Overview
Table of Contents
On 1 February 2023, BONq DAO, an Ethereum-based decentralized lending platform, suffered a significant breach, resulting in an estimated loss of $120 million.
The exploit was executed through an oracle attack, manipulating the price of AllianceBlock’s $ALBT tokens via the Tellor Oracle. This methodology enabled the attackers to drastically inflate and then decrease the price of $ALBT tokens, leading to a substantial financial loss.
About BONq DAO
BONq DAO operates as a non-custodial, decentralized lending platform that allows users to secure loans against their digital assets.
By locking assets in user-controlled smart contracts or troves, users can mint BEUR, a stablecoin pegged to the Euro. The platform’s governance is overseen by BNQ token holders, including DAO directors and members.
BONq DAO distinguishes itself by utilizing the Tellor Oracle for price data, an immutable and decentralized protocol that facilitates open and verified data reporting.
Root Cause
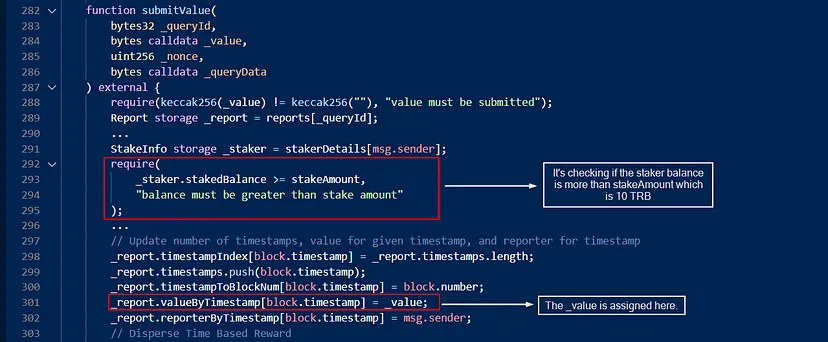
The core vulnerability that led to the BONq DAO hack was rooted in the protocol’s integration with the Tellor Oracle system. Specifically, the BONq Protocol was set up to immediately consume the latest data points reported to the TellorFlexOracle, which presents a significant risk.
Key Points of Vulnerability
Instant Price Feed Consumption: The BONq Protocol’s immediate consumption of the latest data points from TellorFlexOracle was a critical flaw. In decentralized finance (DeFi), real-time data can often be manipulated, making it dangerous to rely on such instant updates for critical financial decisions, especially in a lending platform where asset values directly affect lending and borrowing limits.
Tellor Oracle Mechanics: The Tellor Oracle allows anyone to stake 10 TRB tokens and update the price of a token. While this open participation is a strength of decentralized systems, it also poses a risk if not properly safeguarded. The lack of adequate checks or delayed verifications of these data points can lead to exploitation, as it happened in this hack.
Lack of Safeguards Against Price Manipulation: Ideally, oracles should have mechanisms to prevent drastic price manipulations, such as using time-weighted averages or requiring multiple confirmations of price updates. In the case of BONq DAO, these mechanisms were either absent or inadequately implemented.
Integration with WALBT / BEURtrove: The specific integration of the Tellor Oracle with the WALBT / BEURtrove in the BONq Protocol was flawed. The protocol was designed to adjust lending limits based on the current prices of the assets, which, when manipulated, allowed the hacker to borrow excessively against minimal collateral.
Technical Details
Contract addresses:
TellorFlex Contract: 0x8f55D884CAD66B79e1a131f6bCB0e66f4fD84d5B
BONq DAO Contract: 0x4248fd3e2c055a02117eb13de4276170003ca295
BonqProxy Contract: 0xb1b72B3579b03dFdCfF3195486277605e55Cf703
Detailed Technical Analysis of the Hack
Technical Details:
Attacker’s Address: 0xcAcf2D28B2A5309e099f0C6e8C60Ec3dDf656642
Attacker’s Contract: 0xed596991ac5f1aa1858da66c67f7cfa76e54b5f1
The attack on BONq DAO was executed through a series of calculated steps that exploited the protocol’s dependency on Oracle data for asset valuation.
The attack involved manipulating the price data of WALBT tokens provided by the Tellor Oracle and then leveraging this manipulation to extract significant assets from the protocol. Here’s a step-by-step breakdown:
Initial Oracle Manipulation:
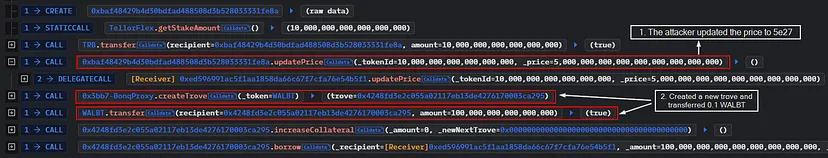
- Action: The attacker staked 10 TRB tokens on the TellorFlex oracle (a system within the Tellor Oracle protocol), which allows users to report data.
- Manipulation: They reported a drastically inflated price for WALBT tokens, setting it at $5,000,000 per token.
- Result: Since BONq DAO’s system was configured to immediately use the latest data from TellorFlex without sufficient validation or delay, this manipulation caused the protocol to register an unrealistically high value for WALBT.
Exploiting the Inflated Price:
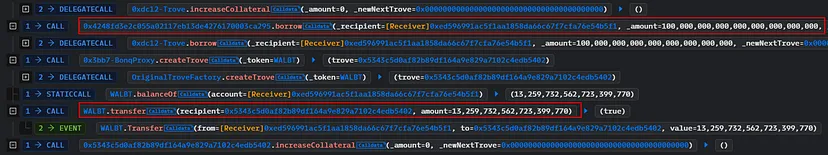
- Creation of a Trove: The attacker created a trove (collateralized debt position) in the BONq DAO system, depositing minimal WALBT tokens (0.1 WALBT).
- Borrowing Against Inflated Value: Leveraging the inflated valuation of WALBT, the attacker was able to borrow a massive amount of BEUR tokens, equivalent to $100 million.
- Conversion to Stablecoins: The borrowed BEUR tokens were then swiftly converted into USDC, a stablecoin, using the Uniswap platform.
Second Price Manipulation and Trove Liquidation:
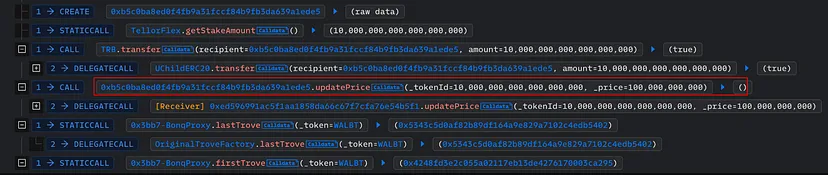
- Further Manipulation: From a different address, the attacker again staked 10 TRB tokens on TellorFlex, this time reporting an extremely low price for WALBT tokens ($0.0000001).
- Liquidation of Troves: The attacker then liquidated multiple WALBT tokens at this artificially low price.
- Result: This step allowed the attacker to acquire significant WALBT tokens at a fraction of their actual value.
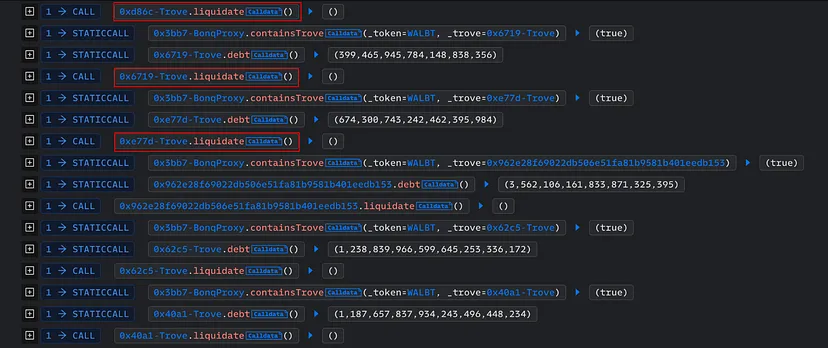
Completion of the Attack:
Final Outcome: By executing these steps, the attacker successfully extracted 113.8 million WALBT tokens and 98 million BEUR tokens from the protocol.
First Attack Transaction: 0x31957ecc43774d19f54d9968e95c69c882468b46860f921668f2c55fadd51b19
Second Attack Transaction: 0xa02d0c3d16d6ee0e0b6a42c3cc91997c2b40c87d777136dedebe8ee0f47f32b1
This attack demonstrates a sophisticated understanding of the interaction between decentralized finance protocols and oracle services.
The attacker capitalized on the immediate and unquestioned acceptance of Oracle data by the BONq DAO system, exploiting this vulnerability to manipulate the system for personal gain.
Stolen Fund Details
The stolen funds, consisting of $534,000 worth of converted BEUR tokens and 113.8 million WALBT tokens, were initially bridged to the Ethereum network. Subsequently, on February 3, 2023, the attacker dispersed these assets through Tornado Cash.
Hack Aftermath
Loss of Investor Trust
Following the hack news, there was a notable decline in investor confidence. This was most prominently reflected in the market response to the Bonq token ($BNQ), where investors, reacting to the uncertainty and risk posed by the security breach, began selling off their holdings.
This sell-off indicates a profound impact on investor sentiment, highlighting the vulnerability of decentralized finance (DeFi) platforms to such incidents.
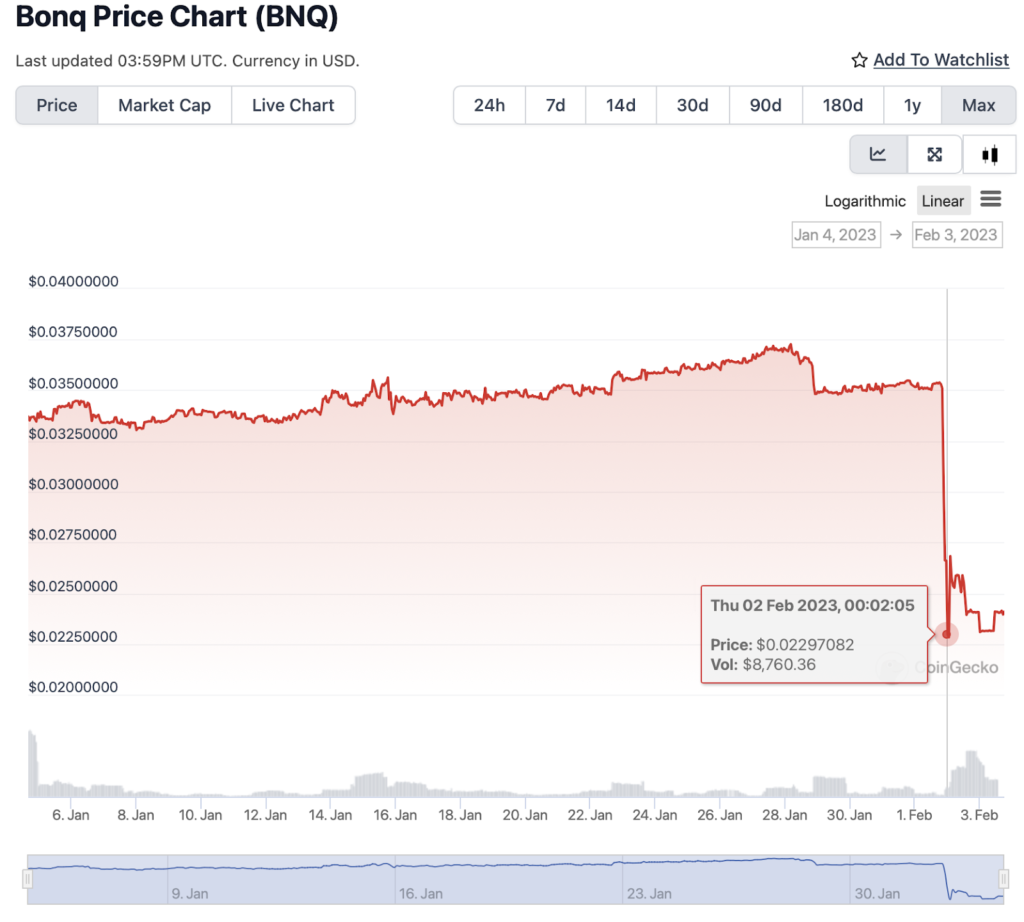
Impact on Bonq Euro ($BEUR)
The $BEUR, a stablecoin pegged to the Euro, experienced a catastrophic decline, plummeting to an all-time low of $0.15 on February 3.
This drastic decrease in value is a severe blow to any stablecoin, as maintaining a peg to a fiat currency is critical to its functionality and trustworthiness. For $BEUR, recovering from such a significant devaluation presents a daunting challenge, potentially undermining its viability as a stablecoin.
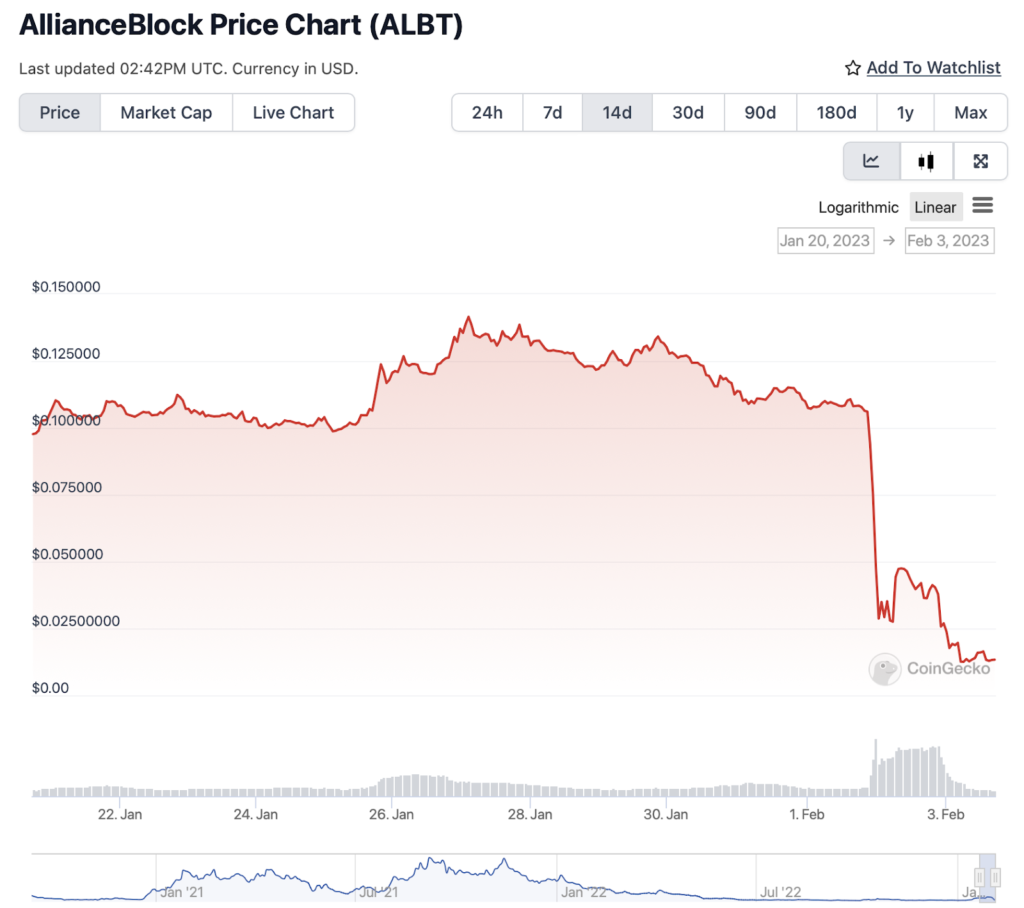
Secondary Effects on AllianceBlock Token ($ALBT)
The AllianceBlock Token ($ALBT) also suffered considerable indirect damage from the hack. The manipulation of $ALBT’s price during the attack not only facilitated the exploitation but also led to a loss of trust and value in the token itself.
This secondary impact underscores the interconnectedness of assets within the DeFi ecosystem and how the vulnerability of one component can have ripple effects on others.
Protocol’s Response
In response to the hack, the Bonq Protocol team immediately paused the protocol. This was necessary to prevent further exploitation and assess the damage.
The team also actively communicated with the community, providing updates and information about the incident via mirror. This transparency is crucial in managing the fallout from such incidents and starting to rebuild trust.
https://mirror.xyz/bonqdaoblog.eth/hF4wGAKBG0YvMEnGTUaa0scGcQDZ8cTxtBo-RpQXRJ0
Mitigation Steps
Implementation of Time Delays and Data Verification in Oracle Feeds:
- Problem: The immediate consumption of the latest data point from the Tellor Oracle was a critical vulnerability. In this hack, the attacker was able to manipulate the price of WALBT tokens by updating the Oracle with false data, which the BONq protocol then immediately used.
- Mitigation: Implementing a time delay between the data submission to Oracle and its consumption by the protocol can allow for sufficient time to verify the accuracy of the data. This delay would enable other participants or automated systems to challenge or confirm the data before it impacts the protocol’s functions.
Utilization of Multiple Oracles for Price Verification:
- Problem: Sole reliance on a single Oracle for price feeds creates a single point of failure, as seen in this incident where the price of WALBT was easily manipulated.
- Mitigation: Using multiple Oracles can provide a system of checks and balances. For instance, the protocol could require that the price of a token must be confirmed by at least two independent Oracles before being accepted. This redundancy makes it significantly harder for an attacker to manipulate the price, as they would need to compromise multiple Oracles simultaneously.
Enhanced Input Validation on Oracle Feed Parameters:
- Problem: The lack of robust input validation allowed the attacker to submit an extremely unrealistic price for the WALBT tokens.
- Mitigation: Implementing strict validation rules for data submitted to Oracles can prevent outliers or unrealistic data points from being accepted. For example, protocols could set thresholds for how much a price can change within a certain timeframe, or compare incoming data against historical trends and reject values that deviate too drastically. This would help in mitigating the risk of price manipulation through Oracles.
These steps are crucial in enhancing the security of decentralized protocols that rely on external data sources, such as Oracles, to make critical operational decisions. Implementing these measures could significantly reduce the risk of similar attacks in the future.
Conclusion
The BONq DAO hack serves as a potent reminder of the vulnerabilities inherent in blockchain protocols, particularly those related to Oracle data integration and real-time data dependency.
The incident underscores the necessity for more rigorous security measures, such as delayed Oracle feed consumption and multiple data source validations, to prevent similar exploits.
It also highlights the critical role of comprehensive security audits in identifying and mitigating such vulnerabilities. In this context, engaging with expert blockchain security firms like ImmuneBytes could be instrumental for DeFi projects in fortifying their defenses against sophisticated attacks, thereby ensuring a more secure and resilient blockchain ecosystem.

