Overview
Table of Contents
- 1 Overview
- 2 About Cheese Bank
- 3 Root Cause Analysis
- 4 Detailed Analysis
- 4.1 Overview of the Hack
- 4.2 Attack Flow
- 4.2.1 Step 1: dYdX Flashloan Acquisition
- 4.2.2 Step 2: Manipulating Cheese Token Value
- 4.2.3 Step 3: Liquidity Pool and LP Tokens
- 4.2.4 Step 4: Minting sUSD_V2 Tokens
- 4.2.5 Step 5: Inflating CHEESE Price
- 4.2.6 Step 6: Price Feed Refresh
- 4.2.7 Step 7: Borrowing Stablecoins
- 4.2.8 Step 8: Converting CHEESE to ETH
- 4.2.9 Step 9: Additional ETH Acquisition
- 4.2.10 Step 10: Asset Collection
- 4.2.11 Step 11: Loan Repayment
- 5 Stolen Fund Details
- 6 Hack Aftermath
- 7 Lessons Learnt
- 8 Conclusion
The Cheese Bank hack on Ethereum’s blockchain on November 6, 2020, at 19:22:21 PM +UTC, resulted in a significant loss of $3.3 million in USDC/USDT/DAI.
This hack was primarily executed by exploiting a vulnerability in Cheese Bank’s method of determining asset prices using an AMM-based oracle, notably Uniswap.
The attackers leveraged this flaw in combination with a flash loan attack, leading to a substantial financial impact on the platform.
About Cheese Bank
Cheese Bank, a Decentralized Autonomous Digital Bank on Ethereum, offers a range of services, including asset management, lending, fund management, and insurance.
Operating within the rapidly expanding DeFi ecosystem, which boasts over $16 billion in total value locked, Cheese Bank is recognized for its innovative approach in the DeFi sector.
However, it has also highlighted vulnerabilities in its security systems, underscoring the need for enhanced safety measures in this evolving market.
Root Cause Analysis
The core vulnerability in the Cheese Bank hack was the flawed mechanism in determining the value of collaterals through an Automated Market Maker (AMM) based oracle, specifically Uniswap.
This method of valuation proved to be susceptible to manipulation. The attacker exploited this vulnerability by using flash loans to artificially inflate the price of the Cheese token on Uniswap.
As Cheese Bank relied on this inflated value for collateral assessment, the hacker could borrow significantly more assets than what the collateral was truly worth.
Detailed Analysis
Overview of the Hack
- Date and Time of Attack: November 6, GMT
- Total Loss: Over $3.3 million (USDC/USDT/DAI)
- Initial Transaction: Transfer of 1 ETH for handling fees
- Hack Transaction ID: https://etherscan.io/tx/0x600a869aa3a259158310a233b815ff67ca41eab8961a49918c2031297a02f1cc
- Malicious Contract Created By Attacker: https://etherscan.io/address/0x9e0259437804c7bf175421a451bc80611a0b93c3
- Attacker’s Wallet: 0x882d72aaae187f54e85c7a0cb19dfec5316cd9aa
- Stolen Assets Deposition Address: 0x02b7165D0916E373f0235056a7e6FCcdb82d2255
Attack Flow
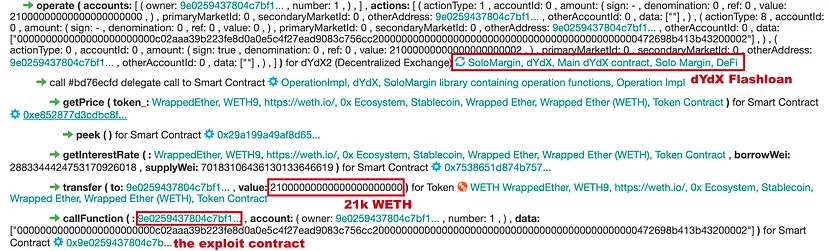
Step 1: dYdX Flashloan Acquisition
- Borrowed 21,000 ETH from dYdX.
- Utilized this borrowed ETH for subsequent steps in the hack.
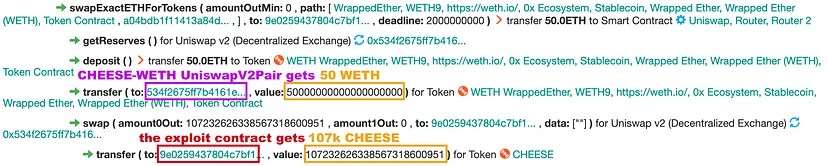
Step 2: Manipulating Cheese Token Value
- Token Swap at UniswapV2: Swapped 50 ETH for 107,232 CHEESE.
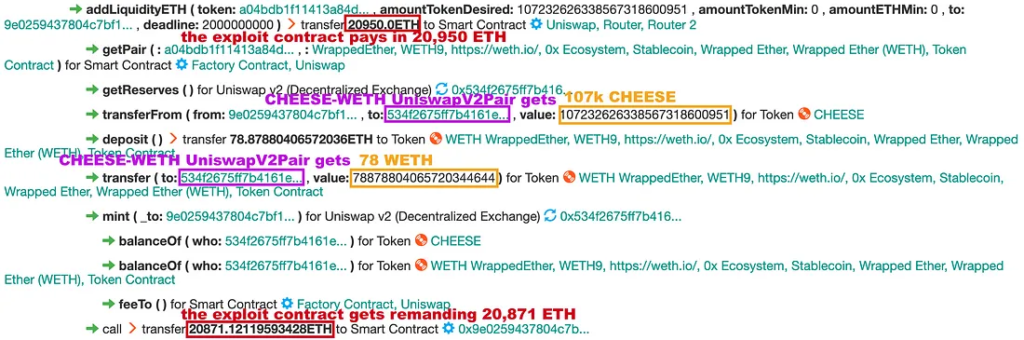
Step 3: Liquidity Pool and LP Tokens
- Added 107,232 CHEESE and 78.8 ETH to Uniswap’s liquidity pool.
- Received UNI_V2 LP tokens in exchange.
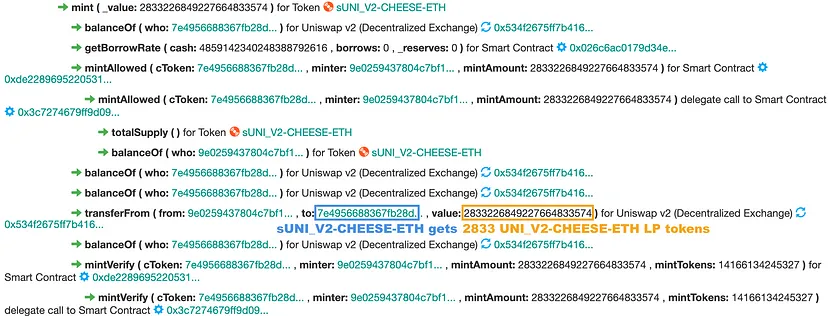
Step 4: Minting sUSD_V2 Tokens
Minted sUSD_V2 tokens using UNI_V2 LP tokens as collateral.
Step 5: Inflating CHEESE Price
- Swapped 20,000 ETH for 288,000 CHEESE, significantly raising CHEESE price.
- Inflated value of UNI_V2 LP tokens held as collateral in Cheese Bank.
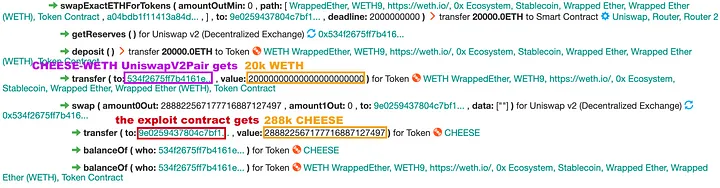
Step 6: Price Feed Refresh
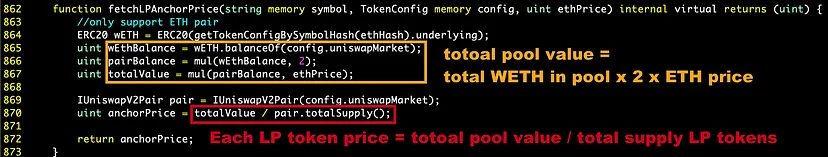
- Invoked CheesePriceOracle::refresh() to update the price of UNI_V2-CHEESE-ETH LP tokens.
- Calculated new inflated value of LP tokens for borrowing purposes.
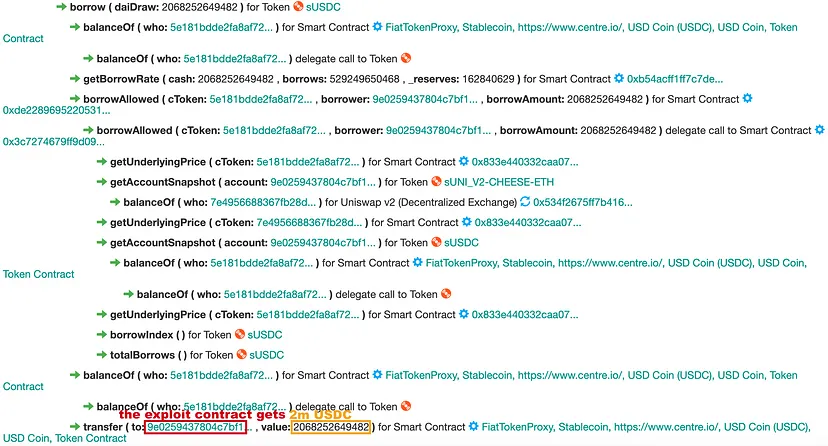
Step 7: Borrowing Stablecoins
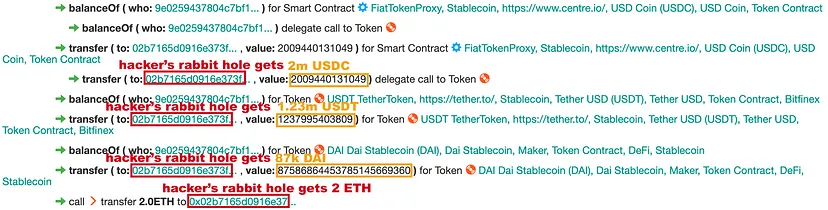
- Drained 2 million USDC, 1.23 million USDT, and 87,000 DAI from Cheese Bank.
- Thoughtfully borrowed the exact balances available in Cheese Bank.
Step 8: Converting CHEESE to ETH
Swapped 288,000 CHEESE back to approximately 19.98k ETH.
Step 9: Additional ETH Acquisition
Converted 58,812 USDC to 132 ETH to cover ether spent in previous steps.
Step 10: Asset Collection
Consolidated hacked assets into address 0x02b7.
Step 11: Loan Repayment
Returned 21k ETH flash loan to dYdX.

Stolen Fund Details
Due to the Oracle price manipulation, the attacker stole away with 2m USDC, 1.23m USDT, 87k DAI, and 2 ETH. The total fund loss amounted to around $3.3 million.
- Movement of Stolen Funds: After the hack, the stolen assets were converted to BTC through multiple DeFi platforms and underwent complex transfer operations to various addresses.
- The stolen funds were converted to BTC through multiple DeFi platforms and renBTC.
- Undertook complex and intensive transfer operations to obscure the trail.
- Attacker’s address when retrieving BTC: bc1q8eraa350aw8tcmftulrjnagrtexaukz0mzv8u6
Here’s the list of Bitcoin (BTC) addresses that the attacker used to transfer the stolen funds:
| 18F8R5sFbPRuNzPe9nKiPV72jhLNWKSxBm 1EovLRynmhV2WNtSuD8zSnGeFZYPE17tK8 3M3uCSqjo1TiMeo9iFzxXH9SXpbgRd3D4R 1HCBUU9C3dfBPDx1WPXsFY595FhEWGTj3C 1F5DYeTmuHKESjE4DVVGXH8HWM7TFxP87u | 3JNPxwpBqUuvFSFCdj2ZKaTkn1riygJ3bc 1Lx4fuNsD4MjA2hWF7hctmmjpgiC8kTuep bc1q9z8rrrqrfaxuwm9wr6d6ajdaysqk3mze3ppzu3 1FomPPUQbhgUHYCo5NN2pRvYr254zb4eRL 32sBB6YNMT9BmbJCVM5VuTuBy3agb4EYqP | bc1q7fkuj48fuus2k90escf5h7mm2dctzu79vuyu30 14z1JiLLiRZFYMSQpPfszbkwdequaxqbW4 bc1qfj708765t5vnlsqz2uymwws53nvdzhhljurng4 1HuvmCBh4CVwvtXQQECk51LV89wZdQaraj 37gqaYKM2d67Yx3FnYE7EaNP2vhG2HS9mM |
| 1DAj1P8smLGUR8y8exBHU7VY2bXhw2NTcN 1KXfBP2YTyZsN5vamAxgNWgfEN7f78Mejy bc1qsmht2jqz53kg9e5en373hyelatk05ujte93rtn 3N6iroGcEu8UwZLsPDQfQCk6vjRE8rndyP 3HtAawMXPPcuqjrKqpgx1YZQ1b82sud4x1 | 15eWFYqZhkp9A5i3TZtJup2BYznkBGKMhj 1GsfRr1h7w74qg61ZXB9Y2rhX3dzVNv5Uk 1JzZSqHhnnfzNyFkcHtqcwD3PrkMiG8bbD 1LrbjZrpQ6DY2nqPR3Jve6d1ZPHeoqTssh 14NEtCWaUb7d7S5bzRf3ar4yGXzyARrNAv | 19qTpSHx86psLjz6zqxFF2bRJxy7AbFnLa 1HKNCCd5mvrY99ioPQfUnDg2wkgCNvVA8M 1F1bRXmoQX9U2aqND36Uzw92EQdqSVjGru 1155jCBDHzdfbEXDMtFSQhVFpQuZewU3qD 1JQDayFfSkJvZ52jbJv8SZNE3joXLv3Ywk |
| 1Pgopx47qYzfW2YTUBCMutoNeMjxf47iqF 3QeLaBDPkLjrCRonr2vtvtrNH8ieeVN18d 16vnhg2PnFBm68CVQrcVSvpBVZrSwu8fcH 1DszZPG4ubAHJ5F1cgSLm2nRJwaYXYLi2f 194KZcRtTmrfa5shfyuEzvsVY16GuQLq9d | 3BGjNdCsb2v3K5sEmcUvcFXRxKCLSrSyTj 16T6Duph2tTP4nciWkNV7Z7HYDzQPiohsS 36GmNTX467AnVddbXteNMCE7fFT9AMqTYo 1NLpSqFJtaR4Df3SnEwTSV4aA51sDhQM7j 1GDdNFgrwcua54ob3NKZnEzoFiWf5d6Zkz 3QxHS7UsDqLNX5uYtAaoztafUBpWeG4rbv | bc1qkl508lqgmg052mu0vu4flg022l74s7s0styjvp 1GZsBEuybC15axLkKhWw6LXjepoB1EMeB6 1BDn8wXEodpMzP4G7V27Nztv4vp7pHrPW8 1KghogGG2D6xzFvLwx6uTr5YGNFT5jC3P 1GoCEuaDzegBYn2ThFFfrG87Xa6ggHZFfT |
| bc1q2j46da5ht2mqfz6tyta5eupujtdy9wzn0tuj8r 34T8Zk7ExYJfmdgnNfr1KMtRZ6fSn8caL4 145bsmL93icXQAEQNYPx7NGkMLyZYfbztr 35G6CmwJuXMQASjATphQvvXLxgHgV9bFce 1QDBMM5VUYnYWX3JBH8kjSn6yt82RMpHVt | 3NNi3mZhrBpx7nFrxgG5PTPpo9abGUwoCD 1FLTK2gbwZowdWY65d4UZfVAqXVbB3EqYm 1KpudrBRpjZxJ2ZBeYy6R8xSeECSFrAdyz 15e6XbibjXrYqZ8fkqus4xoR4G9qbmXCF9 1DFBkadYZSfAmdAff5qagFKoDuWKAuSYoP | 18a67Kko8FSHM95JkaX2nCiKMomT7mEG99 1QE1ZjzeV13pBAMbzfBdZ8oC23F7ugx6Tj 16e7o53A27iBfKhMLLMw49h8ABUps8d2iV 1HnBgKUmoDvmCncmHRj8d66ZJUhh6hbcRA 1Nd2RhFaXLGdUBVNviZbdwvSxFWiuAq2NM |
Hack Aftermath
Actions Taken by Cheese Bank
- Temporarily paused deposit function.
- Informed main exchanges about the attack.
- Cooperated with security experts and blockchain analysis providers.
- Reviewed development and security processes.
- Filed investigations in related countries.
- Implemented fixes to the relevant bugs involved in the incident, including modifying the LP price generation mechanism and setting price refresh thresholds.
Initial Response and Tracking Efforts (November 24, 2020)
Tracing and Identifying Suspect:
Cheese Bank announced on Twitter that they had traced some of the stolen assets and related individuals, focusing on a suspect identified as “Mr. Zhang” in Zhejiang, China.
The team made contact with Mr. Zhang, issuing a warning that if the illegal gains were not returned that day, they would hand over all relevant evidence to the Chinese police.
Stance on Decentralization and Judicial Intervention:
In a subsequent tweet, Cheese Bank emphasized its nature as a decentralized product and its general reluctance to involve centralized judicial institutions.
However, they stressed that their users’ assets should be protected from occupation by malicious actors, expressing their commitment to using every means to fight for their recovery.
Further Actions and Ultimatum (November 24, 2020)
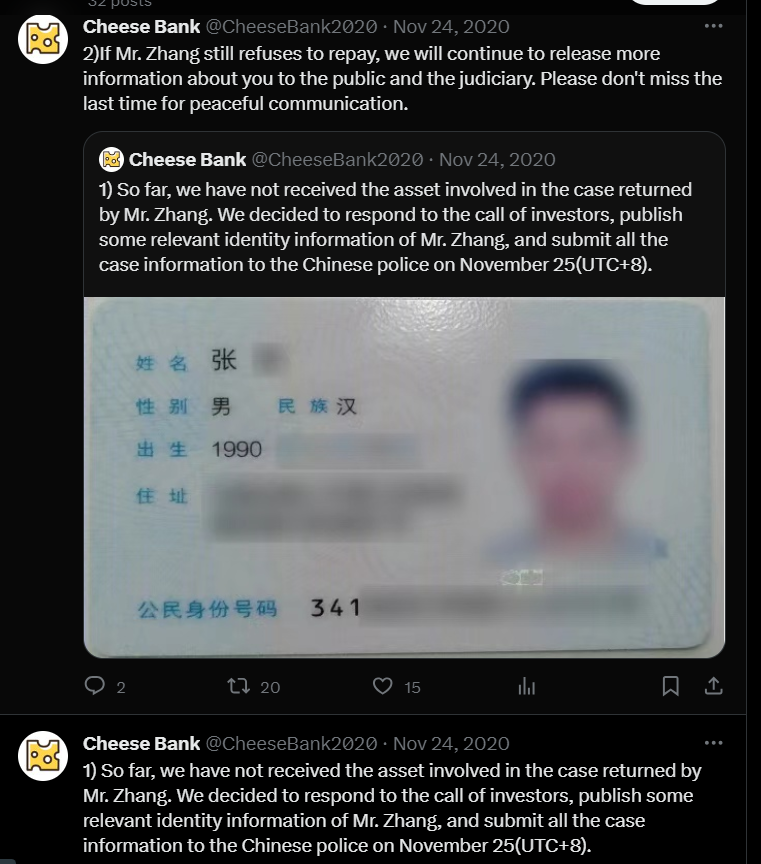
Lack of Cooperation from the Suspect: Cheese Bank updated that Mr. Zhang had not returned the assets involved in the case. Consequently, they decided to respond to investors’ calls by publishing some of Mr. Zhang’s identity information and planning to submit all case information to the Chinese police on November 25 (UTC+8).
Warning to the Suspect:
The bank warned Mr. Zhang that if he continued to refuse the return of stolen funds, they would release more information about him to the public and judiciary. They urged him not to miss the last opportunity for peaceful communication.
Case Handover to Police (November 26, 2020)
Formal Police Involvement:
Cheese Bank announced that the case involving Mr. Zhang had been formally transferred to the police for handling. They assured that relevant information would be announced successively, provided it did not affect the progress of the case.
Subsequent Silence on the Matter
Following these updates, there were no further releases or updates from Cheese Bank’s Twitter account regarding the case or the recovery of the stolen assets. The situation remains to be clarified regarding the final resolution or recovery of funds.
Lessons Learnt
The Cheese Bank hack underscores several critical vulnerabilities in DeFi platforms, particularly in Oracle security, smart contract integrity, and the handling of flash loans.
Below are expanded lessons learned and mitigation strategies that Cheese Bank and similar DeFi platforms can implement to prevent future hacks:
Strengthening Oracle Security:
- Implement Multi-Source Price Feeding: Instead of relying on a single AMM-based oracle, use multiple price feeds from different sources to calculate an average price. This approach reduces the risk of price manipulation.
- Time-Weighted Average Price (TWAP) Oracles: Employ TWAP mechanisms to smooth out price fluctuations over a period, making it harder for attackers to manipulate prices through flash loans.
Enhanced Smart Contract Auditing and Testing:
- Regular Audits: Conduct thorough and regular audits of smart contracts by reputable security firms like ImmuneBytes to identify and fix vulnerabilities.
- Rigorous Testing: Implement extensive testing procedures, including stress testing and simulation of attack vectors like flash loans.
Flash Loan Attack Mitigation:
- Limiting Transaction Size: Set limits on the size of transactions or loans to mitigate the impact of a single large flash loan.
- Monitoring and Alerts: Develop real-time monitoring systems to detect unusual activities, such as sudden spikes in loan volumes or collateral values.
Improving Governance and Emergency Response:
- Decentralized Governance Mechanisms: Implement a robust governance framework that allows for quick community response in case of detected vulnerabilities or ongoing attacks.
- Emergency Protocols: Establish clear emergency protocols, including the ability to pause contracts or transactions in case of a suspected attack.
Enhancing User Awareness and Education:
- User Education: Educate users about the risks involved in DeFi platforms and the importance of security practices.
- Transparent Communication: Maintain transparent communication channels with users, especially regarding security measures and responses to potential threats.
Collaboration with the Broader DeFi Ecosystem:
- Sharing Intelligence: Collaborate with other DeFi platforms to share intelligence about emerging threats and best practices.
- Joint Initiatives: Participate in or initiate joint efforts to develop industry-wide standards and solutions for common security challenges.
By implementing these lessons and strategies, Cheese Bank and other DeFi platforms can significantly enhance their resilience against similar attacks in the future, protecting both their operations and their users’ assets.
Conclusion
The Cheese Bank hack has put the spotlight on the inherent vulnerabilities in DeFi platforms, particularly emphasizing the risks associated with relying on Automated Market Maker (AMM)-based oracles for price measurement.
This incident demonstrates how attackers can exploit these oracles to manipulate market prices and execute fraudulent transactions. The ability to artificially inflate or deflate asset values through such manipulation poses a serious threat to the integrity and stability of DeFi systems.
It calls attention to the urgent need for more resilient and secure mechanisms in managing and verifying price data within these platforms.
To address these vulnerabilities, DeFi platforms must consider implementing more robust security measures. This includes the integration of diversified oracle systems that do not solely rely on AMM-based data, thereby reducing the risk of price manipulation.
Regular and comprehensive security audits conducted by specialized firms like ImmuneBytes can play a pivotal role in identifying and rectifying potential security flaws.
These audits should extend beyond mere code review to include a thorough analysis of the platform’s interaction with external data sources and its response to market anomalies.
Such proactive measures are crucial in enhancing the security framework of DeFi platforms, ensuring the protection of assets, and maintaining user trust in these emerging financial systems.

