Overview
Table of Contents
The Eminence project, operating on the Ethereum blockchain, fell victim to a hacking incident on September 29, 2020.
This exploit resulted in a substantial loss of $15 million worth DAI cryptocurrency. The methodology employed in this hack was a flash loan attack that exploited the protocol’s bonding curve and token exchange mechanism, leading to this significant financial breach.
About Eminence
Eminence, a DeFi protocol designed as a “gaming multiverse,” drew its roots from a 2016 Kickstarter trading card game named ‘Eminence: Xander’s Tales’ and garnered attention for its potential integration of NFTs.
The project, significantly linked to Andre Cronje, was in an alpha testing phase without a fully developed front-end. Despite this, it quickly attracted substantial investment from the DeFi community, largely spurred by a tweet from Cronje, highlighting its rapid rise to prominence within the sector.
Root Cause of the Hack
Primary reeason for the hack was the the vulnerability in the protocol’s unfinished state and its open access to the public without adequate warnings or safeguards.
The exploit used a flash loan attack, a tactic in DeFi where large amounts of cryptocurrency are borrowed and repaid in a single transaction.
Detailed Analysis
Incident Timeline
On Sep 28, 2020, Andre Cronje, the project’s founder, tweeted graphic designs related to Eminence, garnering interest from the DeFi communities.
Within hours, $15 million worth of DAI was invested in Eminence, despite it being in an alpha testing phase without a proper front-end. Exploitation
The Exploit
Eminence used a bonding curve for token distribution, exchanging EMN tokens for others, like DAI.
Users could either deposit DAI for EMN or burn EMN to reclaim DAI. EMN could also be swapped for other Eminence versions of popular tokens (e.g., eAAVE, eLINK).
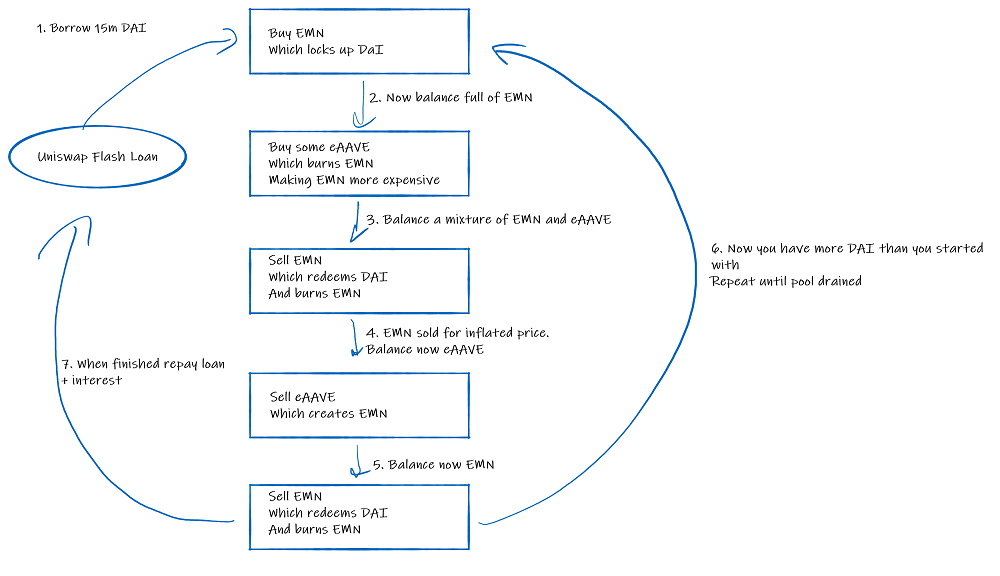
On the night of Sep 28, 2020, the attacker exploited the bonding curvy dynamics using a flash loan attack and drained the entire $15 million investment.
Attack Strategy
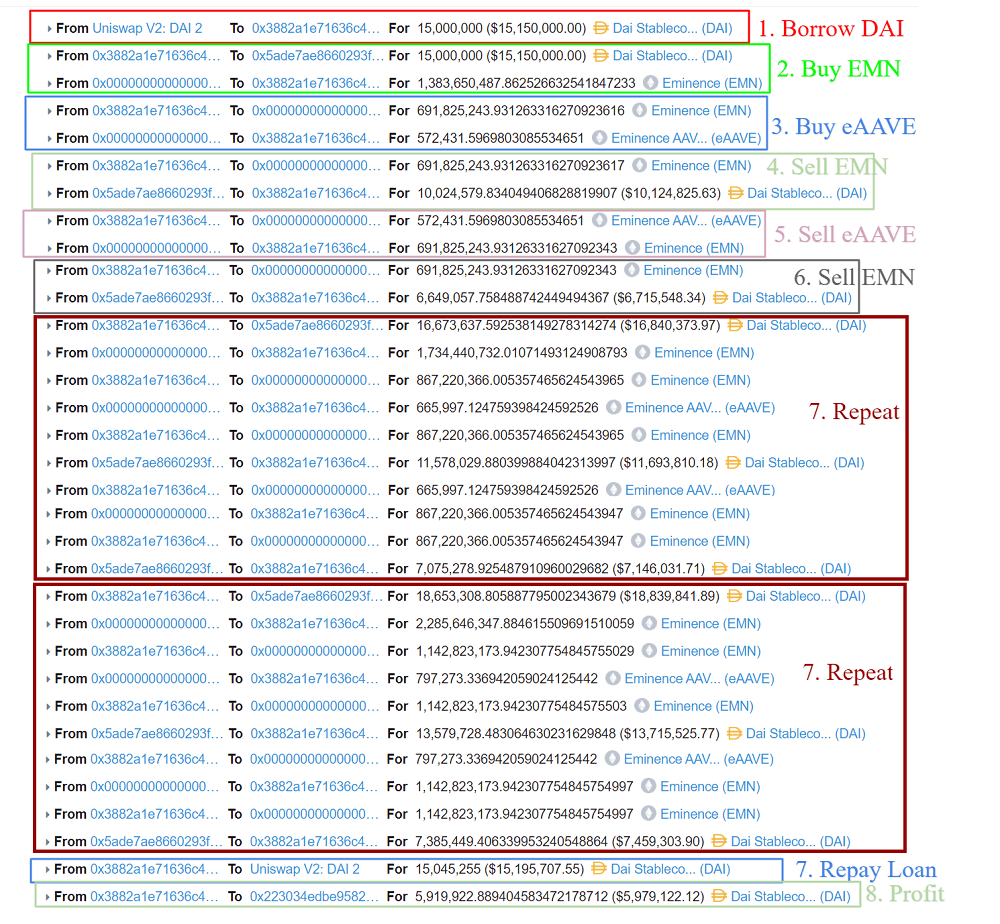
Method: Utilizing a flash loan, the attacker borrowed 15 million DAI from Uniswap.
Execution:
- Initial Purchase: The attacker bought EMN with the borrowed DAI.
- Token Trade and Burn: Half of the EMN was traded and burned for eAAVE, boosting EMN’s price.
- Conversion to DAI: The remaining EMN was swapped back for DAI.
- Repeated Process: The attacker exchanged eAAVE to mint more EMN and again traded it for DAI.
- Outcome: This cycle was repeated thrice, resulting in the hacker amassing 15,015,533 DAI.
Attacker’s Address: 0x223034EDbe95823c1160C16F26E3000315171cA9
Hack Transaction: https://etherscan.io/tx/0x3503253131644dd9f52802d071de74e456570374d586ddd640159cf6fb9b8ad8
What Happend to the Stolen Funds?
The attacker initially siphoned off $15 million but returned $8 million to a Yearn contract.
Hack Aftermath
Steps Taken by Eminence: Developers, including a Yearn core member, distributed the returned $8 million to affected users.
Market Reaction: The incident led to divided opinions in the DeFi community regarding project responsibility and investor due diligence.
Official Statements: Andre Cronje stressed his personal development philosophy and cautioned the community to wait for official project launches.
Reparations: After the exploit, developers (including a Yearn core member) formulated a strategy to distribute the returned $8 million to affected users. These preparations were made to those who traded for EMN both from the bonding curve contract and Uniswap.
Community Split: The DeFi community was divided. Some criticized Cronje for teasing an unready project while others argued that traders should not have invested without proper information. Questions arose regarding Cronje’s decision to test on the mainnet instead of a testnet.
Yearn Finance’s Stand: Andre Cronje took to Twitter to clarify his actions, emphasizing his “build for myself” philosophy and urging caution. He continued to express his commitment to the Eminence project and asked the community to wait for official announcements in the future.
The Broader Implications
DeFi’s Risk-Reward Conundrum:
The incident highlights the inherent risks in the rapidly evolving DeFi space. While traders are continually looking for the next lucrative opportunity, this comes with significant risks, especially when venturing into unvetted protocols.
Trust and Greed:
The driving forces behind this event were the DeFi community’s trust in a known figure (Cronje) and the inherent human instinct of greed. The allure of potential gains often blinds investors to the possible pitfalls.
Similar Hacks
This incident mirrors previous DeFi exploits like Yam Finance and SushiSwap, where rapid investment in unvetted projects led to significant losses.
Lessons Learnt from the Eminence Hack
Proceed with Caution:
The Eminence incident serves as a stark reminder for the DeFi community to be more cautious. Not every project, even if associated with a known figure, is immediately safe for investment.
DeFi’s Recurring Issues:
The Eminence situation is not the first of its kind in DeFi. Previous events, such as those with Yam Finance and SushiSwap, indicate a pattern of “rushing in” without proper due diligence.
Importance of Thorough Vetting:
Before investing in new projects, it’s crucial to await proper announcements, vetting, and even third-party audits to ensure contract safety.
Role of Auditors:
The involvement of reputable third-party blockchain and smart contract auditors like ImmuneBytes could provide an additional layer of security and trust.
Conclusion
The Eminence exploit marks a critical lesson in DeFi’s history, emphasizing the need for cautious investment practices, thorough vetting, and the potential risks associated with influential figures in the blockchain industry.
This incident underlines the evolving nature of DeFi and the importance of enhanced security measures, including the potential role of experienced auditors in preventing similar occurrences in the future.

