Probably everything you read about the Metaverse on the internet starts with Zuckerberg changing facebook’s name to Meta. That one incident made many curious to know about the Metaverse.
And now it’s Microsoft’s turn, stepping on the gaming metaverse. Microsoft is currently in the process of acquiring Activision Blizzard, a leader in the game development ecosystem.
Evidently, the Metaverse is swiftly emerging as the following essential idea for businesses looking to boost engagement. But with much boost around the concept, cybersecurity threats persist.
This blog will discuss Metaverse’s cybersecurity risks and how to manage them. But let’s first start with the basics of the Metaverse.
What is Metaverse?
Table of Contents
An evolutionary iteration of the internet, Metaverse can be thought of as a virtual, online 3D Universe encompassing almost every domain of life.
In other words, a 3D digital simulation enables us to virtually experience almost every facet of the real world.
Metaverse seeks to connect several platforms, similar to how the internet connects various websites that may be accessed using a single browser.
In the 1982 book Snow Crash by Neil Stevenson, the phrase “metaverse” first appears. Their characters communicate with one another in their Metaverse’s virtual world by using digital avatars.
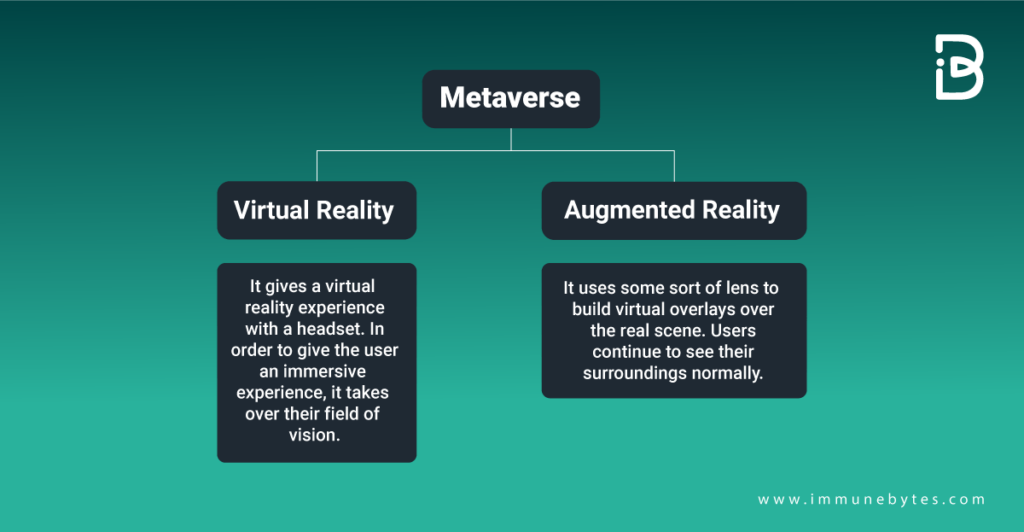
There are two primary forms of Metaverse: Virtual reality and augmented reality.
How to Get into Metaverse?
Imagine sitting in your comfortable room wearing a virtual reality headset, attending a client meeting in a pseudo-office space. Once you finish it, change the settings to your favorite game.
And BAM!!!! You are on a battlefield playing against real competitors again in a virtual space.
You can actually party, spend time with your friends, and manage your finances and portfolio with just one entity, “Metaverse.”
Although some of these facets are existential, like the gaming metaverse, the complete picture isn’t still a reality.
At present, there is no single metaverse creating a universal entity. With Web3.0 rising in space, it can potentially bring the Metaverse into existence.
Some well-known platforms of Metaverse or its alternatives are Axie Infinity marketplace, Decentraland, Sushiswap, Render, TCG world, Sandbox, and more.
Let’s discuss in brief the Axie infinity here:
Getting started with Axie infinity play-to-earn gaming platform built on the Ethereum network.
For working with Axie infinity, you have to set up a Ronin wallet followed by purchasing Axies and account setup to download and play games on the platform.
Players compete against one another in battles in the game Axie Infinity to gain cryptocurrency. Now that commercially available VR headsets have finally hit the tipping point, the popularity of metaverse games has increased significantly.
Now that we have a fair idea about the metaverse, let’s move on to the security issues related to the metaverse.
Must Read: Web3 VS Metaverse
Concerns in Metaverse Cybersecurity
With every development in the web world, cybersecurity concerns have been an integral part. Although their nature changes with the evolution in cyberspace.
In a similar sense, cybersecurity and metaverse paint an analogous picture. Following are some of the cyber metaverse concerns.
- Phishing threats, data hacking, and other malware attacks
These cyberattacks have evolved their way through the current internet iteration to the metaverse. Hackers and con artists typically desire access to your private key in order to steal digital assets from your wallet.
Cybercriminals employ phishing links that seem like legal metaverse protocols to drain investors’ wallets of digital assets.
- Safeguarding user’s virtual identity
Companies operating in the metaverse must protect all sensitive data related to online commercial transactions. In order to guarantee the long-term viability of the metaverse as a distinct business category, user identity preservation is the most critical step.
- Cryptocurrencies and NFTs
In most metaverse platforms available today, the transactions usually occur in crypto.
To prevent financial threats in the metaverse, it is necessary to verify the authenticity of the business and the individual’s identity with whom the transaction is taking place.
- Regulation
Metaverse is a reasonably new domain and is essentially unregulated by laws. Due to the unregulated nature of the metaverse, hackers can use these platforms to breach users’ sensitive information by getting through its loopholes.
- Intellectual property rights
An unregulated domain of the metaverse lays a quintessential ground for scammers to engage in unlawful activities. It is necessary to link all newly developed, acquired, and/or sold intellectual property to a real-world identity in order to verify and validate it. Otherwise, there will be an open ground for disputes, fraud, conflicts of proving ownership, and more.
- Data privacy and data governance
Data privacy encompasses securing the personally identifiable information of users by businesses. On the other hand, data governance requires a specific set of rules to be maintained in order to create a homogenous security environment for the users.
Recommended: Cybersecurity Company
How to Manage Metaverse Cybersecurity?
Organizations should strive to maintain the data they acquire and validate the third parties with whom they communicate data.
Instead of depending solely on authentication and authorization, parties must constantly examine every level of digital contact to combat the exfiltration of sensitive information.
Cybersecurity solutions will become more effective at analyzing user access and behavioral patterns on a larger scale as we move toward automation. It includes AI and machine learning participating in successfully preventing the increasing number of unknown hazards in the metaverse.
By returning users’ identities to their proper owners and dramatically reducing hacks and data breaches, Web3, which aims to build a pro-privacy, anti-monopoly web utilizing decentralization, would successfully tackle the problem of data privacy.
Using decentralized technologies is a solution to protect metaverse identification while simultaneously preventing fraud.
Wrapping Up
Despite the fact that the metaverse is still a relatively new concept, significant cybersecurity concerns associated with the same are coming up that information technology professionals must be ready to address.
Undoubtedly, this is not the end, and the dangers of the metaverse will be around with its evolution. Although, it is critical to ensure a way out of these threats. We hope metaverse developers come up with hack-proof technologies to cater to the privacy and security concerns of the users.
Additional Resources
Traits of Cyber Security Auditor

