Overview
Table of Contents
Sturdy Finance, a project on the Ethereum blockchain, fell victim to a security breach on June 12, 2023, where attackers exploited a read-only reentrancy vulnerability facilitated by the manipulation of a faulty price oracle, leading to a significant loss of approximately $800,000, equivalent to 442 ETH.
About Sturdy Finance
Sturdy Finance is a Decentralized Finance (DeFi) protocol that provides lending and borrowing services in the DeFi ecosystem, with a focus on delivering competitive yields for its users. Renowned for its innovative approach to decentralized financial services, the protocol stands out as a significant player in the field of DeFi.
What Caused the Hack?
The root cause of the Sturdy Finance hack was the exploitation of the Balancer’s read-only reentrancy vulnerability, which was present during the manipulation of the B-stETH-STABLE price oracle.

Price oracles are those external services that provide price feeds for smart contracts. A faulty oracle can lead to manipulated price reporting, which the attacker took advantage of and executed reentrancy attacks where a function is repeatedly called, and funds are withdrawn before the initial function call is settled.
Detailed Attack Analysis
The orchestrated attack on Sturdy Finance was a calculated and multi-step process that leveraged a critical vulnerability within the system. Here is a step-by-step breakdown of the exploit:
1. Flashloan Initiation
The attacker started by taking a flash loan, which is a feature allowing loans without collateral that must be returned within the same transaction, of 50,000 Wrapped Staked Ether (WstETH) and 60,000 Wrapped Ether (WETH) from the Aave protocol.
2. Liquidity Pool Manipulation
In this step, the attacker:
- Proceeded to add 1,100 ETH to the steCRV liquidity pool, resulting in the minting of 1,023 steCRV tokens.
- Subsequently deposited 50,000 WstETH and 57,000 WETH into the Balancer B-stETH-STABLE pool to mint 109,451.7 B-stETH-STABLE tokens.
3. Collateral Deployment and Debt Manipulation
The attacker:
- Used 1,000 steCRV and 233 B-stETH-STABLE as collateral within the Sturdy Finance platform.
- By leveraging the collateral, borrowed 513 WETH from Sturdy.
- Manipulated the price of the B-stETH-STABLE, inflating it to three times its normal value. This manipulation misled the protocol into accepting the 233 B-stETH-STABLE as adequate collateral for the 513 WETH loan. During this price inflation, steCRV was marked as non-collateral, making it unusable for further borrowing.
4. Extraction and Liquidation
With the inflated prices, the attacker withdrew the 1,000 steCRV they had initially deposited.
Once the B-stETH-STABLE price reverted to its original value, they liquidated their position by paying back 236 WETH and reclaimed 233 B-stETH-STABLE, which was now worth approximately the equivalent of 106 WstETH and 120 WETH.
5. Repetition and Profit Maximization
The sequence of earlier steps from ‘liquidity pool manipulation’ to ‘Extraction and Liquidation” were meticulously replicated across five different contracts to amplify the amount of funds withdrawn from the protocol.

6. Closure of Attack Loop
Upon completing the repeated transactions, the attacker returned the flash-loaned amount to Aave, thereby closing the loan loop and securing the illicit gains.
The attack’s sophistication was evident in how the exploiter systematically used the flash loan feature, manipulated liquidity pools, and deceitfully inflated collateral value to extract and maximize profits from the protocol.
Each step was crafted to leverage the protocol’s vulnerabilities, ultimately leading to a significant financial advantage for the attacker.
Attacker address: 0x1E8419E724d51E87f78E222D935fbbdeb631a08B
Attack contract: 0x0B09c86260C12294e3b967f0D523B4b2bcdFbeab
Attackers transaction: 0xeb87ebc0a18aca7d2a9ffcabf61aa69c9e8d3c6efade9e2303f8857717fb9eb7
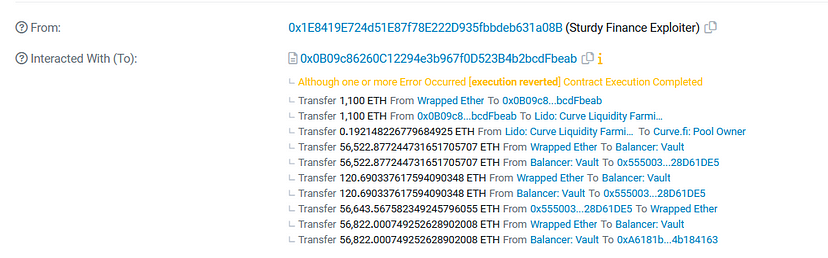
Stolen Fund Details
The stolen funds, amounting to ~ $800,000 in ETH, were routed to the crypto mixer Tornado Cash, via multiple transactions.

Hack Aftermath
In response to the security breach, Sturdy Finance took immediate and decisive actions to mitigate the impact and address the concerns of its users:
Immediate Measures Taken by Sturdy Finance
Market Suspension: The protocol swiftly suspended all trading activities to prevent further exploitation and to maintain the integrity of the market.
User Reassurance: Sturdy Finance issued assurances to its user base, confirming that no additional funds were compromised beyond the initial theft.
Bounty Implementation: A bounty of $100,000 was announced, offering the hacker a legal and financial incentive to return the stolen assets, which constituted approximately an eighth of the total value extracted during the hack.
Official Statement and Negotiations
Founder’s Communication: On June 13, 2023, Sam Forman, the founder of Sturdy Finance, publicly addressed the incident, outlining the steps taken by the protocol. He declared that the team had contacted the hacker, proposing that no further legal actions would ensue provided that the stolen funds were fully returned.
Security and Community Outreach: In addition to internal measures, Sturdy Finance engaged with the broader crypto community. The protocol’s security incident resonated across the ecosystem as attackers also commandeered eight prominent Twitter accounts, promoting fraudulent schemes.
It was highlighted that in the wake of the hack, scammers had appropriated approximately one million dollars in crypto by hijacking the accounts of notable figures such as DJ Steve Aoki, Cole Villemain, the founder of Pudgy Penguins, and commentator Peter Schiff.
Through these strategic responses, Sturdy Finance demonstrated a commitment to transparency and rectification in the face of a complex and multifaceted security challenge.
What Could Have Prevented the Sturdy Finance Exploit?
In light of the Sturdy Finance incident, several targeted mitigation strategies have been identified to bolster security against such vulnerabilities:
Smart Contract Auditing
Conduct comprehensive and regular audits of all smart contracts, ideally by reputable third-party services such as ImmuneBytes, to identify and rectify potential vulnerabilities before they can be exploited.
Reentrancy Guards
Implement reentrancy guards in smart contracts. These are state checks that prevent a function from being called again until it has finished executing, thus mitigating potential reentrancy attacks.
Oracle Enhancement
Utilize multiple reliable oracle services to fetch external data, thereby reducing reliance on a single price feed source. This can prevent oracle manipulation by ensuring that a consensus of multiple sources is required for price data.
Flash Loan Monitoring
Monitor and potentially restrict the size of flash loans or impose additional checks during their execution to prevent large-scale exploits.
Economic Incentive Adjustments
Adjust economic incentives to discourage attacks. This could involve implementing a sliding scale of fees for large transactions or operations that may pose a systemic risk.
Code Freeze and Staging Protocol
Implement a code freeze period after updates where no significant changes are allowed, and use a staging environment to simulate and monitor the behavior of updated contracts before they go live.
Conclusion
The Sturdy Finance hack underscores the persistent vulnerabilities within DeFi protocols, particularly related to reentrancy and price oracle manipulation. While the protocol’s response was prompt, the incident highlights the need for continuous security enhancements.
The future of blockchain security rests on the community’s ability to learn from such exploits and the adoption of rigorous security measures, including smart contract audits by experienced firms like ImmuneBytes.

