Have you ever wondered how platforms like Trust Wallet and MetaMask can automatically retrieve your assets with 12 or 24 lists of random words? The answer is by implementing HD wallets.
Since the inception of Hierarchical Deterministic (HD) crypto wallets in 2012, things have changed quickly. Can you believe now a hexadecimal string of characters (a single master key) has the power to generate unlimited accounts (new public and private keys)?
The industry standard for these crypto wallets is simple. Any random number can be used as a ‘seed’ to generate an infinite number of private and public keys. The defined standards for them are BIPs: 32, 39, 43, and 44 for their implementations.
This blog will give you a better understanding of Hierarchical Deterministic wallets, their structure, their work, the pros and cons of using an HD wallet, and so on. ImmuneBytes is the perfect platform to get all the answers germinating in your mind.
Let’s begin.
What Are Hierarchical Deterministic Wallets?
Table of Contents
- A hierarchical deterministic wallet generates infinite public and private keys from a single master key.
- Hence, users can create new wallets and retrieve their assets and keys.
- In these wallets, users can easily back up the wallets using a single seed phrase.
- They also get a lot of benefits from extended keys.
- There are numerous applications for these wallets in diverse fields like online shopping, trustless auditing, departmental funding distribution, etc.
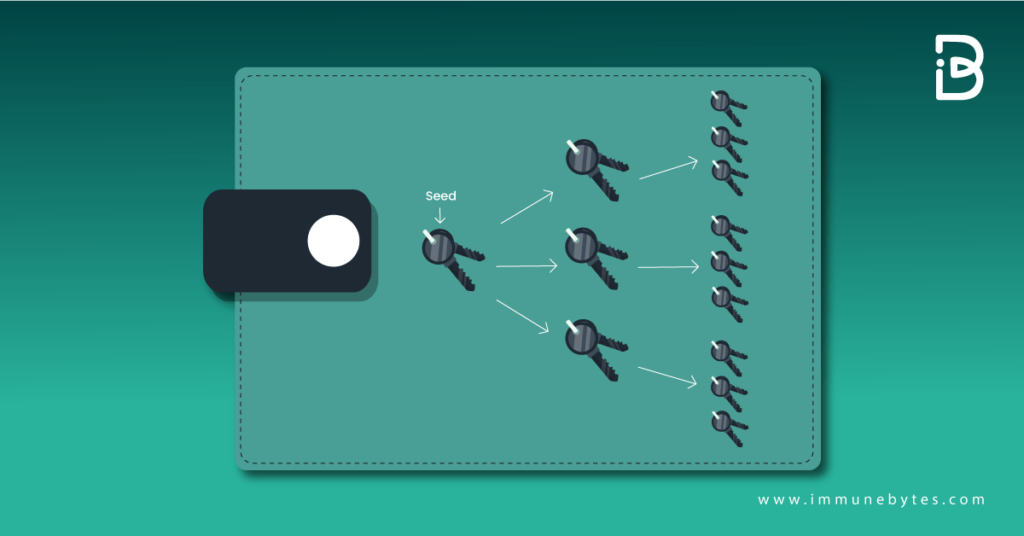
So, this is a hierarchical deterministic wallet explained. Now, let us proceed with its structure.
The Structure Of Hierarchical Deterministic Wallets
Let us now get a brief understanding of the structure of an HD wallet. As shown in the graphic below, the tree is deterministic.
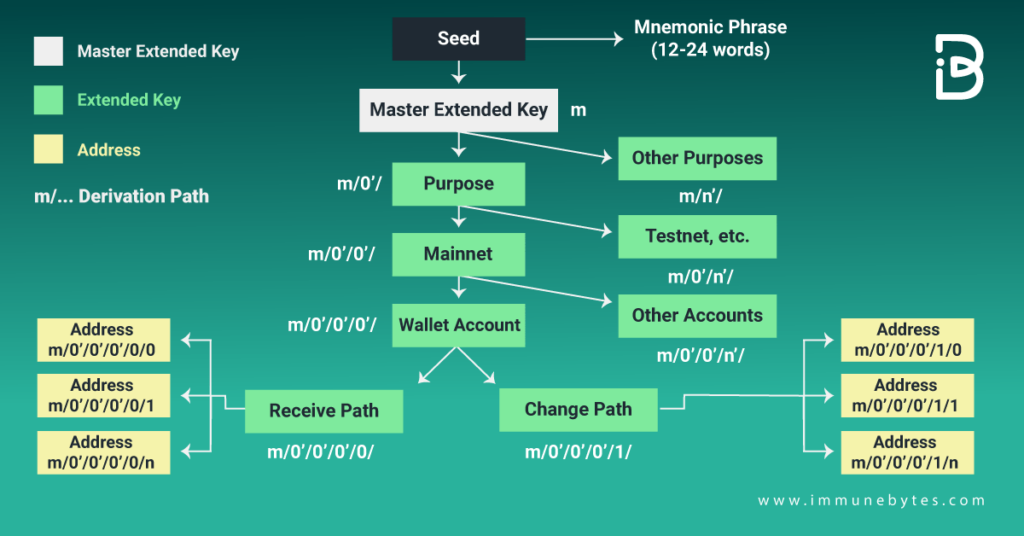
Fig 2: The structure of Hierarchical Deterministic Crypto Wallets
As you can see, there is a seed phrase or a master key, which will always generate the same tree of keys. Here, we have a master key. The derivation path will always generate the same key. Thus, users can simply back up this key instead of keeping a check on hundreds of keys.
A parent public key (extended public key) also helps generate new addresses without accessing any private keys. Hence, users can store their private keys in cold storage while using the public keys for receiving Bitcoin.
How Does Hierarchical Deterministic (HD) Crypto Wallet Work?
The main aim of using HD wallets is to enhance security and privacy. It creates a fresh pair of keys from the master key for every crypto transaction.
With the BIP-32 standard, these wallets become the de facto standard for Bitcoin. BIP-32 is the Bitcoin Improvement Proposal (BIP) that paved the way for a wallet structure similar to a hierarchical tree.
Let us understand how MetaMask, which is an HD wallet works.
- There is a wallet seed from which a master key derives.
- Now, this master key generates child keys.
- Each of the child keys then becomes capable of generating its children.
- Seed is often represented as a mnemonic phrase. It is the information used to produce both public and private wallet keys.
- The master key has an extended pair of the private key (XPRIV) and public key (XPUB) in a typical HD wallet for Bitcoin. Then, pseudorandomly, the master private key creates a private child key. In addition, anyone with access to the master public key can create the matching child public keys.
- XPRIV generates all the child private keys, while XPUB displaces the child public keys in the HD wallet. In this situation, the need for storing multiple pairs of keys gets eliminated, as the address in these wallets can easily be generated from the master key or seed.
The Pros And Cons Of Using An HD Wallet
Advantages
- The privacy of the users who use these wallets improves as they just need to share the master public key; they don’t need to worry about jeopardizing their funds.
- These wallets are more secure as funds are diversified over numerous addresses.
- As HD wallets stick to the hierarchical structure, every key generated through the seed can be utilized as a master private key. This key can, in turn, generate new keys further.
- When there are multiple changing addresses, it becomes difficult to find out the exact balance of the wallet from the public ledger, which translates to enhanced privacy.
Disadvantages
With so many benefits of using these HD wallets, there are some cons too. These include:
- In case users reveal the master key or private keys to the public, there is a high chance of losing access to their funds.
- Anyone with access to the extended private keys can easily steal the user’s funds. Thus, no one should share it with those they don’t trust.
- Hackers can steal all the funds in the wallet if the seed is compromised.
Are Hierarchical Deterministic Crypto Wallets Safe to Use?
Recently, 1inch Network launched a hardware wallet for storing users’ private keys in a secure offline setting. The 1inch team says that the architecture of this hardware wallet supports a hierarchical deterministic (HD) wallet algorithm. Each wallet uses the Hierarchical Deterministic (HD) wallet algorithm in accordance with BIP44 to create a new wallet set.
These wallets are as secure as the medium on which they are stored.
BIP-32 enables an HD wallet to create a hierarchical structure like a tree. This structure encompasses private keys that are generated from a seed. If you lose the device or it gets destroyed, the seed backup can help you restore the wallet and the private keys. Since they issue new addresses with every new transaction, it becomes a challenging and intricate process to hack them.
Wrapping Up
A Hierarchical Deterministic (HD) wallet has paved the way for a lot of security for the users within the crypto world. They have helped secure digital assets and contributed immensely to enhancing users’ privacy manifold times. With so many advantages, some disadvantages make users reluctant to use them. However, those disadvantages can easily be mitigated.
ImmuneBytes is a pioneering smart contract auditing company that specializes in blockchain security audits, and pentesting, Web3 security consulting, digital assets security.

