Overview
Table of Contents
Transit Swap, a cross-chain trading platform supported by TokenPocket, suffered a significant security breach on October 2, 2022.
The hack resulted in the theft of nearly $21 million, including 3180 ETH (worth $4,161,559) on the Ethereum chain, 49,612 BNB (worth $14,011,105) on the Binance Smart Chain, and other tokens.
The vulnerability exploited was in the platform’s claimTokens function, which lacked proper input validation for critical parameters, allowing the hacker to manipulate contract addresses and parameters to transfer funds illicitly.
About Transit Swap
Transit Swap is a cross-chain decentralized exchange (DEX) that enables asset exchanges across different blockchain platforms.
As a prominent player in the DeFi space, it facilitates token swaps using a system of approvals and permissions. Unfortunately, the platform became the target of a sophisticated hack due to a vulnerability in its smart contract, leading to a massive loss of funds.
This incident adds to several high-profile DeFi hacks that happened in the year 2022, including the Wintermute and Curve Finance breaches, highlighting the escalating security challenges in the blockchain and DeFi sectors.
Root Cause of the Hack
The root cause of the Transit Swap hack was a critical vulnerability in the platform’s claimTokens function. This vulnerability arose due to insufficient input validation for key parameters within this function.
In the context of Ethereum token transfers, this function plays a crucial role as it involves calling the token’s contract with source and destination addresses, along with the amount to be transferred.
Detailed Explanation of the Vulnerability
User-Provided Values Without Validation:
In the Transit Swap contract, the values for the token contract address, as well as the source and destination of the transfer, were provided by the user.
Critically, these input values were not subjected to adequate validation checks before the contract made an external call to execute the transfer.
Exploitation of the claimTokens Function:
The attacker manipulated these vulnerabilities by providing specific values for the token contract address and the transfer parameters.
By doing so, they were able to redirect the transferFrom function of a token contract to execute unauthorized transfers.
Abuse of User Approvals:
Users of Transit Swap had to create approvals, allowing the platform’s permissions management contract to withdraw tokens from their wallets.
These pre-existing user approvals, when combined with the flawed claimTokens function, enabled the attacker to illegitimately withdraw approximately $21 million in tokens from multiple user wallets.
Attack Mechanics Involving Multiple Contracts:
The attack was orchestrated using multiple contracts within the Transit Swap ecosystem:
An entry contract (0x8785bb8deae13783b24d7afe250d42ea7d7e9d72) determined the path for the token transfer.
A routing proxy contract (0x0B47275E0Fe7D5054373778960c99FD24F59ff52) was used to initiate the attack via the claimTokens function of another contract (0xed1afc8c4604958c2f38a3408fa63b32e737c428).
Failure of Contract Interactions:
- The routing bridge contract’s
callBytesfunction was invoked with constructed data from the routing proxy contract, but neither contract performed adequate checks on the incoming data. - The
claimTokensfunction was then used to redirect user tokens to the attacker’s address, exploiting the fact that the user had authorized the permissions management contract.
Contract Addresses Involved:
- Entry Contract:
0x8785bb8deae13783b24d7afe250d42ea7d7e9d72 - Routing Proxy Contract:
0x0B47275E0Fe7D5054373778960c99FD24F59ff52 - Vulnerable Contract (
claimTokensfunction):0xed1afc8c4604958c2f38a3408fa63b32e737c428
The fundamental issue was the lack of strict validation of user-supplied data during token exchanges in the Transit Swap protocol. This oversight allowed for arbitrary external calls, which the attacker exploited to execute unauthorized token transfers.
Detailed Hack Analysis
Attack Transaction Links:
BSC Transaction: https://bscscan.com/tx/0x181a7882aac0eab1036eedba25bc95a16e10f61b5df2e99d240a16c334b9b189
Ethereum Transaction: https://etherscan.io/tx/0x743e4ee2c478300ac768fdba415eb4a23ae66981c076f9bff946c0bf530be0c7
Initial Contract Calls and Permissions Check:
The hacker first interacted with the entry contract to start the token exchange process.
Initial calls involved balance checks and permission validations for the transferFrom function.
Exploitation of the callBytes Function:
- The hacker utilized the callBytes(bytes) function of the routing proxy contract with malicious data.
- This function is crucial as it interprets and executes encoded function calls.
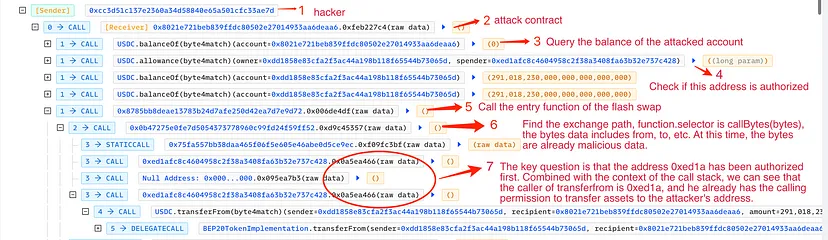
Rate Check Using getFeeRate Function:
The hacker called the getFeeRate(address, uint256, uint256, string) function of another contract (0x75fa557bb38daa465f06f5e605e46abe0d5ce9ec) to determine transaction fees.
Critical Exploitation of claimTokens Function:
- The final and most critical step was calling the claimTokens(address, address, address, uint256) function of the target contract.
- This function erroneously authorized 0xed1afc8c4604958c2f38a3408fa63b32e737c428 to perform transfers.
- The function executed transfers with various branches inside, allowing the theft of funds.
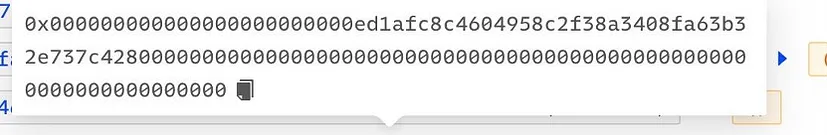
Manipulation of Data and Unauthorized Transfers
- The attacker crafted data that neither the routing proxy, the routing bridge, nor the permissions management contract could adequately validate.
- The routing bridge’s callBytes function was invoked with this manipulated data.
- The data designated the claimTokens function to transfer tokens to the attacker’s address.
- This resulted in the theft of tokens from all users who had authorized the permissions management contract.
Stolen Fund Details
The Transit Swap hack resulted in the theft of significant cryptocurrency assets, which were subsequently moved through various channels:
- Initial Transfer to Tornado Cash: The hacker transferred 2,500 BNB to Tornado Cash.
- Use of LATOKEN and Other Services: Examination of the hacker’s transaction history revealed interactions with LATOKEN and other financial services for the purposes of depositing and withdrawing funds.
Hack Aftermath
The aftermath of the Transit Swap hack has seen significant efforts towards recovery and legal negotiations:
Recovery of Stolen Funds:
- Initial Recovery: Transit Swap, with the assistance of security firms like security firms, successfully recovered approximately 70% of the stolen funds, totaling about $18.9 million. This was achieved by triangulating the hacker’s IP address, email address, and associated on-chain addresses.
- Public Statement: Transit Swap communicated these developments through a blog post and Twitter, highlighting ongoing efforts to recover more assets and the continued tracking of the hacking incident.
- Agreement with Hacker: On October 10, an agreement was reached with the primary hacker for the return of funds. The hacker consented to return an additional 10,000 BNB, valued at roughly $2.74 million, in exchange for legal immunity from Transit Swap. In recognition of exposing the security vulnerability, the hacker was allowed to retain 2,500 BNB, valued at approximately $685,600.
Actions Against Imitator Hackers:
- The hack led to other individuals mimicking the security breach, exacerbating the loss to over $23 million in user funds.
- Transit Swap set a deadline of October 12 for two hacker-imitators and one hacker-arbitrageur to return the stolen funds. Failure to comply would result in legal actions, as stated by the developers.
Ongoing Security Measures:
- The security teams and project teams involved continue their vigilance in tracking the incident and engaging in communications with the hacker, using both email and on-chain methods.
- The Transit Swap team emphasizes their commitment to recovering more assets and enhancing security measures to prevent future incidents.
Contextualizing the Hack:
The Transit Swap hack is part of a larger trend of DeFi-related exploits witnessed in the same year, including the significant $160 million Wintermute hack and the $570,000 Curve Finance hack.
Mitigation Steps to Avoid Such Hacks
- Strict Input Validation: Proper validation of all input parameters in smart contracts.
- Regular Security Audits: Frequent and thorough security audits by reputable firms to identify vulnerabilities.
- User Authorization Checks: Enhanced checks for user approvals and permissions in DeFi protocols.
Conclusion
The Transit Swap hack underscores the critical importance of rigorous input validation in smart contracts and the potential risks associated with user approvals in DeFi platforms.
While a significant portion of the funds has been recovered, the incident highlights the ongoing challenges in blockchain security. Engaging services like ImmuneBytes for regular security audits could be instrumental in identifying and mitigating such vulnerabilities before they are exploited.

