Solana’s popularity has sky-rocketed in a short period, as it claims to beat the blockchain scalability trilemma and is seen as an Ethereum killer.
In December 2020, the price for a Solana crypto-token, SOL, was about $1.5, while in October 2021, it heightened to around $251 a token.
Founded by Anatoly Yakovenko, who released the first white paper on Solana architecture in 2017. Then, in 2020 the first Solana coin, SOL, entered the crypto market.
As Solana is set to become the developer’s best pick for smart contracts, questions regarding its security start impeding. Therefore, the need for Solana smart contract audit comes into being.
Let’s Begin!
Why do We Need a Solana Smart Contract Audit?
Table of Contents
- 1 Why do We Need a Solana Smart Contract Audit?
- 2 What are the Attack Surfaces in a Solana Smart Contract?
- 3 Solana Smart Contract Example: Entry Point
- 4 What are the Common Vulnerabilities Causing Solana Security Issues?
- 5 How ImmuneBytes Perform your Solana Smart Contract Audit?
- 6 How ImmuneBytes perform Solana Audit? – Detailed Analysis
- 7 Methodology Pertaining to Solana Smart Contract Audit
- 8 Conclusion
In a short span of 2-3 years, Solana has become one of the three most used blockchain protocols, while SOL stands at 7th position in the list of highest cryptocurrencies.
Solana-based Dapps continue to grow in value, mandating the development of auditing techniques to ensure the highest standards of trustworthiness.
Here are a few reasons why Solana Smart Contract Auditing is Required
- Check if the code works as intended on the smart contract.
- To prevent issues pertaining to leakage of funds from smart contacts.
- Addressing vulnerabilities regarding the gas optimization
- General issues associated with Solana and Rust programming
- Possible attacks associated with Solana Programming
What are the Attack Surfaces in a Solana Smart Contract?
An attack surface consists of all the entry points that a hacker or any unauthorized person could use to enter a system. Once a hacker discovers these vulnerabilities in your smart contract, they can ingress confidential data, plant viruses, or create leakage of funds.
Unlike Solidity, which allows every public and external function to be called by an attacker. There is a single entry point associated with Solana Smart Contract.
Solana Smart Contract Example: Entry Point

In the above example, process_intruction is the only entry point that can act as an attack surface for a hacker. An attacker can supply arbitrary data, leading to a Solana smart contract exploitation.
What are the Common Vulnerabilities Causing Solana Security Issues?
Although, most vulnerabilities arising in a smart contract are common to most blockchain protocols. However, in the case of Solana, there are a few specific vulnerabilities.
So, Let’s have a look at some of the bugs causing Solana security issues:
- Solana account confusions
- Insufficient-SPL token account verification
- External Program Validation failure
- Missing signer check
- Missing ownership check
- Signed invocation of Unverified Program
- Re-Entrancy
- Arithmetic Over/Under Flows
- Delegate call
- Default Visibilities
- Entropy Illusion
- External Contract
- Short Address/Parameter Attack
- Unchecked CALL Return Values
- Race Conditions / Front Running
- Denial Of Service (DOS)
- Block Timestamp Manipulation
- Floating Points and Numerical Precision
How ImmuneBytes Perform your Solana Smart Contract Audit?
For instance, in Feb 2022, a $320mn Defi exploit took place in the wormhole protocol which is the largest attack to date on Solana. Here, the wormhole protocol acts as a bridge between Solana and Ethereum.
A more recently introduced competitor of Ethereum, Solana, is growing in popularity because it is cheaper and faster to use. Thereupon, with the arrival of more and more highly valued Solana projects, Solana security audits have become imperative.
We at ImmuneBytes offer a detailed manual analysis balanced against automated testing techniques to make your Solana projects a tough nut to crack for hackers. Solana audit is a security audit methodology that uses various simulations to test security controls.
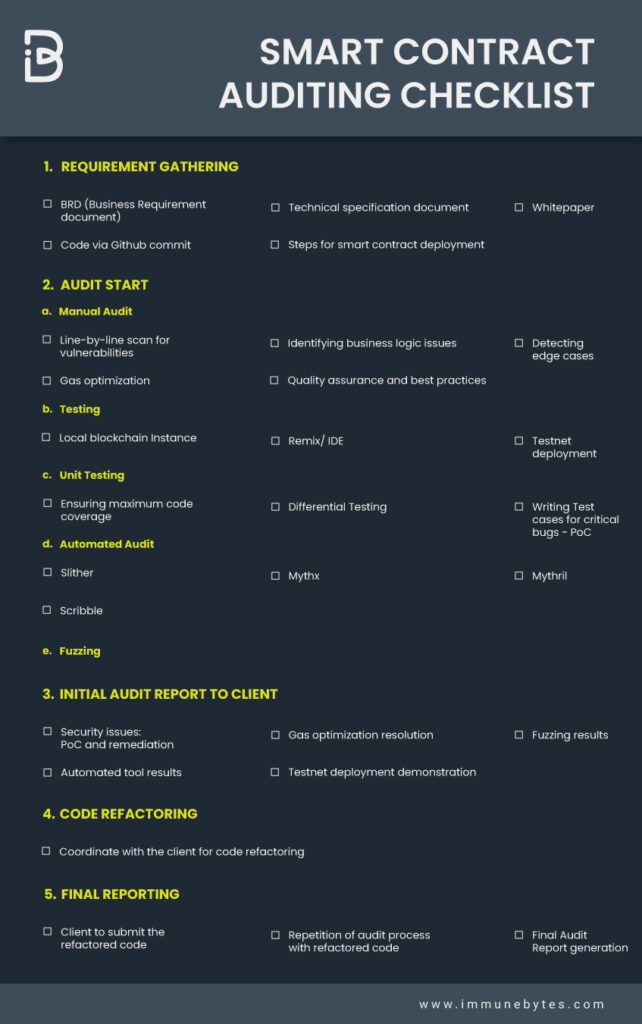
How ImmuneBytes perform Solana Audit? – Detailed Analysis
? One machine can do the work of 50 humans.
No machine can do the work of one extraordinary man?
Elbert Hubbard
Our top smart contract auditors manually analyze your code to point out every glitch possible to keep all the doors close to hackers. Thereupon, we deploy two autonomous teams of smart contract auditors for independent audits and a thorough review of your code. Thereby, our project manager integrates the findings of both reports highlighting all the issues and recommendations. Finally, we deploy a business analyst to understand the project scenario, along with providing test cases for every functional step.?
Methodology Pertaining to Solana Smart Contract Audit
Auditing a contract has become an unavoidable precautionary measure to prevent it from malicious attackers. Here is a step-by-step methodology for auditing smart contracts to remove any vulnerabilities present in the code.
- Formal verification
At first, we verify if the code is written as per the intended behavior described in the business specifications.
- Highlighting critical issues
Our prime focus is to look for glitches that can lead to financial fraud. For example, issues that can result in leakage of funds from smart contracts, and more
- Integration testing
This includes testing for dependency issues liable to creating unexpected errors in the primary smart contract.
- Highlighting major and minor issues
At this point, the focus is to look for all the major and minor vulnerabilities commonly arising in a smart contract. For Example, issues around using SafeMath, smart contract code upgradability, denial of service, low-level calls, and standard practice to enhance code reusability among others.
- Preliminary reporting- Highlight areas of recommendations
At this instant, we make a report including Proof of Concept and unit test cases for clients to understand the significance of recommendations made by our smart contract auditors. These suggestions if implemented can further improve your code. For example, techniques on gas optimizations, code reusability, and others.
- Refactor
It involves optimizing the client’s code based on the recommendations made by the smart contract auditors.
- Final Audit
Finally, after making the required changes, our auditors will perform a re-audit to check if any other vulnerability persists.
Conclusion
Auditing can be a wise choice to secure your Solana smart contract’s vulnerabilities from being exploited by hackers.
Solana audit is a security auditing methodology that tests security procedures through simulation. Security controls are created in the Solana audit as parts and autonomous operations that comprise the security architecture, which can be broken down into a number of modules, such as authentication and authorization, each of which is made up of a number of elements, such as rules, procedures, or policies ( e.g., solo audit).
So, Stay tuned with ImmuneBytes, to be in the known with more such information about Ethereum, and other blockchain protocols.
About ImmuneBytes
We at ImmuneBytes offer enterprises and startups comprehensive smart contract auditing solutions for their applications to have a secure commencement. Our journey begins with an aim to foster security in the upcoming blockchain world, improving the performance of large-scale systems.
However, Blockchain fosters a secure transactional environment, and applications built on this technology come with their own set of vulnerabilities. As there is no scope for alterations in blockchain transactions, smart contracts need to be thoroughly evaluated to prevent any further loopholes from turning your project into an extravagant exploit.
ImmuneBytes administers stern smart contract audits, employing both static and dynamic analysis, alongside examining a contract’s code and gas optimization, leaving no escape route for bugs.

