Introduction
Table of Contents
This report details a significant exploit incident targeting Team Finance on the Ethereum blockchain, which occurred on October 27, 2022, for ~$14.5 million.
Incident Overview
The hacking incident took place when Team Finance was executing a migration from Uniswap v2 to v3.
An attacker exploited vulnerabilities in the LockToken contract, leading to the unauthorized transfer of tokens from the V2 liquidity pool to the V3 liquidity pool, namely WTH, CAW, USDC, and TSUKA.
The attacker manipulated the Initialize price of the V3 liquidity pool using `sqrtPriceX96` to secure significant refund arbitrage.
Key Data Related to the Attack
Attack Transaction: 0xb2e3ea72d353da43a2ac9a8f1670fd16463ab370e563b9b5b26119b2601277ce]
Attacker’s Addresses:
0x161cebB807Ac181d5303A4cCec2FC580CC5899Fd
0xBa399a2580785A2dEd740F5e30EC89Fb3E617e6E
Contracts Involved
- Attack Contract: 0xCFF07C4e6aa9E2fEc04DAaF5f41d1b10f3adAdF4
- Victim Contract: 0xE2fE530C047f2d85298b07D9333C05737f1435fB
- Token A: 0x2d4abfdcd1385951df4317f9f3463fb11b9a31df
Vulnerability Analysis
The core of the exploit lies in the LockToken contract’s ‘migrate’ function. The checks and validations in this function were weak, enabling the attacker to bypass them with ease and manipulate prices during the migration phase.
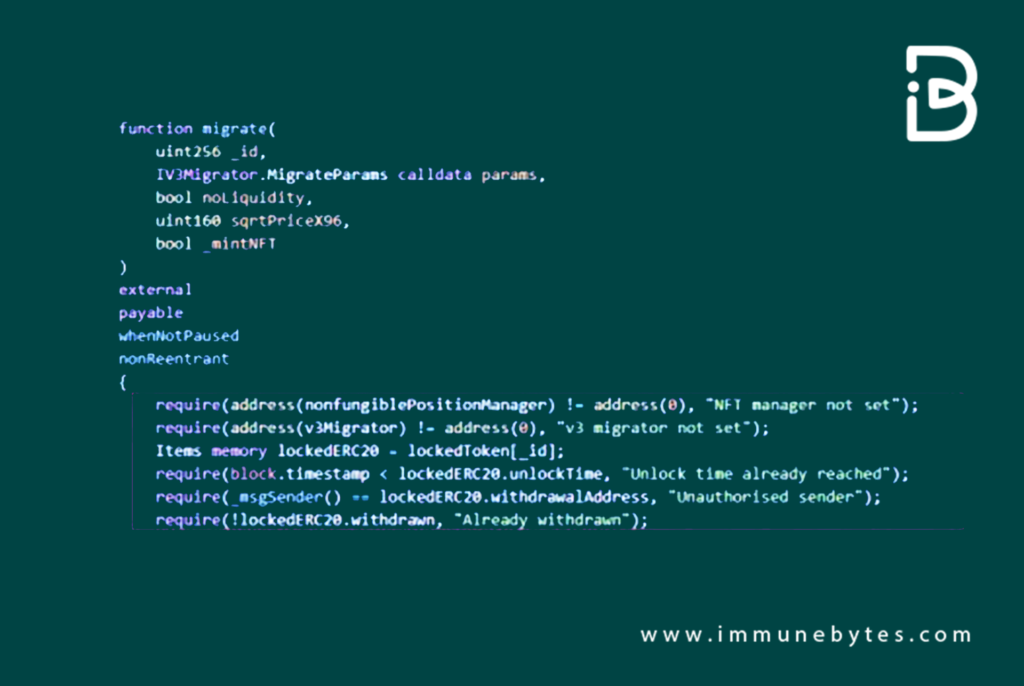
The migrate function within the compromised LockToken contract facilitates the transition of specific liquidity from Uniswap-V2 to Uniswap-V3 for users. Post-migration, users receive a portion of the tokens as a refund, determined by the prevailing price. To invoke this function, parameters such as lock ID, the duration of the lock, and a designated withdrawal address are necessary.
Attack Flow
Pre-attack Preparations
The attacker deployed the attack contract and also generated “token A” through the token contract 0x2d4abfdcd1385951df4317f9f3463fb11b9a31df.
Token Locking
The lockToken function within the LockToken contract allows users to secure their tokens and subsequently generate an NFT serving as a Liquidity Provider (LP) token.
It provides users the latitude to specify details, including the token type, quantity, withdrawal address, and the duration of the lock.
In this specific exploit, the attacker leveraged this function to lock ‘token A’, designating the withdrawal to the attack contract’s address. This action resulted in the creation of four distinct NFTs, bearing the LP ids 15324, 15325, 15326, and 15327.
Locking Time Adjustment
The `extendLockDuration` function in the LockToken contract was used to adjust the locking time for each of the NFT tokens.
Migration Preparations
The attack contract initiated a query to the LockToken contract, aiming to determine the specific number of LP tokens. This data extraction was pivotal as it formed an integral part of the parameters required to execute the attack successfully.
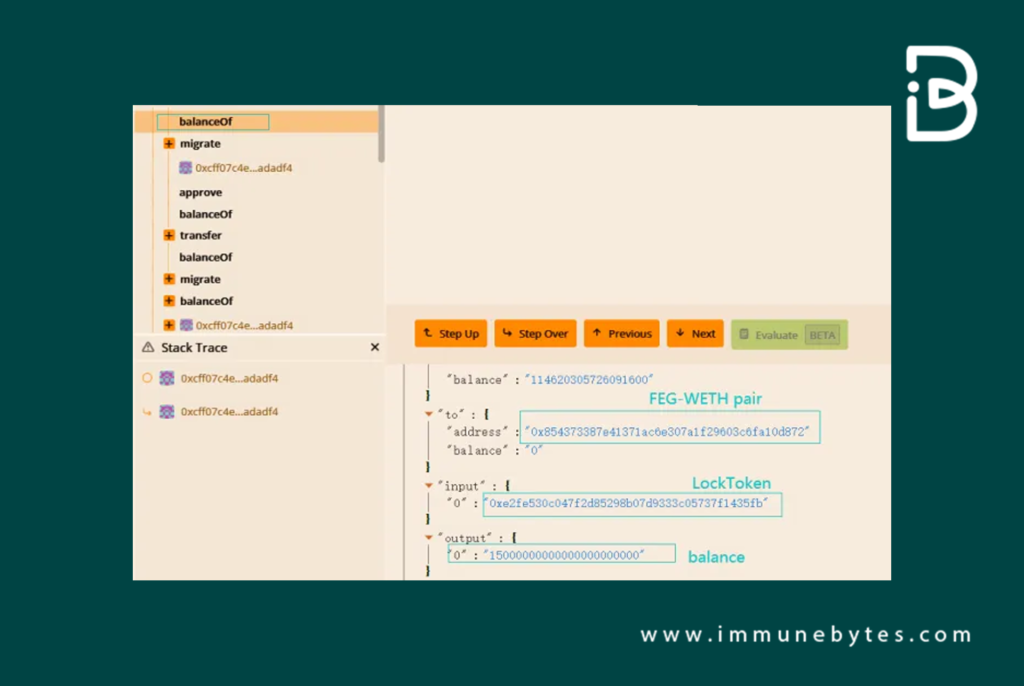
Exploitation Through Migrate Function
Leveraging the NFTs acquired in earlier stages, the attacker invoked the migrate function. This orchestrated action served two malicious purposes:
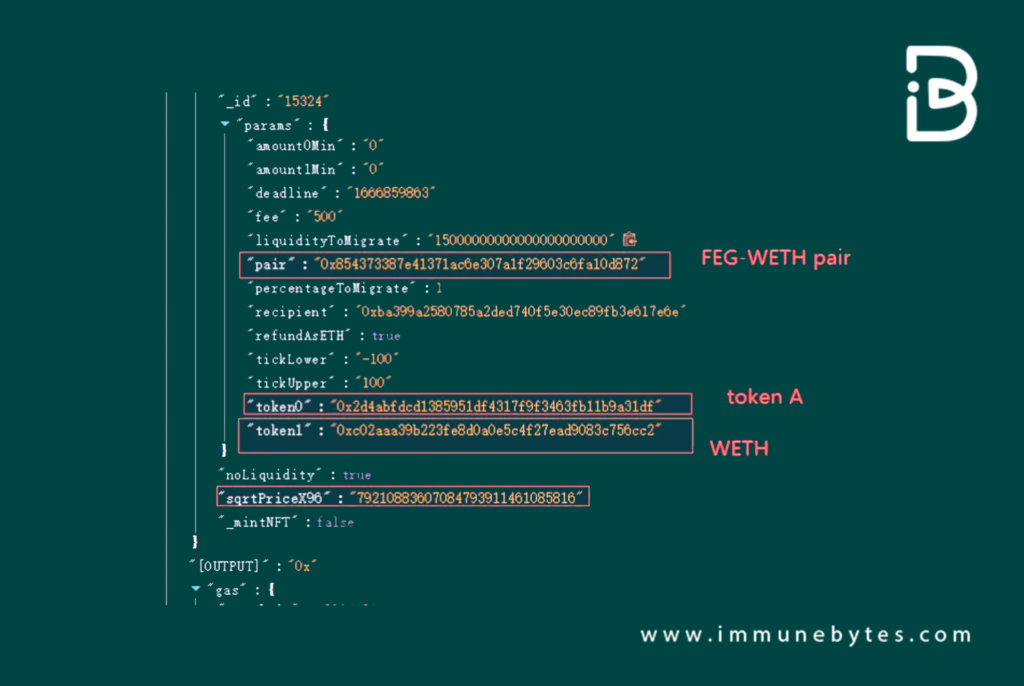
Bypassing Safeguards
The preparations using the NFTs allowed the attacker to sidestep various validations embedded in the migrate function. Specifically:
- The verification checks tied to the NFT’s id and its associated lock time.
- The requirements associated with the withdrawal address.
As a result, the NFT id that was obtained by locking the token A was now primed to engage in the migration of the FEG-WETH token pair. This occurred despite the absence of checks confirming if the user’s locked token matched the one currently in operation.
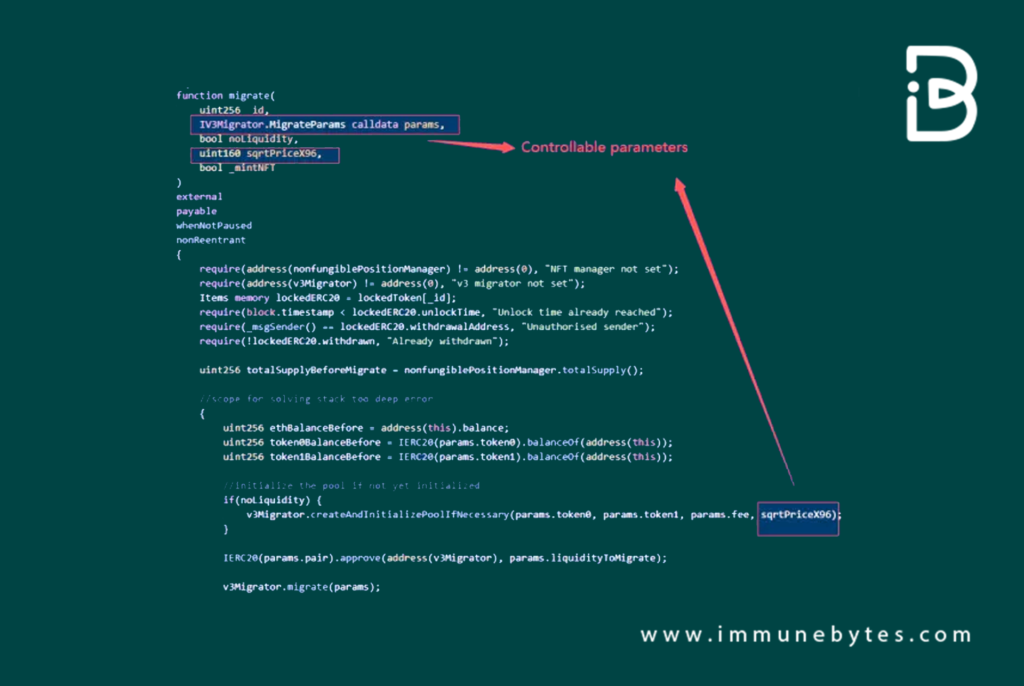
Price Manipulation
The attacker had the ability to input the sqrtPriceX96 parameter, which is integral to the price calculation during the UNI-V3 migration. This not only intensified the exploit but also gave the attacker undue advantage over price adjustments.
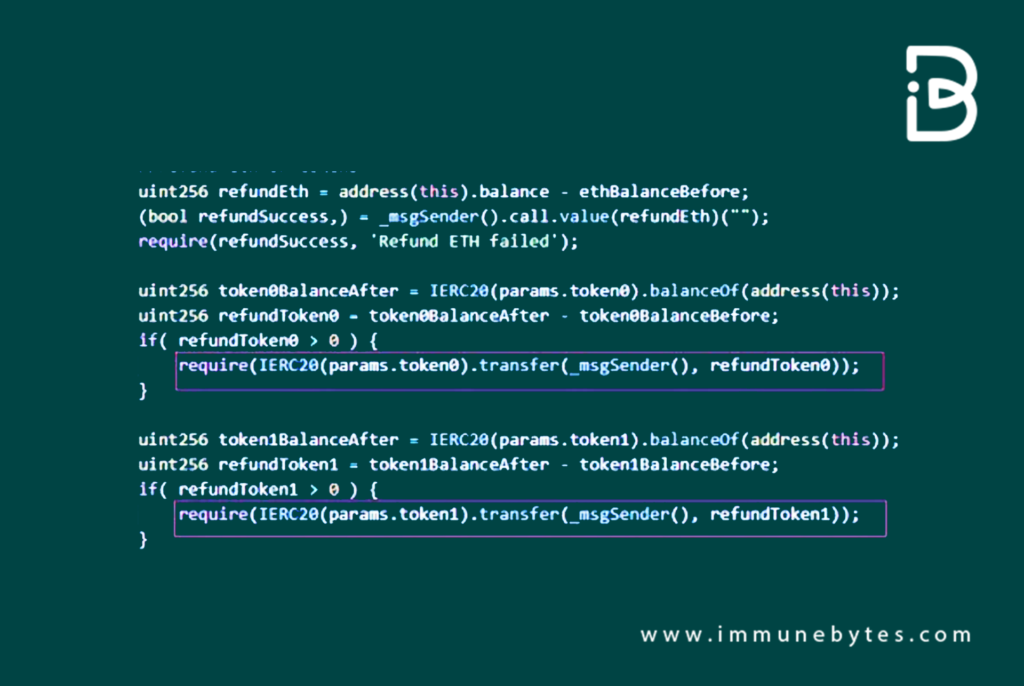
Funds Transfer
Post-exploitation, the attacker mobilized the pre-configured NFTs to secure migration refunds for four specific tokens. These were:
- WETH
- DAI
- CAW
- TSUKA
These refunded tokens, which were an illicit gain from the exploit, were promptly sent to the address: 0xBa399a2580785A2dEd740F5e30EC89Fb3E617e6E.
Impact Analysis
The stolen funds of this attack are divided as:
- ETH: 880.258
- DAI: 6,429,327.6
- CAW: 74,613,657,704.3
- TSUKA: 1,183,757.7
The combined value of these stolen funds was around $14.5 million.
Post-Incident Update
Subsequent to the exploit, which totaled a staggering $14.5 million, the attacker returned approximately $7 million in stolen tokens. The attacker identified themselves as a “whitehat” within transaction remarks.
Here are the returned amounts:
- DAI: Over $765,000
- TSUKA: 11.8 million tokens
- ETH to Kondux: 209
- ETH to Feg Token: 548
Conclusion
The Team Finance exploit underlines the imperative for robust security protocols and continuous vulnerability assessments in the realm of smart contract design and deployment.
The subsequent actions by the attacker, who self-identified as a “whitehat”, bring forth the intricate nature of cybersecurity within the blockchain ecosystem.
Therefore, conducting regular smart contract audits is absolutely necessary to uncover the bugs, which could not be identified earlier.

