Since the invention of cryptocurrency, 51% of attacks have existed in the crypto community. No cryptocurrency, including Bitcoin and Ethereum, is immune to the fear of this attack. An attempted 51% attack on Verge, a cryptocurrency focused on privacy, occurred last week on February 16th, leading to a significant blockchain redesign that erased more than six months’ worth of transactions.
51% Attacks: Introduction
Table of Contents
Before we begin with the explanation of 51% attacks, it becomes crucial to understand mining in blockchain-based systems.
In a blockchain-based system, the most important underlying structure is the distributed nature of the building and verifying data. The Bitcoin consensus algorithm, Proof of Work, is what assures that miners are only able to validate a new block of transactions if the network nodes collectively agree that the block hash provided by the miner is accurate, thus revoking the command of any single centralized authority on the network.
Since the process of mining involves the validators investing huge amounts of electricity and computational resources, referred to as hash power. The mining power is distributed over different nodes across the globe, which means the hash rate is not in the hands of a single entity. At least, it isn’t supposed to be. But what happens if one single entity or organization can obtain more than 50% of the hashing power?
One possible consequence is a 51% attack, also known as a majority attack.
Additional Resource: Most popular Blockchain Security Issues
What is a 51% Attack?
51% attack? occurs when a single miner or mining group takes majority control of a Proof of Work-based blockchain and double-spends some of its coins.
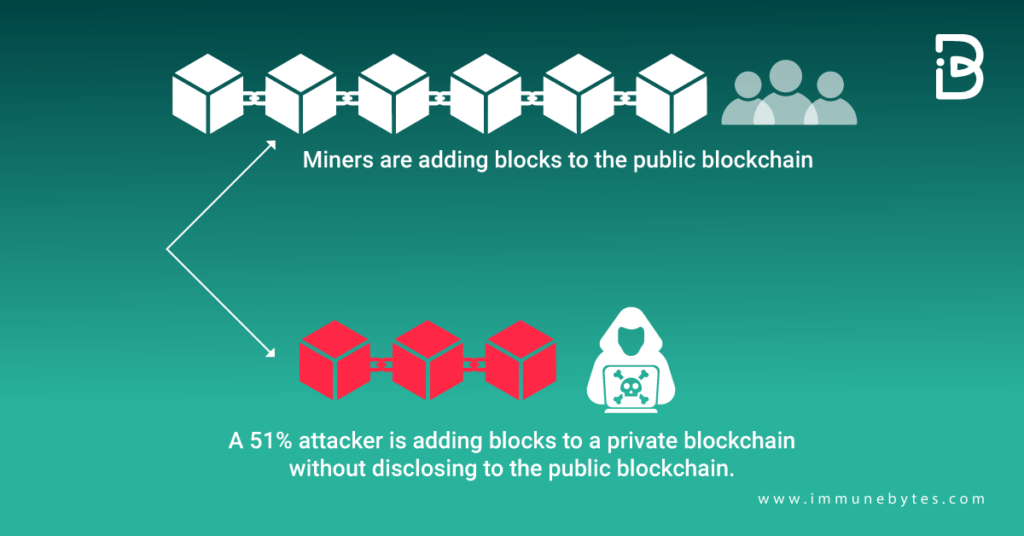
An actual 51% attack happens in just a few steps. First, the entity or person that is interested in attacking the network would have to acquire enough hash power to successfully mine blocks on a copy of the network’s chain secretly. This secret chain works in parallel to the original. Thus, buying a network’s hash power becomes the key to carrying out a 51% attack.
51% attack: How Hazardous is it?
Although a 51% attack can allow the double-spend of millions of dollars worth of cryptocurrencies, the resources required to carry it out do not come cheap.
For example, the cost of carrying out a 51% attack for an hour on Bitcoin’s blockchain would require $612,664, while an hour-long 51% attack on Litecoin would require only approximately $17,712. So, even though Bitcoin is under a 51% attack, the manipulation is unprofitable.
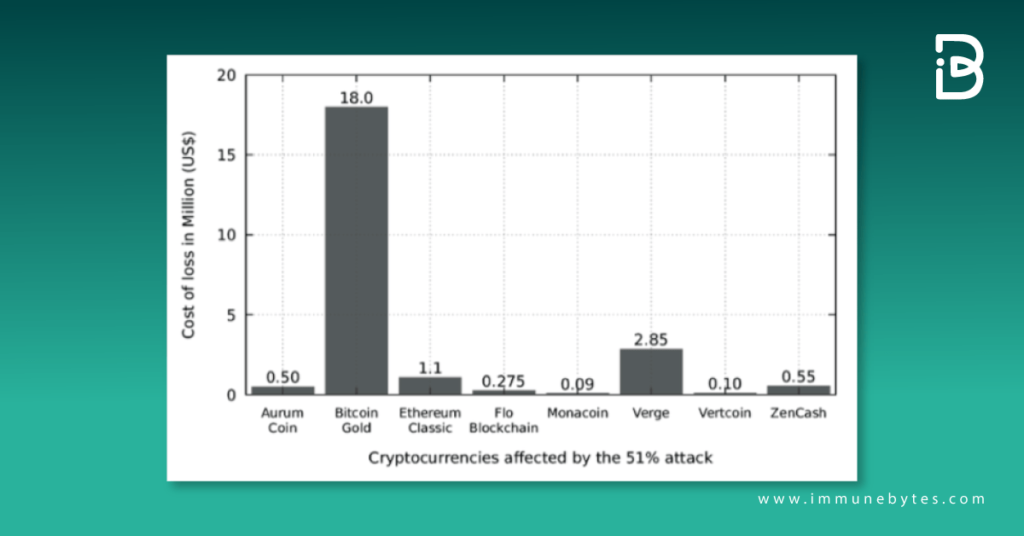
Source: https://www.researchgate.net
It is easier for a hacker to obtain more hash power on smaller networks than on the Bitcoin network, as they have a relatively lower hash rate. Examples of networks that have been victims of this attack include Monacoin, Bitcoin Gold, Verge, and ZenCash.
How to Prevent 51% Attacks
The most promising solution is to use a different consensus algorithm, Proof-of-Stake (PoS). PoS is based on a mining node staking its coins to become validators. Ethereum, Binance, and Neo have already made the shift from PoW to PoS.
Most networks use the Ethereum blockchain, but Ethereum 2.0 plans to use a PoS-based system to avoid problems. A 51% attack is unlikely because it would be unprofitable.
Recommend for Ethereum Smart Contract Audit
Conclusion
In the end, 51% of attacks are a threat that present PoW blockchains, not sufficiently decentralized or secure, suffer from. Combatting centralization and being one step ahead of potential bad actors is the most optimal solution given that there is an absence of bugs in the blockchain codes.
Cyber invasion continues to be inevitable even though more and more solutions are being found that promise to dodge this insufficiency. The good news is that these attacks give this industry, which is constantly evolving, valid grounds to research and advance.
About ImmuneBytes
We are a group of specialized security professionals situated in India. We work hard to advance and offer our clients top-notch service and general surveillance. We guarantee the security of your project and give business owners the freedom to operate hassle-free blockchain apps. Over 175 blockchain companies and businesses have hired us to make their audit of smart contracts at a reasonable price.