Blockchain technology’s prospects remain prominent with the constantly changing scenarios within the security domain, creating a sudden buzz worldwide. And as a well-acknowledged fact, smart contracts are the core of every blockchain. Thus, the role of blockchain security services is pivotal.
These go hand in hand with revolutionizing efficient and smoother transactions and workflows without the interference of a central authority. Although the trajectory of growth toward enhancing blockchain technology focusing on smart contracts is progressing, there are still many loopholes in reviewing the security of smart contracts.
Security remains one of the greatest concerns regarding smart contracts; even its minutest flaw can lead to major financial losses. Developers must prioritize security when writing smart contracts. Also, the role of smart contract auditors is omnipotent here to free the code from every possible vulnerability they find.
This blog will give you some security tips while writing smart contracts. Try sticking to these if you wish to avoid falling prey to expensive hacking exploits! ImmuneBytes is where we will cater to all your queries within a jiffy.
Top 5 Security Tips to Consider While Writing Smart Contract
Over the years, we have gained prominence within this industry and slowly evolved as a Web3 cybersecurity firm. So, we have a list of the top 5 security tips we would like you to follow while writing your smart contracts.
These are:
Think and Brainstorm Before Writing the Contract
To do a well-designed project, you must devote ample time to thinking about it. As a result, you can write professional code with a trusted algorithm. All you need to consider is how to build the project logic. For this, you can draw the architecture instead of just starting with writing the code quickly. It is the secret to being a professional developer.
Make It a Habit to Use the Latest Versions of Programming Languages.
Be it solidity or any other programming language you use to write smart contracts, ensure it is the latest one. The latest versions have a lot of advantages over the older versions, like they are more secure, have more libraries, provide comfortable syntaxes, optimize codes, and more. So, if you use the latest version, you will be in your comfort zone.
Never Call the Untrusted Contracts.
Calling untrusted contracts is very harmful. Here’s an example.?
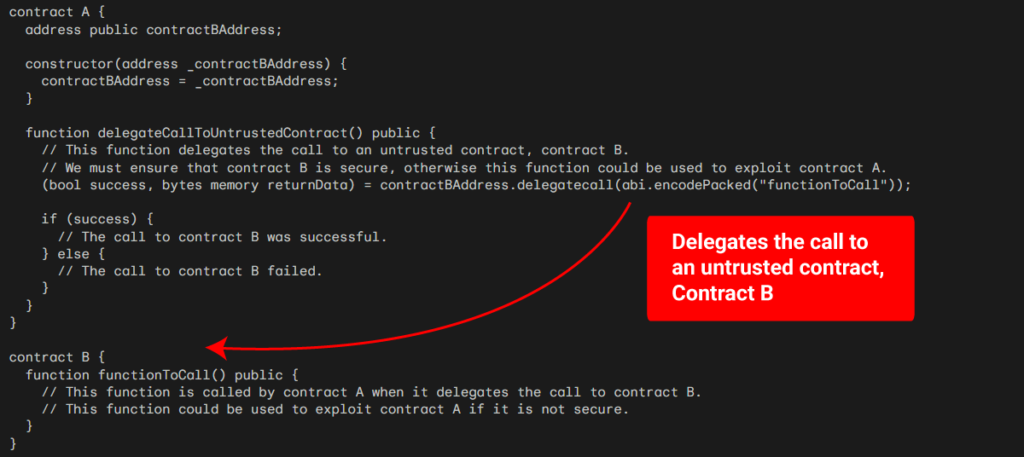
As you can see in the code above, you must ensure that the delegatecall is used securely. The delegatecall has call functionality at a low level. When we manage the contracts, contract B’s code will run using the parameters of contract A if contract A conducts a delegate call to contract B. To use the deployed address in contract A, we must first deploy contract B. On the other hand, any external contracts will challenge contract B if the owner does not modify contract B because contract B is unreliable.
Avoid State Change After an External Call
For this, the best way is to set up a Check-Effects-interaction pattern. Then, it will get easier for you to understand. Below is an example of withdraw function. Let’s describe the safe and unsafe code in it.?
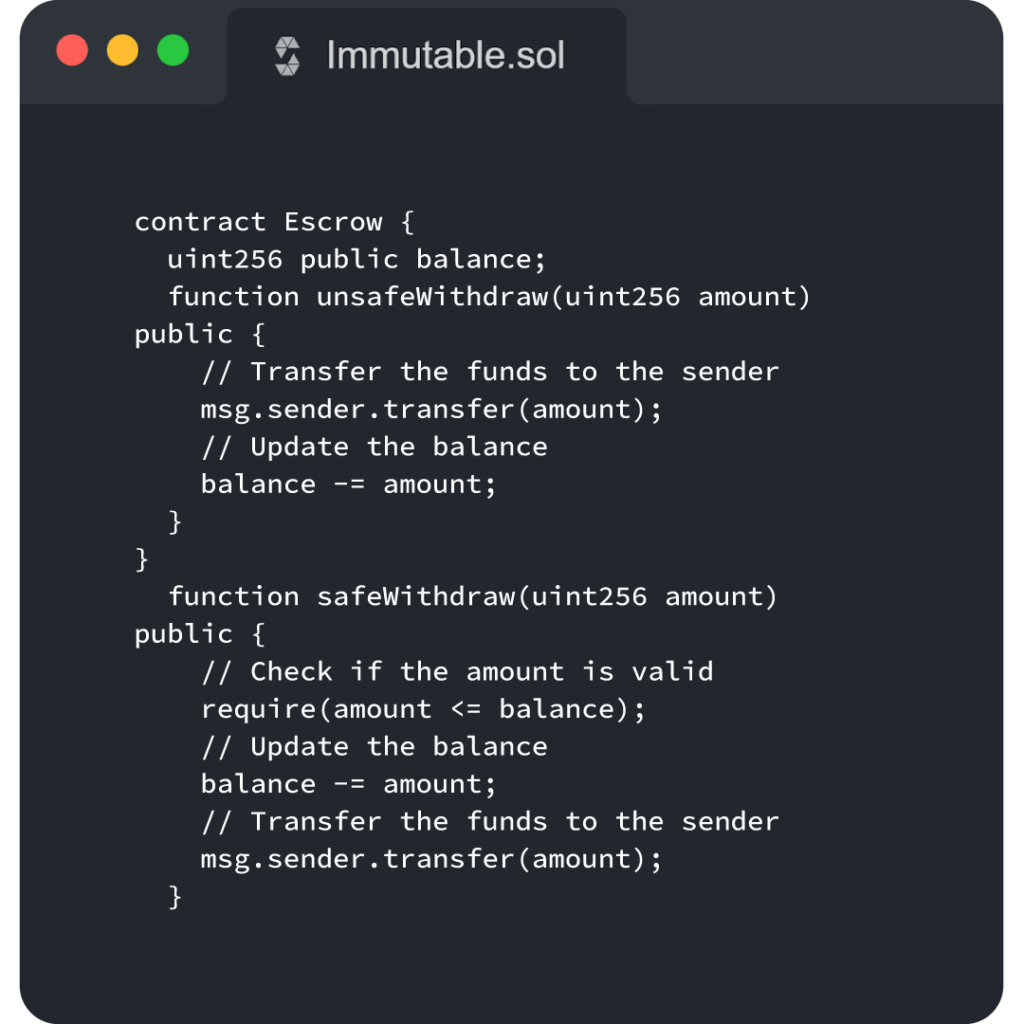
In this instance, the Escrow contract has two withdraw functions. Both safeWithdraw and unSafeWithdraw functions are available. The Check-Effects-Interaction pattern covers these. As we can see from the unSafeWithdraw function code, if we don’t follow the pattern, customers can withdraw from the Escrow contract an amount that is greater than what they initially put. Line 4 must therefore go into line 3 in contrast. Here, we have the safeWithdraw function.
Reentrancy and Ownership Takeover
You risk a reentrancy attack when you design a function that calls another untrusted contract externally before it resolves any consequences. Reentrancy assaults fall into two categories: single-function and cross-function reentrancy.
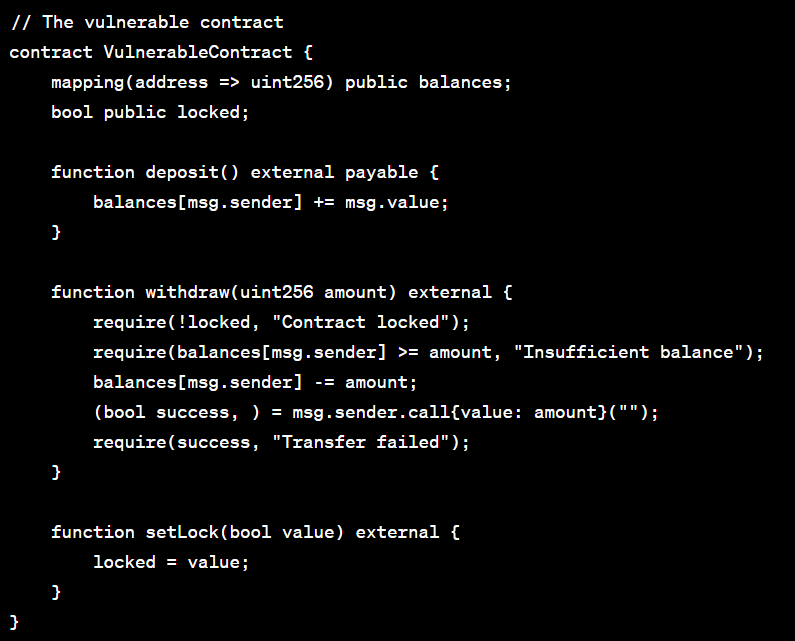
The code above demonstrates a single function reentrancy attack. Attackers can repeat interactions that would not have taken place once effects were resolved by making a recursive call back to the originating function.
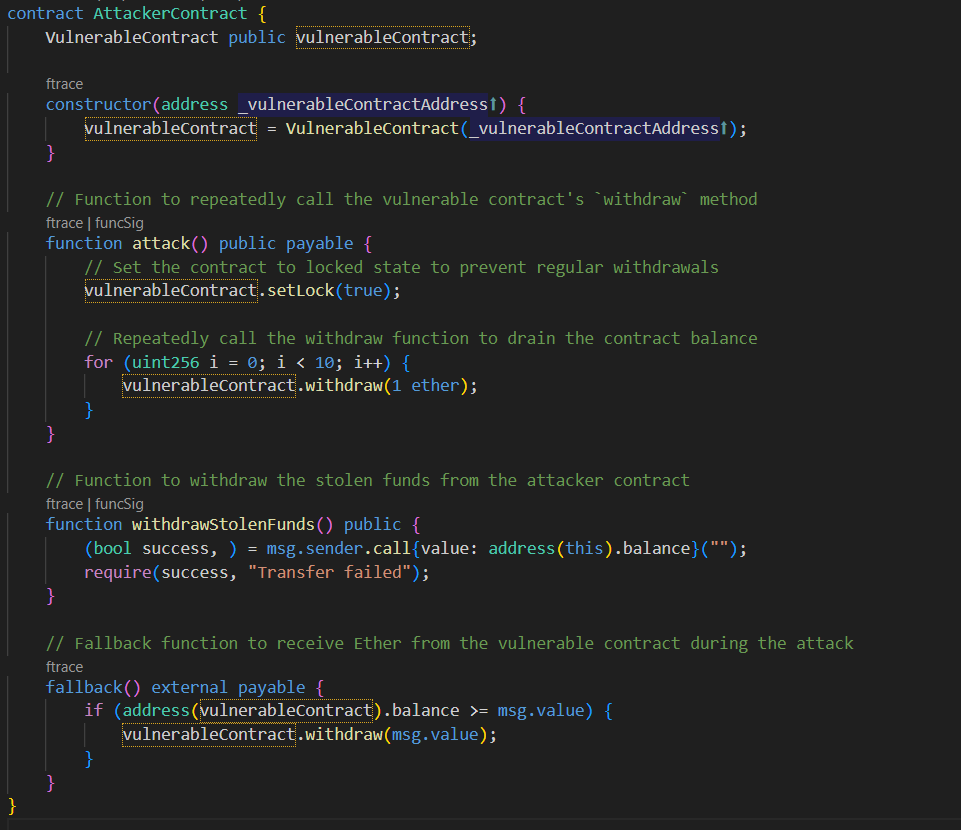
Before the ramifications of the aforementioned code are addressed, the attacker repeatedly calls the sendMoney method. In order for the attacker to possess more money than was first deposited. Here, there are two ways to stop this.
- Before calling external contractors, ensure all state modifications have taken place.
- Utilize function modifiers to stop re-entry.
Final Thoughts:
Attacks will get more sophisticated and include intricate interactions between functions and contracts in order to change the state. The greatest thing we can do to remain ahead is to use best practices and the checks-effects-interactions pattern to organize our functions, keeping interactions as straightforward as feasible. When we tighten the security parameters from our end, we are making it difficult for hackers to exploit it.
After writing the code, the last and final step is relying on the best smart contract auditors who would audit the code to find security flaws. Once they are through this process and you?ve accommodated all their recommendations, you can still think that the security of the smart contracts is robust.
ImmuneBytes is a pioneering Web3 cybersecurity organization that has provided top-notch blockchain security services to clients worldwide. In the last two years, we?ve always been up and moving to solve all the queries and come up with instant solutions. Do you wish to know more about smart contract security? Get in touch with us.

