2022 has undoubtedly been one of the most significant years in the history of Decentralized Finance in many ways. One of them is the rise of crypto hacks! As the stats suggest, ?The amount stolen by hackers from DeFi exploits sums up to more than $120 million in the year 2020. DeFi accounted for 50% of all hacks and thefts in the year’s second half.?
It is needless to say that decentralized finance has the attention of malicious actors in the community. The more it attracts investors, the more it compels hackers to get creative!
According to a report by the crypto research company Messari, DeFi protocols have lost about $284.9 million to hacks and other exploit attacks since 2019. This figure is estimated to be about 0.65% of the adjusted TVL of the Ethereum-based DeFi market, reports DappRadar.
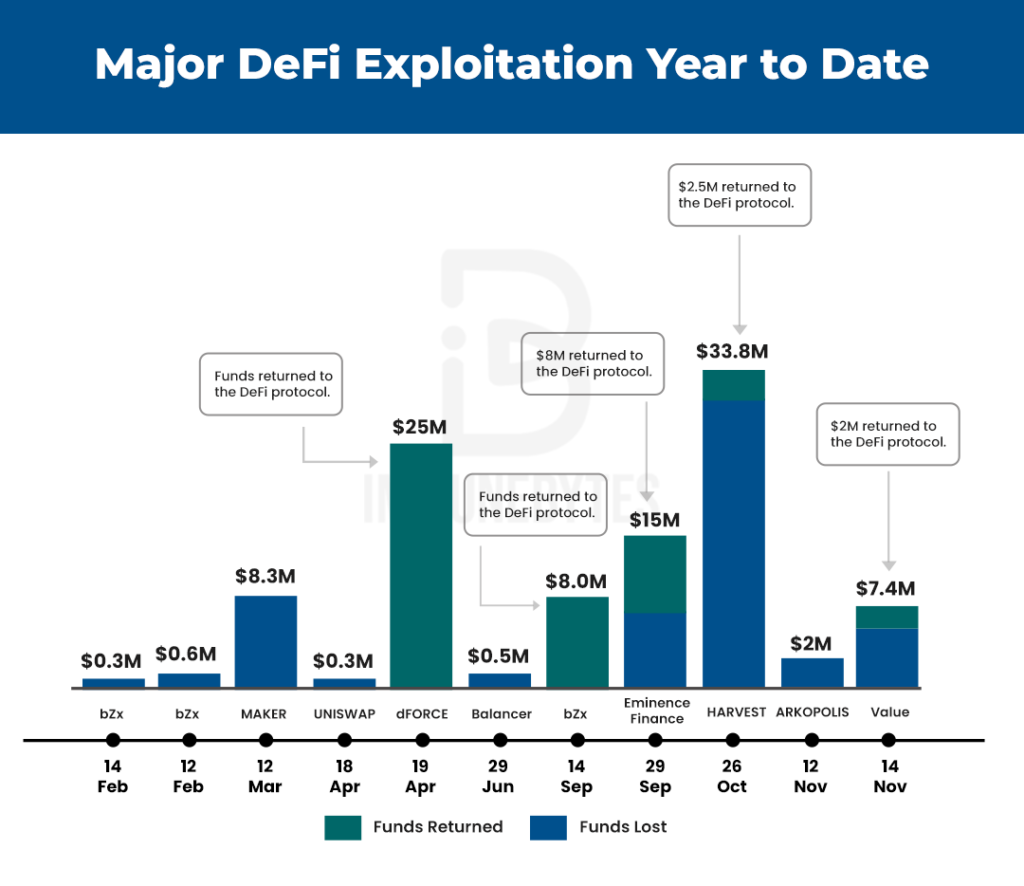
2022 became the year to encounter some of the major hacks in the history of Crypto! Hacks like bZx, Harvest Finance, Value Defi, and many more shook the community to its core. We have a whole list of hacks that happened in 2020. Go, check it out!
As analysts say, the attacks were anticipated, however, the pattern of the hacks that were observed startled the community. While the community was somewhat familiar with the hacks like re-entrancy, 51% attacks, and DDoS, it didn’t apprehend attacks like Oracle Price Manipulation or Flash Loans which are comparatively newer.
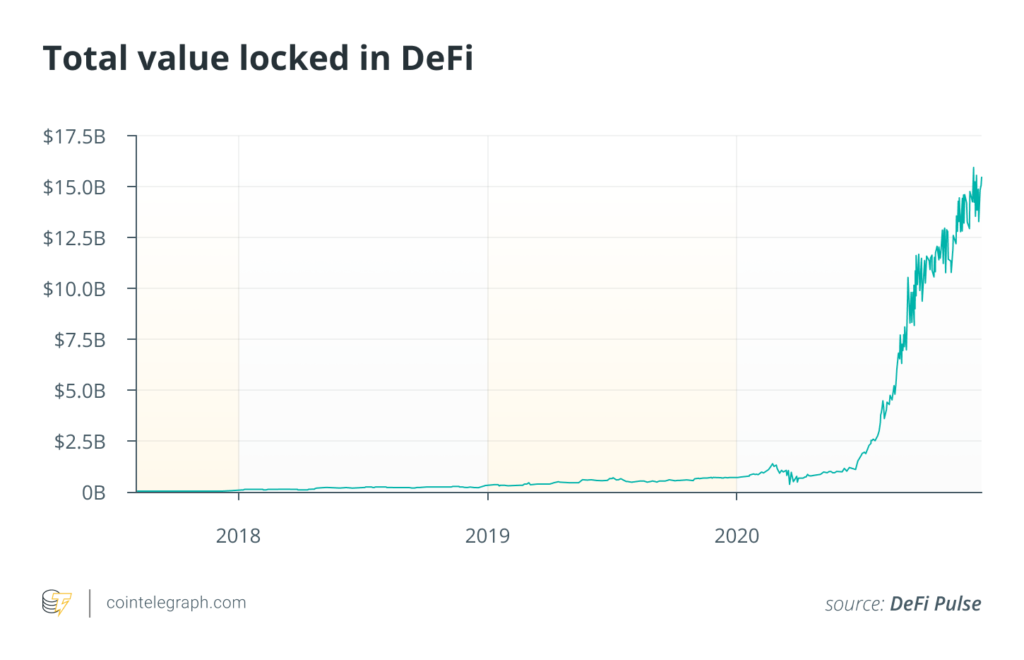
As the TVL in DeFi grows, it becomes critical for users to get at least a basic understanding of these hacks. Attacks such as price oracle manipulation, flash loans, and external referencing continue to surface time and again.
Let’s dive in and break down some of the major vulnerabilities in DeFi and how they’ve been successfully draining millions of dollars from renowned DeFi protocols!
Price Oracle Manipulation Attacks
Table of Contents
It becomes almost impossible to write this post without mentioning price oracle manipulation, considering it was one of the major attacks that blasted off in 2020 and are continuing to cause significant harm.
A report published by samczsun.com shows several issues with price oracle manipulation stemming from a few decentralized applications. The analyst notes that price oracle manipulation has resulted in ?over $30 million in losses so far and shows no signs of slowing.?
While developers are familiar with vulnerabilities like reentrancy, price oracle manipulation is not something that is often considered. Conversely, exploits based on reentrancy have fallen over the years while exploits based on price oracle manipulation are now on the rise.
Considering the current scenario, a smart contract heavily relies on Oracles which provide an effective interface between the contracts and the external source to push the required data. Truth be told, getting accurate data with utmost security and reliability is still an enormous concern for the DeFi community.
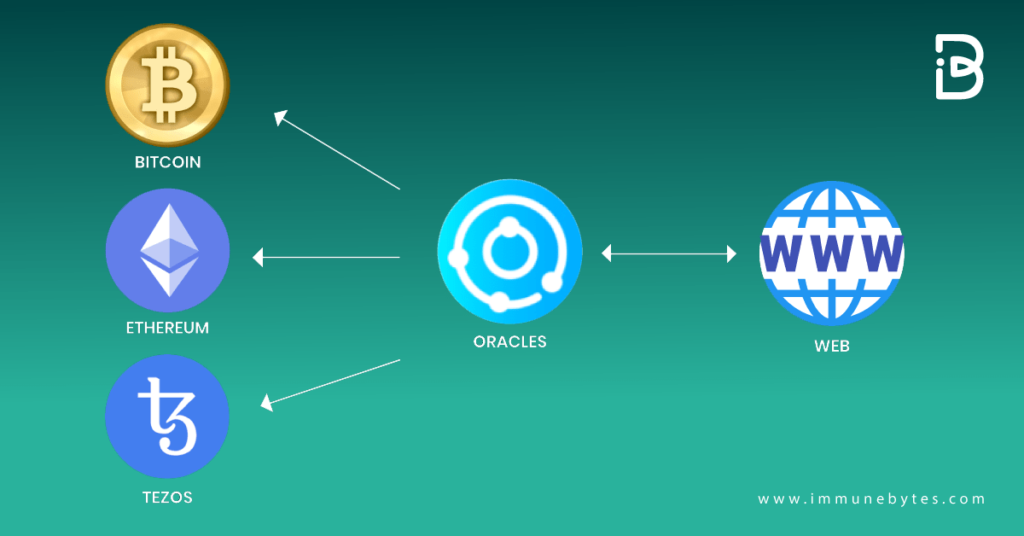
An oracle is a protocol that can record both on-chain and off-chain data and submits the data into a blockchain like Ethereum. These oracles are used in smart contracts, automated market makers (AMM), and trading platforms. One of the most popular ETH-based oracles is Chainlink.
So, why are these dangerous? Well, we haven’t reached the ?manipulation? part of it yet!
We already know that smart contracts are immutable. So, what happens when these oracles push inaccurate data into smart contracts?
You guessed it right, HACKS! It undoubtedly results in the faulty execution of the smart contract and that in turn favors some malicious actor. And with some of the biggest Defi hacks like the bZx hack, Harvest, Cheese Bank hack, etc, the manipulation of decentralized price oracles can no more be overlooked.
Price oracles are a critical, but often overlooked component of the DeFi security audit
Moving on, we have another very important and popular member. You guessed it right! Flash Loans!
Flash Loans
A Flash loan is the ability to leverage uncollateralized DeFi capital to earn a profit. They enable users to borrow funds instantly from a liquidity pool.
The catch? A flash loan must be repaid in the same transaction.
And what’s the point of such a loan? In the case of a flash loan, you can think of your transaction as being made up of three parts: receive the loan, do something with the loan that earns you some profit, and repay the loan. And all that happens in a flash!
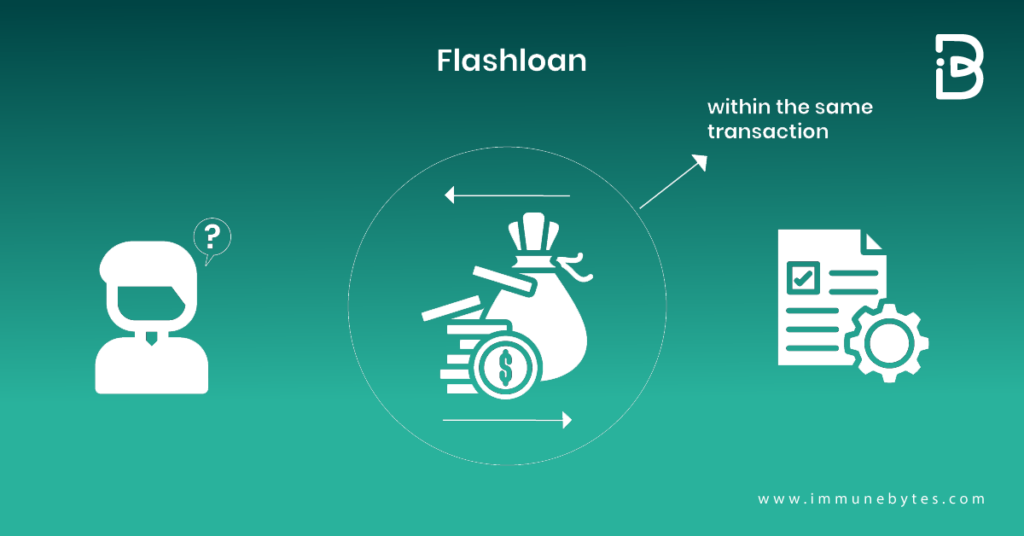
In simpler words, flash loans are atomic. If you, by chance, fail to pay back the loan, the whole thing gets reversed as though the loan never even happened. Something like this could only exist on blockchains as smart contract platforms guarantee that transactions are processed one at a time.
Projects such as Aave or dYdX developed smart contracts that allow DeFi users to borrow different coins from a designated pool under the condition that they are repaid within the same Ethereum transaction. There is usually a fixed cost associated with using flash loans.
Flash loans were used in most of the recent DeFi hacks and allowed hackers to magnify their potential profits as they do not require any upfront funds. One of the most famous acks was the BzX hack where a flash loan was used to manipulate the Uniswap oracle price. Of course, the issue was not in the use of flash loans, but rather in some incorrect assumptions when it comes to using Uniswap as a price oracle.
In itself, a flash loan isn’t necessarily bad. The problem lies in the fact that flash loans permit anyone to access an enormous amount of funds without any collateral. And these funds can then quite easily be used to manipulate the entire market, cause massive slippage, etc.
Flash loans are a burgeoning innovation in the DeFi industry, but they’ve certainly made a lasting impression. This concept of uncollateralized loans opens up a whole new world of possibilities in a new financial system, if only you’re careful though!
That’s flash loans for you! Next up is External Calls!
External Calls
One of the most renowned hacks in the history of DeFi, The DAO Hack, was a consequence of External Contract Calling. The hack where the attacker was able to steal 3.6 million ETH in the very first few hours of the attack by sampling the re-entering of the contract again and again.
Additional Resource: What is a DAO?
While making an external call you shift the control over execution to an external party. Now, one of the most crucial parts that should be noted here is the fact that re-entering the contract is just one of the many things that the attacker can do with an external contract.
It’s not possible to eradicate the usage of external contract referencing as they hold their significance. However, we can minimize the repercussions of an external call in a smart contract.
How do you ask?
By keeping in mind some of these simple pointers!
- Identifying an external call
- Now, can this reference be manipulated?
- If yes, check for the following:
- Is the state changing before the external call?
- Can the data be read after the external call? If yes, can it be manipulated?
- Data can be read before the external reference but is modified once the call is executed.
If you successfully rectify these issues, rest assured you’ll be safe!
How Do Smart Contract Audits Help?
The DeFi market is growing at an incredibly exponential rate and its rise is inevitable. So, are the hackers.
With so much at stake, it’s high time for the community to understand that?smart contract audits can no longer be neglected.?
As the dependency on smart contracts increases, DeFi audits become crucial where an external party reviews every line of code and helps to identify the bugs and bottlenecks. If left unaudited, the DeFi contracts may result in extreme consequences that involve heavy loss of funds and manipulation of the blockchain system. Sometimes, it may even lead to the shutdown of the company. Therefore, it becomes essential to check the quality of the team auditing your DeFi contract and get familiar with their process of auditing.
A third-party security audit not only secures your application but also provides you with propositions on how to make it better!
About Us
ImmuneBytes is facilitating blockchain security by employing the use of cutting-edge techniques on smart contracts and decentralized applications. We have a team of experienced security professionals who are adept at their niches and provide innovative solutions and consultation. So far we have worked on 175+ blockchain start-ups on different blockchain frameworks, with clients spread across the globe, and are continually unfolding ourselves to make this decentralized movement thrive.

