Introduction
Table of Contents
If you are on the lookout for performing a penetration test on your project/s, it might be a better option if you are aware of the different types of tests available. With the correct knowledge, you will be better equipped to define the scope for your project, hire the right expert and, ultimately, achieve your security goals.
However, with so many types of penetration testing on offer, it can be difficult to ascertain which assessment meets the needs of your business.
This blog aims to cut through the industry jargon to provide all the information you need to identify the right pen test for your organization, including the important question of whether you require a black box, white box, or gray box testing style.
Let’s get started!
What is Penetration Testing?

Penetration testing, commonly referred to as “pen testing,” is a technique that simulates real-life attacks on your IT systems to find weaknesses that hackers could exploit. Whether to comply with security regulations such as ISO 27001, gain customer and 3rd party trust, or achieve peace of mind.
Penetration testing is an effective method used by modern organizations to strengthen their cyber security posture and prevent data breaches. It is recommended that all organizations commission security testing at least once per year, with additional assessments following significant infrastructure changes and before product launches, mergers, or acquisitions.
Penetration tests can examine whether a system is robust enough to withstand attacks from authenticated and unauthenticated positions and a range of system roles. With the proper scope, a pen test can dive into any aspect of a system.
Additional Resource: What is a Penetration Testing
Why is Penetration Testing Important?
Ideally, software and systems were designed from the start to eliminate dangerous security flaws. A pen test provides insight into how well that aim was achieved. Pen testing can help an organization in many ways, some of which are listed below.
- Find weaknesses in systems.
- Determine the robustness of controls.
- Support compliance with data privacy and security regulations (e.g., PCI DSS, HIPAA, GDPR).
- Provide qualitative and quantitative examples of current security posture and budget priorities for management.
Additional Resource: What is a Penetration Testing
The Different Types of Penetration Testing
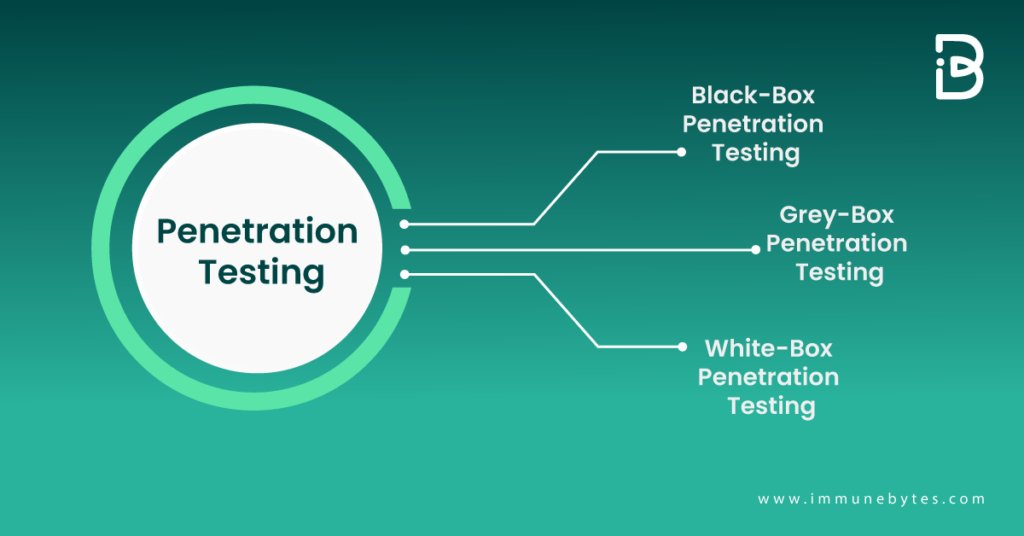
If you’re looking at getting a penetration test done and you want to know what kind of test is right for you, it is very important to understand the difference between black-box, gray-box, and white-box testing.
Let us see what they are and compare the three!
Black Box Penetration Testing
In a black-box testing assignment, the penetration tester is placed in the role of the average hacker, with no internal knowledge of the target system. Testers are not provided with any architecture diagrams or source code that is not publicly available. A black-box penetration test determines the vulnerabilities in a system that are exploitable from outside the network.
The pen tester in this instance follows the approach of an unprivileged attacker, from initial access and execution through to exploitation. This scenario can be seen as the most authentic, demonstrating how an adversary with no inside knowledge would target and compromise an organization.
Advantages of Black Box Penetration Testing
- Testers need not necessarily be an expert, as it does not demand specific language knowledge.
- The tester verifies contradictions in the actual system and the specifications.
- The test is generally conducted from the perspective of a user, not the designer.
Disadvantages of Black Box Penetration Testing
- Particularly, these kinds of test cases are difficult to design.
- Possibly, it is not worth it, if the designer has already conducted a test case.
- It does not conduct everything.
White Box Penetration Testing
White box penetration testing, sometimes called crystal or oblique box pen testing, involves sharing full network and system information with the tester, including network maps and credentials. This helps to save time and reduce the overall cost of an engagement. A white box penetration test is useful for simulating a targeted attack on a specific system utilizing as many attack vectors as possible.
Advantages of White Box Penetration Testing
- It ensures that all independent paths of a module have been exercised.
- It ensures that all logical decisions have been verified along with their true and false value.
- It discovers typographical errors and does syntax checking.
- It finds the design errors that may have occurred because of the difference between the logical flow of the program and the actual execution.
Disadvantages of White Box Penetration Testing
- Certain functionalities could be missed out as only the available code is tested.
- Many developers are against it as it is a tedious process.
- It is very time-consuming as the codes must be redesigned and test cases must be rewritten.
- Requires resources and professional skills as testers with in-depth programming skills are necessary.
Gray Box Penetration Testing
In this type of testing, a tester usually provides partial or limited information about the internal details of the program of a system. It can be considered an attack by an external hacker who had gained illegitimate access to an organization’s network infrastructure documents.
Advantages of Gray Box Penetration Testing
- As the tester does not require access to source code, it is non-intrusive and unbiased
- As there is a clear difference between a developer and a tester, so there is the least risk of personal conflict
- You don’t need to provide internal information about the program functions and other operations
Disadvantages of Gray Box Penetration Testing
- Testers have no access to source code and may miss certain critical vulnerabilities.
- Gray box testing may be redundant if the application developer has already run a similar test case.
- Gray box testing is not ideal for algorithm testing.
- Testing every potential input is too time-consuming and unrealistic, meaning certain program paths will not be tested.
To make things easier, here’s a comparison chart between the three types of pen testing!

Conclusion
Penetration testing is a broad discipline that encompasses different techniques, so it is important to understand the relative risks that your organization is facing to choose the most appropriate type.
Suppose you are still unsure of what type of testing is appropriate for your organization. In that case, you can reach out to ImmuneBytes? team of experienced penetration testers, who can help you!
Additional Resources
* What is Internal Penetration Testing?
* What is External Penetration Testing?
* Difference Between Internal vs. External Penetration Testing.