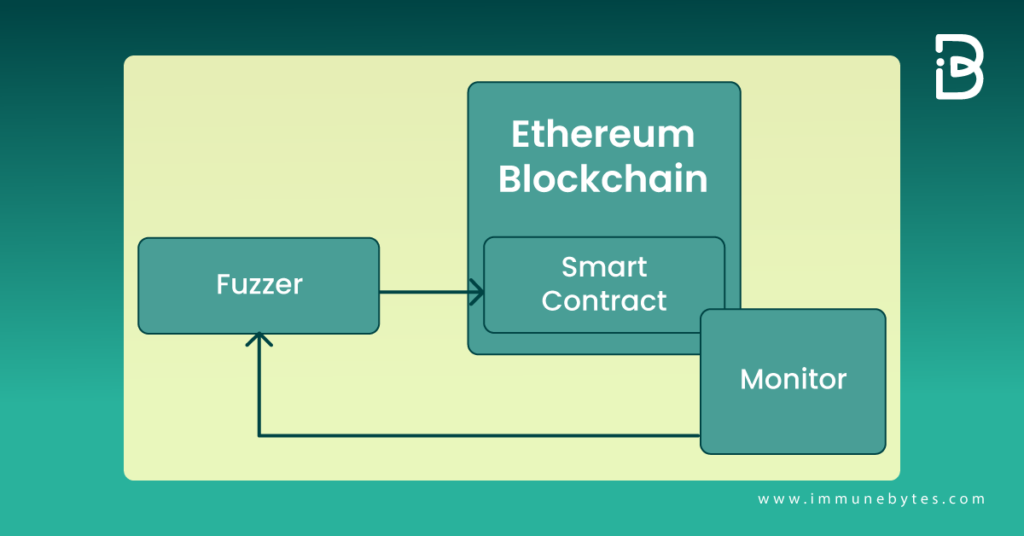
Smart Contract Fuzzing Tool Architecture
To start with Fuzzing, you will need to have a tool that can do that for you. There are a lot of them on the Internet to choose from. In this article, we’ll be using Echidna for reference.
Echidna is a Haskell program designed for fuzzing Ethereum smart contracts. It uses sophisticated grammar-based fuzzing campaigns based on a contract ABI to falsify user-defined predicates or Solidity assertions.
Now let’s get Fuzzing!
Step 1: Install Echidna. Alongside, you will also need to install cryptic-compile and slither.
Step 2: Code a Solidity contract with the invariants that you want to test.
Let’s take an example of this smart contract snippet with the muld() from DecimalMath.sol.
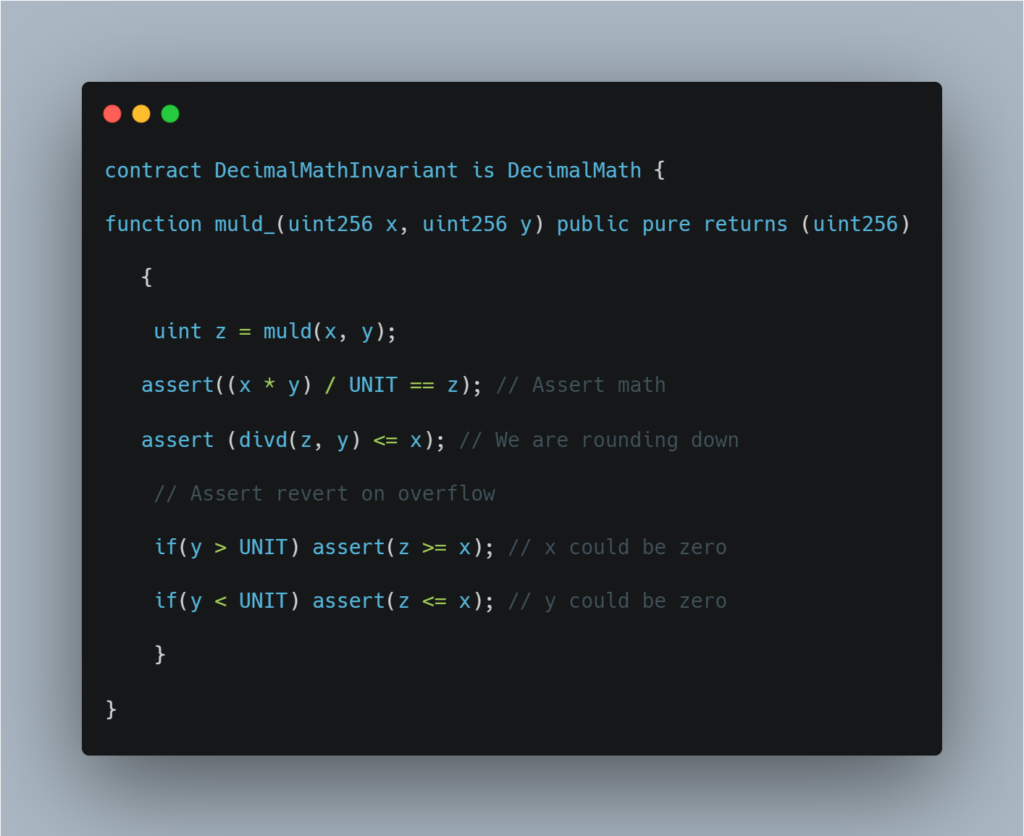
Step 3: Now, use echidna to call the DecimalMathInvariant.muld_ in this contract 20,000 times.
Echidna knows that it has to run this function because it is public. The function has two parameters (x and y), so the echidna will use random values on those for each run.
Step 4: You are ready to test now:
$ echidna-test. ? contract DecimalMathInvariant ? config contracts/invariants/config.yaml
Step 5: Echidna will spend some time analyzing the contract and getting set up, and eventually you’ll see this:
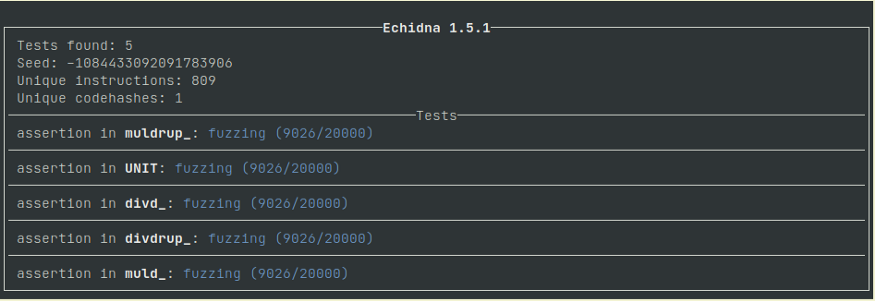
Note: For the functions that you do not wish to test, declare them as internal, and echidna will ignore them. Declare all state variables internal as well, or they will get uselessly fuzzed.
Step 6: It’s great if all the test cases passed. If not, it’s time to debug the fuzz.
When tests fail, Echidna finds a combination of function calls that makes an assertion failure.
It will then work out the shortest sequence that causes that failure, often bringing it down to one or two calls. Echidna will tell you if the function calls it executed.
And that’s it!
Once you know what the failing functions are in your code, fix them and fuzz again. Keep fuzzing until you’re satisfied with the results or until all the assertions are passing.
Final Thoughts
Fuzzing is not as simple as other testing methodologies present in the market, the tools are rough, and the math is hard, but it is worth it. A fuzzed smart contract will give you and your investors a greater level of confidence when on the mainnet. Relying just on unit testing anymore and poking around in a testnet seems reckless now.
At ImmuneBytes, we have adopted this new technology in our smart contract audits to ensure maximum efficiency and risk coverage. We leave no stone unturned in making your smart contract vulnerability-free!
Connect with the ImmuneBytes team to get audited at https://www.immunebytes.com/contact-us/
About Us
ImmuneBytes is facilitating blockchain security by employing the use of cutting-edge techniques on smart contracts and decentralized applications. We have a team of experienced security professionals who are adept at their niches and provide you with innovative solutions and consultation. So far we have worked on 175+ blockchain start-ups on different blockchain frameworks, with clients spread across the globe, and are continually unfolding ourselves to make this decentralized movement thrive.

