If you’ve been a keen observer of cryptocurrencies or Blockchain in any way, then you might have come across terms like layer one and layer two protocols. And, with all the curiosity bubbling up in your mind, you are here to know what these layers are all about. You have just landed in the perfect place, then. We will discuss more blockchain layer architecture here in this blog.
It is not a secret that blockchain technology is an amalgamation of several existing technologies- game theory and cryptography’that have many possible applications, such as cryptocurrencies. Blockchain technology eliminates the scope of intermediaries, slashes costs, and enhances efficiency by offering robust security and transparency.
The underlying technology does not need a central authority, and distributed ledger technology (DLT) verifies the information using cryptography. This builds trust between people and makes it possible for blockchain networks to carry out transactions between users securely.
As there is no central authority, blockchain technology is considered secure. It can also hold increasing users because of its scalable property. This is the reason more, and more layers were born out to accommodate more users. Let’s see what these layers are in this blog. ImmuneBytes is a one-stop destination for all your queries.
What Do We Mean By Blockchain Scalability?
Table of Contents
?Scaling? in Blockchain technology means an increase in the throughput rate. It is measured in transactions per second. With the skyrocketing of people adopting cryptocurrencies in their day-to-day lives, it is required to improve network security, recordkeeping, and other functions. This is what is the job of Blockchain layers.
For instance, while VisaNet’s electronic payment network can process more than 20,000 transactions/second, for BTC, the throughput is seven transactions/second.
Within the decentralized ecosystem, blockchain is the first layer. Then comes a third-party integration of layer one and layer two to enhance nodes and throughput. Nowadays, people are working on a wide range of layer-two blockchain technologies to implement them. To automate the transactions in them, they are using smart contracts.
Blockchain developers aspire to reduce the processing times and increase TPS through layers of blockchain and by optimizing the scalability of layer two.
What Is The Blockchain Trilemma?
There’s a commonly held notion regarding blockchain decentralization, scalability, and security. It says that in terms of decentralization, security, and scalability, a decentralized network can only offer any two of the three benefits at a given time. The widely accepted belief is that security, decentralization, or scalability must be compromised in public blockchain infrastructure.
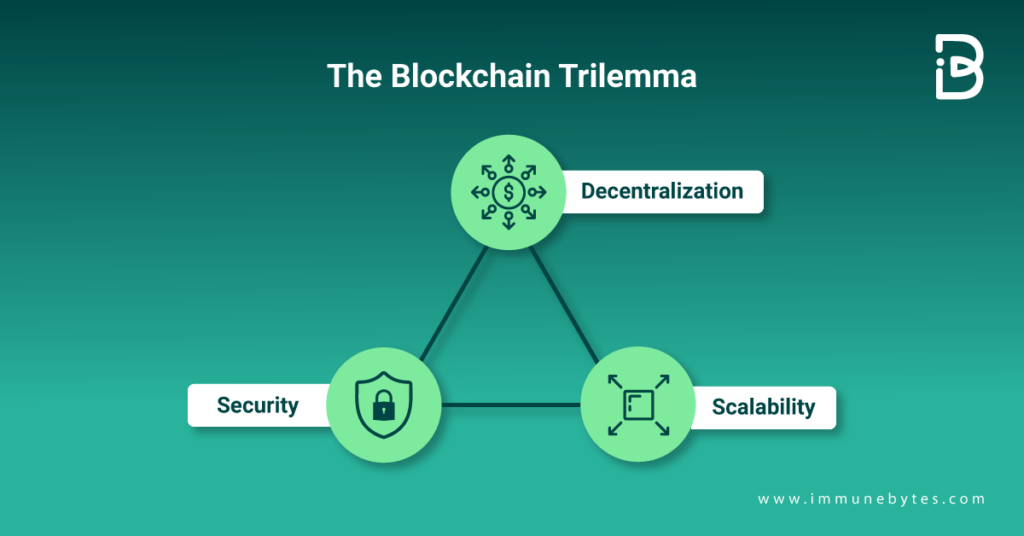
Before understanding the dynamics of the blockchain trilemma, let us give you a quick overview of scalability, security, and decentralization in general terms:
- The scalability of a blockchain means how efficiently it can handle a high volume of transactions.
- Security means the ability to secure blockchain data from malicious hacking exploits and how it can defend itself against double-spending.
- Decentralization is a network redundancy that ensures fewer entities do not control the network.
Now, let us dwell deeper and understand the interplay among these three components.
First, let us take a look at
Scalability and Decentralization?
The network must first agree on its validity if it wishes to settle a transaction. If many members wait to make the transaction, the agreement will take some time. Hence, scalability has to be inversely proportional to decentralization if the security parameters are the same.
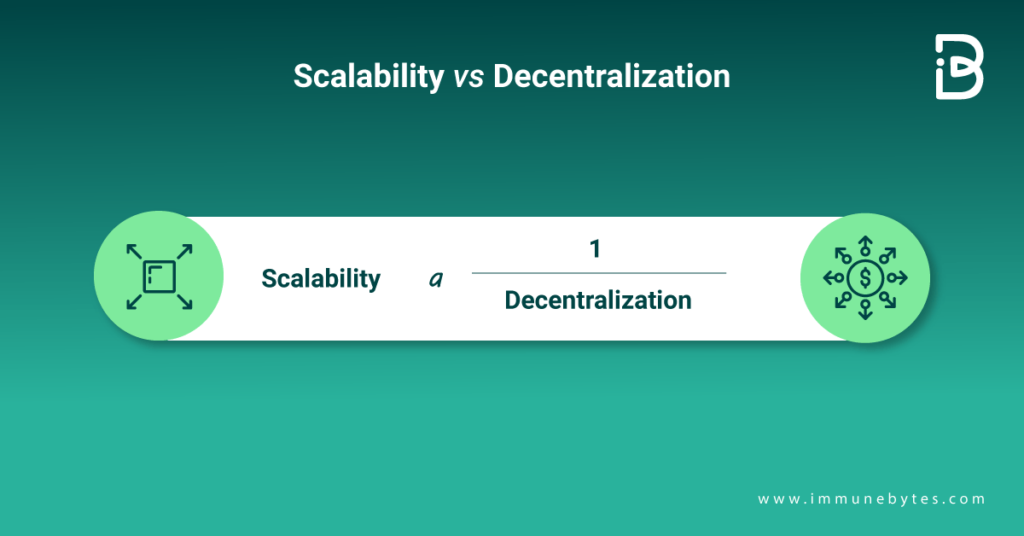
Consider two blockchains with proof-of-work that have the same degree of decentralization and think that security is the blockchain’s hash rate. As the hash rate rises, confirmation time decreases, and as security improves, scalability also increases. Hence, scalability and security go hand in hand when decentralization remains constant.
Ethereum is one of the examples of the trilemma. With the increased demand, transaction fees have also increased. It is also an example of the trilemma because it is only possible for Ethereum to scale without sacrificing decentralization or security. It is, thus, observed that Blockchain cannot optimize all three together.
Thus, startups and corporations are working on layer one and two solutions to solve this problem of blockchain trilemma. Now, we can demystify all the layers of blockchain architecture.
Blockchain Architecture: The Layered Structure
We can categorize the layered structure of blockchain into five layers of blockchain.
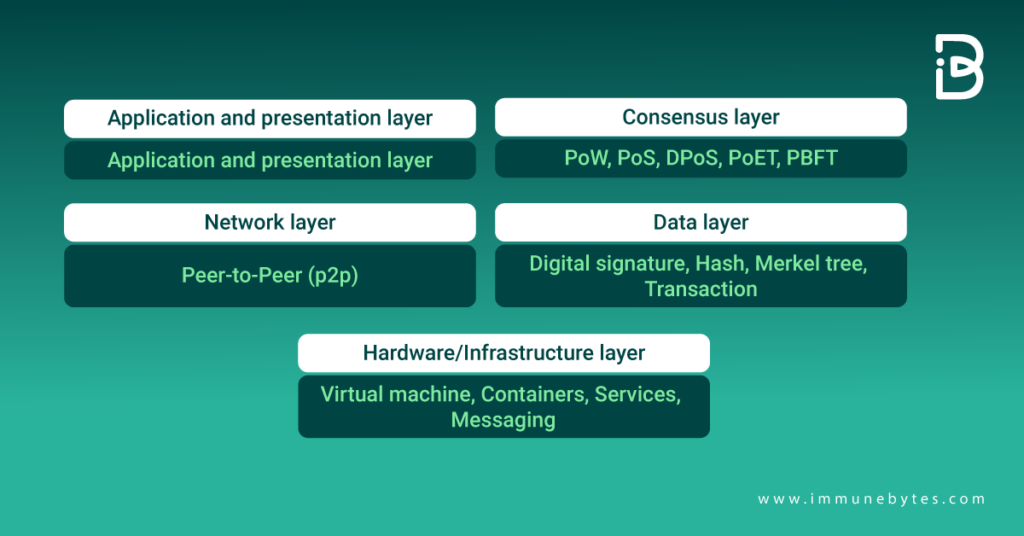
Let us understand them one by one.
Hardware Infrastructure Layer
First, the blockchain content s stored on a server within any data center. Clients browse the web or utilize any application. From here, they request content from the data center. This is known as client-server architecture.
Once they get that data, they can easily connect to peer clients and share it. Now, a peer-to-peer (P2P) network has been created. This distributed database (blockchain) stores data, transactions, and all other data.
Data Layer
We can express the data structure of a blockchain as a linked list of blocks, wherein we will find an ordered pattern of transactions. This structure has two fundamental elements? a linked list of chained blocks and pointers to the previous block.
The Merkel tree is a binary tree of hashes. Each block consists of the root hash of the Merkel tree and several other information, such as the block hash of the preceding block, current difficulty goal, timestamp, block version number, and nonce. It provides irrefutability, security, and integrity. The blockchain system is designed on Merkle trees, consensus algorithms, and cryptography.
It must be noted that the genesis block (the first block in a blockchain) does not have a pointer.?
Transactions are digitally signed to safeguard the security and integrity of the data that is stored in the blockchain. A private key is used to sign transactions, while anyone with a public key can verify the signer. The purpose of the digital signature is to detect information manipulation. Digital signatures guarantee unity by encrypting and signing the encrypted data. Therefore, any tampering will invalidate the signature.
Since the data is encrypted, it cannot be found. Even if it is discovered, it cannot be tampered with again. The identity of the sender or owner is likewise shielded by a digital signature. A signature is, therefore, irrevocably connected to its owner and cannot be ignored.
The Network Layer
Also known as P2P and propagation layer, the network layer ensures that nodes can find each other, interact, disseminate, and synchronize. This ensures that the blockchain network works smoothly in a legitimate state. The nodes carry out the transactions of the blockchain.
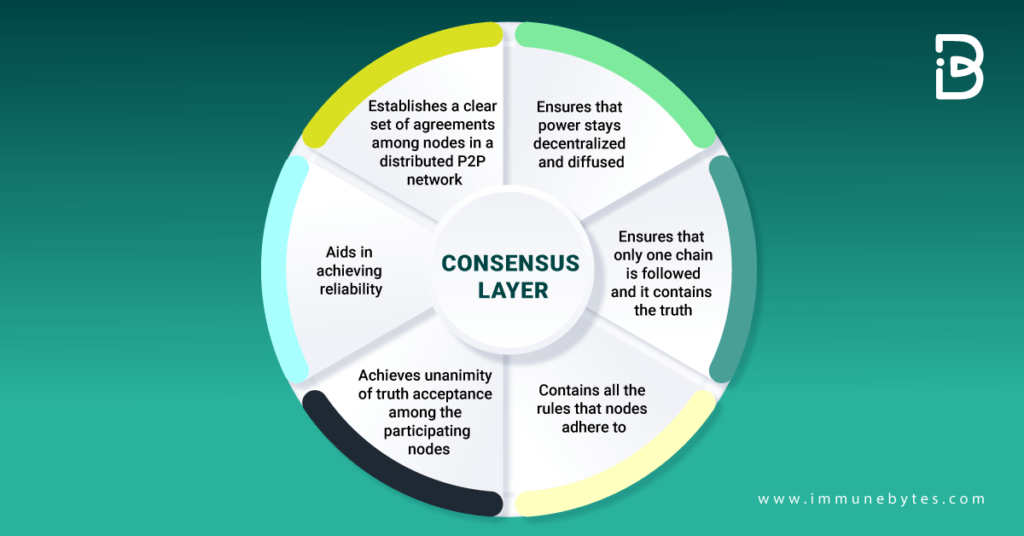
Consensus Layer
It is one of the most essential layers for the blockchain platform to exist. Irrespective of whether the blockchain is Ethereum, Hyperledger, or any other, the consensus layer has to be the most critical layer in the blockchain? it is responsible for validating the blocks and ordering them while ensuring that everyone agrees.
These are some of the most essential features of the consensus layer:
The Application Layer.
This layer includes smart contracts, chaincode, and DApps. Further, there are layers of application blockchain? application and execution layers. Also, there are programs that users use to interact with the blockchain network. APIs, scripts, UI, and frameworks are the parts of this layer.
A transaction is approved and carried out at the semantic layer even though it passes from the application layer to the execution layer. Applications direct the execution layer, which carries out commands and maintains the determinism of the blockchain.
Blockchain Layers Explained
Layer 0
This layer contains all the components that aid in making blockchain a reality and making it function smoothly. It includes components like the internet, hardware, and all those connections that make layer one run smoothly.
There is a long list of layer 0 blockchains today in the world. Some of the most popular Layer 0 blockchain examples include Horizen, Cosmos, and Polkadot.
Layer 1
Also known as the Foundation layer or implementation layer, layer 1’s security is based on its immutability. It is responsible for looking after all the consensus processes, dispute resolution, programming languages, and rules to make the functionality of the blockchain smoother.
Bitcoin is a layer one blockchain example.
However, initially, there were some problems with layer one, such as:
- Layer one needed to catch up with an increase in the number of blockchain users. The clumsy proof-of-work consensus was being followed in L1.
- As a result, the speed was limited.
- More computational power, more time, less processing speed and capacities
As a possible solution for these problems, proof-of-stake has now been adopted. With the Ethereum merge 2.0, sharding has been suggested as a scaling solution and is now being used.
Additional Read: Top 5 Programming Languages for Smart Contracts
Layer 2
Some overlapping networks sit on top of layer one and are known as layer two solutions. Protocols use this layer to enhance scalability by eliminating certain interactions from the base layer, resulting in smart contracts handling just the deposits and withdrawals.
Examples of L2 blockchains include Bitcoin’s Lightning Network.
What distinguishes layer one from layer two blockchains, then? The foundation of a decentralized ecosystem is the blockchain. When layer one and layer two are combined, the number of nodes and, consequently, the system throughput increase. Currently, many layer-two blockchain technologies are in use.
These are some of the L2 scaling solutions.
- Nested blockchain: Layer two blockchains are nested on the other. In essence, layer one creates the conditions, whereas layer two performs the actions. There could be numerous blockchain levels on a single mainchain. Example- OMG Plasma Project
- State channels: By enabling two-way communication between a blockchain and off-chain transactional channels via various methods, a state channel increases overall transaction volume and speed.
Example- Bitcoin Lightning and Ethereum’s Raiden Network
- Sidechains: A sidechain is a separate transactional chain that works in tandem with the blockchain and is used for large transactions. A utility token is typically used as part of the data transfer mechanism between side and main chains, and side chains have their own consensus algorithm that can be modified for speed and scalability.
- Rollups: By doing transactions outside of the layer one network and uploading the resulting data to the layer two blockchains, rollups are layer two blockchain scaling options. Rollups help increase transaction throughput and open participation and reduce gas prices, which are advantageous to users.
Layer 3
Layer three, or L3, is frequently used to refer to the application layer. The L3 projects provide a user interface while hiding the communication channel’s technical details. Blockchains’ real-world usability is a result of L3 applications.
Final Thoughts:
Scalability has always been one of the pain areas for blockchain users. While there has been some improvement in expanding the blockchain protocols, the demand for cryptocurrencies is huge. Accordingly, there has to be more expansion to meet the demands of the users. Both levels of blockchain have their own set of loopholes; therefore, the best solution would be to think of a solution that is effective enough to solve the scalability trilemma.
L1 is crucial because it is the foundation for decentralized systems and has a lot of scalability issues. Unfortunately, a wide range of DApps run on this layer. The scalability issues are addressed via L2 protocols.
L3 applications are significant because they aid in designing the use cases for blockchains in the real world.
Still confused? Come to the experts at ImmuneBytes for guidance. We will clear all your doubts within no time.

