Whether in Web 2.0 or Web3.0, hackers have been a scary part of both, looking for data theft and other vulnerabilities in the web application. Therefore, managing the security aspect of your project is of utmost importance. One such way of doing this is Penetration testing.
Penetration testing is an offensive security strategy that deploys ethical hackers to actively look for vulnerabilities in your project, making it insusceptible to hacking.
Out of the different forms of pentesting, this blog is going to talk about internal penetration testing methodology.
Internal pen testing provides a periodic means of screening for your projects to detect any loopholes that come along the way.

What is Internal Penetration Testing(IPT)?
Table of Contents
The perspective of performing penetration testing differs between internal and external pentesting.
Internal network penetration testing is a process of exploiting your own system from an insider’s view to detect the vulnerabilities present. Here, the objective is to secure the system from an attacker who already has access to the system.
Internal pentesting entails an integral team of security professionals who have initial network access. They simulate an attack from an insider to determine the extent of the systemic bugs.
IPT intends to look for security gaps before an attacker plugs vulnerabilities before being exploited.
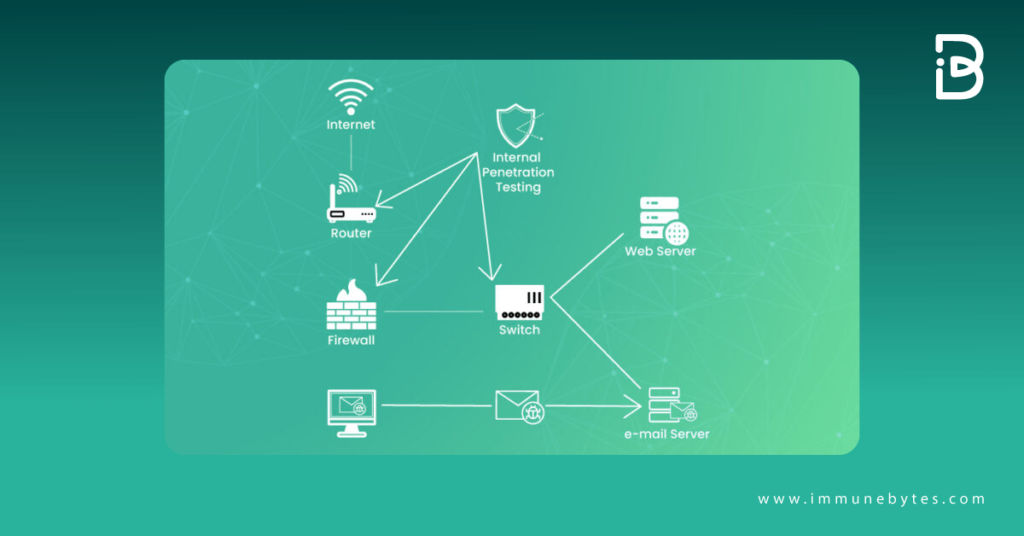
Internal penetration testing is an effective way to enhance an organization’s security by identifying potential vulnerabilities in your IT infrastructure before a hacker enters it. Also, the best part of internal pentest is it provides a dynamic and regular means of monitoring your system.
Must Read: External Penetration Testing
How Does Internal Penetration Test Work?
Internal network penetration testing is meant to exploit the system from the inside to simulate a real attack situation. It aids in identifying bugs and measuring the extent of damage they can cause to the system if exploited.
Internal Penetration Testing Methodology
The internal network penetration test checklist includes the following tests:
- Computers, workstations, and portable devices
- Points of entry
- Servers
- Wireless networks
- HVAC systems with internet access
- Firewalls
- Intrusion Detection Systems (IDS)
- Intrusion Prevention Systems (IPS)
An ethical hacker performs pentests on these entities, exploiting them for vulnerabilities. Following is a step-by-step guide explaining the methodology of Internal pentesting.
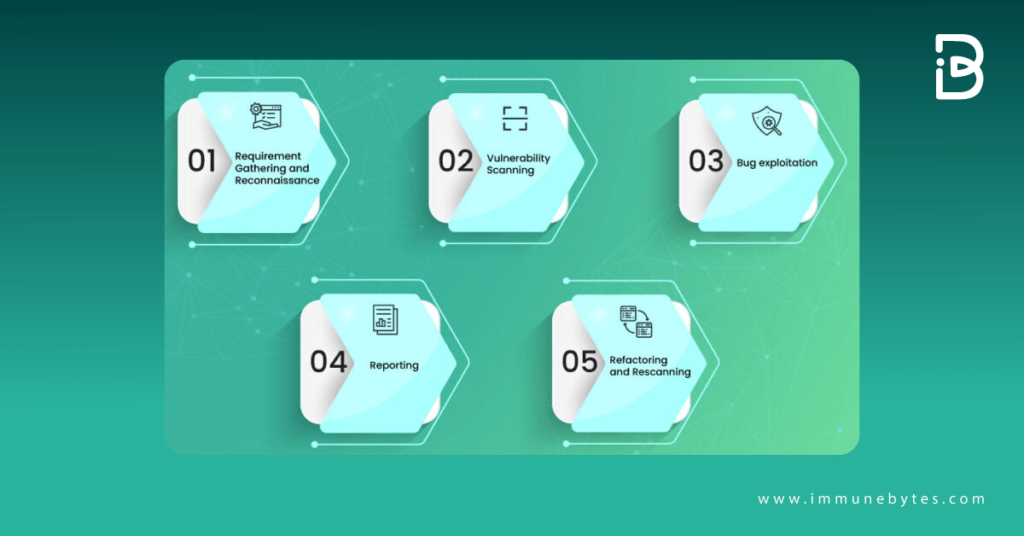
1. Requirement Gathering and Reconnaissance
The preliminary stage of penetration testing begins with fixating on the scope of the testing process. It involves analyzing the essential documents defining the intended business behavior.
This stage defines the entire roadmap, from identifying testing assets to deploying various techniques and penetration tools.
3. Vulnerability Scanning
The target code is scanned for vulnerabilities using static and dynamic automated tools.
In static analysis, the tool entirely scans the code and intrudes it for various inputs. While in dynamic testing, code is analyzed at its execution stage.
3. Bug exploitation
Probably, the most exciting and important part of the pentesting, where hacking is actually performed, is termed bug exploitation.
Here, the vulnerabilities detected at the previous stage are exploited to determine the extent of the problem they can cause. This phase’s goal is to gain access to the decryption key. If the hacker gains access to the target system, they can use it to their advantage.
Various tools such as Nmap, Wireshark, Metasploit, Nessus, Burp Suite, and others are used for bug exploitation. These tools, however, are dependent on the project’s requirements.
4. Reporting
Reports usually come with PoC(proof of concept) for pen testers to attach evidence to their findings.
The report must contain all the vulnerabilities detected along with a detailed explanation of the issues arising out of it. It should include the sensitive data that an ethical hacker could retrieve it and for how long they could remain undetected.
5. Refactoring and Retesting
Post initial pentest, the developers are supposed to work there as per the test report findings. After making the required amendments, rechecking is performed to ensure the correctness of the code.
Tools of Internal Penetration Testing
Risk assessments are part of penetration testing. Finding tools to assist your testers is a more effective and efficient way to reduce complexity.

There is no such thing as a one-size-fits-all pen-testing tool. Instead, different tool sets are required for port scanning, application scanning, and direct network penetration on different target systems. The various types of pen testing tools can be classified into five groups.
- Tools for discovering network hosts and open ports.
- Vulnerability testers examine systems, web applications, and APIs for flaws.
- Proxy tools include specialized web proxies as well as standard middleman proxies.
- Tools for gaining systemic footholds or asset access.
- Post-exploitation tools for interacting with systems, gaining and maintaining access, and achieving attack objectives.
Here are a few Internal penetration testing tools deployed by penetration testers to make your project bug-free.
- Burp Suite Pro
- Wireshark
- Nikto
- Sqlmap
- Nessus
- Archini
- Metasploit Framework
- Nmap
- Custom Scripts
- Hydra
- GHDB
- Openvas
Pros of Internal Penetration Testing
It is estimated that 47% of the time, it is the internal attacker who is responsible for the cybercrime. An internal penetration test determines what an attacker could do with initial system access. An internal network pen test can reflect insider threats, such as employees acting maliciously on purpose or unintentionally.
The following are the merits of internal network penetration testing:
- Security compliance
Deploying an internal team for pentesting prevents outsourcing and provides periodic security checks on your project. Organizations can save funds and ensure that all relevant vulnerabilities are identified and fixed by performing their own tests.
- Data protection
Both organizations and users have expressed grave concern about the data breach. Pentesters, who act like real-world hackers, simulate cyberattacks as close to real-world attacks as possible. This allows for detecting data leakage points, which can then be used to prevent future data attacks.
- Identifying the extent of errors
The foremost reason for conducting pentests is to identify vulnerabilities and the extent to which they can damage your system. This acts as a mitigation strategy to prevent future potential threats.
- Enhancing the project’s security posture
Penetration testing protects your project from threats such as:
- DDoS attacks
- Insider assaults
- Cyber-heists
What Can You Gain from Internal Penetration Testing?
In most cases, we fear outsiders getting access to the system and exploiting it for flaws. But what about the people with mal intentions who already have initial access to the network?
In many cases, an insider with access to the system or an organization’s employee could be a malicious attacker.
Internal pentest hence employs security professionals and gives them initial access to the system, similar to an employee.
An internal penetration test can credit the system with the following benefits.
- Enhancement of your security capabilities through penetration testers’ recommended remediations.
- Understanding the occurrence of an attack allows you to develop an incident response plan tailored to specific threats.
- A clear view of how a malicious attacker might compromise your cyber systems.
- Internal pentest requires less planning and can be done periodically.
Mapping Up
Secure and robust infrastructure is critical to ensuring your organization’s cyber security. Given the monetary consequences of a breach, it is prudent to conduct regular penetration testing to identify and address vulnerabilities.
Ideally, both internal and external penetration testing must be deployed to provide 360? security coverage to your project.

