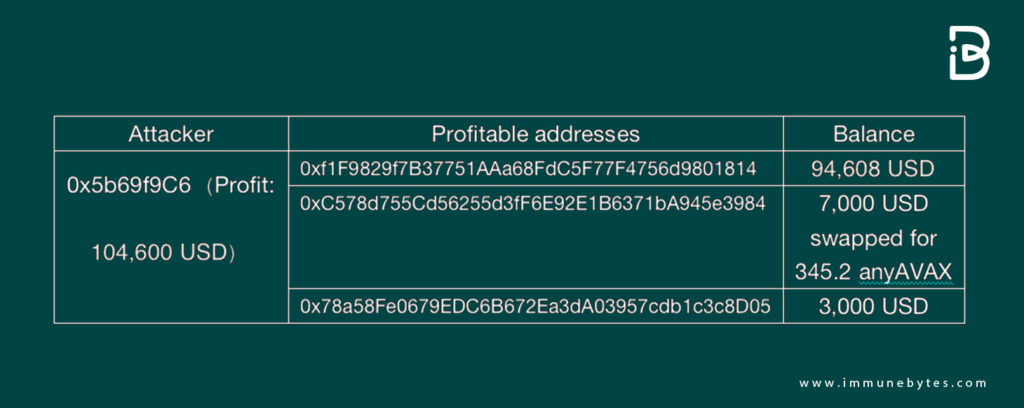
On Aug 28, 2022, $DDC token BSC was exploited for $104,600 due to smart contract vulnerability.
This oversight allowed an attacker to manipulate the function’s parameters and get away with the funds.
The vulnerability stemmed from the `handleDeductFee` function of the DDC contract, which lacked appropriate checks for both `feeAmount` and incoming addresses.
Hack Details
Table of Contents
Hack Transaction: https://bscscan.com/tx/0xd08cfb22d14bc4f2808970b5ce2557124ae3d7dc9fda756647a3427b8275f054
The Attacker’s address
https://bscscan.com/address/0x5b69f9c6cbb4958008eae46072886e6b9524fdef
Coincidently, this attacker transferred some portion of stolen funds to another address https://bscscan.com/address/0xc578d755cd56255d3ff6e92e1b6371ba945e3984 which was involved in the UF DAO Attack.
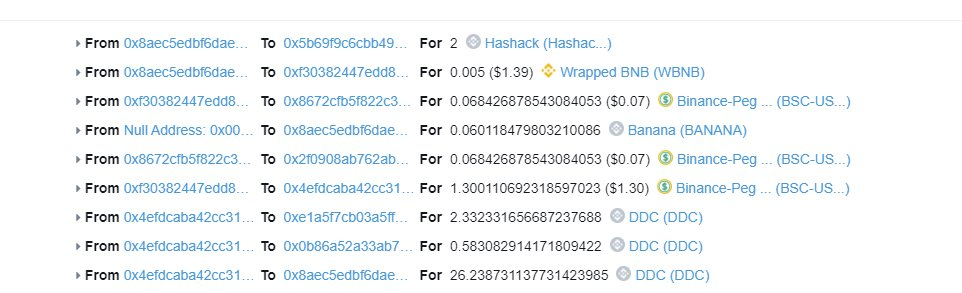
The Attack Flow
- Initial Swap: The attacker commenced the exploitation by swapping 1.3 USD in exchange for 26 $DDC.
- Manipulating
balanceOf: The attacker utilized the `balanceOf` function to ascertain the total amount of $DDC in the pool.
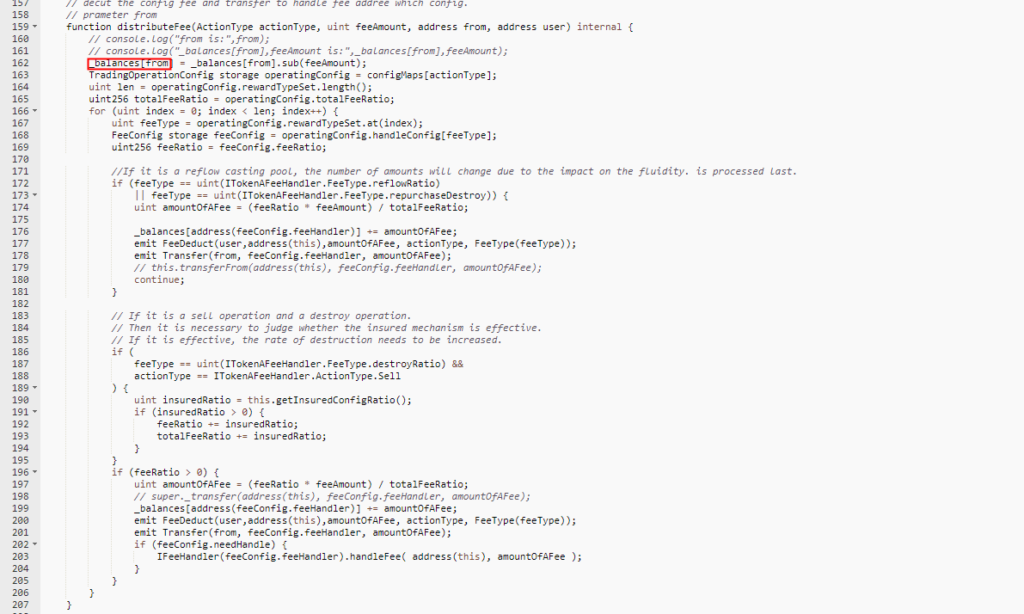
Following this, the attacker proceeded to call the handleDeductFee function of the DDC contract.
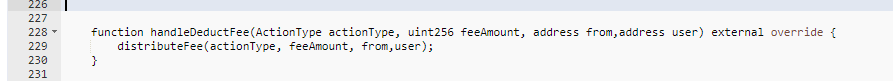
A vulnerability was exposed here as the `handleDeductFee` function does not validate `feeAmount` and does not check the incoming addresses. This made the function’s parameters manipulable by the attacker.
- Transferring Tokens
Capitalizing on the above vulnerability, the attacker transferred nearly all the DDC tokens that were present in the victim’s pool to the `handleDeductFee` function.
Afterward, the attacker invoked the `sync` function with the purpose of updating the k-value.
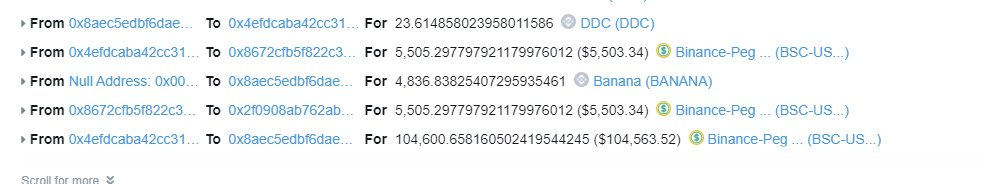
- Exploiting Price Discrepancy
The culmination of the above steps resulted in the balance of DDC in the pool plummeting to a mere 0.0003 DDCs.
Subsequent to the k-value update, the exchange rate of $USD to $DDC experienced a significant hike.
Leveraging this skewed rate, the attacker was able to swap just 23 $DDC to procure 104,600 USD.
Mitigations
- Contract Review: It is vital to have smart contracts audited by professional firms like Immunebytes to uncover potential vulnerabilities.
- Update
handleDeductFee: A quick mitigation would be to update thehandleDeductFeefunction to include checks forfeeAmountand incoming addresses. - Pool Monitoring: Implement monitoring tools to notify of any suspicious activities or sudden changes in token balances.
- This incident serves as a cautionary tale on the importance of thorough code reviews and the implications of unchecked vulnerabilities.

