In the rapidly evolving realm of Web3, the digital environment is experiencing a profound transformation. Decentralized systems and applications take center stage in this shift, pledging to eliminate intermediaries and foster transparency and user autonomy. At the heart of this decentralized revolution lies the pivotal mechanism of token approvals. These approvals play a crucial role in safeguarding your assets and maintaining control while you embrace the advantages of decentralized platforms.
This article delves into the advantages, risks, and recommended practices associated with token approvals. Let’s dive right in!
ERC-20 Tokens and Token Approvals
Table of Contents
ERC-20 tokens are a type of fungible token standard on the Ethereum blockchain. These tokens adhere to a set of rules and functions that allow them to be easily and seamlessly exchanged with other tokens and interact with decentralized applications (DApps) on the Ethereum platform. One important concept related to ERC-20 tokens is the concept of “approvals,” particularly when dealing with smart contracts.
The PERMIT2 ERC-20 token standard, like the general ERC-20 standard, incorporates approval mechanisms for secure interactions between token holders and smart contracts. Below, we explore the PERMIT2 approval process and delve into potential risks associated with this functionality.
What are Token Approvals and How It Works?
Token approvals, also known as token allowances, denote the permissions bestowed upon token holders. These permissions allow specific smart contracts to retrieve and manage a predetermined quantity of their tokens.
For instance, if you’ve ever engaged with a decentralized exchange or participated in a DeFi protocol, you’ve likely encountered a request to grant approval for the platform to interact with your tokens. This process exemplifies token approval in action. It serves as a foundational element in numerous decentralized applications, facilitating functionalities that are often taken for granted.
For expample, when you list an NFT for sale on a platform like OpenSea, you essentially authorize the platform to conduct the NFT transfer on your behalf once a buyer is identified.
Let’s take a look at how it works.
A standard ERC-20 approval consists of:
- Maximum amount of token approval to the contract, without time limitation
- One-time approval for first execution for each contract with a dapp
1) Transfer Function: The ERC-20 standard includes a basic transfer function, allowing token holders to send tokens from their address to another.
function transfer(address to, uint256 value) public returns (bool);2) Approval Mechanism: To enable more complex interactions, such as allowing smart contracts to spend tokens on behalf of a user, ERC-20 introduces an approval mechanism. Token holders approve a specific address (typically a smart contract) to spend a certain amount of tokens on their behalf.
function approve(address spender, uint256 value) public returns (bool);3) Allowance Function: After approval, the allowance function is used to check how many tokens the approved address is allowed to spend on behalf of the token holder.
function allowance(address owner, address spender) public view returns (uint256);4) Transfer From: The approved address can then use the transferFrom function to move tokens from the token holder’s address to another.
function transferFrom(address from, address to, uint256 value) public returns (bool);Example:
- Token holder A approves smart contract B to spend a specific number of tokens.
- Smart contract B checks how many tokens it is allowed to spend on behalf of A.
- Smart contract B transfers tokens from A to another address, staying within the approved limit.
The traditional approve() function, as defined in the ERC-20 token standard, has been the foundation of token approvals since the inception of Ethereum-based tokens. While this method certainly still works, it has several drawbacks:
- Gas Fees: Every approval is an action on the blockchain, which means it requires a separate transaction – and this leads to additional gas fees. If you want to interact with multiple contracts or perform multiple operations, the costs can add up.
- Repeated Authorizations: If you exhaust your approved amount for a particular contract, you must approve again, leading to redundancy and a less-than-ideal user experience.
- Security Concerns: Unlimited approvals can pose risks (e.g. approving a dApp to interact with all your tokens in a specific currency). If a malicious actor gains control of a contract with unlimited approval granted, they could drain your tokens.
EIP-2612: PERMIT Signatures
EIP-2612 presents an innovative approach to token approvals known as Permit signatures. This mechanism empowers you to generate a signed message off-chain, providing consent to a contract. Subsequently, the contract can employ this signature to validate and execute the approval on-chain.
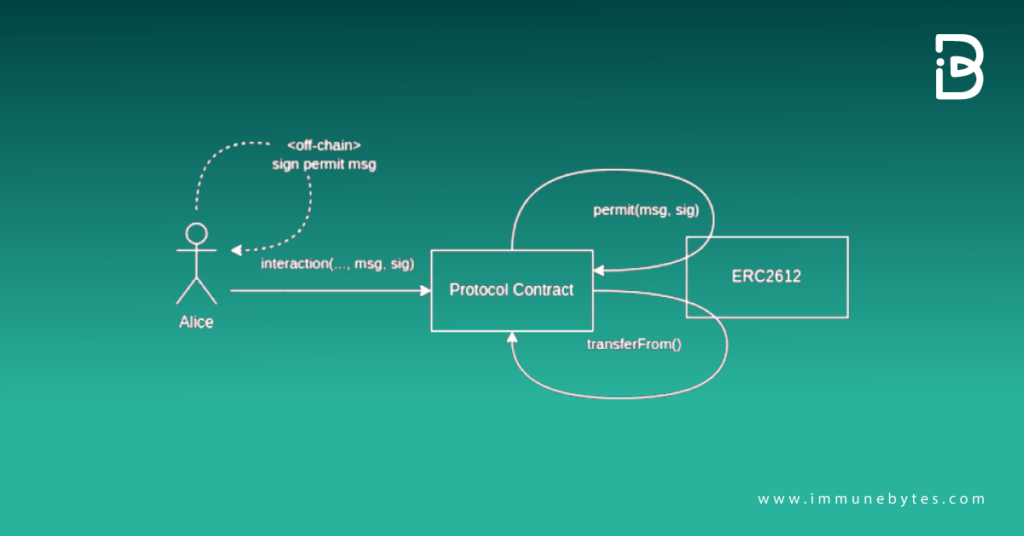
The advantages of this approach encompass:
- Gasless Approvals: As the approval is signed off-chain, there is no need to expend gas until the actual on-chain transaction takes place.
- Enhanced User Experience: Approvals can be granted without initiating a separate blockchain transaction, simplifying interactions with decentralized applications (dApps).
- Augmented Security: EIP-2612 mitigates the risks associated with unlimited approvals by enabling you to establish precise limits and expiration times for your approvals.
However, EIP-2612 is still not universally adopted and still requires tokens to integrate this standard, even though it would be a significant improvement.
Uniswap’s PERMIT2 Approval Model
Permit2 is a token approval contract that can safely share and manage token approvals across different smart contracts. Permit2 improves the user experience by reducing transaction costs while improving smart contract security.
Originally defined in EIP-20, the canonical token approval method suffered from a couple of weaknesses:
- Users were required to initiate an approval transaction for every new application they intended to utilize. This resulted in a perplexing user experience, as individuals could be prompted to send numerous transactions before gaining access to an application, resulting in both gas and time inefficiencies.
- For convenience’s sake, applications asked users to approve the maximum allowance, giving applications access to a wallet’s entire token balance for an indefinite amount of time.
It builds on the foundation laid by EIP-2612 but aims to make gasless approvals universal for every token. Key features and improvements of Permit2 include:
- Universal Gas-Free Approvals: Permit2 seamlessly collaborates with any token, whether integrated with EIP-2612 or not. This widens the reach of gas-free approvals, providing accessibility to a broader spectrum of tokens and users.
- Automatic Expiration: A standout feature of Permit2 is the automatic expiration of approvals, enhancing security by ensuring that lingering approvals don’t pose long-term risks.
- Developer-Friendly Simplicity: Permit2 streamlines the approval process for developers, simplifying integration and usage across diverse dApps and protocols.
By overcoming the limitations of the traditional approve() function and EIP-2612, Permit2 offers a forward-looking solution that harmonizes user experience, security, and developer convenience.
Associated Risks
Token approvals, if misused or exploited, can potentially facilitate scams and fraudulent activities in the following ways:
Front-Running Attacks:
Front-running occurs when a malicious actor observes a pending transaction and quickly submits a transaction with higher gas fees to get executed first. If users approve large amounts of tokens for a contract without careful consideration, it could lead to front-running attacks, where scammers exploit the approved amounts for their gain.
Unauthorized Transfers:
If users approve a contract to spend an unlimited amount of their tokens and the contract turns out to be malicious, it could lead to unauthorized transfers of a significant portion or all of their tokens without their explicit consent.
Phishing and Social Engineering:
Scammers might create fake applications or websites, encouraging users to approve token transfers. Users who unwittingly grant approvals to these malicious platforms may end up losing their tokens.
Infinite Approvals:
Granting infinite approvals without expiration can pose a risk. Even if a user intends to use an application for a short duration, leaving unlimited approvals in place for an extended period increases the likelihood of unauthorized token transfers.
False Promises:
Scammers may create applications or smart contracts promising attractive rewards or benefits in exchange for token approvals. Users who fall for such scams risk losing their tokens without receiving any promised benefits.
Preventative Measures
Limited Approvals:
Users should carefully review and limit the approved amount when interacting with smart contracts. Avoid approving unlimited allowances unless absolutely necessary.
Check Contracts:
Before approving tokens, users should verify the legitimacy of the smart contract or application. Using well-established and audited platforms reduces the risk of scams.
Expiration Dates:
Whenever possible, users should set expiration dates for approvals to ensure that permissions automatically expire after a specified period.
Educate Users:
Token developers and platforms should educate users about the risks associated with token approvals and provide clear guidelines on how to interact securely with their systems.
Regularly Review Approvals:
Users should periodically review and revoke unnecessary approvals. This helps minimize the potential impact in case a platform or contract becomes compromised over time.
Conclusion
It is crucial for users to comprehend the permissions they provide when approving tokens. Each approval should be evaluated from a trust perspective: Do you have confidence in the contract or dApp to handle your tokens responsibly? When in doubt, it is advisable to prioritize caution.
This is particularly important when dealing with unfamiliar or unverified contracts. Always ensure the legitimacy of a contract or dApp before giving any approvals.
By being cautious, staying informed, and exercising prudence in granting approvals, users can mitigate the risks associated with potential scams facilitated through token approvals. Additionally, ongoing efforts in the blockchain community to improve standards and security practices contribute to creating a safer environment for users.

