The UK-based Crypto Exchange, EXMO, went down on Monday, 15th Feb 2021 after being hit by a Distributed Denial of Service attack. This outage was preceded by another incident, on December 21, 2020, in which the hackers earned 5% of EXMO’s assets from its ‘hot’ wallets.
The question now arises, What are DDoS attacks?
A DDoS attack is one of the many powerful weapons on the internet. When we hear about a website being “brought down by hackers,” it usually means it has become a victim of a DDoS attack. Precisely, meaning that hackers have attempted to make a website unavailable by flooding or crashing it with too much traffic.
Additional Read: DDoS vs DoS Attacks
DDoS Attacks: Introduction
A DDoS attack, as we explained above, is used to create service malfunctioning, even a complete shutdown. For a cryptocurrency system, such attacks generally target transaction processes, instantly increasing the number of transactions processed and thus inhibiting the generation of new ones.
Within a blockchain, a DDoS attack can overload a blockchain with incoming bits of data which forces a blockchain to sever and further utilize its processing power. By doing this, a blockchain server can lose connectivity to any crypto exchanges, online crypto wallets, or any other connected applications. For example, 2017 saw an alleged DDOS attack targeting Bitfinex, a Bitcoin cryptocurrency system, resulting in a performance slowdown.
As far as statistics are concerned, in Q4 2020 there were only 10% more attacks than in Q4 2019. And compared to Q3 2020, the number of attacks in Q4 2020 fell by 31%, while Q3 2020 also saw a drop compared to Q2. This drop may be the result of the growing interest in cryptocurrency mining.
The graph below shows the dynamics of the number of DDoS attacks, in Q3 2020.
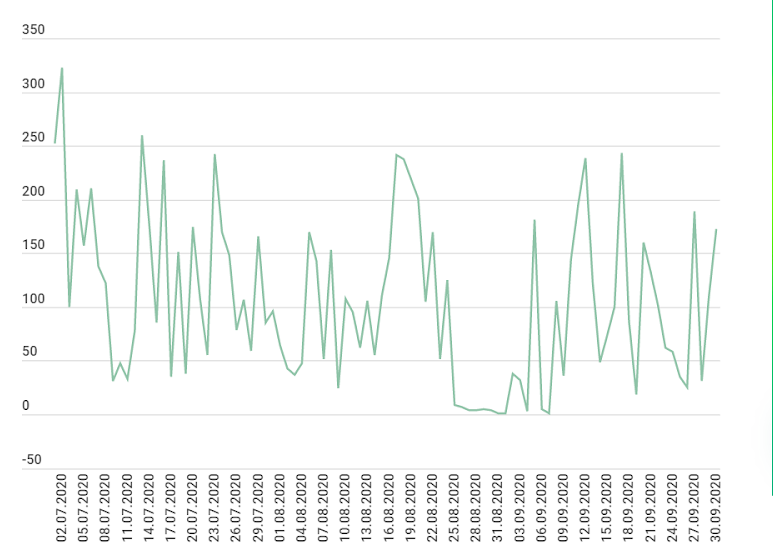
In addition to the immediate damage, these attacks, also leave consequences in the form of increased data storage and processing volume. A DDoS attack is also a rather costly attack to carry out, as transaction fees depend on the amount of currency transferred and on the volume of generated data. Despite this, the profit of potential system slowdown or shutdown is notably higher than expenses on fake transactions.
How Does a DDoS attack work?
Table of Contents
The basic idea behind a DDoS is slowing down a server, service, website, or network by flooding it with Internet traffic. Once the traffic overwhelms the target, its server, service, website, or network is rendered inoperable.
Different types of DDoS attacks focus on the different layers of the Open Systems Interconnection (OS) model. A few examples:
Layer 3, the Network layer. Known attacks— Smurf Attacks, ICMP Floods, and IP/ICMP Fragmentation. Layer 4, the Transport layer. Attacks include SYN Floods, UDP Floods, and TCP Connection Exhaustion.Layer 7, the Application layer. Mostly, HTTP-encrypted attacks.
What Happened with EXMO?

EXMO tweeted that it experienced an unusual amount of traffic at 16.10 GMT, with the number of connections disrupting its activity temporarily for two hours. They suspended all withdrawals following the incident and added that all user losses following this incident will be covered and refunded completely by EXMO.
“Our team is currently developing a new infrastructure for hot wallets. Since each blockchain needs a separate server, the process will take some time,” EXMO added in a later update.
How to Prevent a DDoS Attack on a Blockchain?
DDoS attacks are often made possible by attacking a single point of connectivity to the Internet. However, as blockchains are already decentralized, they can be prevented only through further decentralization of a network. This would not only reduce the capacity of the attack but also offer bandwidth to other specific servers facing attacks without compromising the whole chain.
Another way to prevent DDoS attacks on a blockchain would be to tweak some modifications in your miner software and reduce the gas limit targets.
Final Thoughts
In this article, we have explained the DDoS attack, how it works and how you can prevent it. With the rising popularity of cryptocurrency exchange platforms, hackers are becoming more and more creative with every attack. It is always advisable to get your smart contract a third-party audit so that your application is immune to such attacks.
About ImmuneBytes
We are a team of India-based blockchain security professionals who are skilled in their niche. We strive to push forward and provide overall surveillance and quality service to our customers. We ensure the security of your project and allow business owners to run their blockchain applications hassle-free. We’ve been hired by over 175+ blockchain startups and corporations to make their audit of smart contracts at an affordable cost.

