Overview
Table of Contents
On February 2, 2022, at 5:58 PM +UTC, Wormhole Bridge on Solana was exploited for ~$320 million due to smart contract vulnerability. These malicious actions resulted in one of the most significant cryptocurrency thefts in DeFi history, leading to the loss of approximately 120,000 Wormhole Ethereum (WeETH) tokens, valued at over $320 million.
Hack in a Nutshell
- Before initiating the attack, the assailant received 0.94 ETH from Tornado Cash, a privacy-focused Ethereum mixer, to facilitate the payment of transaction fees associated with their subsequent actions.
- An additional 0.1 ETH was transferred to an address associated with a prominent international cryptocurrency exchange.
- During the exploitation phase, the attacker manipulated the verification process by introducing a counterfeit Sysvar account, allowing them to create a fraudulent “message” requesting the minting of 120,000 wETH.
- By invoking the “complete_wrapped” function with this malicious “message,” the attacker successfully minted 120,000 wETH tokens.
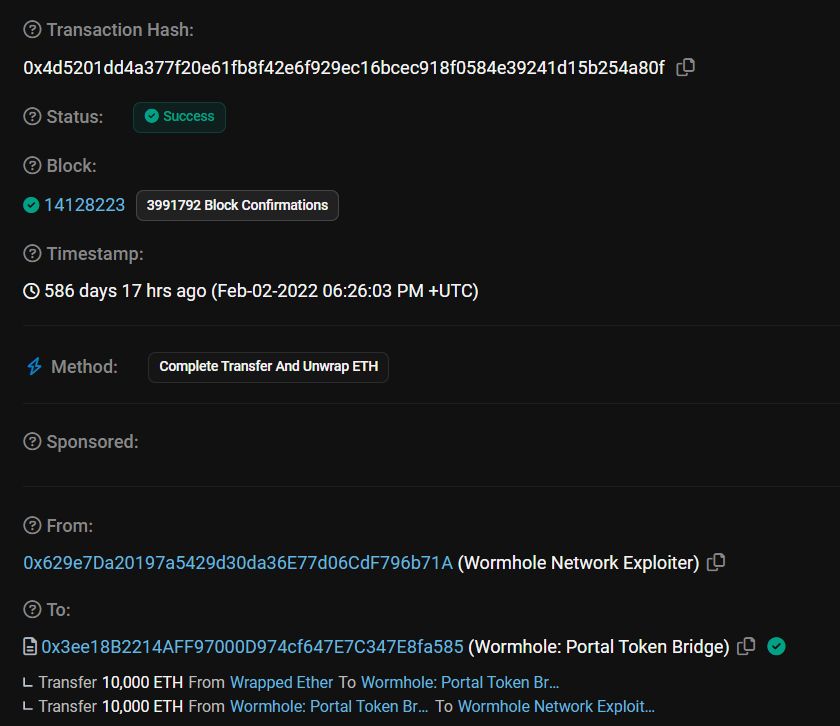
- Shortly thereafter, the assailant executed a transaction, bridging 10,000 ETH to the Ethereum blockchain, followed by another transaction involving 80,000 ETH roughly 20 minutes later.
- As of the present, the ill-gotten assets remain within the attacker’s control, with primary addresses being Account CxegPrfn2ge5dNiQberUrQJkHCcimeR4VXkeawcFBBka and 0x629e7Da20197a5429d30da36E77d06CdF796b71A, among others.
- Wormhole acknowledged the security breach on the day of the incident through their official Twitter account.
- On February 3, 2022, Jump Trading, the parent company of Wormhole, attempted to reach out to the attacker by offering a $10 million bounty in exchange for the return of the stolen assets. Unfortunately, this offer was met with silence.
Attack Technical Analysis
The attacker meticulously executed a series of steps to exploit vulnerabilities within the Wormhole bridge’s verification process:
Step 1: Spoofed “verify_signatures” Function
- The attacker initiated the attack by invoking the “verify_signatures” function. This function is integral to the verification process and plays a critical role in ensuring the authenticity of transactions.
- Within this function, a malicious “Sysvar account” was introduced to deceive the system. You can view the transaction here: (https://solscan.io/tx/25Zu1L2Q9uk998d5GMnX43t9u9eVBKvbVtgHndkc2GmUFed8Pu73LGW6hiDsmGXHykKUTLkvUdh4yXPdL3Jo4wVS).
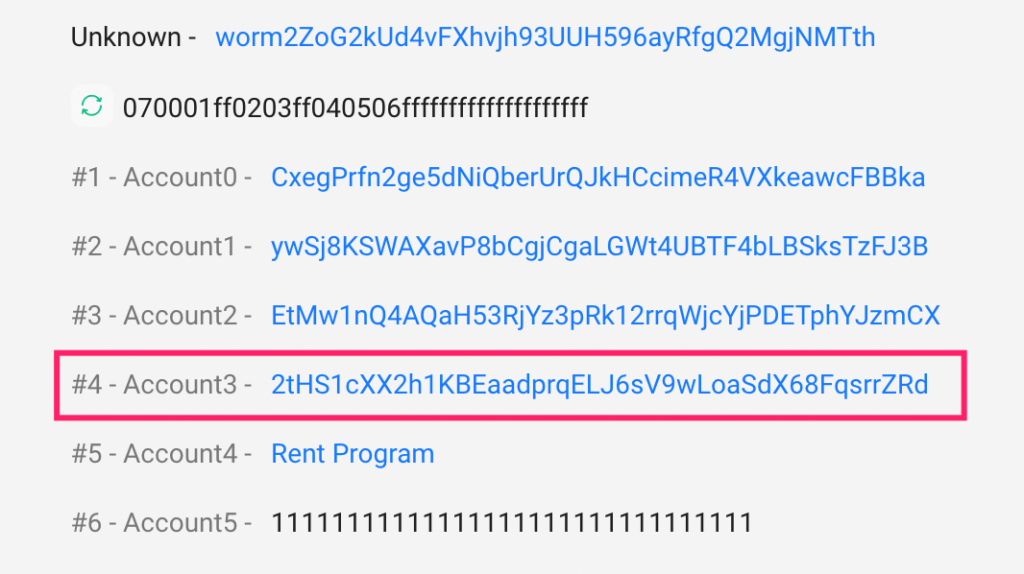
Step 2: Counterfeit “verify_signatures” Function
- The attacker employed a counterfeit “verify_signatures” function with the injected malicious “sysvar account.” This deceptive function aimed to subvert the verification process and grant the attacker unauthorized access.
- A genuine “verify_signatures” function with a legitimate “Sysvar account” is shown for reference.
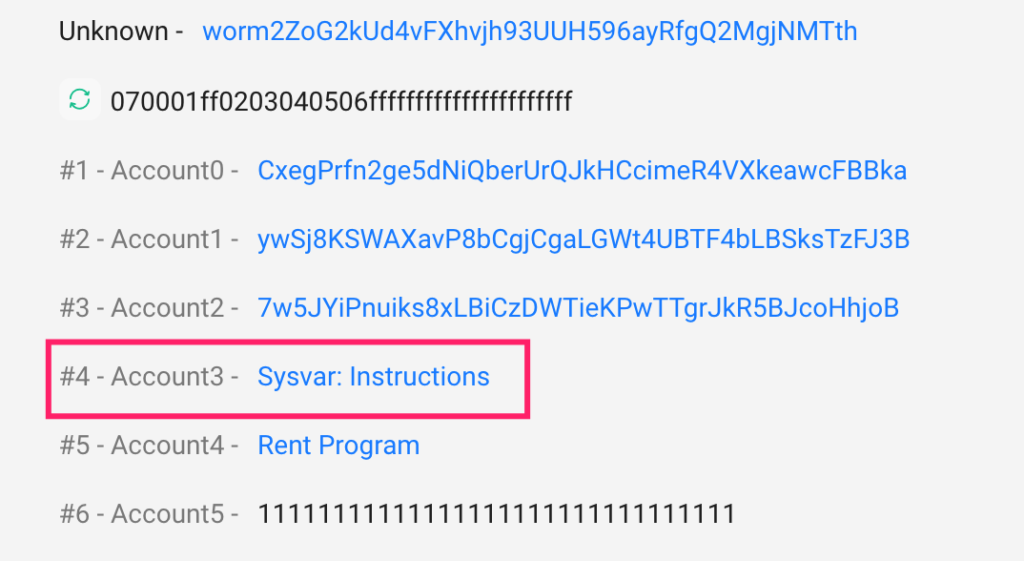
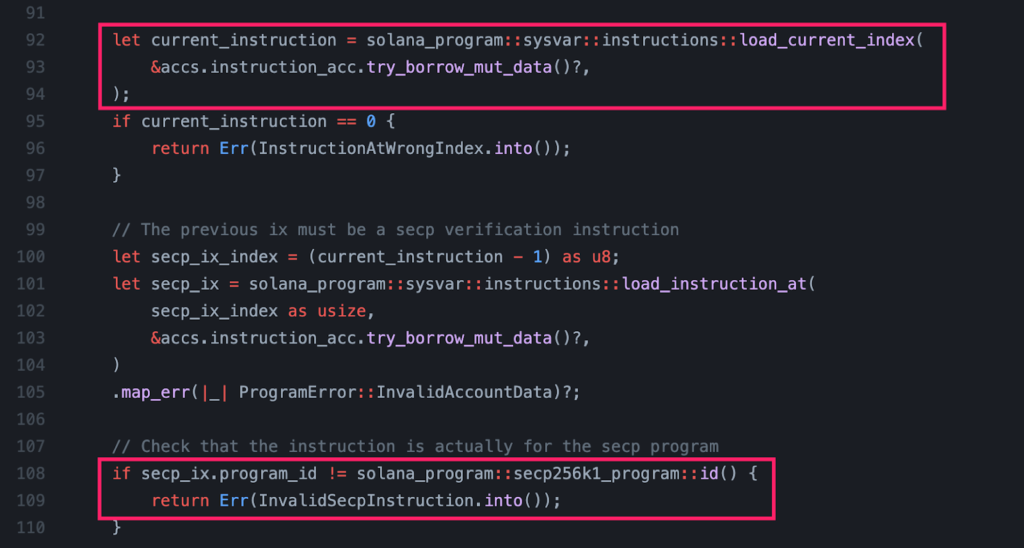
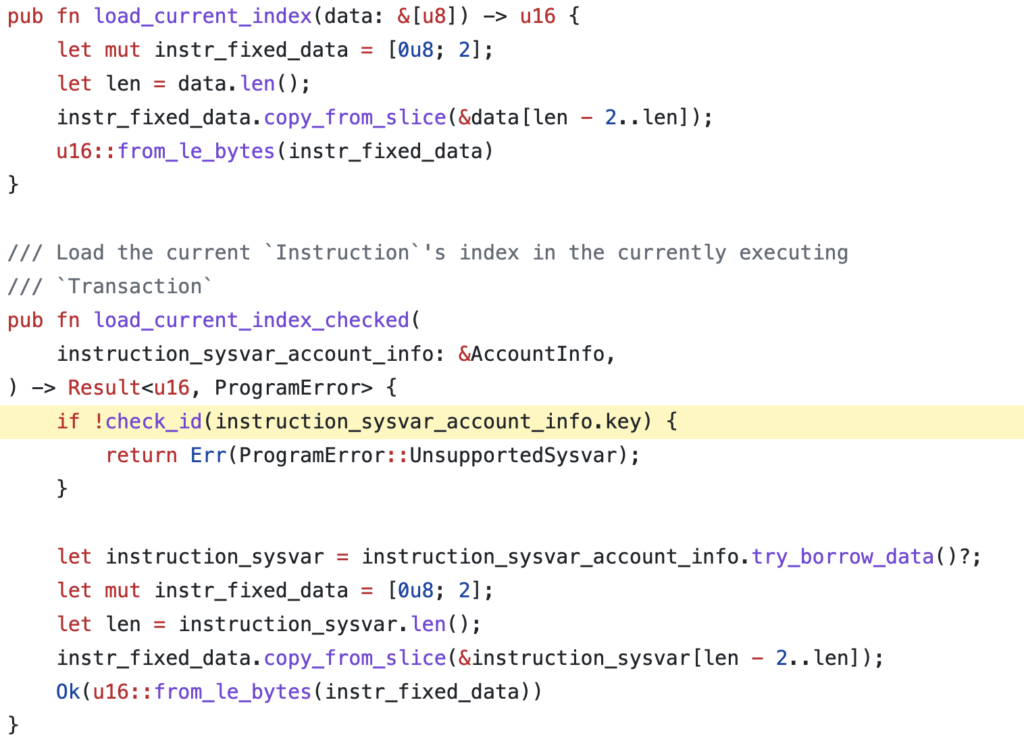
Step 3: Exploiting “load_current_index” Vulnerability
- Within the legitimate “verify_signatures” function, the system typically loads the current instructions from the Sysvar, specifically at instruction L92.
- However, a critical vulnerability was exposed in the function “load_current_index.” This vulnerability failed to validate whether the injected “Sysvar account” corresponded to the authentic “system sysvar.”
- As the current instruction (L92) retrieved from the “sysvar” was under the attacker’s control, it enabled the attacker to manipulate the verification process with impunity.
Step 4: Malicious “post_vaa” Function
- With the verification process compromised, the attacker proceeded to invoke the “post_vaa” function using the verified signatures obtained in the previous step.
- Within this action, the attacker created a malevolent message account specifying the minting of 120,000 wETH. The transaction can be viewed here: (https://solscan.io/tx/2SohoVoPDSdzgsGCgKQPByKQkLAXHrYmvtE7EEqwKi3qUBTGDDJ7DcfYS7YJC2f8xwKVVa6SFUpH5MZ5xcyn1BCK).
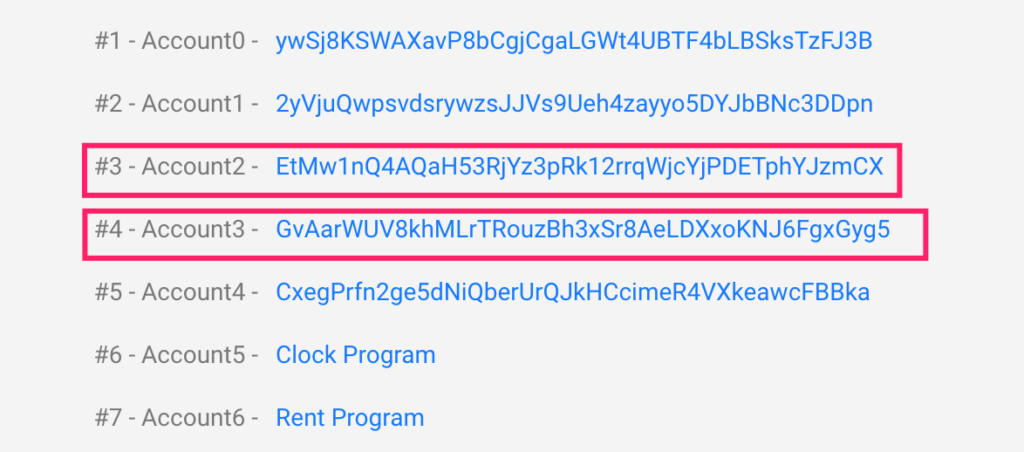
Step 5: Executing “complete_wrapped” Function
- Building on the foundation established in the previous steps, the attacker proceeded to invoke the “complete_wrapped” function.
- This function processed the data contained within the malicious message account created in the “post_vaa” step, culminating in the minting of 120,000 wETH tokens. The transaction details can be found here: (https://solscan.io/tx/2zCz2GgSoSS68eNJENWrYB48dMM1zmH8SZkgYneVDv2G4gRsVfwu5rNXtK5BKFxn7fSqX9BvrBc1rdPAeBEcD6Es).
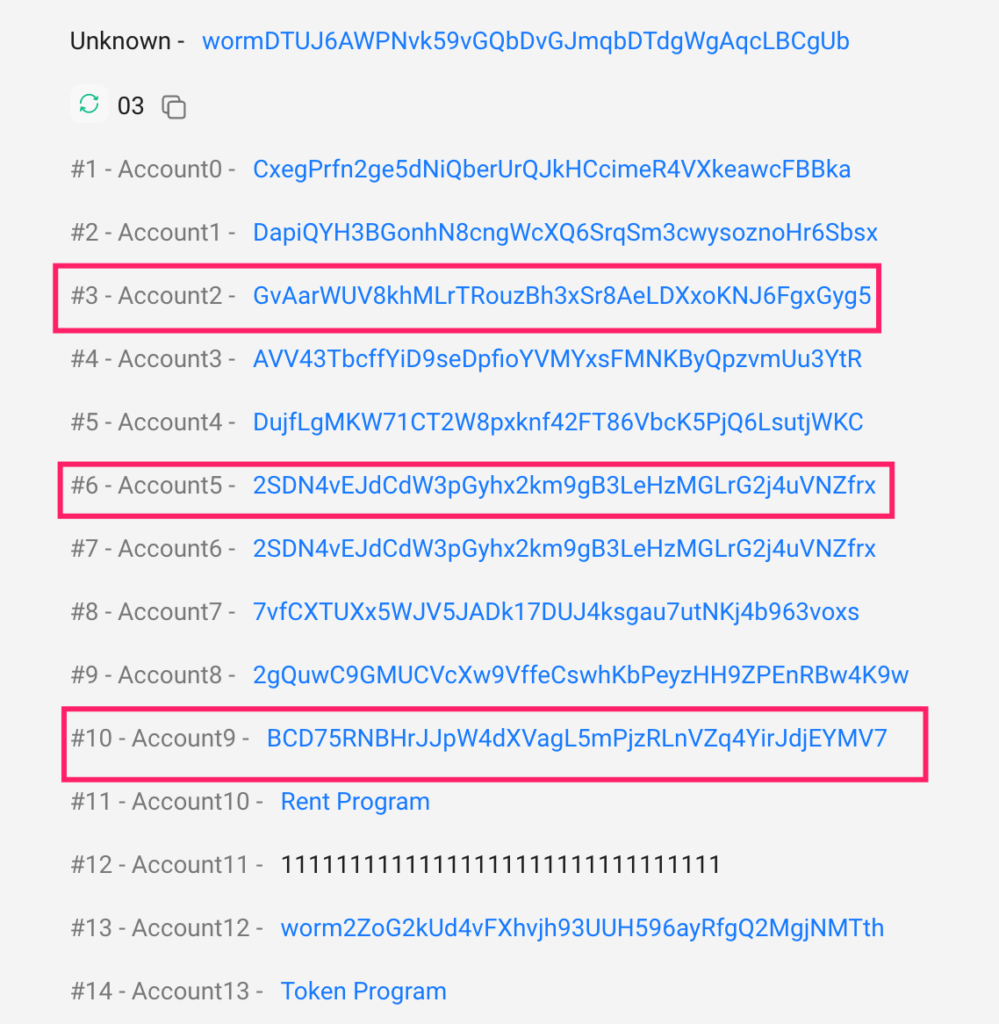
Step 6: Asset Movements
- Following the minting of wETH, the attacker orchestrated a series of asset movements:
- Some of the minted wETH tokens were transferred to the Ethereum blockchain.
- The remaining wETH tokens were exchanged for USDC and SOL on the Solana blockchain, utilizing various transactions:
- https://solscan.io/tx/j3jUDG43di8Dsg7Q3jQhstamtBovu1GLqnDJ7yNvM3r4pnK9e7uqgt9uBobCjT5S1BKhZZFQNQwDxypEYqLknec
- https://solscan.io/tx/5UaqPus91wvAzKNve6L8YAHsESomZQ7GWi37gPFyzTHcXNMZA641bb8m8txo7bS7A5cAnzKDKYyiKcQC8GgDcAuf
- https://solscan.io/tx/3AugXqrXunBa96YfqENhPBiWZWpnSnJdqAHS64qcHTVU9KtfGon8cN9cUuXsDmBobBBXjYUtuRxnYxgERS42nh6G
- https://solscan.io/tx/2SndtH3tU4j6v14HJzEde3d3dnpdHqTPn4VnvhTj4zKLo26H5kmtCwjn2nANfjXNVbmFsyEGtD4Jte25azsPwaRk
Contract Vulnerability Analysis
The underlying cause of this exploit can be attributed to a critical oversight within the verification process, specifically within the “verify_signatures” function. The flaw resided in the usage of the deprecated function “load_current_index” which failed to validate the authenticity of the provided “sysvar account.” Consequently, the attacker could manipulate this critical account, enabling the successful execution of the exploit.
Fund Movement
- The stolen assets include 432,662.14 SOL, 93,750 ETH, and 1444.16 USDC.
- Key attacker-controlled addresses encompass CxegPrfn2ge5dNiQberUrQJkHCcimeR4VXkeawcFBBka and 0x629, collectively holding assets valued at approximately 297.6 million USD.
Attacker Accounts Holding Assets
- SOL Account (CxegPrfn2ge5dNiQberUrQJkHCcimeR4VXkeawcFBBka):
- Holds 432,662.14 SOL valued at $46,649,632.46.
- Ethereum address: 0x629e7da20197a5429d30da36e77d06cdf796b71a.
- Total assets held: Approximately 297.6 million USD.
Assets Transfers
- 1444.16 USDC were sent to DiLuXdZ5TbQ1jUNEF6tNstHNqXJ3mTCrsVrM6DeX18Mh
Txn: https://solscan.io/tx/29Rb5q5hYb2bxMKNeT2jkJ4WLqgGWqYmA8aNvrE5vG8BTtHMUDesxbyGMcmGaZj3tqXDacPQAQkPbz1kaF5fYer6 - 16879.39 ETH was converted to 269,356.66 SOL.
Txn: https://solscan.io/tx/2SndtH3tU4j6v14HJzEde3d3dnpdHqTPn4VnvhTj4zKLo26H5kmtCwjn2nANfjXNVbmFsyEGtD4Jte25azsPwaRk - 1866 ETH was exchanged for 4.9 million USDC.
Txn: https://solscan.io/tx/29Rb5q5hYb2bxMKNeT2jkJ4WLqgGWqYmA8aNvrE5vG8BTtHMUDesxbyGMcmGaZj3tqXDacPQAQkPbz1kaF5fYer6 - 7504 ETH was swapped for 18 million USDC.
Txn: https://solscan.io/tx/4ZYmPrwPUXfyUqp4GAh6thxe8TM8rJ5JEC7ns7nhE6Jeq4dbp3PpLem1TX6b4Ntg3fPF5gU7ZDYvXkQQcsj3RyvC - 18,044,852.11 USDC was converted to 122,049 SOL.
Txn: https://solscan.io/tx/2wor1JjWFLLwgzVgjREXbHDk9HVkPAnY5xjWnVKRK18hvkFtSw9KkmdQyUbWdSQu8KTTMv43x7VWpA1527zQjArH
Attacker Accounts on Solana
- The account responsible for minting 120,000 Ether (Wormhole) is 2SDN4vEJdCdW3pGyhx2km9gB3LeHzMGLrG2j4uVNZfrx.
- Account CxegPrfn2ge5dNiQberUrQJkHCcimeR4VXkeawcFBBka created the above account.
Source of the First Transaction Fees
- The transaction fees for the initial attack were sourced from Account 2ojv9BAiHUrvsm9gxDe7fJSzbNZSJcxZvf8dqmWGHG8S.
Txn: https://solscan.io/tx/mHJoRkfJGiUy54LQjRtMBd8pz82GgZmDVx8jVzXWVkzpg7JUT3EDb4BEBq8HcYZ15HjRUojoroMpYs7KBCYyzE9
Similar Incidents
- A notable cross-chain bridge attack targeted the Harmony network, where an attacker took control of a MultiSig Wallet to authorize the transfer of 13,100 ETH to their own address.
- An earlier attack on the Qubit network resulted in an $80 million theft. In this instance, the attacker manipulated the QBridge contract to mint 77,162 qxETH on the target blockchain.
Conclusion
The Wormhole bridge exploit can be attributed to the oversight in validating “guardian” accounts, ultimately allowing the attacker to mint 120,000 wETH tokens without proper backing.
This incident underscores the critical importance of fortifying security measures within DeFi protocols and cross-chain bridges. Always get your projects audited by Top leaders like Immunebytes to avoid loss of funds and reputation.

