What comes to your mind when you hear “Blockchain”? Undoubtedly, the foundation of this concept is rooted in deep on the ideas of consensus, cryptography, and decentralization.
However, in today’s world, coming across several blockchain security issues is not something exceptionally uncommon. With so many advancements in blockchain technology, it has become quite natural to find blockchain vulnerabilities now and then.?
Initially, the application of blockchain was just in cryptocurrency. But with time, we can now find its application in many fields like healthcare, smart contracts, real estate, and more.
In this blog, we will try to give you a list of the privacy issues in blockchain that people face nowadays. Not just this, but our inventive team of experts at ImmuneBytes will also let you know how to prevent blockchain security issues.
Let us proceed.
What is Blockchain Technology?
Table of Contents
- 1 What is Blockchain Technology?
- 2 How Does a Blockchain Work
- 3 Are Blockchains Secure?
- 4 Notable Privacy Issues In Blockchain In The Year 2022
With blockchain technology, data is gathered and stored in groups called “blocks,” and each block has a maximum storage capacity. The brilliantly chosen word “blockchain” refers to the fact that when a block is complete, it is chained to the previous block, producing a data chain.
The technology has illustrated how security principles in money transfers and information transmission are changing. It offers a unique data structure in addition to integrated security measures.
If Blockchains are inherently secure, why do we encounter so many blockchain security issues? This question looms large in our minds.
Let us understand this imperative concept now.
Additional Resource: What is a Blockchain Security Audit?
How Does a Blockchain Work
A record-keeping system, blockchain technology makes it impossible to hack the system. This way, it makes it immutable.
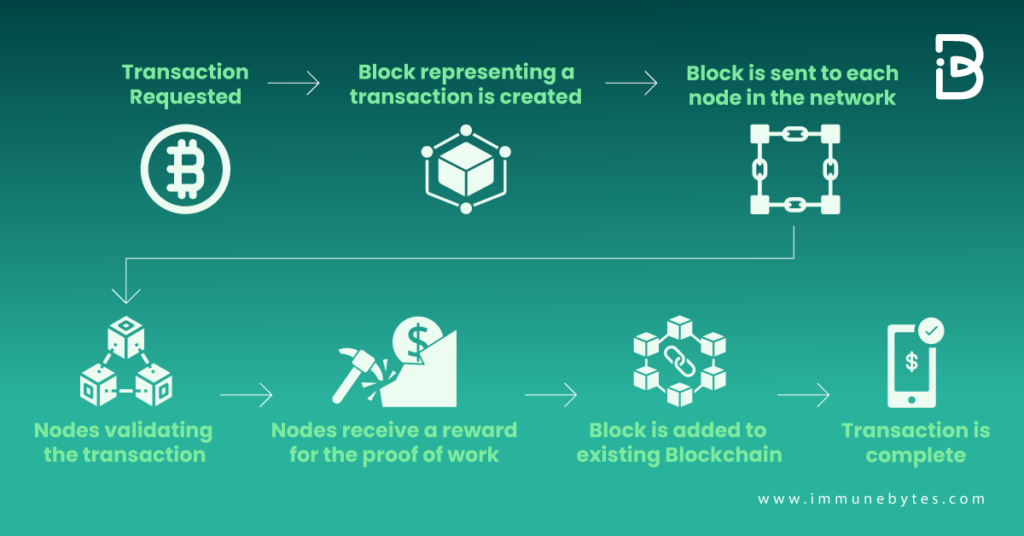
Blockchain operates through a multi-step process, which can be summarised as follows:
- An authorized participant enters a transaction, which the technology must authenticate.
- A block that reflects that particular transaction or piece of data is produced by that action.
- Every computer node in the network receives the block.
- Nodes validate the transaction.
- Nodes receive a reward for the proof of work.
- A block is added to the current blockchain after authorized nodes have verified the transaction.
- The transaction is completed when the update is delivered throughout the network.
These actions involve a variety of components and happen in almost real-time.
Are Blockchains Secure?
Before learning about the cryptocurrency security issues in the blockchain, let’s take a quick look at its components. The blocks comprise three essential pieces of information, including
- Transactional data, such as the time, price, and date of the purchase
- Hash or code specific to an algorithm distinguishes one block from others.
- The names of all parties involved in the transaction
Though the blockchains are secure, with the advancement of technology, hackers are trying their best to utilize their capabilities and make this blockchain world unsafe for users.
Now, we are ready to give you the list of the essential blockchain security issues, and don’t worry; we at ImmuneBytes won’t leave you without their solutions.
Recommended: Blokchain Security Audit Firm
Notable Privacy Issues In Blockchain In The Year 2022
It is not wrong to think that Blockchain technology is secure. However, We can also not neglect the other side. There are several drawbacks, too, when it comes to security.
So, without any further ado, let us get straight to the list of the top threats to blockchain security in 2022.
51% Attacks
Did you know in 2018, three renowned cryptocurrency platforms faced many security issues from 51% attacks? Those were Ethereum Class
For malevolent entities to achieve majority control over a blockchain’s hash rate, computing power is essential. Therefore, corrupted blockchains could lead to duplicate spending and transaction reversals.
How to Prevent 51% Attacks?
Now, it’s time that we help to let you know how to prevent 51% attacks. To do so, you should:
- Boost mining pool surveillance.
- Check that the hash rate is greater.
- Steer clear of proof-of-work (PoW) consensus techniques.
Phishing Attacks
Hackers most commonly use Phishing attacks as bait to trap people. They send fraudulent emails to the owners of the wallets and pose to be authentic and authoritative accounts. With the help of this scamming attempt, they try to get the users’ credentials.
Now that you know what phishing attacks are, you must also know how to prevent them.
How to Prevent Phishing Attacks?
You can prevent Phishing attacks by
- Install a trusted add-on to your browser to receive alerts about dangerous websites to increase browser security.
- Improve device security by installing malicious link detection software and dependable antivirus software.
- Confirm with the partner if you get an email asking for login information regarding the problem.
- Click on the link only after carefully reading it. Enter the address into your browser rather than clicking on any links.
- Stay away from open Wi-Fi networks when using an electronic wallet or conducting other crucial banking operations.
- Verify that your software and system are current.
Sybil Attacks
In Sybil attacks, hackers generate a wide range of fake network nodes. With those nodes, it becomes quite convenient for the hackers to get access to a majority of the consensus, and as a result, they can easily disrupt the transaction between the chains.
How to Stop and Prevent Sybil Attacks?
- Apply the suitable consensus algorithms.
- Keep an eye on how other nodes behave and look for any that only send blocks from one user.
- These algorithms make it impossible for the hacker to carry out these attacks, even though they might not prohibit them.
Routing Attacks
One of the most significant blockchain security issues has always been routing attacks.
Massive amounts of data move in real time within a blockchain network. This is where hackers take advantage of anonymity to intercept the data.
Most of the time, Blockchain users are unaware of the threat of a routing attack because all the processes and transactions occur as usual. The danger is that these attacks could regularly reveal private information or steal money without the user’s knowledge.
How to Prevent Routing Attacks?
So, the following are some strategies you can use to prevent these privacy issues in the blockchain.
- Put secure routing methods into practice (with certificates).
- Use encryption for data.
- Use strong passwords and change them frequently.
- Become knowledgeable about the risks of information security for you and your staff.
Blockchain Endpoint Vulnerabilities
Another very vital kind of security concern that people experience in blockchain security is this.
A network endpoint in the blockchain is the point where users get connected with the blockchain, be it on computers or smartphones.
Hackers can target devices and monitor user activity to steal the user’s key. One of the most apparent blockchain security problems is Blockchain endpoint vulnerabilities.
How to Prevent Blockchain Endpoint Vulnerabilities?
- Never store your blockchain keys in computer documents like Word documents, Notepad files, sticky notes, etc.
- Make sure to use a trusted encryption program if you want to store keys on a device.
- Eliminate the practice of distributing emails with keys in the message body and keeping draught emails. It is strongly encouraged to use the email capability included in the blockchain wallet if you want to share keys via email.
- Install an antivirus program for Windows and Android devices.
Private Key Security Attacks
Blockchain technology’s fundamental building block is public-key cryptography. Therefore, incorrect public-key cryptography implementation or management can lead to some significant blockchain security vulnerabilities.
If key signing is poorly implemented in a blockchain, the hackers can obtain the private key from the public key.
So, the question here is how to secure your private keys.
How to Prevent Private Key Security Attacks?
- Use a random password or key.
- Keep a check on your keys.
- Use an offline wallet.
Vulnerable Smart Contracts
Smart contracts are essentially contracted with blockchain record-keeping that is written in code.
For instance, if you lend someone money in real life, you will get periodic interest payments until the loan term is over, at which point you will receive your principal back.
This may now be done in code, substituting Bitcoin for actual money. The advantage is that you don’t need a mediator like a bank. The contract cannot be changed once it has been signed.
These contacts can, however, occasionally have lousy coding. This makes it possible for an attacker to identify and take advantage of potential code weaknesses.
SMART CONTRACT AUDITING SERVICES
How to prevent vulnerable smart contracts?
So, this is how you can prevent vulnerable smart contracts.
- Use industry best practices to create smart contract code that is more secure.
- Conduct recurrent penetration tests and smart contract security audit.
- A blockchain security checklist should be followed.
Additional Resources: Types of Smart Contract Vulnerabilities
While Blockchain has several security issues, experienced cybersecurity professionals can mitigate these issues within no time. In this blog, you might have learned about some of the strategies to use for preventing cryptocurrency security issues.
It might be argued that blockchain is a truly innovative technology that combines the rigorousness of coding with the process of consensus-building. A blockchain’s security depends on the programming that powers it.
Run extensive tests and audits for any blockchain security vulnerabilities before making your blockchain public. Your blockchain is increasingly vulnerable to attacks as its value rises in the marketplace.
Even though a blockchain security audit company may appear pricey, it is nothing in comparison to the costs you can incur if your blockchain-based service is the victim of an unlucky attack. Your blockchain won’t become obsolete in the future with the help of routine, in-depth security audits and pentesting, and you will easily be able to prevent blockchain security issues.