Did you know? Over $2B of crypto was lost in the year 2020 to security breaches and thefts. Adding another name to the list, we have ForceDAO.
4th April 2021, saw ForceDAO, a newly launched DeFi aggregator, suffer an attack, draining the project of 183 ETH, amounting to approximately $367K. The project had launched its airdrop only hours before the hack, on 3rd April.
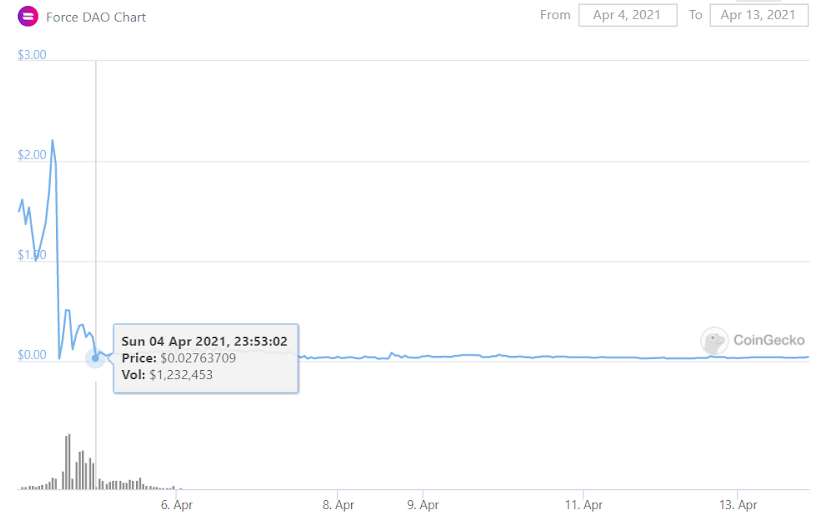
Source: https://www.coingecko.com/en/coins/force-dao
The price of FORCE came down to $0.07 from a rise of $2.
According to the post-mortem of the incident, five hackers were responsible for the attack. One of the attackers, however, turned out to be a ‘white-hat’ hacker, who assisted the team by warning them of the exploit before any further damages were done to the platform.
Technical Analysis of the Incident
Table of Contents
A little backstory before diving deeper into the incident, like any traditional computer program, smart contracts can experience errors. A common issue that Solidity developers face is properly handling these errors.
The two options to handle errors in the ERC20 contracts are:
- Revert: A reversion in Solidity is equivalent to throwing an exception. This means that the execution state of a transaction is rolled up as if it never happened.
- Return False: The called function returns a value of false, allowing the calling function to perform error handling.
During the finalization of the ERC20 standard, the community had not yet come to a common ground on which error handling method to choose, implying that both options are considered ‘valid’. This burdens the developer to make sure that their code is properly handling all errors.
Getting back to what happened with ForceDAO. The ForceDAO hack happened due to a mismatch in two components within the ForceDAO ecosystem:
- The exploited xFORCE vault is a fork of the xSUSHI contract, which assumes that the failed transfer will result in a reversion.
- And, the token used in ForceDAO is an Aragon Minime token that returns false if a call to the transfer from() function fails.
This mismatch creates a vulnerability in error cases. If somehow, a deposit into the xFORCE vault fails, the deposited tokens will remain in the sender’s wallet.
That is how the attackers were able to deposit FORCE tokens that would fail the transferFrom call and receive xFORCE tokens, as the xFORCE contract expects a revert from the token but instead receives false.
The ForceDAO attackers exploited this vulnerability and received xFORCE tokens. These xFORCE tokens were then exchanged for any FORCE tokens deposited in the vault by other users and liquidated for ETH on exchanges.
The Aftermath:
The ForceDAO team wrote, We’re currently engaged with 2 separate security firms to review and analyze our repos to ensure all contract systems perform as designed. Over the coming days, our team will announce a plan to re-launch xFORCE? with a snapshot and new token.?
The team also issued an advisory that cautioned users to avoid trading on any exchanges until the issue was solved.
Could this have been avoided?
As acknowledged by the team, the incident that took place was preventable: This could’ve been prevented by using a standard Open Zeppelin ERC-20 or adding a safeTransferFrom wrapper in the xSUSHI contract,? the team said.
The ForceDAO ecosystem was built using code from multiple sources, consequently, a solution containing vulnerabilities was deployed.
These vulnerabilities could have been easily detected and fixed through an in-depth smart contract audit. The audit would have identified the mismatch or detected the flaws in the error handling code.
Highlights:
- ForceDAO hacked, hours after being launched
- 183 ETH equivalent to $367k were stolen
- The price of ForceDAO’s native token FORCE plunged more than 80%
- One of the attackers (the white-hat hacker) has returned his share of stolen funds
About ImmuneBytes:
We are a team of India-based security professionals who are skilled and hold experience in their niche. With us, you’ll never have to compromise. We strive to push forward and provide overall surveillance and quality service to our customers. Get in touch with us to get a security audit for your smart contract.

