Introduction
Table of Contents
On March 13th, 2023, Euler Finance, a decentralized finance (DeFi) lending protocol on the Ethereum blockchain, fell victim to a substantial flash loan attack. This report provides an in-depth analysis of the exploit, the vulnerabilities exploited by the attacker, the consequences of the attack, and the subsequent responses from the Euler Finance team.
Euler Finance Overview
Euler Finance is a pioneering lending protocol that leverages mathematical principles to create high-performance, non-custodial protocols on Ethereum and other blockchain platforms. Its architecture facilitates the lending and borrowing of cryptocurrencies in a decentralized environment.
Exploit Description
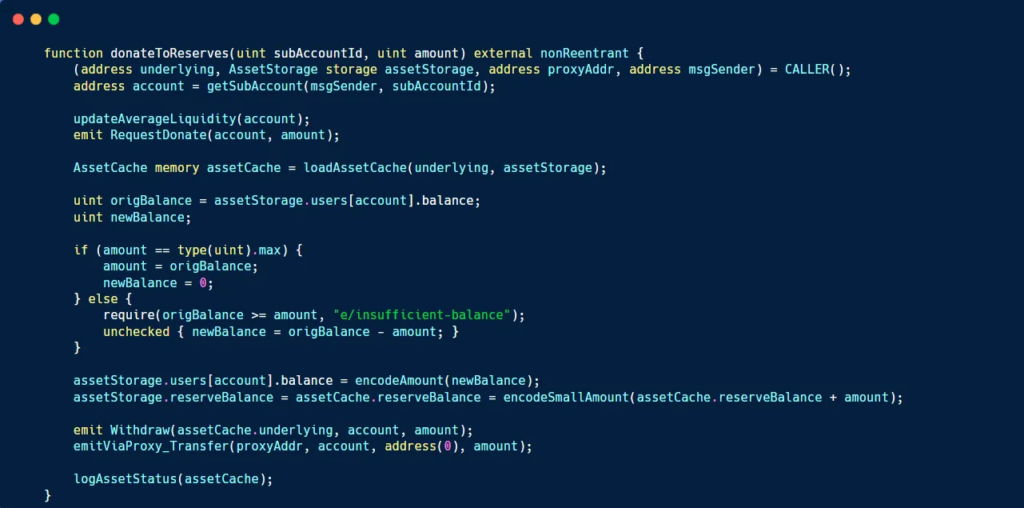
The assailants executed a flash loan attack on Euler Finance, capitalizing on a vulnerability present in the donateToReserves function of the protocol. This flaw enabled the attackers to manipulate lending mechanisms and carry out a sequence of transactions to extract substantial funds. The attack unfolded as follows:
Flash Loan Acquisition
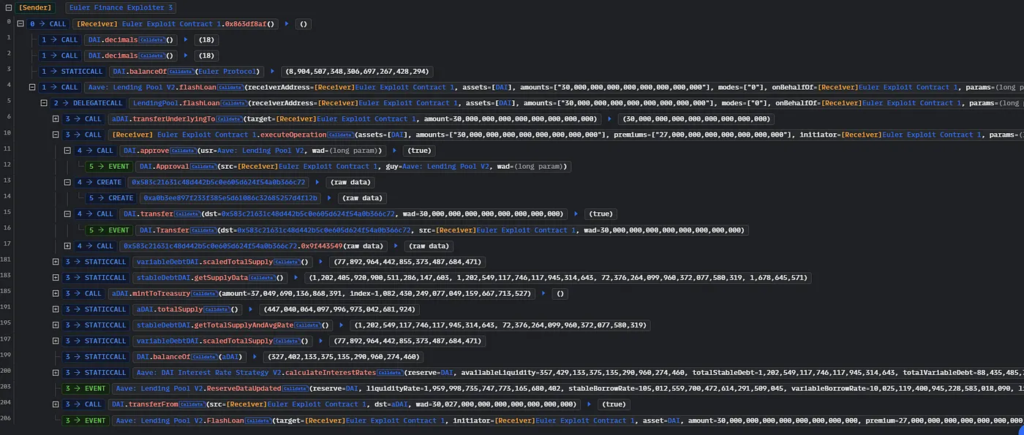
The attackers acquired a flash loan of 30 million DAI through Aave, a prominent flash loan protocol.
Deposit and Borrowing
- The flash loan was injected into Euler Finance.
- Using this flash loan, the attackers deposited 20 million DAI into Euler, receiving around 19.6 million eDAI in exchange.
- The attackers then borrowed a staggering 195.6 million eDAI and 200 million dDAI, leveraging the tokens acquired.
Self-Liquidation and Gain
- A portion of the borrowed amount was repaid using the remaining 10 million DAI.
- The attackers continued borrowing, amassing another 195.6 million eDAI and 200 million dDAI.
- Exploiting the
donateToReservesfunction, the attackers donated 100 million eDAI to Euler’s reserves.
Liquidation and Profits
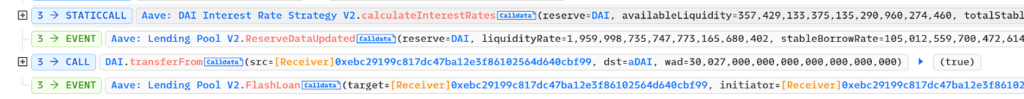
- Leveraging the
liquidatefunction, the attackers capitalized on the discrepancy between eDAI and dDAI values to execute a liquidation operation. - This maneuver resulted in the acquisition of 310 million dDAI and 259 million eDAI.
- The attackers withdrew 38.9 million DAI, repaid the flash loan, and profited approximately 8.87 million DAI.
Replicated Exploits
- The attackers replicated the attack’s logic across other pools, accumulating a total profit of nearly 197 million USD.
Vulnerabilities Exploited
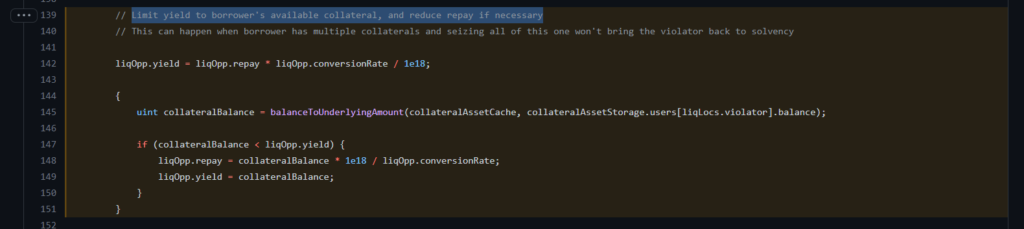
- Lack of Liquidity Checks: The absence of proper liquidity checks in the
donateToReservesfunction enabled users to manipulate their equity and debt tokens. This deficiency allowed attackers to generate bad debt that could not be settled. - Healthscore Flaw: Euler Finance’s health scoring mechanism inadvertently allowed insolvent accounts to obtain collateral without fulfilling their debt obligations. Attackers exploited this vulnerability to orchestrate under-collateralized leverage.
Attack Details
- Attacker EOA-1: 0xb66cd966670d962c227b3eaba30a872dbfb995db
- Attacker EOA-2: 0xb2698c2d99ad2c302a95a8db26b08d17a77cedd4
- Attacker Contract-1: 0xeBC29199C817Dc47BA12E3F86102564D640CBf99
- Attacker Contract-2: 0x036cec1a199234fc02f72d29e596a09440825f1c
- Attacker Contract-3: 0xD3b7CEA28Feb5E537fcA4E657e3f60129456eaF3
- Attacker Contract-4: 0x0b812c74729b6aBc723F22986C61D95344ff7ABA
- Victim Contract: 0xe025e3ca2be02316033184551d4d3aa22024d9dc
Attack Transactions On All Different Pools
- Transaction Hash: 0xc310a0affe2169d1f6feec1c63dbc7f7c62a887fa48795d327d4d2da2d6b111d
- Transaction Hash: 0x71a908be0bef6174bccc3d493becdfd28395d8898e355d451cb52f7bac38617
- Transaction Hash: 0x62bd3d31a7b75c098ccf28bc4d4af8c4a191b4b9e451fab4232258079e8b18c4
- Transaction Hash: 0x465a6780145f1efe3ab52f94c006065575712d2003d83d85481f3d110ed13d9
- Transaction Hash: 0x3097830e9921e4063d334acb82f6a79374f76f0b1a8f857e89b89bc58df1f311
- Transaction Hash: 0x47ac3527d02e6b9631c77fad1cdee7bfa77a8a7bfd4880dccbda5146ace4088f
The Aftermath of Hack
- The attackers exploited Euler Finance’s vulnerabilities to embezzle approximately $197 million, making it the most significant hack of 2023.
- Euler Finance promptly acknowledged the breach and initiated measures to mitigate its consequences.
- Following the initial attack, the hacker initiated on-chain communication with Euler, signaling a willingness to establish a truce.
Negotiation Between Euler and the Hacker
In an attempt to address the situation, Euler Finance engaged in negotiations with the exploiter. The protocol offered a deal in which the hacker would return 90% of the funds within 24 hours to mitigate potential legal consequences.
Additionally, the protocol introduced a $1 million dollar bounty prize aimed at acquiring data pertinent to the exploiter’s identity. This incident emphasized the importance of adopting proactive engagement strategies and negotiation tactics to recover stolen assets and manage security breaches.
The attacker initially appeared to disregard these proposals, proceeding to obfuscate the stolen assets using Tornado Cash, thereby complicating efforts to trace them.
Apology and Decision:
With the passage of time, the hacker expressed remorse for their actions and continued to make substantial returns, encompassing both ETH and DAI. Eventually, the majority of the stolen funds were recovered.
In light of these developments, Euler Finance announced the cessation of the $1 million reward campaign, as the situation had shifted from pursuing the reward to focusing on the recovery and restoration of assets.
This unexpected turn of events highlights the fluid nature of the decentralized finance landscape, showcasing the potential for resolution and amends, even in complex and high-stakes situations.
Stolen Funds Recovery
Transactions on March 25, 2023, witnessed the return of 51,000 Ether, and a subsequent transaction contributed 7,737 ETH, collectively amounting to more than $13 million.
This development followed an earlier transaction on March 18, 2023, in which the hacker returned 3,000 ETH to the protocol. The assets that were returned included 8.8 million Dai, 849,000 Wrapped Bitcoin (WBTC), 85 million Staked Ether (stETH), and 34 million USD Coin.
Chronology of Events
- Mar 13, 2023: Euler Finance fell victim to a flash loan attack, resulting in a loss of nearly $197 million.
- Mar 14, 2023: Euler Finance acknowledged the attack and initiated countermeasures.
- Mar 14, 2023: Sherlock admitted vulnerabilities and agreed to compensate Euler with $4.5 million.
- Mar 18, 2023: The attackers returned around 3000 ETH to Euler Finance.
- Mar 20, 2023: The attackers expressed their intention to return stolen funds and initiated communication with the Euler team.
- Mar 22, 2023: The attackers engaged with Euler via email.
- Mar 25, 2023: The attackers returned additional funds to Euler Finance.
Conclusion
The March 2023 flash loan attack on Euler Finance serves as a striking example of the evolving challenges and intricacies that the DeFi space faces.
The exploit, fueled by vulnerabilities within the protocol’s codebase, enabled attackers to orchestrate a sequence of transactions that culminated in a massive $197 million embezzlement. This breach prompted a rapid and coordinated response from both the Euler Finance team and external parties, resulting in the recovery of some funds and an introspective analysis of the attack.
This incident underscores the critical importance of rigorous testing, ongoing security audits, and vigilance in the development and deployment of smart contracts. The attack’s success hinged on exploiting gaps in code logic and incentive mechanisms, reinforcing the need for comprehensive assessment and meticulous incentive analysis to preclude similar vulnerabilities in the future.

