On August 24, 2022, Kaoya Swap, a decentralized protocol on the Binance Smart Chain, fell victim to a hack exploiting a flaw in its swapExactTokensForETHSupportingFeeOnTransferTokens function.
This vulnerability allowed an attacker to manipulate a swap path involving fee-on-transfer tokens, leading to unauthorized fund transfers and a profit of around 271 wBNB and 37,294 BUSD (approximately $118,000).
Kaoya Swap Overview
Table of Contents
Kaoya Swap is a decentralized transaction protocol built on Automated Market Maker (AMM) and exchange pool principles.
Hosted on the Binance Smart Chain, the platform includes an investment component designed to enhance the earnings of liquidity providers. Kaoya Swap leverages the liquidity pool’s funds to execute automatic trading strategies.
Vulnerability Analysis & Impact
The attack centered on a flaw present in the swapExactTokensForETHSupportingFeeOnTransferTokens function within the contract’s codebase. This function was responsible for swapping Fee-On-Transfer Tokens, which are ERC20 tokens that incur fees for every transfer() or transferFrom() operation.

Unlike standard ERC20 tokens, the receiver of such tokens would receive a smaller amount than the one initially sent.
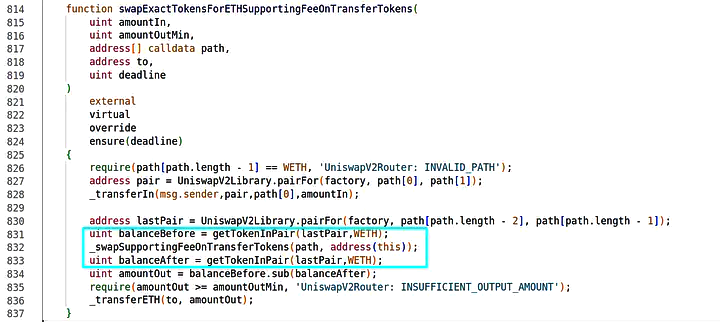
The vulnerability was a result of inadequate logic in the swapExactTokensForETHSupportingFeeOnTransferTokens function. This flaw allowed malicious actors to manipulate the swapping process to their advantage, resulting in unauthorized fund transfers.
The attack exploited the function’s miscalculation of the amount to be transferred in cases where the last pair in the swap path appears multiple times.
Exploit Details
Exploit Txn: https://bscscan.com/tx/0xc8db3b620656408a5004844703aa92d895eb3527da057153f0b09f0b58208d74
The attacker executed the exploit by carefully constructing a swap path involving two custom tokens labeled as tokenA and tokenB. The swap path was designed as follows: [tokenA, wBNB, tokenB, tokenA, wBNB], deliberately including the tokenA and wBNB pair twice in the path.
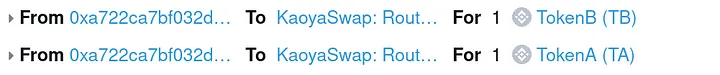
- The initial swap of tokenA to wBNB and the subsequent swap of tokenA to wBNB (second instance) introduced a balance difference in the wBNB pair. This discrepancy led to both parts of the swap being incorporated into the router, causing the router contract to transfer more wBNB than intended to the attacker.
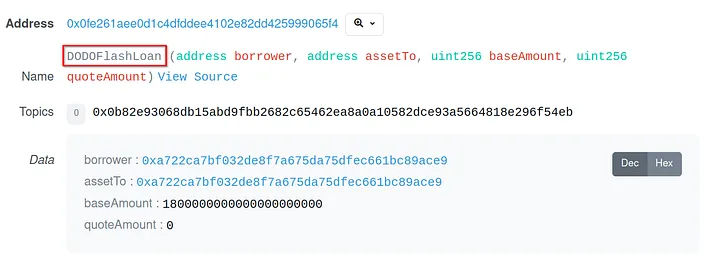
The attacker borrowed a flash loan of 1800 wBNB and utilized these funds to add liquidity to the newly created token pairs: [tokenA, wBNB] and [tokenB, wBNB].
Following the swap and subsequent liquidity removal, the attacker realized a profit of approximately 271 wBNB and 37,294 BUSD, equivalent to approximately $118,000.

Addresses who profited from the exploit:
- 0x8df3dd42bd51dd637580be6f15f651608b749ca1
- 0x236b6150d7cc095d923fc0463977b71e84c891e5
- 0xb77e7ee8e131d7425112df0f0f3c10e1c2208589
- 0xe946bc154baa243b48fcf156977910bbb236df09
- 0x50fc7d751cdde692682a04f59c2c9be2530b4d28
Mitigation Measures
To prevent such attacks in the future, it is essential to implement robust logic for swap functions involving fee-on-transfer tokens.
Specifically, adjustments should be made to the amountOutMin parameter, focusing on evaluating the recipient’s amount rather than the sender’s amount during invariant calculations.
This can help ensure that the correct amounts are transferred, reducing the risk of manipulation.
Conclusion
The Kaoya Swap hack on the 24th of August, 2022, underscored the importance of meticulous code review and thorough security testing in decentralized protocols.
By auditing the smart contract effectively and implementing appropriate safeguards, the DeFi community can strive for a more secure and resilient ecosystem.

