On 30 April 2022, Rari Capital encountered a significant security breach—a re-entrancy attack—that resulted in the loss of approximately $80M from its Fuse Pools.
The primary cause was vulnerabilities in the smart contract’s design. This report provides a comprehensive breakdown and simplified explanation of the incident.
Introduction
Table of Contents
Rari Capital, like many DeFi platforms, relies heavily on smart contracts. Smart contracts, while powerful, can be vulnerable if not implemented correctly. This report aims to shed light on the vulnerabilities that led to the attack on Rari Capital and provide insight into how similar attacks might be prevented in the future.
Attack Overview
Key Details
- Attacker’s Address: https://etherscan.io/address/0x6162759edad730152f0df8115c698a42e666157f
- Exploit Transactions: https://etherscan.io/tx/0xd9ee4fc5ee0b8815e6aae20e8bc5697ee49b8a1c76619a008bf534a4084197dc
- Attacker’s Contract Address: https://etherscan.io/address/0xE39f3C40966DF56c69AA508D8AD459E77B8a2bc1
- Transaction: https://arbiscan.io/tx/0x3212d091792f81f18a31aab753de6b3128d79dcb5e8392167249595f813203ef
Attack Sequence:
The attacker followed the step-by-step process to execute the exploit. The details of which are the following:
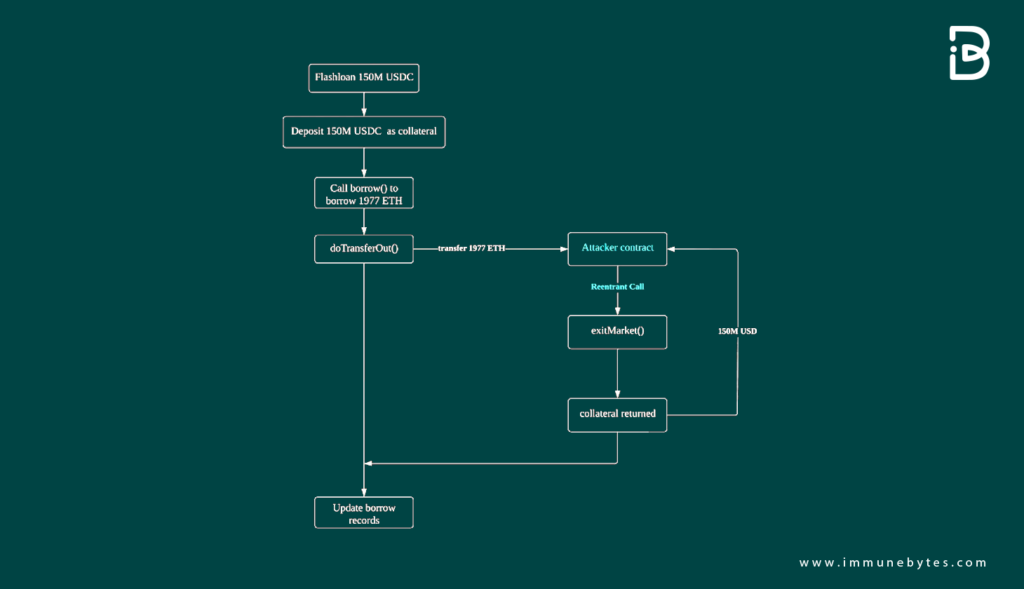
Step 1: Flash Loan Deposit
The attacker started by depositing a flash loan asset into Rari Capital’s lending pool. This asset served a dual purpose. While it was in the lending pool, it acted as collateral, enabling the attacker to borrow other assets against it.
Step 2: Borrowing ETH Using Collateral
Using the deposited flash loan asset as collateral, the attacker borrowed a significant amount, precisely 1977 ETH.
Step 3: Exploiting the doTransferOut Function
The attacker cleverly initiated a reentrant call to the doTransferOut() function. This exploit allowed him to get hold of the borrowed ETH even before the system updated its records about the borrowed amount. In other words, the system was manipulated into releasing funds without registering the debt.
Step 4: Withdrawal of Collateral
Post this manipulation, the attacker invoked the exitMarket() function. Since, according to the system’s flawed records, there was no outstanding borrowed amount (even though in reality, the attacker had borrowed 1977 ETH), the original flash loan asset was no longer held as collateral. This enabled the attacker to withdraw the initially deposited flash loan asset freely.
Step 5: Repeated Exploitation
The attacker didn’t stop at just one exploitation. He repeated this entire sequence multiple times, draining funds from various lending pools within Rari Capital.
Step 6: Concluding the Attack
Once the attacker had drained a substantial amount, he returned the borrowed amount from the flash loan. The excess ETH, which he managed to siphon off without the system’s knowledge, was pure profit. The attacker transferred this “profit” to another address, successfully concluding the heist.
Decoding the Smart Contract Vulnerability
Vulnerability 1: Sequence Mismanagement
Problem: The doTransferOut() function was called prematurely. This allowed the attacker to transfer funds before their borrowing records were updated.
Simplified Explanation: Think of it as a bank releasing funds to a customer before checking if they have the necessary credit score. By the time the bank realizes the customer’s poor credit score, the money is already in the customer’s hands.
Contract Code: https://etherscan.io/address/0xe16db319d9da7ce40b666dd2e365a4b8b3c18217code
doTransferOut(borrower,borrowAmount);
// write the previously calculated values into storage
accountBorrows[borrower].principal = vars.accountBorrowsNew;
accountBorrows[borrower].interestIndex = borrowIndex;
totalBorrows = vars.totalBorrowsNew;
//emit a Borrow Event
emit Borrow(borrower.borrowAmount,vars.accountBorrowsNew,vars.totalBorrowsNew);
return uint(Error.NO_ERROR);
}
Vulnerability 2: Fallback Function Exploitation
Problem: The attacker’s contract contained a mischievous fallback function. This function manipulated the doTransferOut() function, enabling the transfer of all ETHs to the attacker’s address.
Simplified Explanation: Imagine a vending machine that releases a soda when a button is pushed. The attacker found a way to push this button repeatedly, draining all the sodas without paying.
function doTransferOut(address payable to, unit amount) internal {
//sends the ETH and reverts on failure
(bool success , ) = to.call.value(amount)("");
Require (success,"doTransferOut failed");
}Recommendations & Best Practices
- Check-Effects-Interaction Pattern: Always follow this pattern to ensure state changes are made before external calls.
- Avoid Low-Level Calls: Where possible, avoid using low-level calls such as
.call.value()(""), which are more susceptible to re-entrancy attacks. - Regular Audits: Regularly audit smart contracts to identify and rectify potential vulnerabilities.
Conclusion
The Rari Capital Re-entrancy attack of 30 April 2022 serves as a stark reminder of the complexities and vulnerabilities inherent in the DeFi ecosystem.
Despite the advancements in blockchain technology, smart contracts—the backbone of many DeFi platforms—remain susceptible to well-crafted attacks if not meticulously designed and audited.
The attacker’s methodical exploitation of Rari Capital’s vulnerabilities underscores the necessity for platforms to maintain rigorous security protocols.
Regular smart contract audits, adherence to best coding practices, and continuous education on emerging threats are non-negotiable for entities operating within this space.
Furthermore, this incident emphasizes the importance of transparency and prompt communication with stakeholders following such breaches.
Quick and clear communication can mitigate reputational damage and restore trust in the affected platform.
In summary, as the DeFi landscape continues to evolve and expand, it is imperative for platforms to prioritize security above all else.
Failing to do so not only jeopardizes the assets of users but also the very trust and credibility upon which the decentralized finance movement is built.
The Rari Capital incident is a lesson that the entire DeFi community should learn from and ensure that the lapse in security does not happen again.

