Introduction
Table of Contents
On September 12, 2021, the Zabu Finance project, hosted on the Avalanche blockchain, fell victim to a flashloan attack.
The attacker exploited vulnerabilities in the project’s smart contracts to steal approximately $3.2 million worth of ZABU tokens. This incident marked the first DeFi hack on the Avalanche network. This report provides a detailed analysis of the hack and its underlying mechanisms.
The Attack Flow
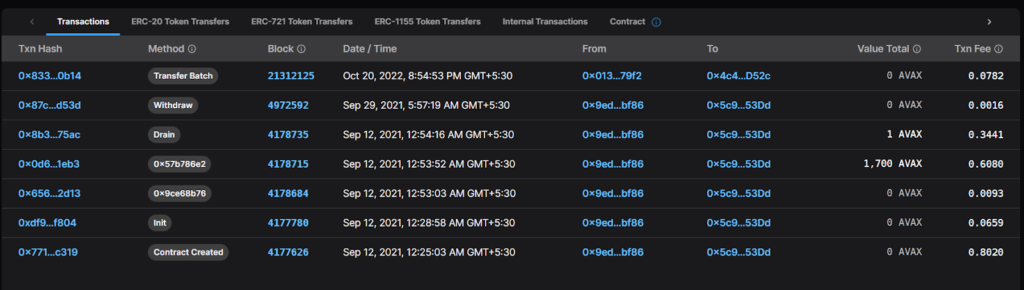
The attacker (0x9ed2D048e90CfFa5e4A778678CBc3acb8A3Abf86) orchestrated the hack by following a series of steps:
Creation of Attack Contracts:
- Attack Contract 1:
0x0e65Fb2c02C72E9a2e32Cc42837df7E46219F400 - Attack Contract 2:
0x5c9AD7b877F06e751Ee006A3F27546757BBE53Dd
Token Swap:
The attacker initiated a swap of WAVAX tokens into SPORE tokens
(https://subnets.avax.network/c-chain/token/0x6e7f5C0b9f4432716bDd0a77a3601291b9D9e985) through Attack Contract 1 on the Pangolin decentralized exchange.
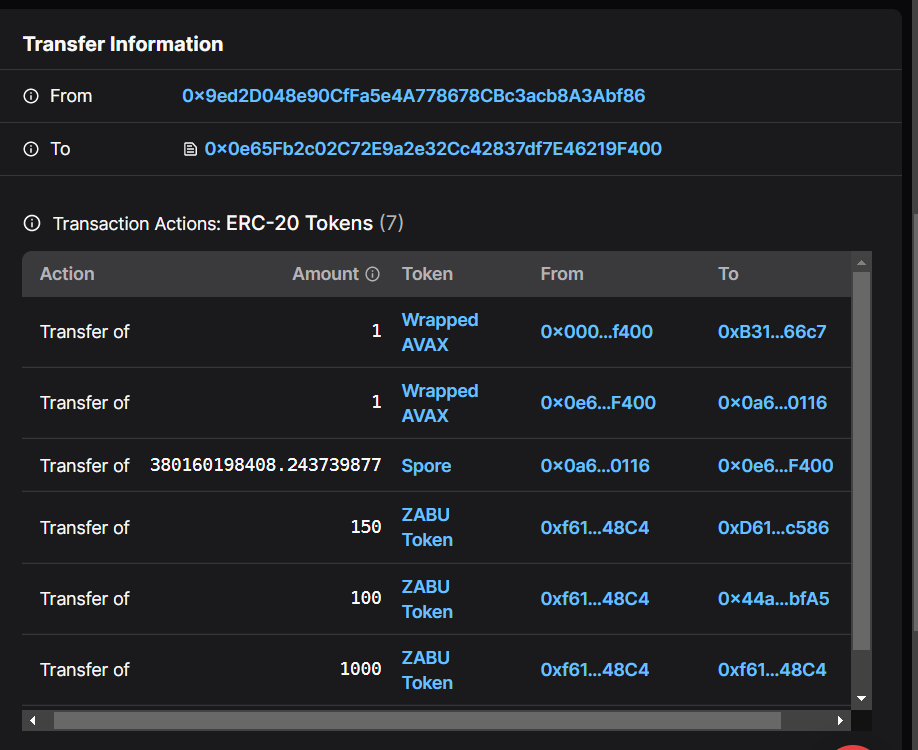
Deposit to ZABUFarm:
The obtained SPORE tokens were deposited into the ZABUFarm (0xf61b4f980A1F34B55BBF3b2Ef28213Efcc6248C4) contract, preparing for the acquisition of ZABU token rewards.
Borrowing SPORE:
To further manipulate the system, the attacker borrowed additional SPORE tokens from Pangolin using `Attack Contract 2`.
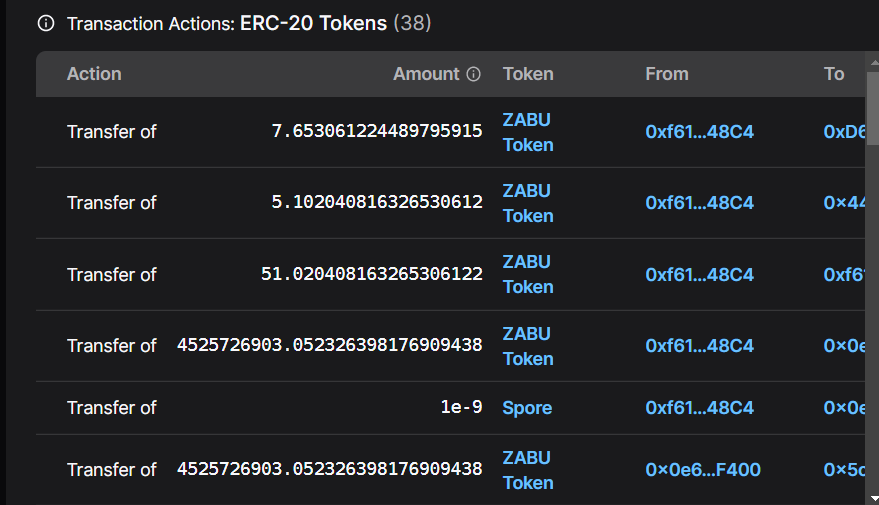
Manipulating ZABUFarm:
The attacker used the borrowed SPORE tokens to conduct a series of `deposit/withdraw` operations within the ZABUFarm contract.
Here, they exploited a critical vulnerability where:
- The SPORE tokens incur a fee during transfers, which is charged in the SPORE contract.
- The ZABUFarm contract incorrectly recorded the number of tokens staked by users without considering the fee charged during transfers.
- When users withdrew their stakes, the contract credited them with the full amount initially staked, disregarding the fee.
- This discrepancy allowed the attacker to withdraw more tokens than they had actually staked.
Transaction hash of staking operation: 0xf76b37ed46c218d4b791e9769b139c3e1f43d1888f37ff0a647c7a8bb58528fb
Transaction hash of the attack: 0x0d65ce5c7a0c072b14ec5da08488d07778f334a7ddb6b7a30df97f274f3e1eb3
Profitable Transaction:
Transaction hash of the profitable transaction where the attacker sold ZABU tokens:0x8b3042e55a63f39bb388240a089cf4d51e59abe7cb0bff303c6dbb19eaeb75ac
Reward Manipulation
By exploiting this discrepancy in the ZABUFarm contract, the attacker continuously drained the SPORE tokens’ balance within the contract to a significantly low value.
Reward Calculation
The ZABUFarm contract calculates staking rewards based on the ratio of accumulated block rewards to the number of staked SPORE tokens. As the total number of SPORE tokens in the contract approached zero due to the attacker’s manipulations, the staking reward calculation resulted in an extremely high reward value.
Token Reward Acquisition:
Taking advantage of the inflated reward pool, the attacker acquired a substantial amount of ZABU tokens through Attack Contract 1 in the ZABUFarm.
Token Dump:
Finally, the attacker proceeded to sell the acquired ZABU tokens, thereby profiting from the hack.
Root Cause Analysis
The primary cause of this attack can be attributed to the incompatibility between Zabu Finance’s staking model and the SPORE tokens’ deflationary mechanism, which charges fees during transfers.
This issue is not unique to Zabu Finance, as similar attacks have occurred in the DeFi space.
Learnings from the Hack
The Zabu Finance hack underscores several important lessons for DeFi projects:
- Smart Contract Audits: DeFi projects should undergo comprehensive smart contract audits by reputable firms to identify vulnerabilities and ensure the security of their code.
- Compatibility with Deflationary Tokens: Projects that use deflationary tokens, which charge fees on transfers, must be cautious and adapt their contracts to account for these fees accurately. Recording the actual token changes in the contract before and after transfers, rather than relying solely on the number of staked tokens, is crucial.
- Monitoring DeFi Ecosystem: Projects should actively monitor the DeFi ecosystem for similar vulnerabilities and attacks, learning from the experiences of others. The PolyYeld Finance attack in July 2021, which shared similarities with this incident, serves as a clear example of the importance of such vigilance.
Conclusion
The Zabu Finance hack is a stark reminder of the evolving threat landscape in the DeFi space. Proactive security measures, constant vigilance, and adherence to best practices are paramount to ensuring the safety and integrity of decentralized finance projects.

