From trading at stock exchanges to trading in crypto or NFTs, unethical practices have been a part of both but in their own ways. However, one such practice that made its evolution from stock markets to blockchain transactions is front running, where untrustworthy players are still managing to con unwary dealers.
These unscrupulous traders exploit the Automated Market Maker(AMM) to profit at the expense of other ethical users.
This article will talk about the front-running attack sieving through crypto and its working and mitigation measures.

What is Front Run in Crypto?
Table of Contents
Front running, coined from the traditional stock market, has also invaded the crypto space. From a traditional perspective, it is illegal to use insider or non-public disclosed information, taking benefit out of the forthcoming price transitions.
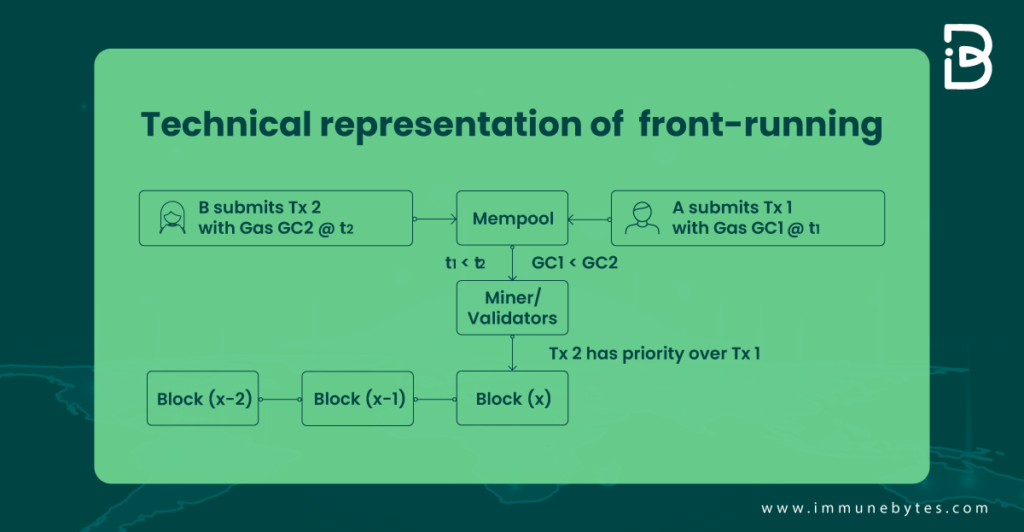
Front running refers to adding a transaction to a queue, knowing that another transaction will follow. On a blockchain platform, front running typically takes the form of a miner placing an order that would profit him based on trade still in progress.
How Does Front Running Work?
Front running, also called Race condition, is an unethical but not illegal practice in the crypto space, unlike in the traditional marketplace. As in brick-and-mortar markets, insider information is not publicly disclosed, but at DEX, manipulation is done based on the publicly disclosed information.
Let us Understand How Front Running Works in Crypto.
In a crypto-market, observers on the network can view and respond to a transaction before it is included in a block since all transactions are briefly visible in the mempool before being processed.
With a decentralized exchange, where a buy-order transaction may be observed, a second-order transaction can be broadcast and executed when the first one is still in transition. It is challenging to defend against this because it would depend on the particular contract.
Here, the attacker can take aid through a front-running bot. They skim over the mempool of the transactions waiting for the miner’s validation. Then, in order to raise the bidding prices, they submit bids on the underlying assets with excessive gas fees.
Let Us Understand this With an Example:
Here we are taking a solidity example to understand the actual working of the frontrunning attack.
In most blockchains, the transactions are pooled together and then put on a block, validated by the miner. The miner decides the order of the transactions, typically based on the gas price.
An attacker can change the state of a contract in a way harmful to the solver, modifying or revoking the solver’s rights. This can be done by keeping an eye out for transactions in the transaction pool that might include a solution to the problem.
Once the attacker has the data from this transaction, they can generate a new transaction with a greater gas price than the original so that it appears in the block before.
Look at the code given below:
Note: This example has been taken from the Ethereum book.
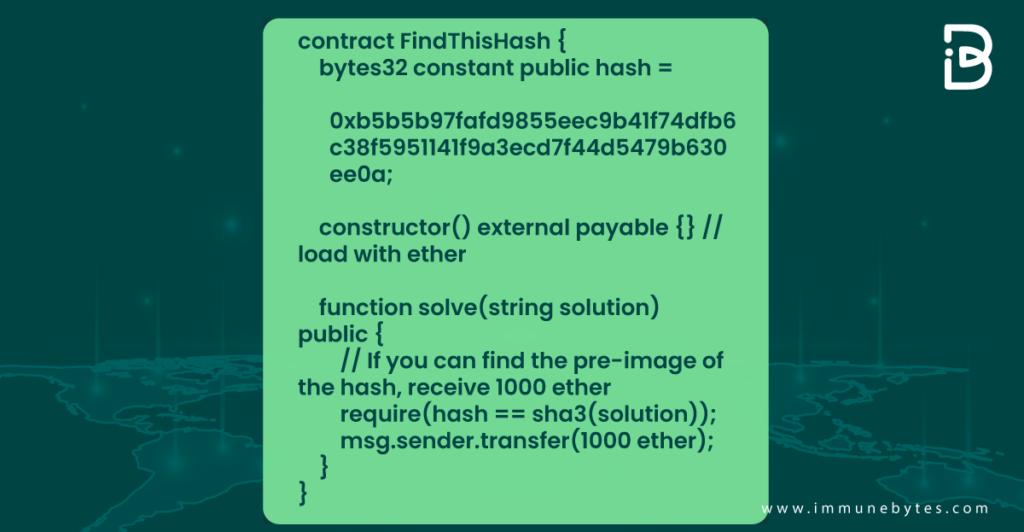
Here the problem includes a price of 1000 Ether for the solver. Suppose there is a solver A who figures out the solution. Here, an attacker is watching the transaction pool for someone to figure out the SHA3, verify its validity, and introduce an equivalent transaction with a higher gas price. This increases the probability of the attacker featuring higher in transaction order, leaving the solver without any incentive.
Now that we know what frontrunning is and how it works in the crypto world, let us look at the categories of frontrunning attacks.
Categories of the Front-Running Attack
Following are the three categories of the front-running attack.
Displacement
A displacement attack is one that is explained through the example given above. In this, the attacker displaces the innocent user by keeping a higher gas fee to appear in the higher transaction order.
Insertion
Here, the attacker needs the user’s transaction to take place after the attacker’s transaction. For instance, a user named X bid a higher gas price for his transaction to be prioritized. Now the attacker will first transact at a gas cost less than X’s bid and, soon after that, transact to profit from the difference between the two.
Suppression
Also known as a “block stuffing attack,” this occurs when the attacker uses a high gas cost and gas amount to delay the user’s transaction by using all the gas and filling up the block’s gas limit.
How to Mitigate Front Running Attacks?
There can be two malicious entities that can perform a front-running attack: an attacker, and the miner itself.
An attacker, actually a user, can modify the gas price of the transaction to appear prior in order. In contrast, a miner can mutate the transacting order irrespective of the gas fee quoted by the users.
An upper limit on the gas fee can prevent the attacker from conducting a front-running attack. However, another way is using a commit-reveal scheme. In this, a user sends a transaction with confidential information(the commit phase), which is out only after the transaction has been completed(the reveal phase).
Although even using this method, transaction value cannot be concealed.
Mapping Up
According to Cybernews, frontrunning has cost unaware traders $280 million each month globally.
In addition to the apparent financial loss, frontrunning can damage the confidence of many current and potential investors.
In a bid to prevent such attacks, a new entrant in the blockchain space, telos, decides to use hierarchy to execute transactions. It implies that transactions are executed on a first-come-first-serve basis. Now, with the Ethereum virtual machine in evolution, let’s see what positive changes it could bring to prevent crypto?users from such malicious attacks.
Additional Resource
What is a Smart Contract Security Audit?

