BSC-based protocol, Uranium Finance, was hacked for $50 million on the 28th of April, during the platform?s migration to its v2.1 version upgrade.
Yet another DeFi protocol fell into the hands of scammers. Uranium Finance, an Automated Market Maker (AMM) on Binance Smart Chain that allows people to trade their digital assets against liquidity pools and claims to give daily dividends to its users, reported that it has suffered a security breach, with millions of dollars in Ethereum (ETH) on the move and laundered through a popular privacy tool.
As stated by the team at Uranium, Uranium migration has been exploited, the following address has 50m in it. The only thing that matters is keeping the funds on BSC, everyone please start tweeting this address to Binance immediately asking them to stop transfers.?
What caused the Hack?
Table of Contents
The hacker took advantage of a vulnerability prevailing in Uranium’s v2 contracts since the exchange upgraded over a week ago, wherein they changed their swap fees from 0.20% to 0.16%.
The attacker, after sending the minimum required tokens into Uranium’s pair contracts, drained the liquidity pools for multiple token pairs—a misplaced zero in the contract’s balance field (or rather, the lack of one in a section that manages reserves) created an open door for the attacker to strike.
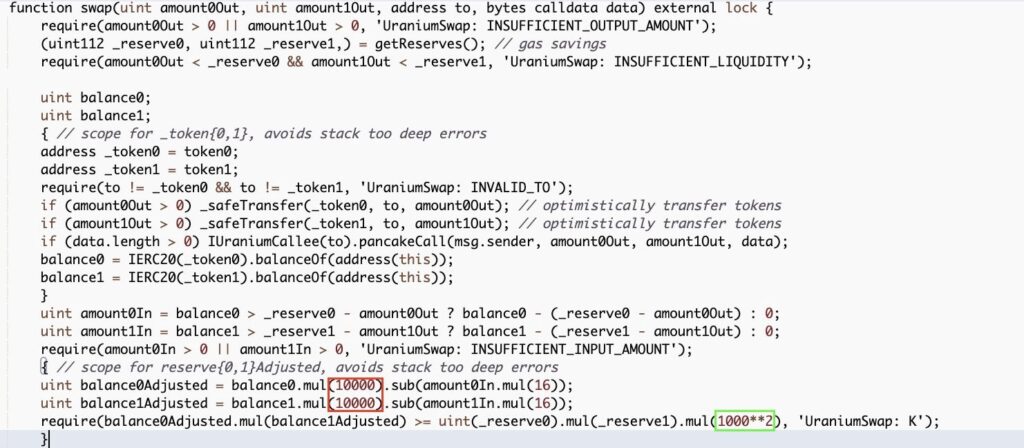
The changes made by the development team in the codebase had the consequences of adapting the sanity checks of the balances, but one line wrongly stayed unchanged, which led to the possibility of an attacker draining the reserves. Literally,a single 0 on a single line.
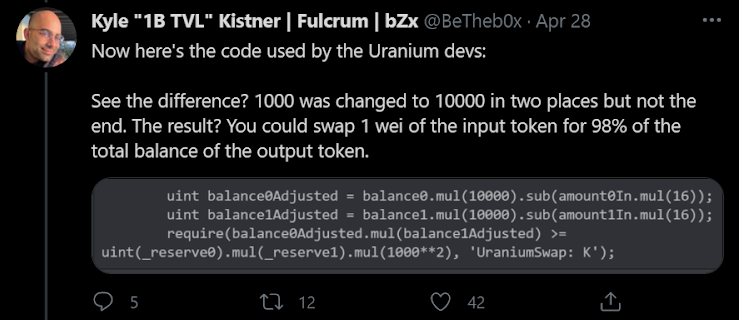
According to a member of the project’s development team, this may have been an inside job. As of the time of writing, the contract created by the hacker still holds $36.8 million in Binance Coin (BNB) and Binance USD (BUSD).
Here is the breakdown of the funds stolen/hacked:
- 34k WBNB ($18M)
- 17.9M BUSD ($17.9M)
- 1.8k ETH ($4.7M)
- 80 BTC ($4.3M)
- 26.5k DOT ($0.8M)
- 638k ADA ($0.8M)
- 5.7M USDT ($5.7M)
- 112k U92
While the team rushed to patch the vulnerability, the hacker sent the stolen funds, estimated to be 2,400 ETH, worth about $5.7 million, to the Ethereum network, exchanged them for ETH, and sent it to Tornado Cash, a fully decentralized protocol for private transactions on Ethereum.
Hacker Add: https://etherscan.io/address/0xc61429117038a1f13881dd7410b80771f28e06ec
What Happened After?
The team is in the process of contacting law enforcement and is currently cooperating with Binance’s security team. They wrote in a tweet,
“We are in contact with the Binance Security Team and are in the process of escalating this. If you are in possession of the funds or know someone who is contact me now to arrange a deal before this goes higher.”
A separate Telegram group for victims of the attack has already been devised, with over 1,200 members at the time of writing. Users have already been asked to refrain from adding any liquidity and remove liquidity if they can.
Is There More to the Story?
The theory was put forth in Uranium Finance’s Telegram channel by a user named Baymax, who is listed as an administrator.
Baymax explained that the vulnerability that led to the exploit happened merely 2 hours before version 2 of the protocol was launched. The suspicious timing of the exploit narrows down the list of potential perpetrators significantly.
Baymax explained:
“There are a total of 7 people in Uranium who knew of the exploit. From the information that we gathered with the community input, it leans towards that someone leaked information that may have led to exploiters finding out about our vulnerabilities.“
This vulnerability is present in all Uranium v2 pools and the exploit still leaves millions of dollars in tokens at risk in these v2 contracts.
?As you all know, we commissioned an audit, and among the findings was an issue of low severity. Devs dug deeper and found an issue that had the whole farm at risk, Baymax’s pinned message reads.
Highlights:
- Uranium Finance was exploited for $50m
- The incident happened during the platform’s migration to its v2.1 upgrade
- The stolen funds were exchanged for ETH and transferred to Tornado Cash
- Currently, the whole farm is at risk
- Users were asked to stop adding any liquidity
Security exploits and hacks are nothing new for the cryptocurrency community. It’s not the first hack on the BSC, many protocols have been exploited lately.
According to an estimate, there were crypto-related hacks in 2020 alone, with the exploited assets worth billions at today’s prices.
To save your project from falling into such pitfalls, get the smart contracts audited and formally verified!
About ImmuneBytes:
We are a team of India-based blockchain security professionals who are skilled and have experience in their niche.
With us, you’ll never have to compromise. We strive to push forward and provide overall surveillance and quality service to our customers. Get in touch with us to get a security audit for your smart contract.

