Over years, the digital business landscape has advanced due to rapid refinements in tech and also because of the adoption of assets, offering a feasible environment to organizations. However, with this digital expansion, cyber risks also boomed with more targeted attacks against communities. Since the last decade, there has been persistent growth in cybercrimes and newly introduced hacking tactics.
Security audits are a high-level depiction of the numerous ways organizations can test and review their overall security measure, including cybersecurity. An organization might employ more than one type of security audit to achieve the desired level of results to meet their business pursuits.

This blog will serve as a comprehensive discussion about the importance of security audits, their methodology, and their benefits to help you assess your security and fill any gaps you might find.
What is a Security Audit?
Table of Contents
A security audit is a comprehensive analysis of an organization’s security practices and information system. Performing a security audit helps organizations in finding and assessing the vulnerabilities existing within their networks, connected devices, and applications. It qualifies you to fix any security loopholes, and achieve compliance.
A security audit exposes all our system’s vulnerabilities. They help institutions stay ahead of insider threats, security breaches, and other cyberattacks that put the organization’s security, reputation, and finances on the line.
Additional Resource : What is a Smart Contract Security Audit
Let us now get familiar with how they work.
How Does a Security Audit Work?
Every organization has its set methodology and tools that it follows while conducting the audit. However, the basic workflow remains the same for all.



According to the auditors at ImmuneBytes, a security audit should follow this basic format:
Agree on Goals and Define Assessment Criteria
A security audit is only as complete as its early definition. Specify the overall objectives the company needs to address in the audit, and then break those down to departmental preferences. Get sign-off on all business pursuits of the security audit and keep track of out-of-scope items and exceptions.
Things to consider:
- Industry and geographic standards (e.g., HIPAA, CCPA, GDPR, etc.)
- Keep a catalog of all uncovered risk vectors
- Utilize outside resources when possible, an experienced security auditor or a blockchain security audit firm can help you ask the correct questions and steer the audit successfully
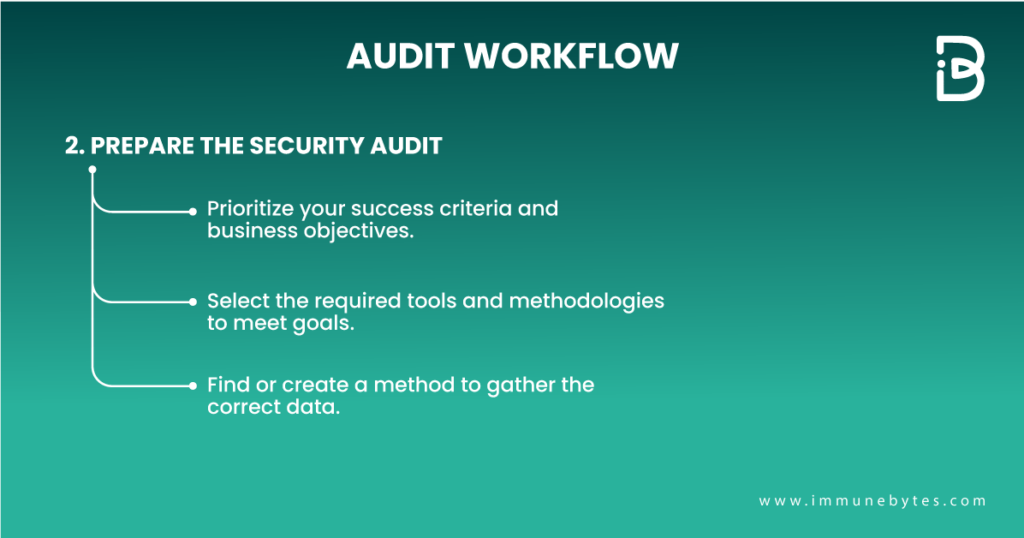
Prepare the Security Audit
In order to deliver a satisfactory audit, companies have to align their actions with the top items on their list. During this phase, select the tools and methodologies required to meet the business objectives. Find or create a suitable questionnaire to gather the correct data for your audit. Avoid square pegging tools into the round holes of your necessities and one-size-fits-all surveys.
Conduct the Security Audit
During the audit, provide appropriate documentation and perform due diligence throughout the process. Monitor the progress of the audit and also the data points collected for accuracy. List potential threats according to their severity levels. Threats can include the loss of data, equipment, or records through natural disasters, malware, or unauthorized users.

There are a few possible challenges surrounding a successful security audit:
- Avoid on-the-fly assessments and trust the process.
- Stand by the facts of your results.
- Beware of poorly defined scope or requirements in your audit.
- Stay focused on risk assessment.
Why is a Security Audit Important?
A security audit protects the critical data resources of an organization and helps in keeping it compliant with various security certifications. It identifies security loopholes before hackers. Getting your platforms audited will keep an organization updated with security measures and helps in formulating new security policies for the organization.
Another very important aspect that an audit possesses is that it prepares the organization for emergency response in case of a cybersecurity breach and the means to tackle it.
What Is The Main Purpose of a Security Audit?
A security audit provides a roadmap of your organization’s main information security weaknesses and identifies where it is meeting the criteria the organization has set out to follow and where it isn’t. It is also crucial when it comes to building trust among your customers and users.
Security audits are critical to developing risk assessment plans and mitigation strategies for organizations that deal with individuals? sensitive and confidential data. An audit will build a hack-proof wall around your project, safeguarding it from any potential threats.
Why Do Companies Need Security Audits?
Companies need regular security audits to make sure they are:
- properly defending their clients? private information
- complying with federal regulations
- and avoiding liability and costly fines
To avoid penalties, companies need to keep up with ever-changing federal regulations like HIPAA and SOX. Periodic security audits are necessary to make sure your organization is up to speed with any new requirements.
What Systems Does an Audit Cover?
During a security audit, each system that an organization employs may be examined for vulnerabilities in the following areas:
Network Vulnerabilities
Auditors examine for network vulnerabilities that an attacker might exploit to access approaches or information or cause damage. Security audits and regular network monitoring keep track of network traffic, including emails, instant messages, files, and other communications. Network availability and access points are also a part of the audit.
Security Controls
In this, the auditor looks at how convincing a company’s security controls are. This includes evaluating how well an organization has enforced the policies and strategies it has established to defend its information and systems.
Encryption
This part of the audit verifies that an organization has measures in place to manage data encryption processes.
Software Systems
Software systems are examined to ensure they are working properly and providing accurate information. They are also checked to ensure controls are in place to prevent unauthorized users from gaining access to private data. The areas examined include data processing, software development, and computer systems.
Architecture Management Capabilities
Auditors verify that IT management has organizational structures and procedures in place to create an efficient and controlled environment to process information.
Telecommunications Controls
Auditors check that telecommunications controls are working on both the client and server sides, as well as on the network that connects them.
Systems Development Audit
Audits covering this area verify that any systems under development meet security objectives set by the organization. This part of the audit is also done to ensure that systems under development are following set standards.
Information Processing
These audits verify that data processing security measures are in the establishment.
What to Include in the Audit Report?
An audit report, though delivered at the end of the whole process, is the most crucial part of the process. It can make or break a deal for you. Here are some pointers that should be included in order to deliver a comprehensive audit report:
- List of all identified vulnerabilities classified into distinct risk levels as High, Medium, and Low severity.
- An elaborate description of every issue should be provided by the auditors.
- Remediations on how to solve the discovered issues and optimize the existing codebase.
About ImmuneBytes
ImmuneBytes is a blockchain security audit firm, focused on providing comprehensive smart contract audit services. We help startups and enterprises safeguard their applications before they turn into expensive exploits. The company was founded with a distinct aim to foster security in the blockchain sphere and enthusiasm to improve the performance of large-scale systems.
Blockchain technology has undoubtedly revolutionized many industries. However, Blockchain networks are secure, and applications running on them might not be. ImmuneBytes conducts rigorous smart contract audits, employing both static and dynamic methods, while also examining a contract’s code and gas optimization, leaving no bugs hidden.

