On July 21, Defi Conic Finance suffered two significant exploits due to vulnerabilities in its smart contracts. These vulnerabilities led to a total loss of approximately $4.2M from its ETH and crvUSD omnipools.
The first exploit, amounting to a loss of ~$3.3M from the ETH pool, was attributed to a read-only reentrancy flaw in the Oracle contract.
The second exploit, leading to a loss of ~$934K from the crvUSD Omnipool, was a sandwich attack on imbalanced pools. These breaches had dire consequences on Conic’s reputation, causing a significant drop in the value of its native token, CNC.
What is Conic Finance?
Table of Contents
Conic Finance is a liquidity pool platform designed for the Curve DeFi protocol. With its base in Milan and founded in 2022, it primarily aims to balance liquidity in the decentralized finance sector.
Conic Finance allows users to efficiently trade, swap assets, and provide liquidity to multiple Curve pools through a single transaction, using the Conic Omnipool.
This feature permits users to diversify their investments across various assets, leading to potentially higher returns.
Hack Analysis
ETH Omnipool Exploit: Timeline and Impact:
Time: 10:51 am UTC
Loss: Around $3.2 million worth of WETH.
Mechanism and Attack Steps
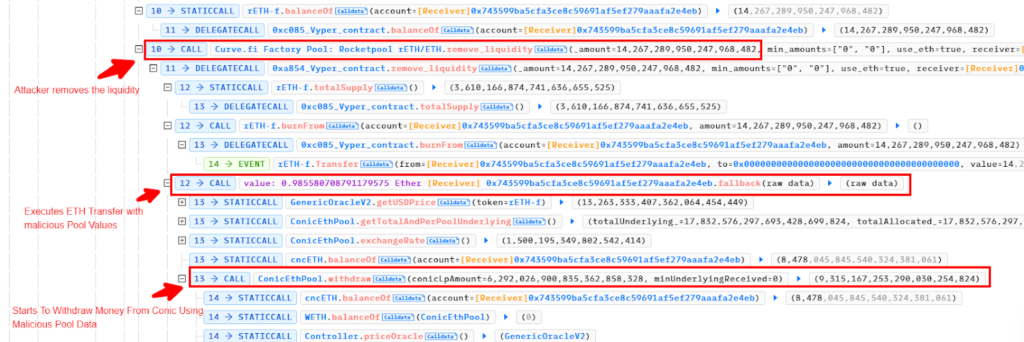
The attacker leveraged a read-only reentrancy vulnerability in the Oracle contract. Here’s a detailed step-by-step breakdown:
- The hacker delved deep into Conic ETH Omnipool mechanisms and discovered a vulnerability in ETH presence determination.
- Identified a mismatch in the
_isETHmethod used by Omnipool. - Realized that instead of the expected ETH address (0xeee…eee), these pools used the WETH address.
- The reentrancy guard for the rETH pool was bypassed due to this mismatch.
- Exploited this flaw to manipulate the rETH Curve LP token’s price.
- Using the manipulated price, the attacker hoodwinked the ETH Omnipool into minting excessive cncETH LP tokens.
- Ran a deposit-withdrawal loop, capitalizing on the manipulated prices, draining the pool by approximately $3.2 million.
Vulnerability Explained
- The Curve pool has a flaw where it allows an attacker to interfere while it’s only halfway through updating its internal data. So when Conic checks the data from Curve, it receives incorrect information.
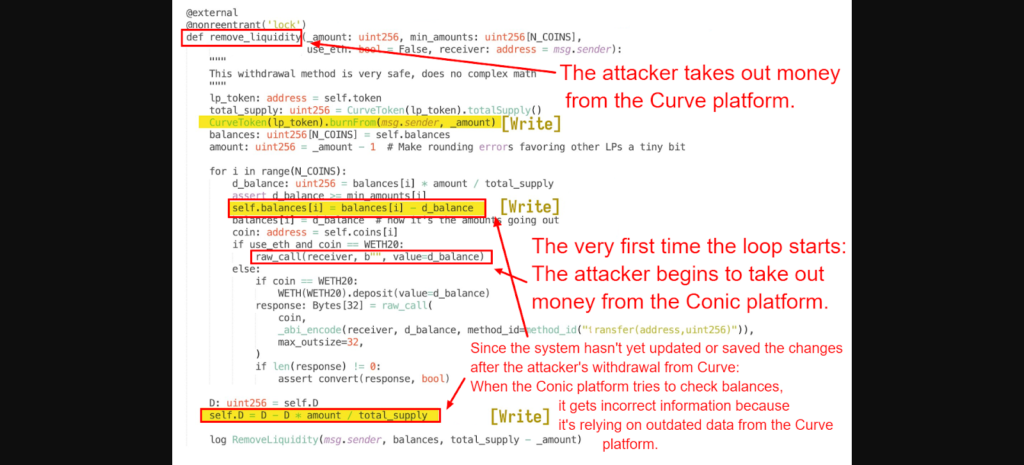
- After messing with the Curve pool’s data, the attacker then requests a withdrawal from Conic. Because Conic relies on the now-corrupted data from Curve to determine how much to give, it ends up giving out the wrong amount.
- So, when Conic tries to check the value of its tokens by looking at the Curve pool (which is now showing wrong data because of the attacker), it gets deceived.
What is Reentrancy Vulnerability?
A reentrancy vulnerability in smart contracts, particularly in the Ethereum context, occurs when an external contract is able to call back into the calling contract before the first function call is finished.
This can allow the external contract to exploit the calling contract, especially in cases where the calling contract’s state (e.g., balances) isn’t updated until after external calls.
The infamous DAO hack in Ethereum was a result of such a vulnerability, where the attacker was able to repeatedly withdraw funds due to the contract’s state not being updated in time. You can read more about Reentrancy Vulnerability at https://www.immunebytes.com/blog/reentrancy-attack/
Important Links:
Exploit transaction:
https://etherscan.io/tx/0x8b74995d1d61d3d7547575649136b8765acb22882960f0636941c44ec7bbe146
Malicious contract:
https://etherscan.io/address/0x743599ba5cfa3ce8c59691af5ef279aaafa2e4eb
Attacker’s Address:
https://etherscan.io/address/0x8D67db0b205E32A5Dd96145F022Fa18Aae7DC8Aa
https://etherscan.io/address/0x3d32c5a2e592c7b17e16bddc87eab75f33ae3010
crvUSD Omnipool Exploit
Time: Started at 19:08 UTC
Loss: Approximately $934,000, leading to a profit of around $300,000 for the attacker.
Mechanism and Attack Steps
The attacker leveraged a type of sandwich attack on imbalanced pools, taking advantage of the favorable exchange rates in the Curve pool.
Though Conic Finance had mechanisms to prevent interactions with imbalanced Curve pools, the set bounds were too lenient, allowing the attacker to siphon funds gradually.
Attack Steps
- Exchange crvUSD to USDC in the Curve pool.
- Deposit crvUSD into Conic.
- Exchange USDC to crvUSD in the Curve pool.
- Withdraw from Conic.
- Repeat
Attacker Add:
https://etherscan.io/address/0xb6369f59fc24117b16742c9dfe064894d03b3b80
Victim Contract:
https://etherscan.io/address/0x4dece678ceceb27446b35c672dc7d61f30bad69e
Transactions attacking the crvUSD pool:
A comprehensive list of transaction hashes is provided, all of which can be inspected on Etherscan for further detail.
- 0x37acd17a80a5f95728459bfea85cb2e1f64b4c75cf4a4c8dcb61964e26860882
- 0x64910b0a07083119403ce1bb30c94503e99e44c334bdb68f3afea09c834bdd9f
- 0x3af57106166b8568a0ace8d0741cf05355d74d7e7e173f1bab7a4434c6f0ed80
- 0xcf484ced351166dee819fcf2417e7df6ac826ac6af53c676e28f6bc96f5bcdbd
- 0x680b7d4947068647b1360904581c843fe6b477e55fe64ece6ef4b733aee12c8f
- 0x69029760e5907a7a82c9ac008602f6cc719f1e64bf7912c1148bb6dce10cea41
- 0xad596a612492bc640eca76afd03a03aed9ad91cf98f226624a9d8829e35e9308
- 0xa267ece5e1321e4a51c2a03fb9592e73f79cc13ddc60d8bd7dafd6daf491d7fa
- 0xe7f54acd58bea522f9aac5d18f8765a96a2b41d1aa620f9df5e084e113976080
- 0x050dec294956f9a036565be9b2c1cfb4e7c74fcdeaed4ae8ef42f42cca17e32c
- 0xde8e5f61c89d3f488e97dad680d314a347fefa3e55eb00221b70527a7d44cea8
- 0xc08bfee8653bdb715144f98bc014eecbab6cf92ddaba16b836f3889fd850a862
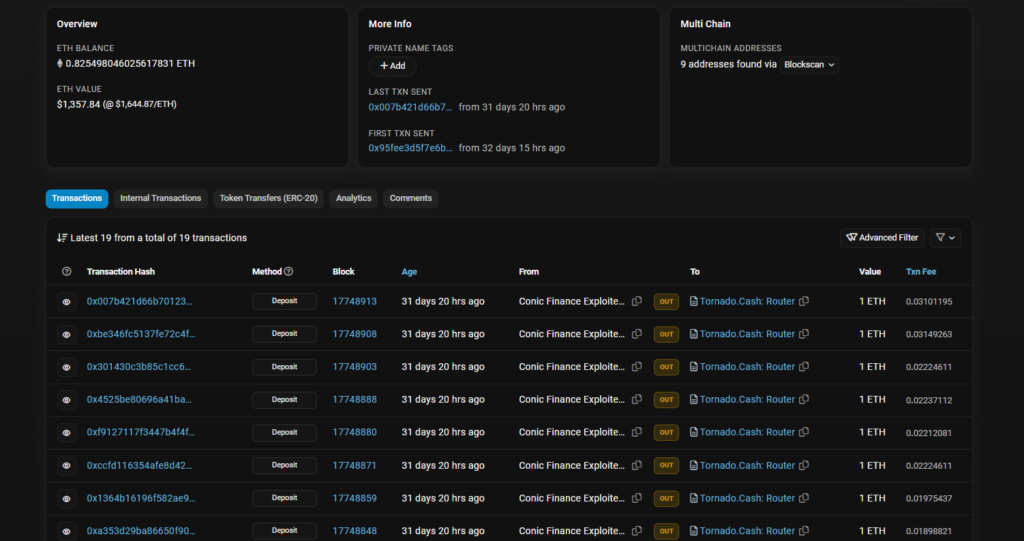
Most of the stolen were either moved to different addresses or deposited to Tornado.cash.
What are sandwich attacks?
A sandwich attack, in the context of decentralized exchanges (DEXes) and DeFi, is a type of front-running attack where a malicious actor observes a pending transaction from a user and places two transactions of their own: one before (front-run) and one after (back-run) the user’s transaction.
The aim is to capitalize on price slippages, liquidity pool changes, or other trade impacts that the user’s transaction will create. Essentially, the attacker “sandwiches” the user’s transaction with their own, thereby profiting at the user’s expense.
Read More on Sandwich Attacks in Blockchain
Repercussions
- Conic’s native token, CNC, experienced a dramatic decline in value post-hack. Before the initial breach, CNC’s price hovered around $6. However, it plummeted by 35% after the first exploit and eventually dropped to $1.72 after the second.
At the time of this report, CNC’s value has stabilized at approximately $2.75, which is just below half of its pre-hack price. - Conic’s prior standing as a highly anticipated DeFi project, with the potential to compete with giants like CVX/Yearn, has undoubtedly been shaken.
Conclusion
The exploits faced by Conic Finance are a somber reminder of the risks inherent to the DeFi sector. It underscores the importance of robust security audits, continuous monitoring, and swift response mechanisms.
As the space continues to evolve, it is crucial for both projects and users to prioritize security and stay informed about potential vulnerabilities.

