Overview
Table of Contents
Elephant Money, a decentralized finance (DeFi) platform on the Binance Smart Chain, experienced a major security incident on April 12, 2022.
An attacker took advantage of a flaw in the minting process of its stablecoin, TRUNK, and used flash loan attacks, including borrowing substantial amounts of WBNB and BUSD and manipulating the price of the ELEPHANT token.
This artificial inflation of ELEPHANT’s prices led to the loss of over 27,000 WBNB, valued at around $11.2 million.
About Elephant Money
Elephant Money is a DeFi project on the Binance Smart Chain, notable for its position at 28 on the DeFi leaderboard.
The platform, which includes a stablecoin named TRUNK and a reserve currency ELEPHANT, was launched with the aim of providing decentralized financial services focused on stability and value growth.
Despite being audited by third-party auditors, Elephant Money faced a severe setback when its token ELEPHANT’s price plummeted by 75%, and its stablecoin TRUNK fell by 40%, following a sophisticated flash loan attack.
Root Cause of the Hack
The hacking incident primarily occurred due to the misuse of the platform’s process for creating stablecoins. During the TRUNK generation phase, the hacker orchestrated a flash loan attack, targeting the ELEPHANT token’s valuation.
This vulnerability stemmed from the process where BUSD was exchanged for WBNB, which was then utilized to purchase ELEPHANT, leading to artificial inflation in ELEPHANT’s value while TRUNK was being minted.
Token Address: 0xe283d0e3b8c102badf5e8166b73e02d96d92f688
Detailed Analysis
Initial Preparation and Flash Loan Acquisition
Action: The attacker started the exploit by acquiring a substantial amount of flash loans.
Details: Flash loans of 131,000 WBNB (Wrapped Binance Coin) and 91 million BUSD (Binance USD) were taken.
Initial Attack Transaction: https://bscscan.com/tx/0xec317deb2f3efdc1dbf7ed5d3902cdf2c33ae512151646383a8cf8cbcd3d4577
Manipulation of ELEPHANT Token Price
- Swapping for ELEPHANT: The attacker swapped 131,162.00 WBNB for a massive quantity of ELEPHANT tokens (34.244e21 ELEPHANT), a key step in their strategy.
- Impact: This swap significantly increased the market price of ELEPHANT due to the sudden demand surge.
Exploiting the TRUNK Minting Process
- Minting TRUNK: TRUNK, the project’s stablecoin, was minted using the initially borrowed BUSD.
- Process Exploitation: During minting, the vulnerable contract swapped BUSD for WBNB and then used this WBNB to purchase ELEPHANT. This action further inflated the price of ELEPHANT, as the contract added to the demand.
Realization of Profit
Selling ELEPHANT: The attacker then converted the ELEPHANT tokens, which had their value artificially inflated, back to WBNB, receiving approximately 164,000 WBNB.
Redeeming TRUNK: The TRUNK tokens were also redeemed, resulting in the attacker gaining an additional 37,000 WBNB and 67 million BUSD.
Profit Calculation: After returning the flash loans, the attacker profited by approximately $4 million in a single cycle.
Repetition and Accumulation of Gains
- Cyclic Repetition: This process was not a one-time event. The attacker repeated the cycle, significantly multiplying the illicit gains.
- Total Gains: The cumulative result of these repeated actions led to the attacker amassing over 27,000 WBNB, equivalent to around $11.2 million.
- Transferring to Various Accounts: Post-attack, the stolen funds were strategically moved through different accounts.
- Bridging and Laundering: Some of the funds were bridged to Ethereum, and others were sent to Tornado Cash, a popular cryptocurrency tumbler, in an attempt to launder and obscure the origins of the funds.
Stolen Fund Details
Funds Movement:
- After the hack, the stolen funds were strategically distributed to various accounts.
- These funds were then either bridged over to the Ethereum blockchain or sent to Tornado Cash, a non-custodial privacy solution on Ethereum that breaks the on-chain link between source and destination addresses.
Ethereum Addresses Involved:
The hacker’s funds were traced to multiple Ethereum addresses:
- 0x8B7245C398E6a42b0475099b878D21101eF58471 472 ETH
- 0x21904B8C9Fa6D7da88E10Ae9e4493B1464A3D56b 472 ETH
- 0xfa2092b35546ef08cb736f1b4f26cc98a949e6f7 337 ETH
- 0x8fac3349Bc2592337bc61d419E12AE2A18Fe6577 339.9 ETH
- 0x2d3F27B6c8CAc4ba8B5D715D25AfcA03c05D0308 331.7 ETH
- 0xEB1521aEf54436F31007D4a9378e1ceBc8cB44d9 180.4 ETH
- 0x39C15D6dbc47F0EAB0fEE2469422E4A109352d54 473.4 ETH
- 0x219395018CfB8e337f2c79010Cd70144Eb16F500 472.1 ETH
- 0x3447d546d18a66Ab99Fe9edca23B6d8ce5c0B0a3 392.2 ETH
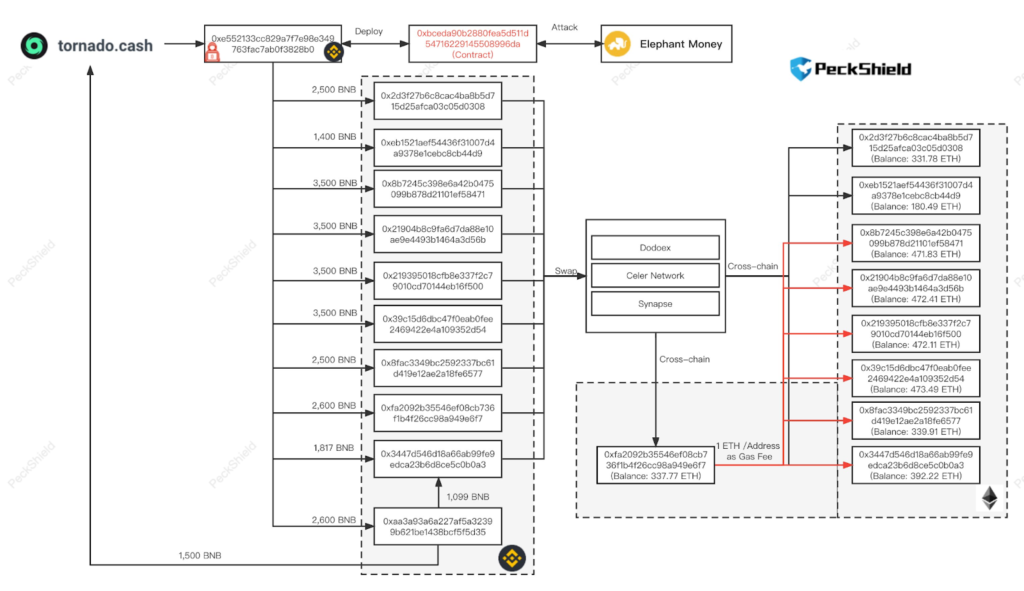
These addresses are being closely monitored by Elephant Money’s partners and law enforcement for any activity.
Notable Transactions:
Key transactions that signify the movement of the stolen funds can be observed in the following:
- https://bscscan.com/tx/0x662607f934518ff5c0255381a95a7e90d5783eb423ef3a51902d4c0dd5df65ae
- https://bscscan.com/tx/0x925f5a1313f4db40fe9e4023ce5671c6aaa6af74a87671bffb2f9364f6f87e80
Hack Aftermath
Immediate Actions by Elephant Money:
- The ELEPHANT Reserve was officially paused following the incident to prevent further exploitation.
- Transactions related to Stampede and the Reserve were disabled, with warnings issued to users about possible failures and BNB losses in attempted transactions.
Impact on Token Values:
- The hack significantly impacted the token prices:
- $ELEPHANT experienced a drastic price drop of 75%.
- The “stable”coin TRUNK fell by 40%, although it partially recovered to $0.78.
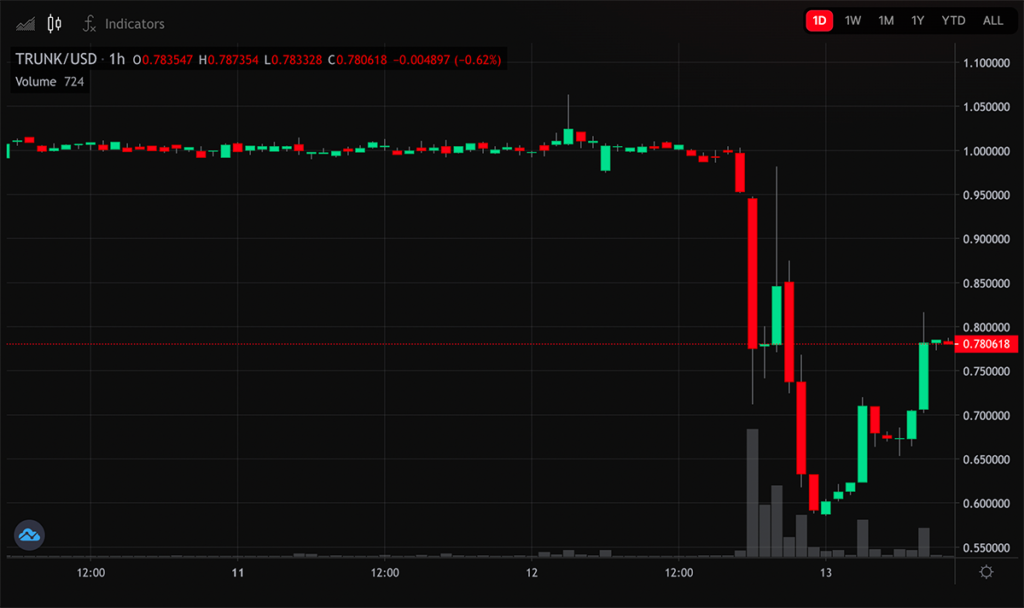
Adjustments and Announcements:
- Adjustments were made to the Reserve reward pools and TRUNK rewards. These adjustments were as follows:
- TRUNK Rewards and Performance pools were adjusted to $2.5M and $500K, respectively.
- Despite efforts to downplay the loss, Elephant Money’s position on the leaderboard was affected, falling to position 28.
Community and User Communications:
- Elephant Money communicated to its users that they would continue to earn Stampede rewards throughout the restructuring process.
- Users were advised about the potential for transaction failures and the associated risks of losing BNB if transactions were attempted.
Monitoring and Law Enforcement Collaboration:
- Elephant Money and its partners have identified and are monitoring the hacker’s Ethereum addresses where the funds were transferred.
- Ongoing collaboration with law enforcement aims to track the stolen funds and possibly apprehend the perpetrator(s).
Audit and Security Review:
The project had been audited by third-party auditors before the hack. However, the incident has likely prompted a re-evaluation of security measures and auditing processes.
Mitigation Steps
Enhanced audit processes, improved smart contract security practices, and continuous monitoring of transaction patterns could have helped in preventing such an exploit.
Implementing safeguards against flash loan attacks and thoroughly testing token minting processes can help mitigate such exploits.
Conclusion
The Elephant Money hack serves as a reminder of the vulnerabilities present in DeFi platforms, especially those related to token minting and price manipulation through flash loans. Comprehensive auditing and proactive security measures are crucial in preventing such incidents.
Engaging credible smart contract auditing firms like ImmuneBytes for thorough security audits can significantly reduce the chances of getting exploited by malicious actors in the Web3 space.

