Penetration testing, more commonly referred to as pen-testing is a security practice where cyber-security experts attempt to reveal and exploit vulnerabilities in a system.
In this post, you?ll learn:
What is Penetration Testing?
Table of Contents
Penetration testing is essentially a form of ethical hacking and security assessment. It involves the intentional launching of cyberattacks that are simulated by ?white hat? penetration testers with the help of tools and strategies especially designed to access or exploit systems, networks, websites, and applications.
The primary aim of pen testing is to pinpoint exploitable issues (e.g., application protocol interfaces (APIs), frontend/backend servers) so that effective security measures can be implemented.
Another use that pen testing offers is that cyber security professionals can assess the robustness of an organization’s security schemes, regulatory compliance, and security awareness.
An organization’s ability to identify and timely respond to security issues and incidents such as unauthorized access, as they occur, can also be validated by pen-testing.
What are Penetration Testing Tools?
Penetration testing involves vulnerability assessment, and it can be tricky. An effective way to help get rid of this complexity is by finding tools that can help your testers be more effective and efficient.
You can not find and employ a one-size-fits-all tool for pen-testing. Instead, different target systems need different sets of tools for port scanning, application scanning, Wi-Fi break-ins, or direct penetration of the network. The different types of pen testing tools can be broadly classified into five categories.
- Investigative tools for tracking down network hosts and open ports.
- Vulnerability examiners for uncovering weaknesses in systems, web applications, and APIs.
- Proxy tools such as specialized web proxies or common man-in-the-middle ones.
- Exploitation tools to achieve system footholds or access to assets.
- Post-exploitation tools for interacting with systems, maintaining and expanding access, and achieving attack objectives.
Top Penetration Testing Tools
Some of the most popular penetration testing tools employed by pen-testers for security assessment are:
- Netsparker
- Wireshark
- Metasploit
- BeEF
- Aircrack
How is Penetration Testing Done?
The pen testing process can be broken down into five stages.
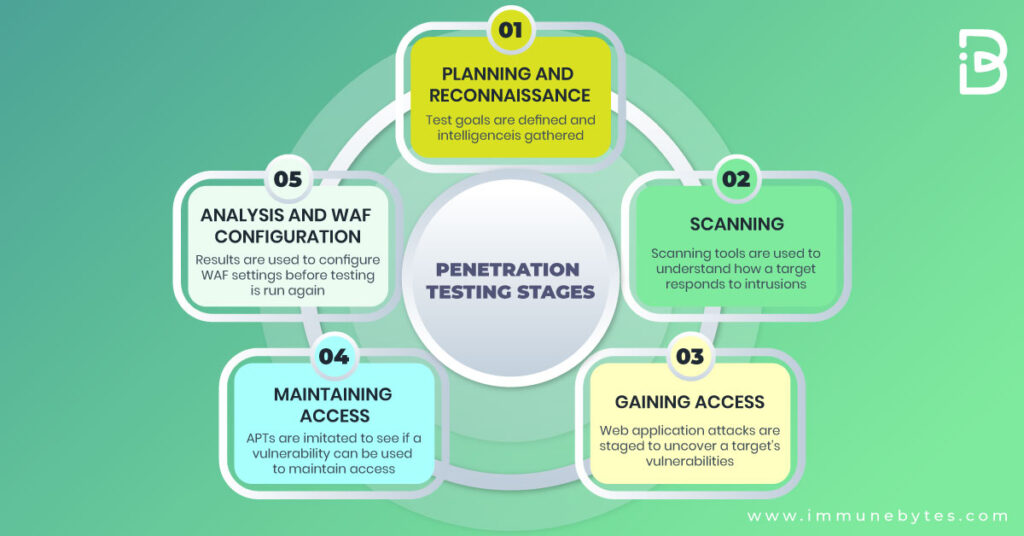
Planning and Reconnaissance
- This phase defines the scope and aims of a test, including the target systems to be addressed and the testing strategies that need to be employed.
- Collecting the necessary intelligence (e.g., network and domain names, mail server) to fully understand how the system works and its potential vulnerabilities.
Scanning
The next phase is to understand how the target system responds to various malicious intrusion attempts. This is done using:
Static Analysis:-
Examining an application?s code to calculate the way it acts while executing. These tools scan the entirety of the code in one pass.
Dynamic Analysis😕
Assessing an application?s code in the execution state, in a more practical way. It provides a real-time view of an application?s performance.
Gaining Access
This phase makes use of web application attacks to uncover a target?s vulnerabilities, such as cross-site scripting, SQL injection, and backdoors. Testers then try to exploit these vulnerabilities, typically by escalating privileges, stealing data, intercepting traffic, etc., to realize the potential damage they can cause.
Maintaining Access
The primary goal of this stage is to see if the uncovered vulnerability can be used to achieve a persistent presence in the exploited system. The idea behind this process is to replicate advanced persistent threats, which often remain in an application for a long period to steal an organization?s most sensitive data.
Analysis
All the findings and results of the penetration test are then compiled into a report detailing:
- The specific vulnerabilities that were revealed during the test.
- Sensitive data was accessed.
- The period the tester was able to remain in the system undetected.
What is Network Penetration Testing?
Most blockchain systems are connected to a network. Therefore, we need to know how devices interact with other devices in a network, as well as how networks work.
Network penetration testing is divided into 3 categories:
Pre-Connection Attacks:–
It is the first part of the network pen-testing. It is performed before connecting the node to the network.
Gaining Attacks:–
This is done to crack Wi-Fi keys and gain access to the Wi-Fi network. Attackers can also validate whether the devices use WEP/WPA/WPA2 network.
Post-Connection Attacks:–
These attacks apply after users can connect to the network. It includes plenty of malicious attacks that intercept the connections and capture everything like the user names, passwords, URLs, and chats. You can also modify the data as it has been sent in the air.
Penetration Testing Certification
The technical demand and skill set involved in penetration testing indicates that it has to be performed by a trusted and certified person. The certification serves as a piece of evidence that the tester has gone through the required training.
Here are some of the best penetration testing certifications you should explore for credibility in pen testing:
- Certified Ethical Hacker, issued by the EC-Council.
- GIAC Certified Penetration Tester (GPEN)
- Certified Penetration Tester (CPT)
- CompTIA PenTest+
- Certified Expert Penetration Tester (CEPT)
Conclusion
With DeFi attacks and thefts on the rise, it is more important than ever for organizations to conduct regular penetration testing sessions to reveal any kind of overlooked vulnerabilities and errors.
Although the primary aim of penetration testing is to uncover errors and bugs, it can also be employed to strengthen a project and check for its robustness.
The penetration test reports help organizations take a proactive stance toward their security policies, regulatory compliance, employees’ security awareness, and the organization?s potential to respond to thefts and attacks promptly.
Penetration tests can be done internally or externally by hiring a security firm that will help you with an outer perspective on your projects. ImmuneBytes offers penetration testing services and has a team of experienced security professionals on board that inspect your project and make it resistant to malicious attacks!
Additional Resources
* External Penetration Testing
* Internal Penetration Testing
* External Vs Internal Penetration Testing