A recent report says that the longest DDoS attack in history occurred in the year 2019 which lasted for 509 hours!
Amazon stated that it was compelled to repel a 2.3 Tbps DDoS assault in the first quarter of 2020. This is significant for a number of reasons. For one, it is the biggest documented assault in history, with over four times the throughput of the previous record-holder (587 GB/s).
Now, it is quite obvious to be curious to know about this type of cybersecurity attack.
This blog would focus on DDoS attacks and several other things related to this type of attack. So, let us begin!
DDoS Attack Stats that you Might Not know!
Table of Contents
Initially, DDoS attacks were seen as minor nuisances by novice attackers who didn’t have any motive to harm the user. Unfortunately, in today’s time, this has become a menace to society, wherein attackers aim to trouble the users a lot with this cyberattack.
Distributed Denial of Service (DDoS) has impacted the entire IT industry, rising with each passing day. According to InfoSecurity Magazine, there were 2.9 million DDoS assaults in the first quarter of 2021, a 31% increase over the same time in 2020.
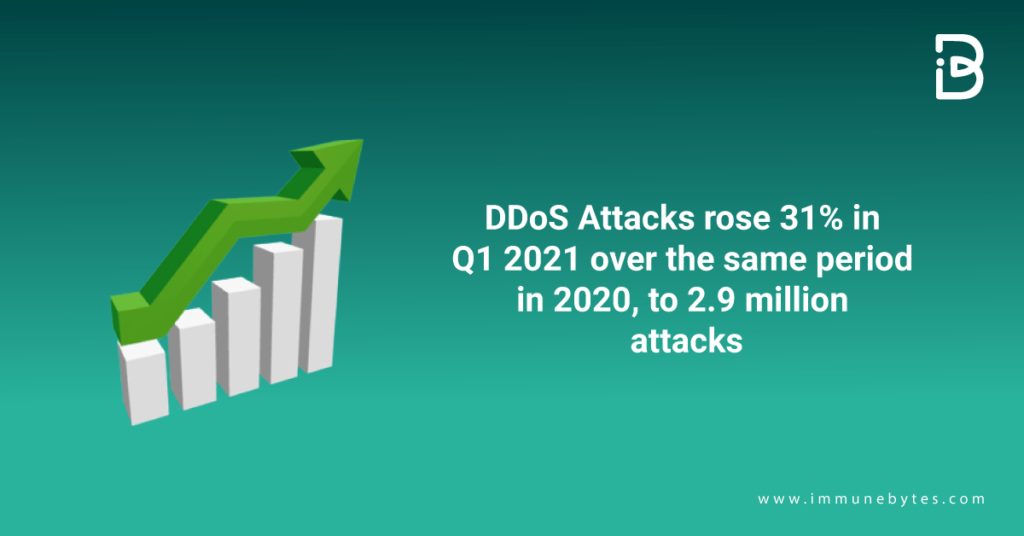
Source: https://www.comptia.org/content/guides/what-is-a-ddos-attack-how-it-works
In the graph above, you can see the exponential increase in distributed denial of services attacks. Imagine how incapacitated the businesses would have been with this situation!
These are some of the stats that demonstrate this point more clearly.
- Amazon Web Services (AWS) came across a DDoS attack in February 2020. It was such that it had occupied the response team for quite some days that, in turn, affected customers worldwide.
- EXMO Cryptocurrency exchange also came across a DDoS attack in February 2021. Because of this cyber attack, the entire organization turned inoperable for about five years.
- Recently, there was a sustained, state-sponsored DDoS attack in Australia.
- In Belgium, there was a DDoS attack that targeted the parliament of the country, universities, as well as police services.
What is a DDoS Attack?
Though these attacks have become so common, it is not easy to combat them. So, what is it?
DDoS, Distributed Denial of Service, is a type of attack in which the threat actor uses a wide range of resources from multiple remote locations to threaten an organization’s online operations. This focuses on generating attacks that impact the smooth working of services and networking equipment.
There is an interruption in the services; wherein the resources are sent HTTP floods. So, the normal working of the network equipment gets hampered, and the targeted organization gets cut off from legitimate users.
DDoS Attacks are one of the top four cybersecurity threats, which include:
- Social Engineering
- DDoS attacks
- Supply chain attacks
- Ransomware
How Does a DDoS Attack Work?
Often, people get perplexed by the difference between DDoS attacks and other cybersecurity attacks.
The expected behavior between network devices and servers is targeted in such attacks. Or in other words, the networking devices that establish a connection to the internet are targeted. So, rather than focusing on individual services, the attackers focus mainly on the edge network devices such as switches, routers, etc. It overwhelms the bandwidth or the devices that provide it.
Let us understand this better. Imagine many people calling you at the same time so that you can’t use your phone. This problem will go on until you block those numbers through your provider.
In this situation, you didn’t do anything with your mobile device; instead, you worked on the connection with the help of your phone provider’s blocking service.
Similarly, you do not modify the resources when you encounter a DDoS attack. Instead, you apply some fixes between the threat actor and your network.
Recommended: Blockchain Security Audit Company
Difference between DoS and DDoS
People often confuse DoS (Denial of service) and DDoS (Distributed denial of services).
Interestingly, there are significant differences between the two. Let us discuss them in detail.
| Denial of Service Attacks | Distributed Denial of Service Attacks |
| Focuses on individual servers or endpoints rather than the entire network. | Uses multiple, distributed devices for flood attacks. |
| Can be waged by single or multiple attackers. | Targets devices or protocols that connect the network to the internet. |
One common thing in both of these is that they both use bogus or sometimes floods of traffic to overwhelm devices.
Types of DoS attacks
Following are the three types of Denial of Service attacks:
Single-source SYN floods
This happens when an attacker exploits a single machine to launch a flood of SYN packets while manipulating the standard TCP three-way handshake. For example, an SYN flood generated by a Kali Linux machine is not a legitimate DDoS assault because the attack originates from a single device.
This holds even if the attacker employs IP address spoofing. An actual DDoS assault is initiated by network-level devices and is directed at network-level devices. To attack a network, you use numerous routers or Memcached servers.
The “ping of death.”
Some years back, some network drivers featured defective code that would cause a system to crash if it received an ICMP packet with specific parameters.
The slow Loris attack
This is often referred to as a DDoS attack, but since only a web server is attacked in this and not the networking devices, this falls under the category of a traditional DoS attack.
Types of DDoS attacks
Following are the four types of DDoS attacks.
Application Layer Attacks
In this, the attacker targets the software which provides different services like Apache Server. Among all other DDoS attacks, this is the most common one, called Layer 7 attacks.
Below is an example of such a DDoS attack.
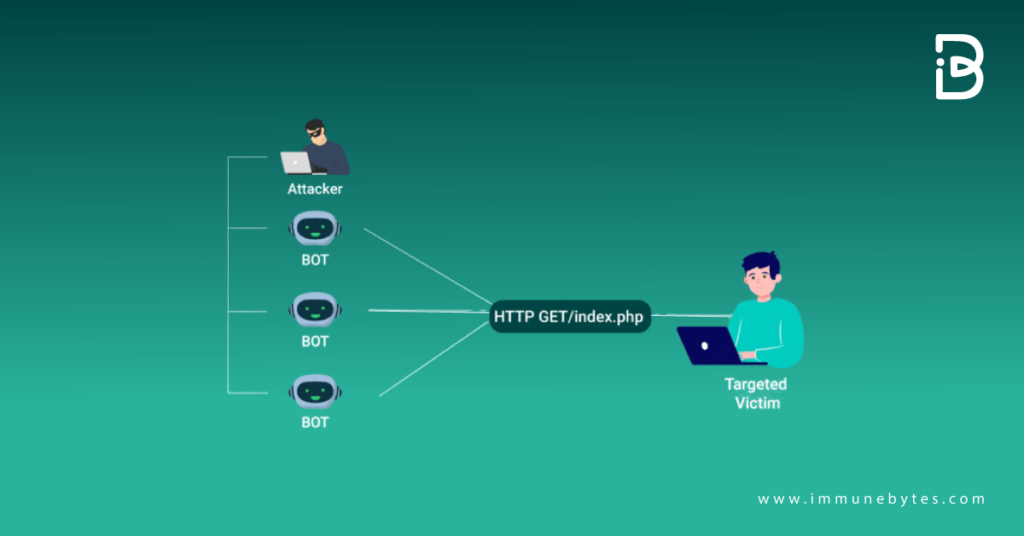
Source: https://www.cloudflare.com/learning/ddos/what-is-a-ddos-attack/
Protocol Attacks
These attacks frequently entail traffic manipulation at OSI/RM layers 3 and 4. This occurs when an assault depletes virtual servers’ resources and network-based devices, such as a server’s operating system or firewalls. Balancers are loaded while those resources are overburdened.
This is an example of a protocol attack.
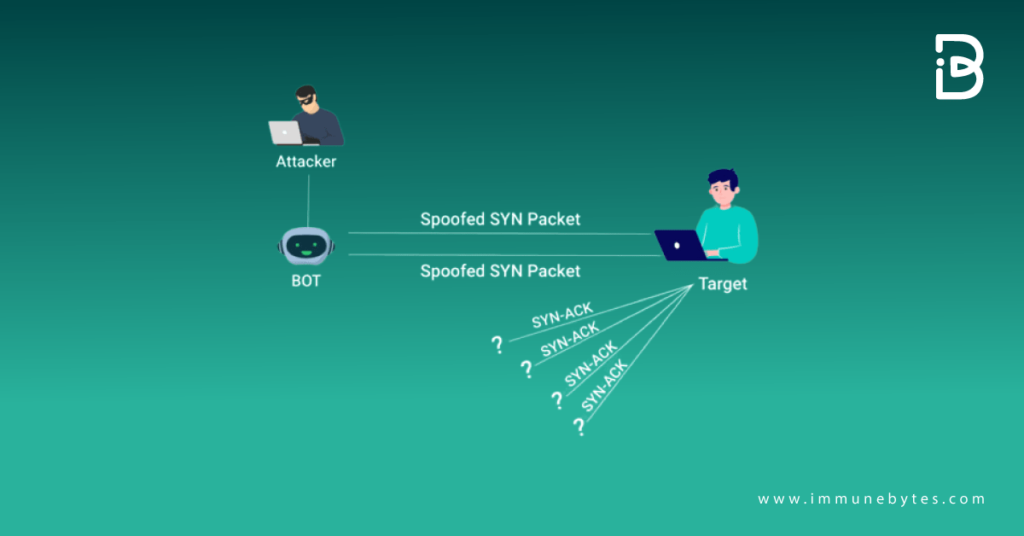
Source: https://www.cloudflare.com/learning/ddos/what-is-a-ddos-attack/
Volumetric Attacks
Volumetric DDoS attacks use incredibly high amounts of malicious traffic to exceed internal network capacity and even centralized DDoS mitigation scrubbing facilities. These DDoS attacks seek to drain bandwidth within or between the target network/service and the rest of the Internet.
Large volumes of data are transmitted to a destination via amplification or another method of producing large traffic, such as botnet requests. This is why they are also known as amplification attacks.
Here is an example of a volumetric attack.
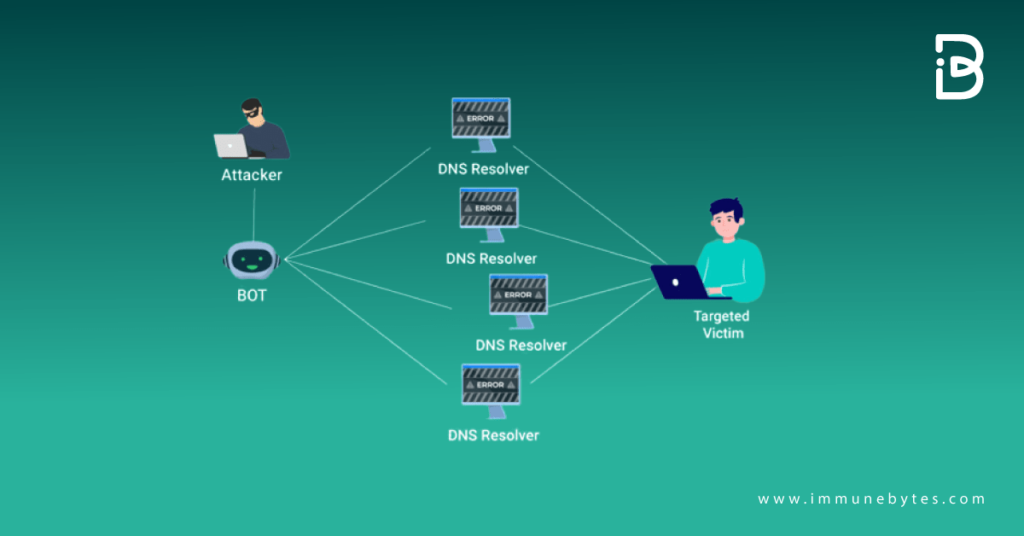
Source: https://www.cloudflare.com/learning/ddos/what-is-a-ddos-attack/
DNS Amplification
A DNS amplification is like calling a restaurant and saying, “I’ll have one of everything. Please call me back and repeat my entire order,” but the callback number belongs to the victim. A lengthy answer is created and emailed to the victim with no effort.
The target IP address receives a response from the server after sending a request to an open DNS server with a faked IP address.
How to Prevent Service DDoS Attacks?
Despite knowing what these attacks are, it becomes pretty tedious to avoid them as detection is a big challenge. The main reason behind this is that the symptoms are not very different from the typical service issues like web pages loading slowly, etc. In addition, the complexity level of DDoS attacks grows exponentially.
Furthermore, many businesses appreciate increased internet traffic, notably if the company has recently launched new products or services or released market-changing news. As a result, while prevention is not always feasible, an organization should prepare for when these assaults occur.
How to mitigate HTTP floods?
An organization has a vast range of options to mitigate the effects of the attack involved in DDoS. Following are the three most commonly used methods.
Risk Assessment
Organizations should regularly conduct risk assessments and audits on their devices, servers, and network. While it is difficult to avoid a DDoS, a detailed understanding of the organization’s hardware and software assets’ strengths and vulnerabilities can help.
Recognizing which technique to execute to mitigate the damage and disruption that a DDoS attack might inflict requires understanding the most vulnerable areas of an organization’s network.
Black Hole Routing
It is an excellent defense method; wherein either the network administrator or the service provider of the organization is responsible for creating a black hole route, and this way, the traffic is pushed into the black hole. Whether it is the good or the bad traffic, everything gets routed and dropped from the network. However, this can also be sad news for the business as legitimate users are turned down while turning down fake connection requests.
Firewalls
Some businesses use a Web Application Firewall to mitigate the impact of an application-layer or Layer 7 assault (WAF). A WAF is a reverse proxy appliance that lies between the internet and a company’s servers. An organization, like any other, can define a set of rules to screen requests. They can begin with one set of rules and then adjust them based on what they notice as patterns of suspicious DDoS behavior.
An anycast network can be used to scatter all the infected traffic across the web. The network uses only valid traffic, and it becomes easier to manage.
Wrapping up
A Distributed Denial of Service (DDoS) attack differs from traditional cyberattacks, which is why people often get confused with it or do not recognize them. If not taken measures properly, an organization can also lose its hard-earned, valuable traffic due to this attack.
Therefore, the hour’s need is to find robust solutions to mitigate these attacks. Get in touch with us for more information about such cybersecurity threats and attacks.
Additional Resource

